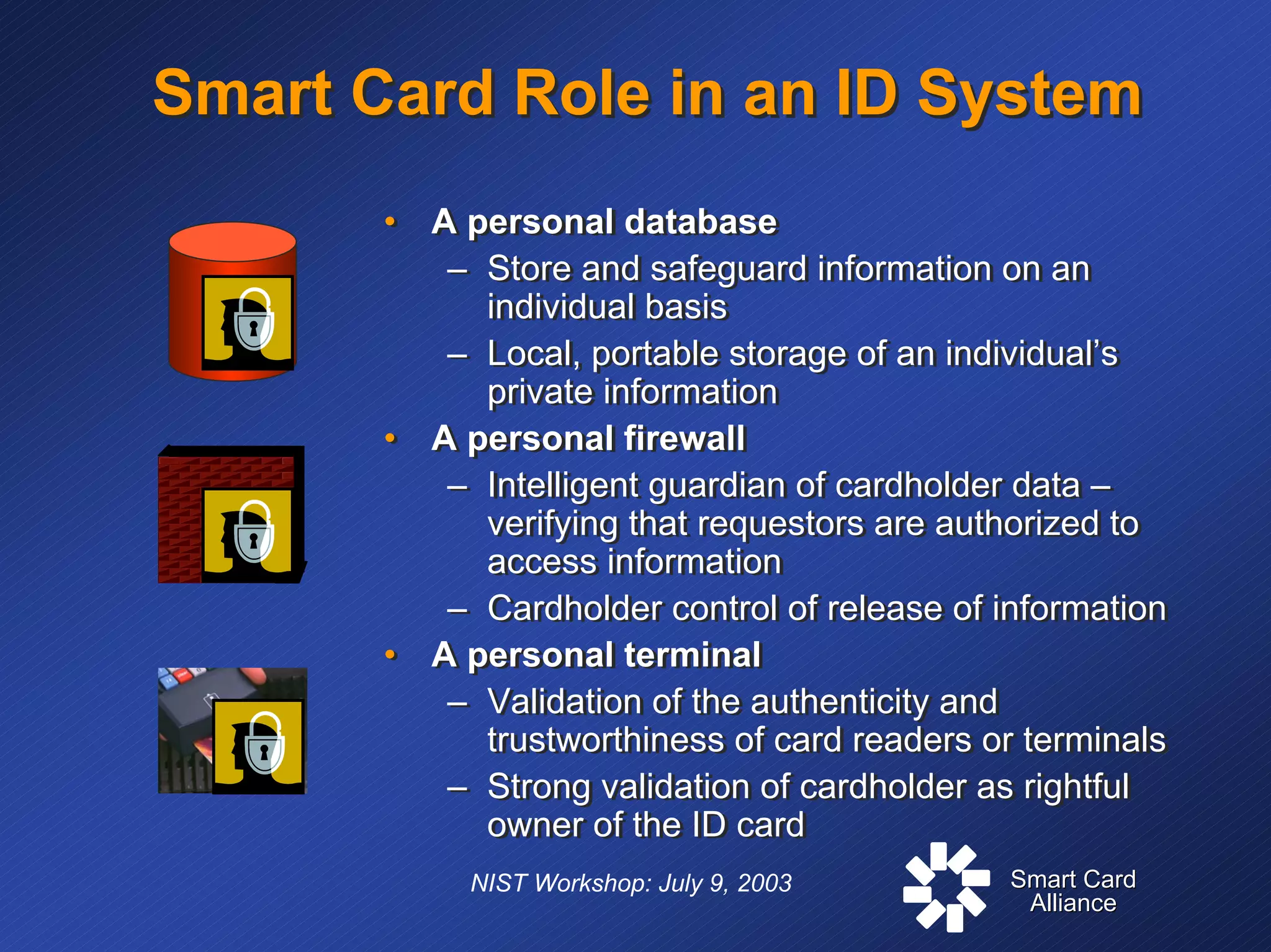
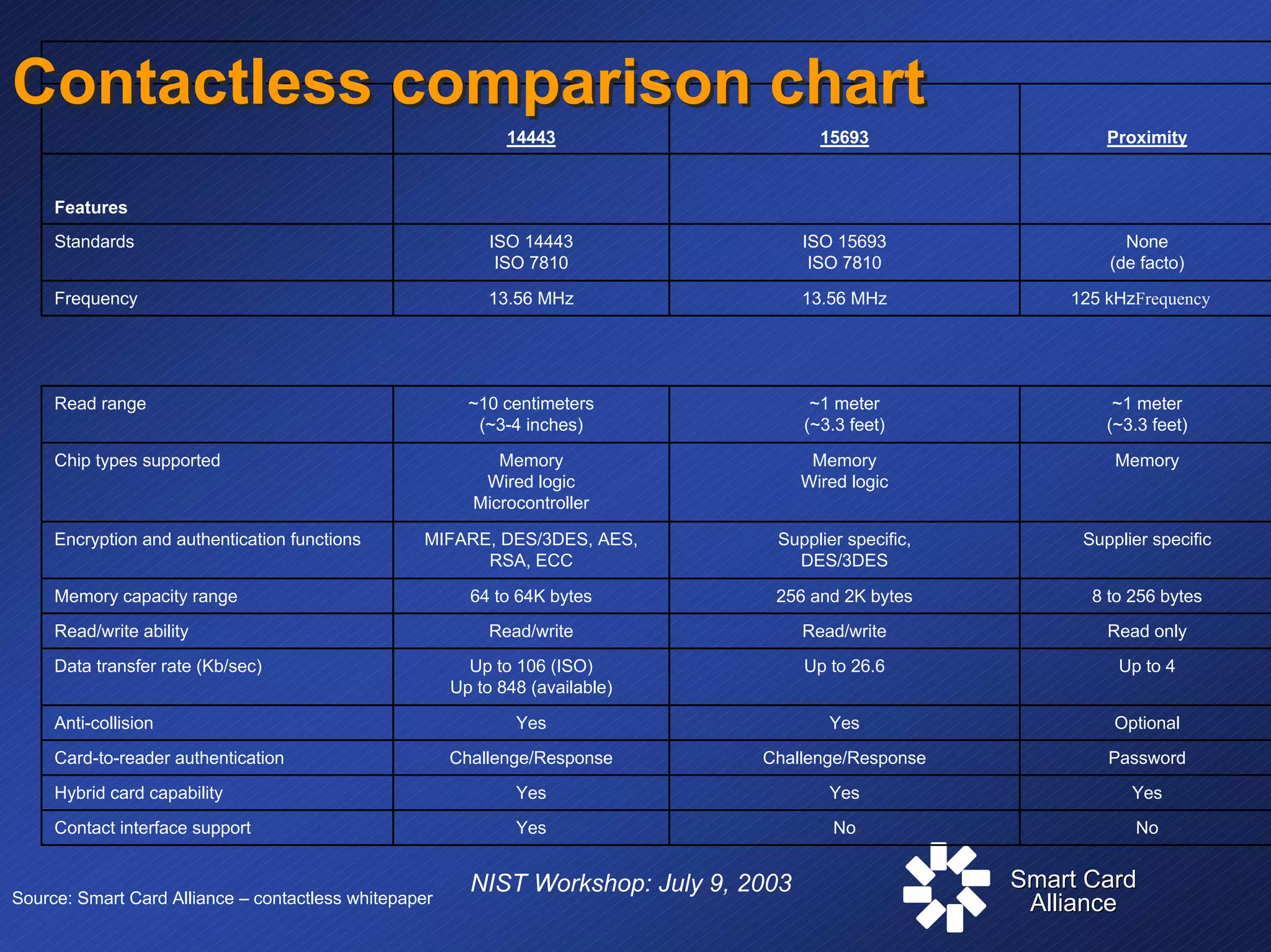
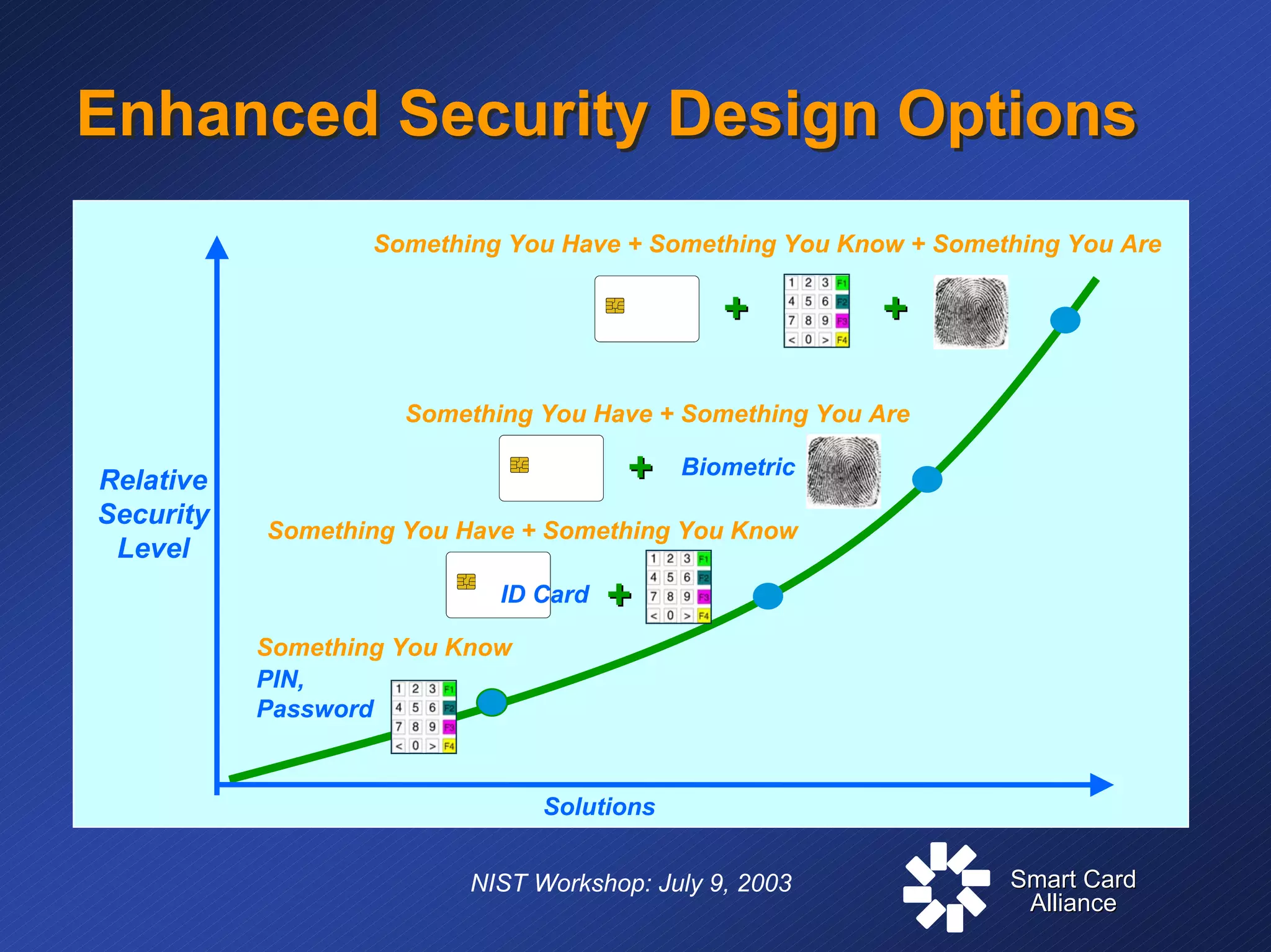
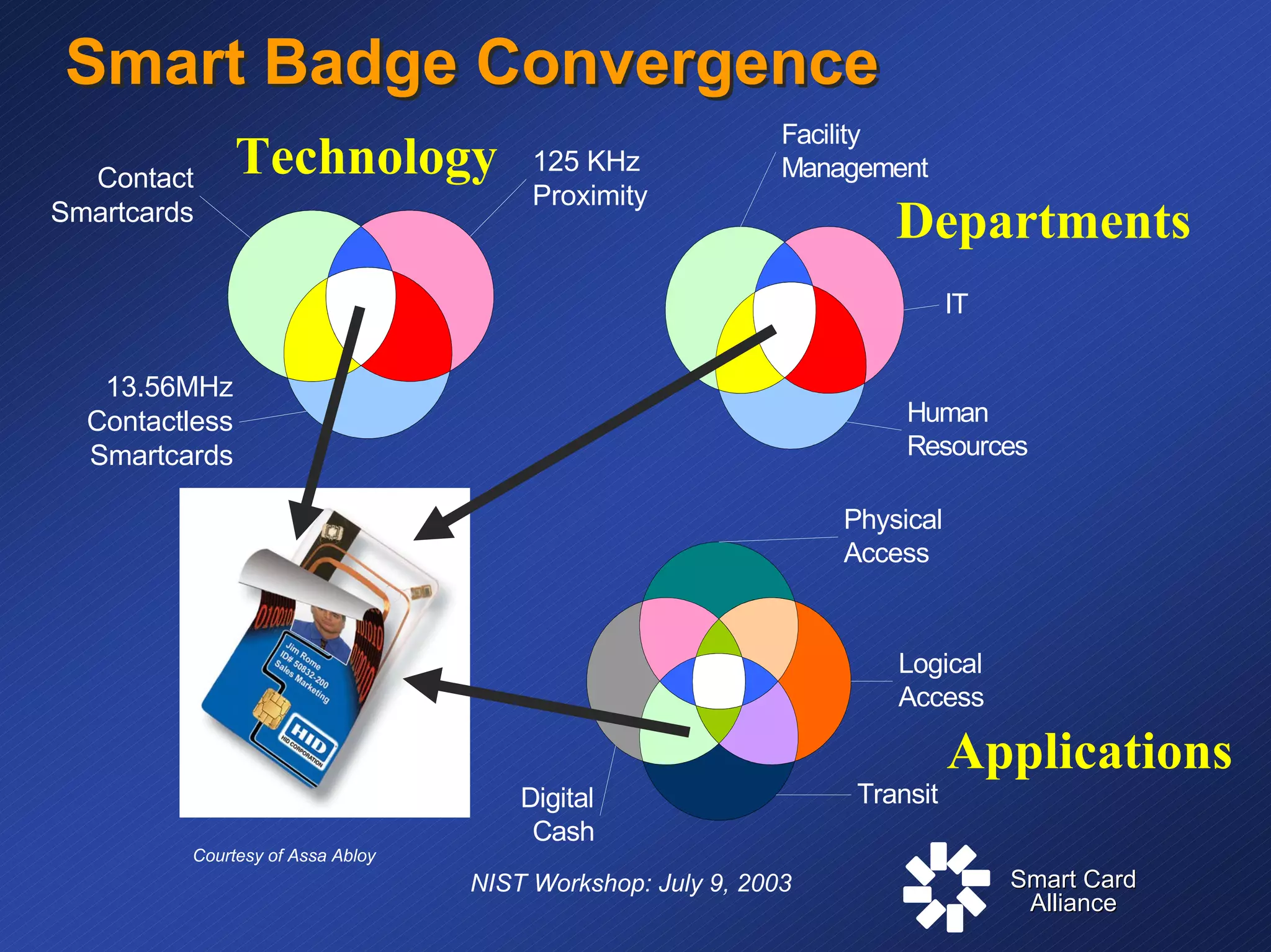
The document discusses standards and specifications for smart card technology for secure ID applications. It covers primary standards like ISO 7816 and PC/SC as well as security standards like FIPS 140. It also discusses specifications for interoperability such as Global Platform and industry specifications like EMV. The document outlines where different standards apply, from the interface between the card and terminal to application management. It addresses challenges in secure identification including balancing security and convenience.