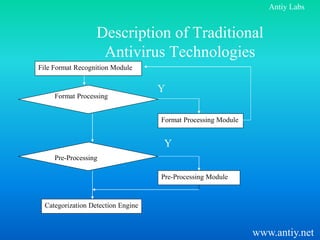
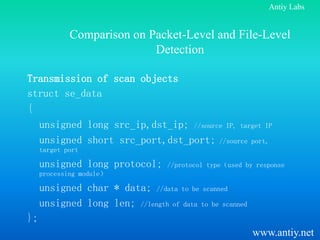
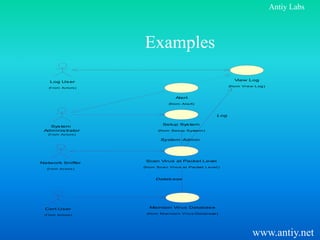
This document discusses virus detection based on network packet flow. It begins by comparing coarse file name detection used in Snort to higher granularity detection using virus signature strings. It then addresses problems with detecting viruses at the network level versus the file level, such as handling encoded network transmissions and meeting requirements for signature codes. Finally, it proposes using virus detection modules in firewalls and gateways to screen for malware without fully restoring files.