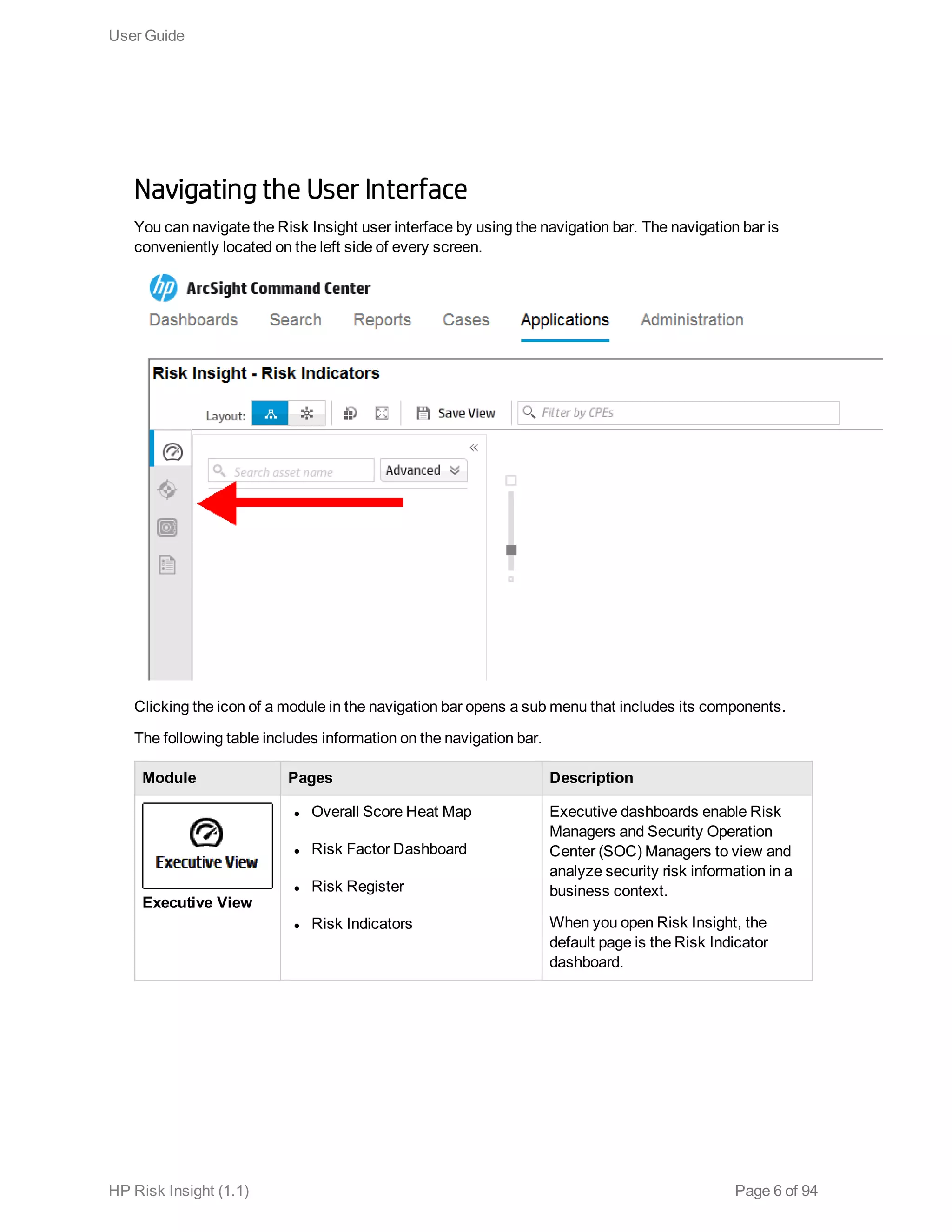
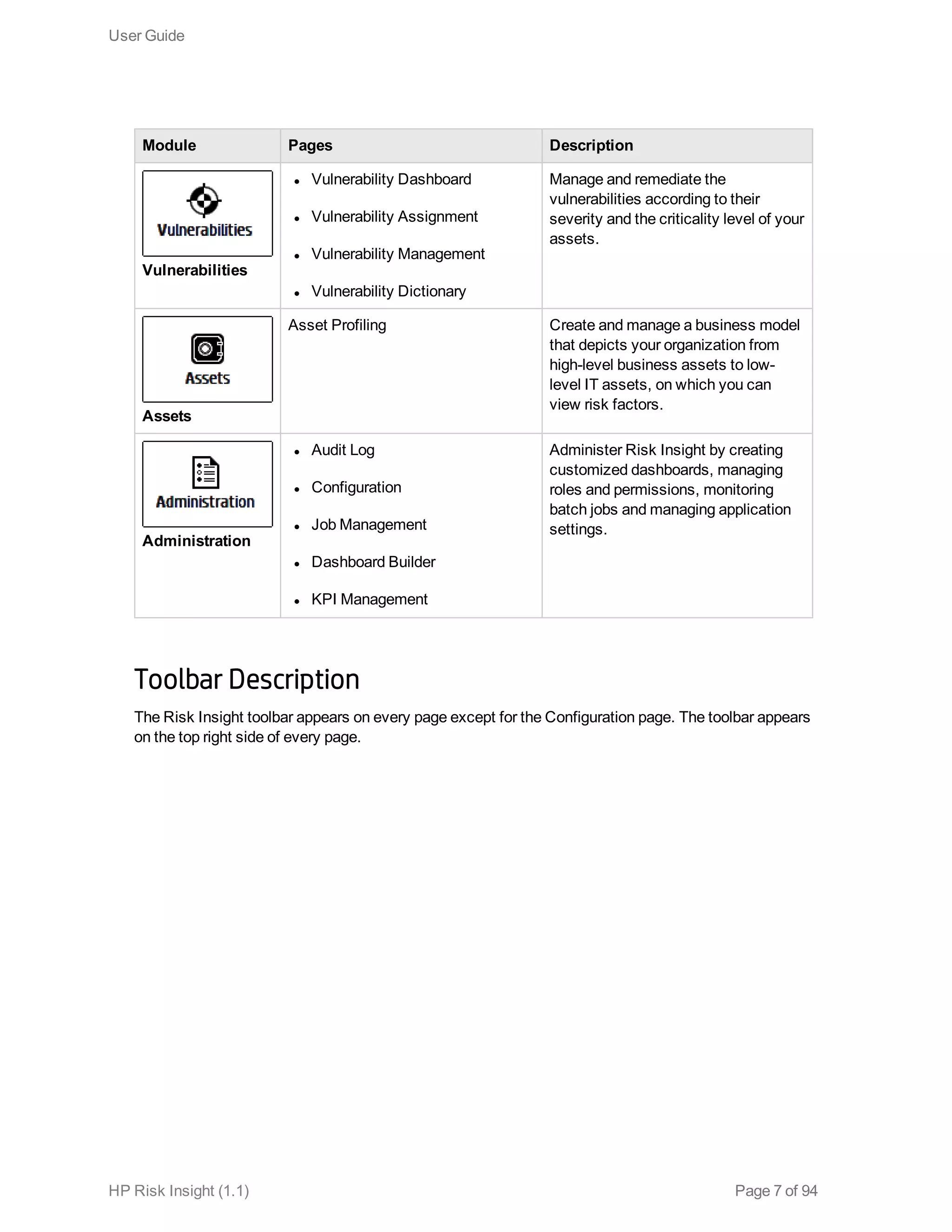
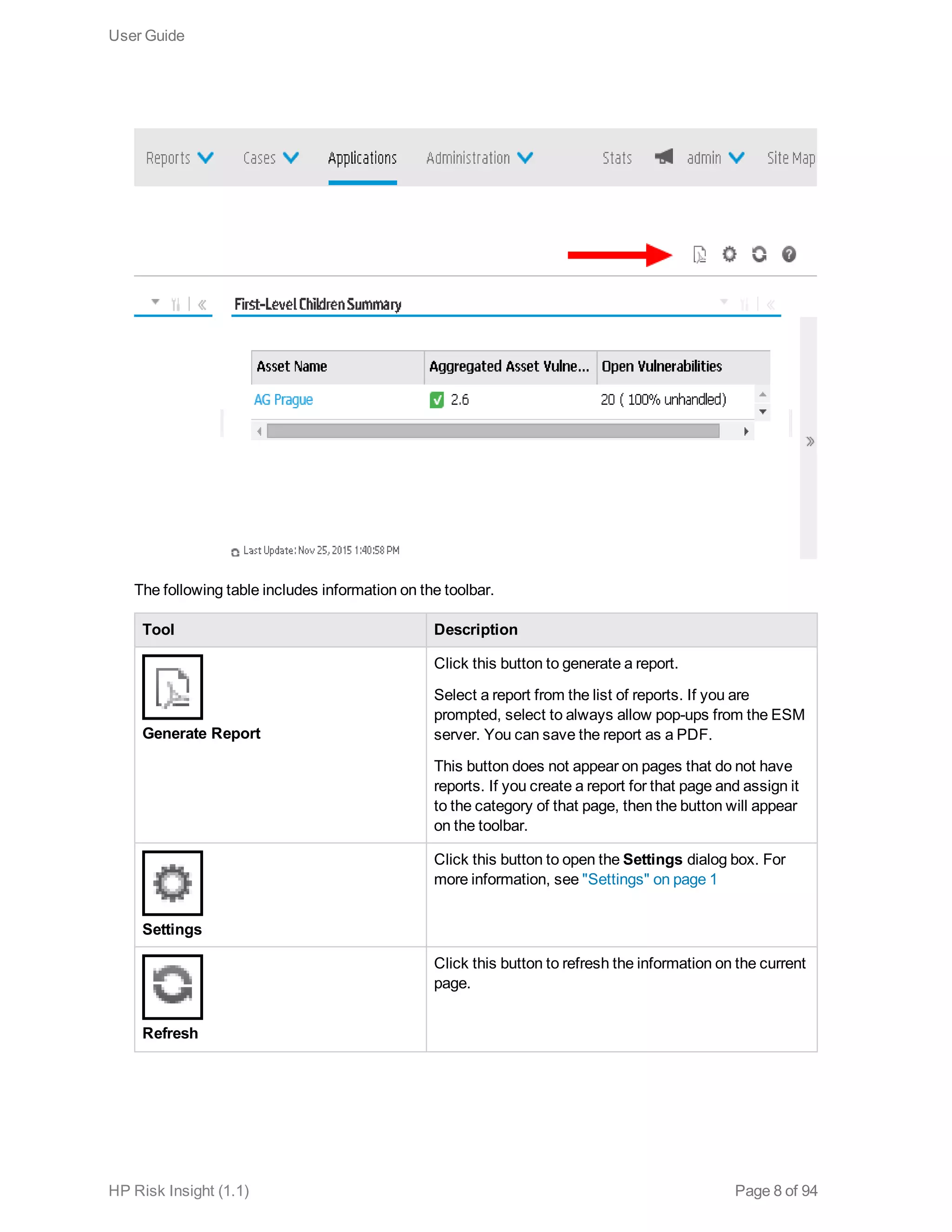
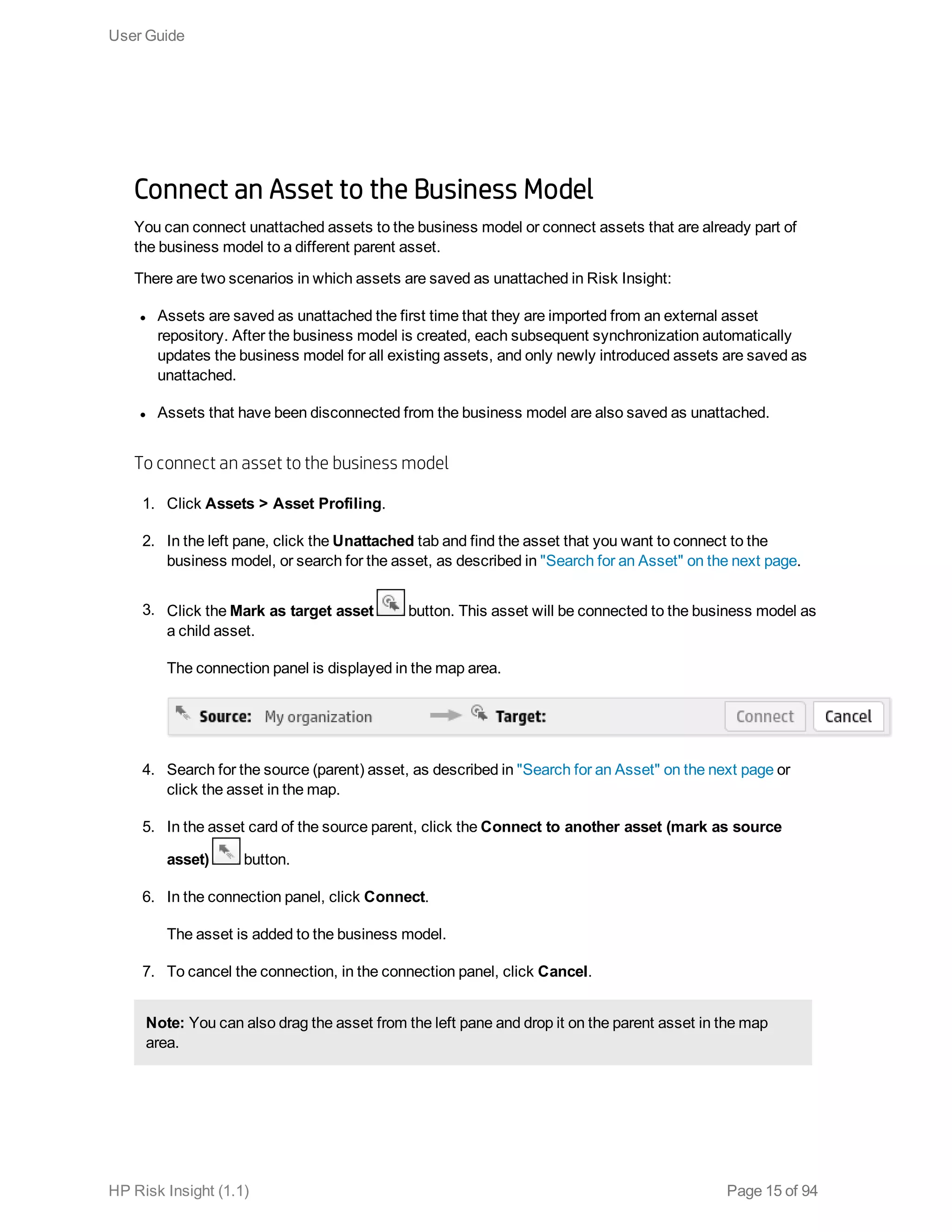
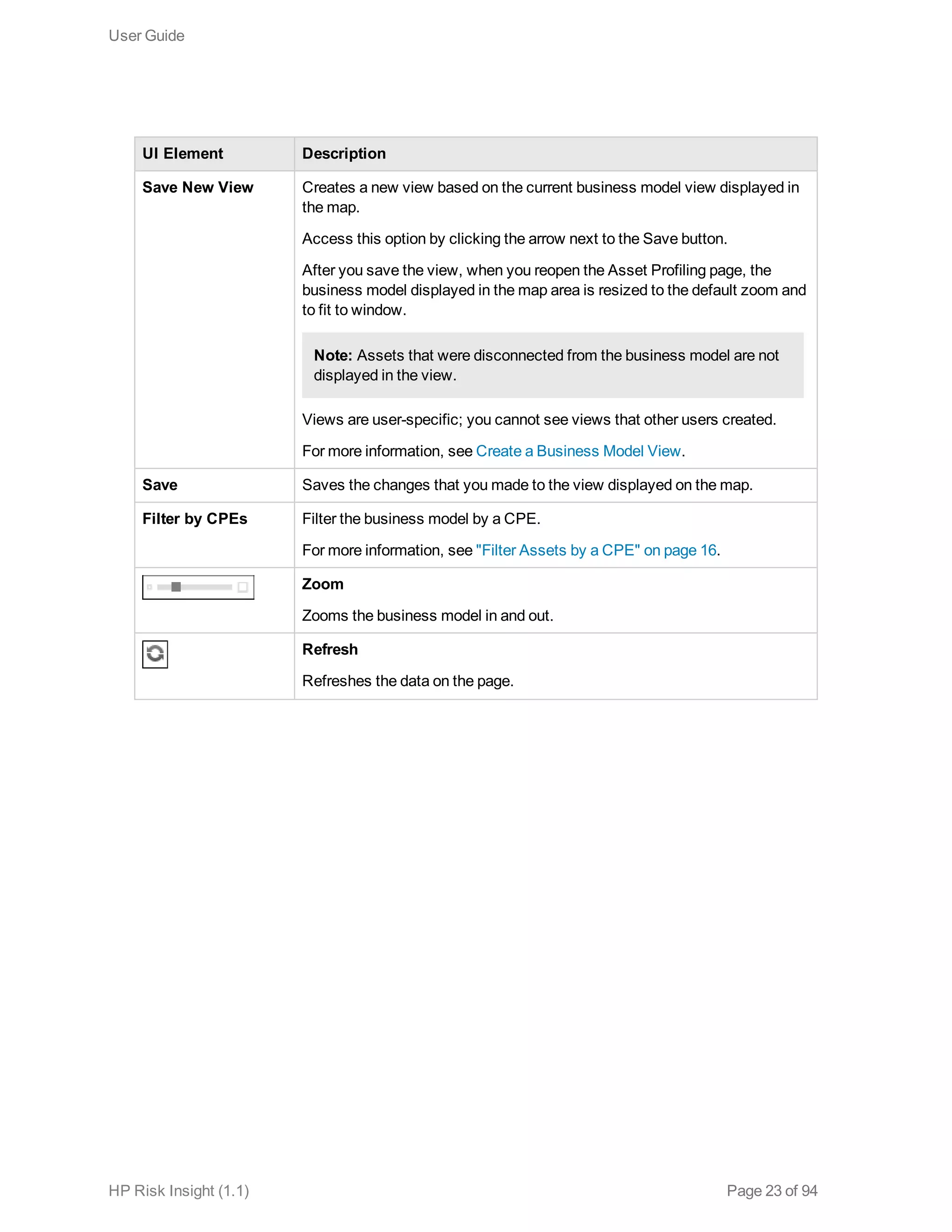
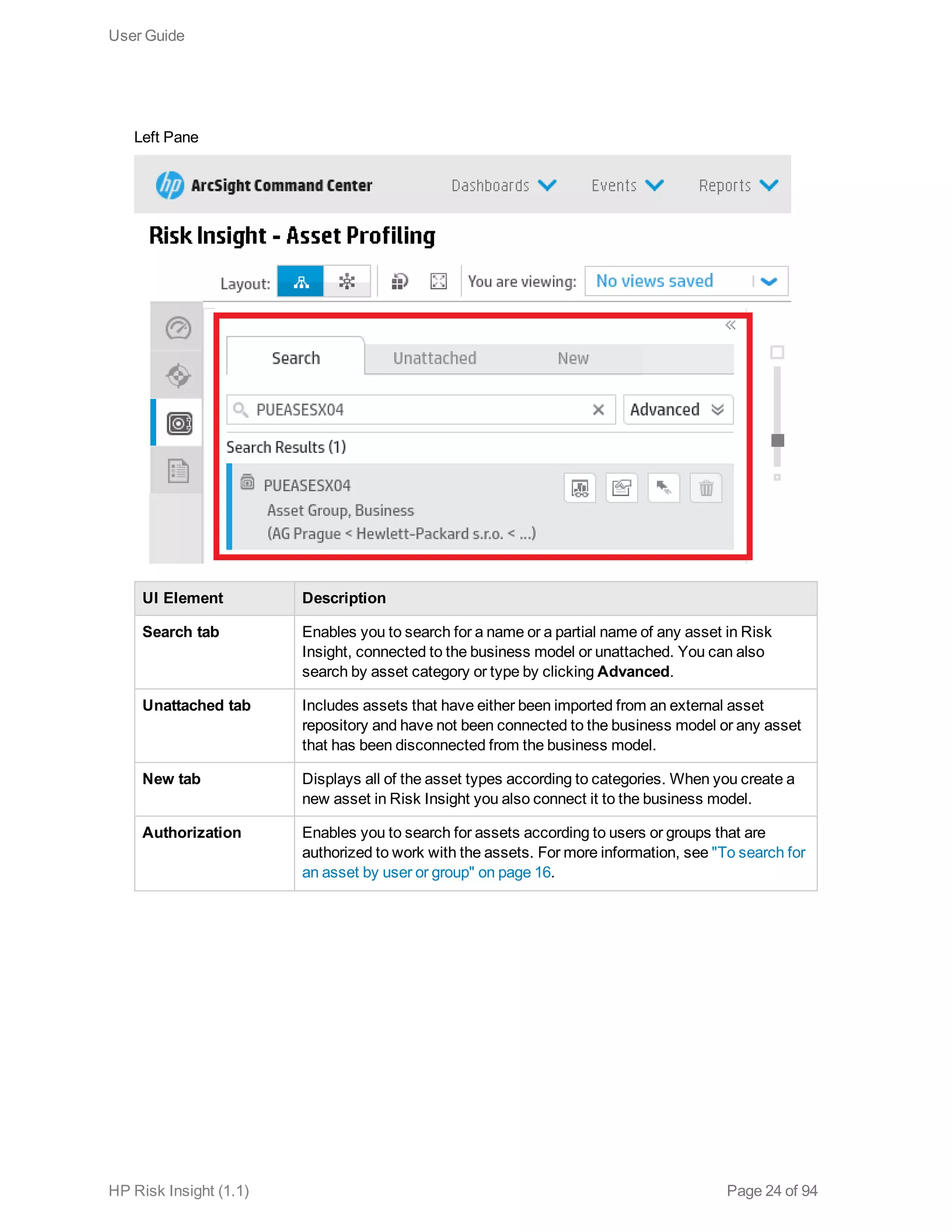
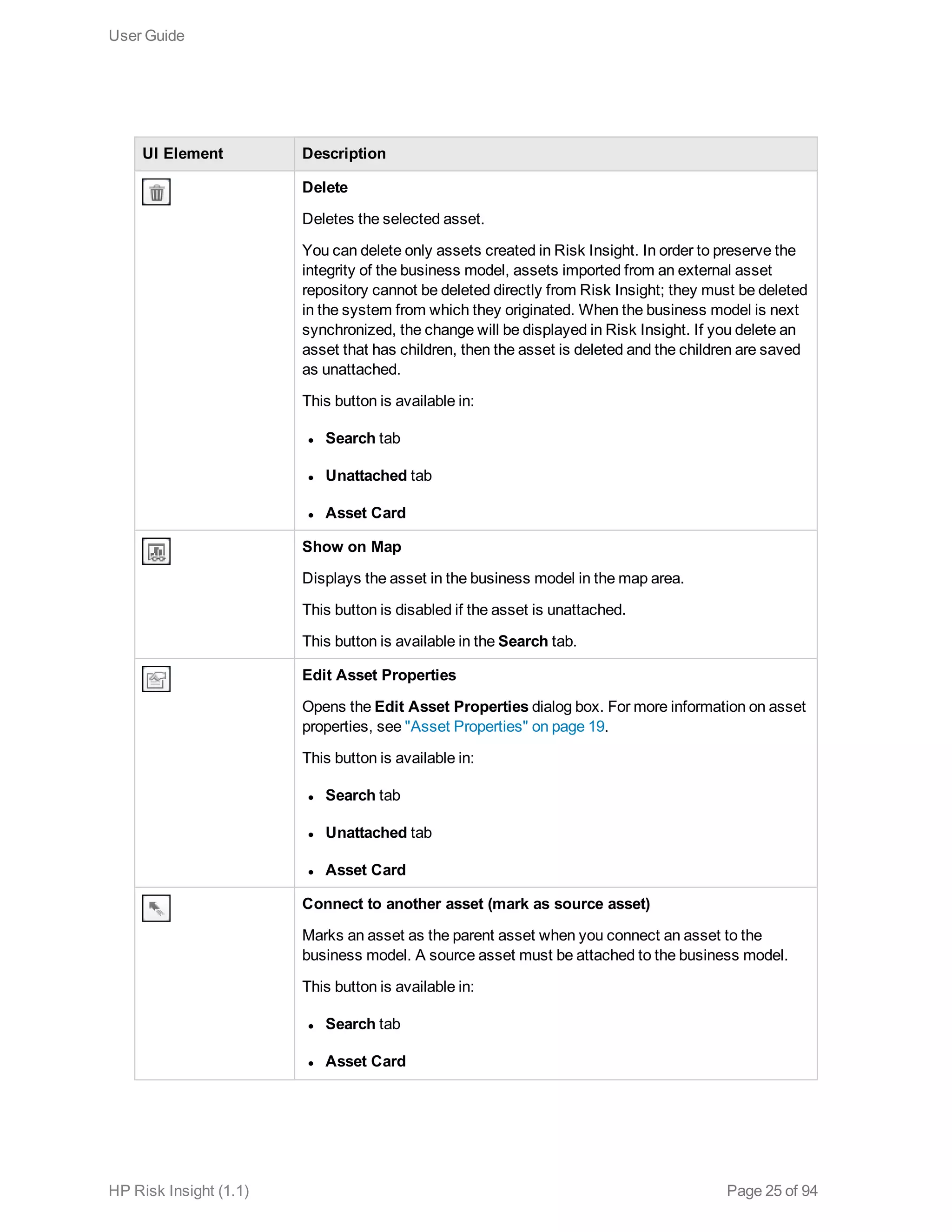
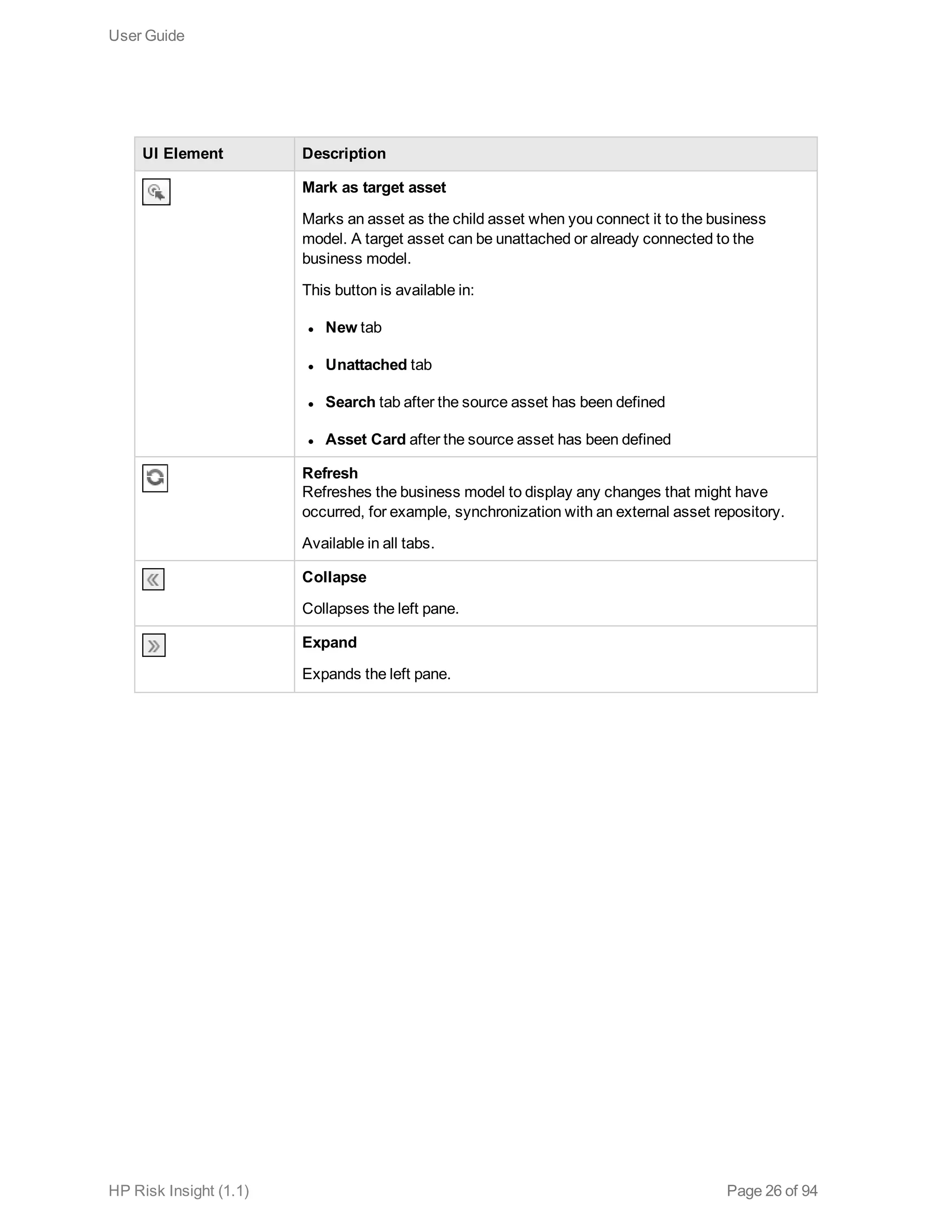
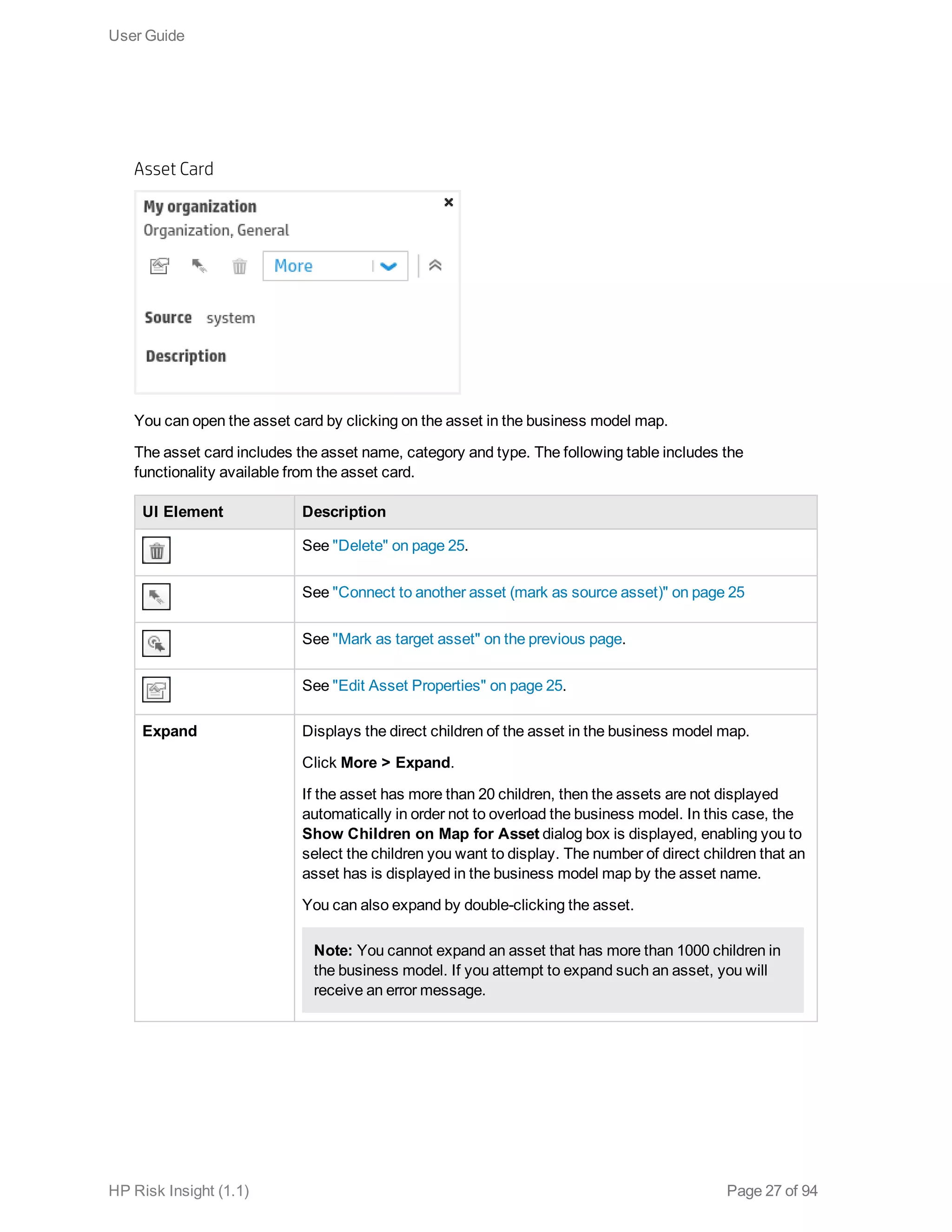
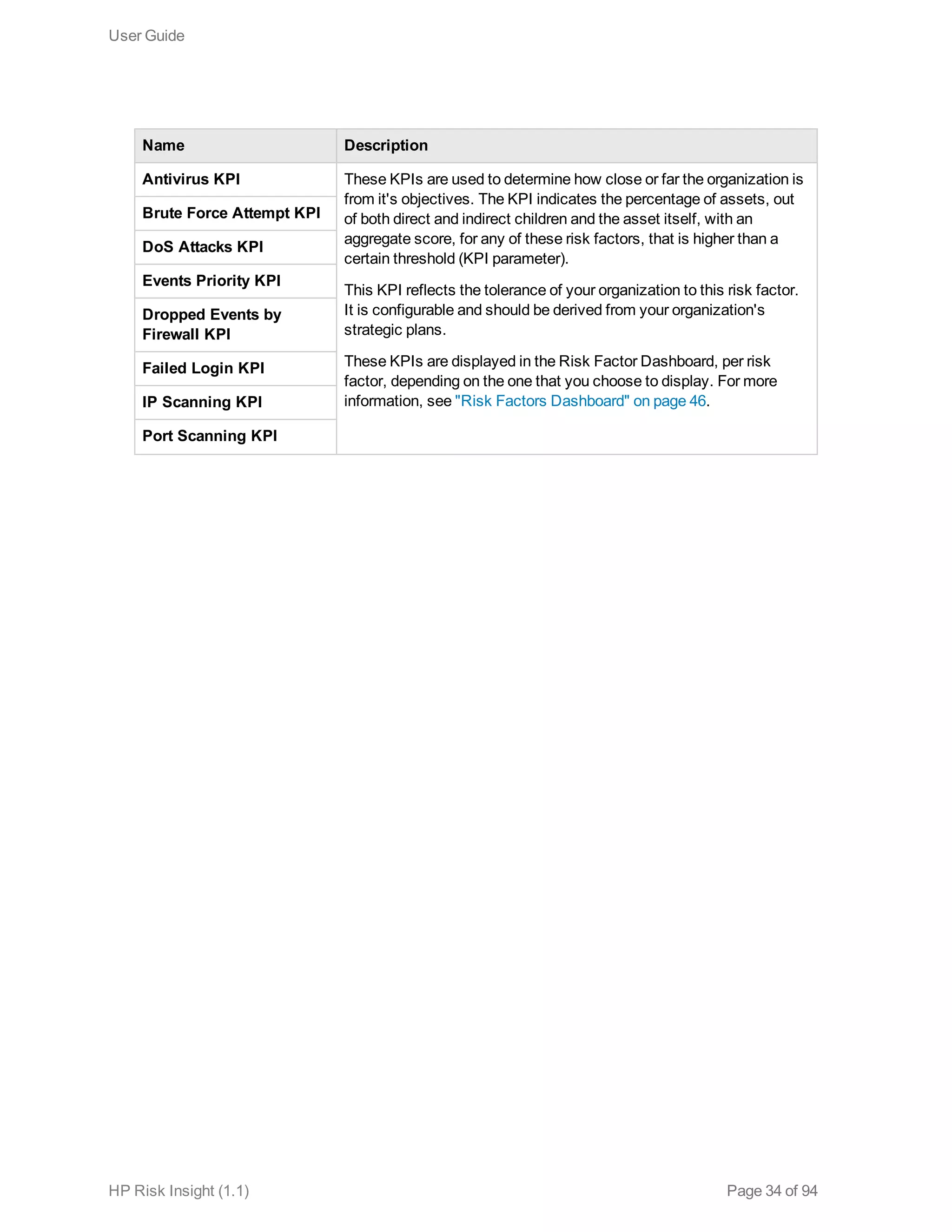
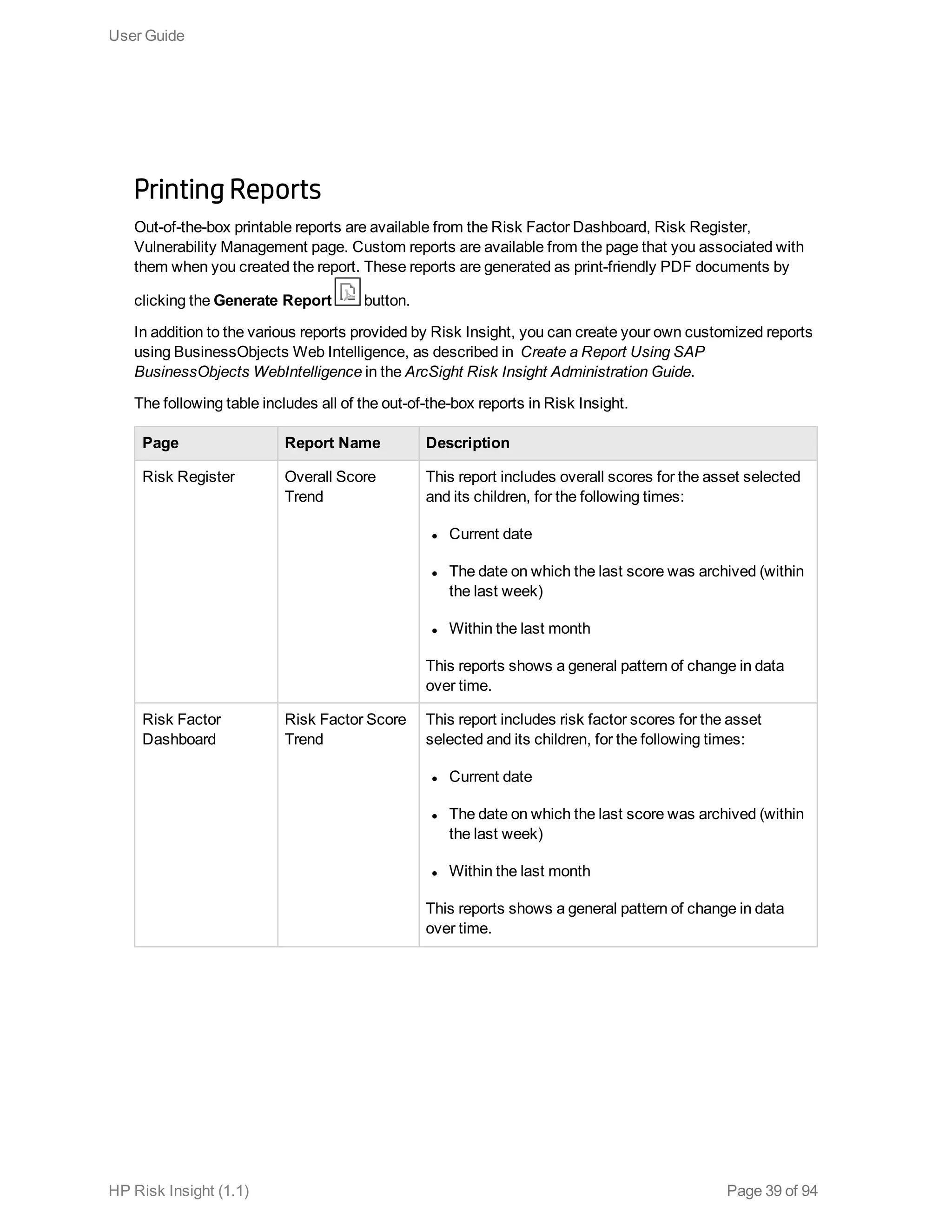
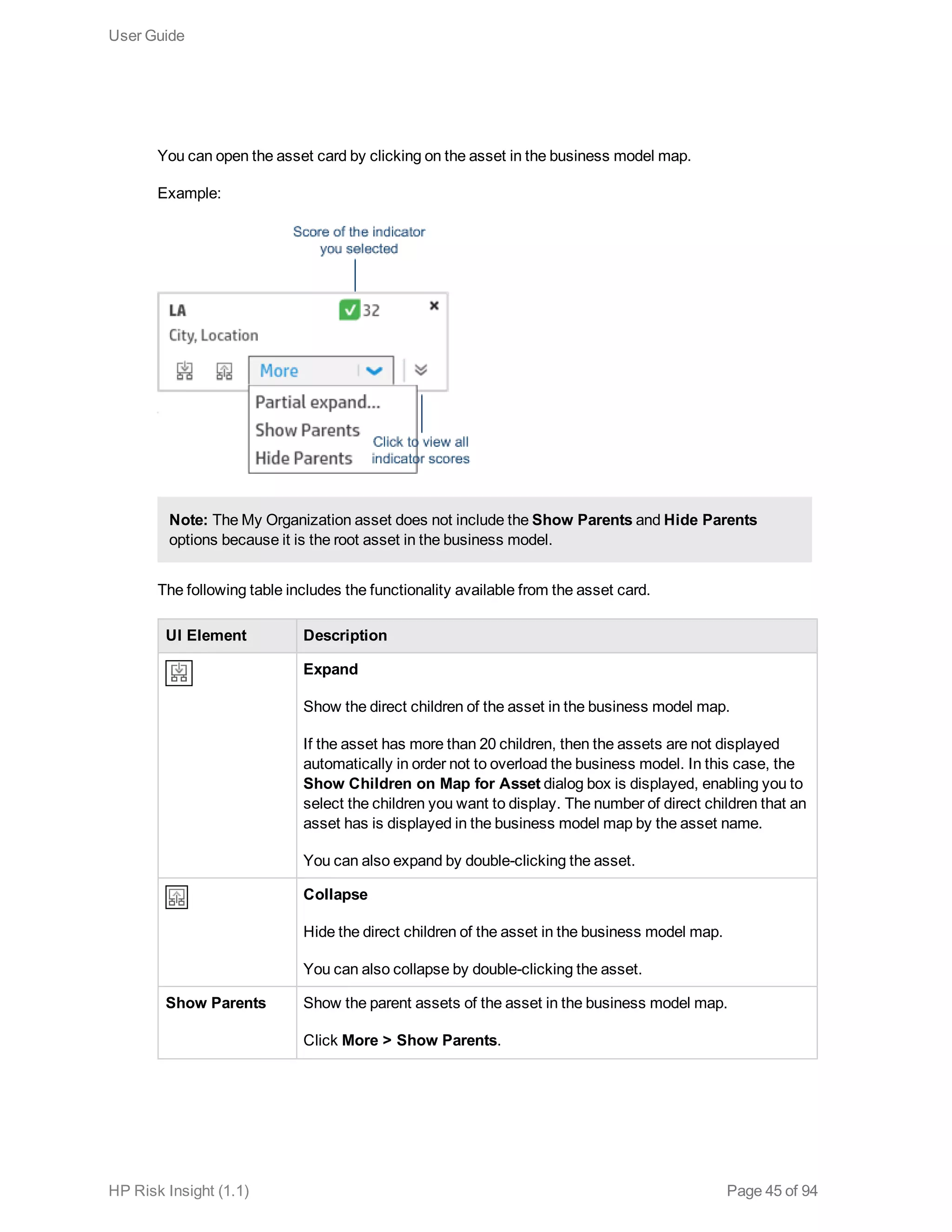
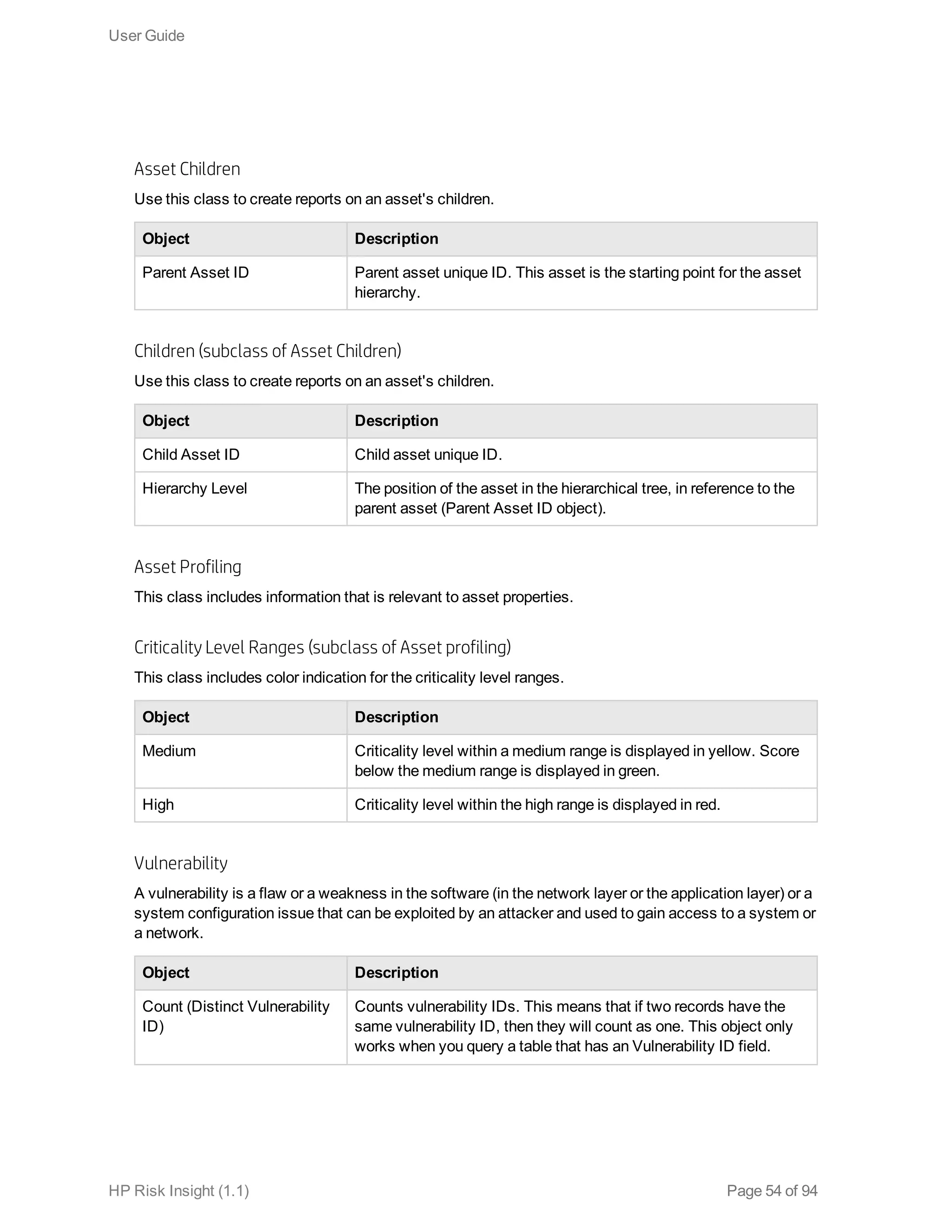
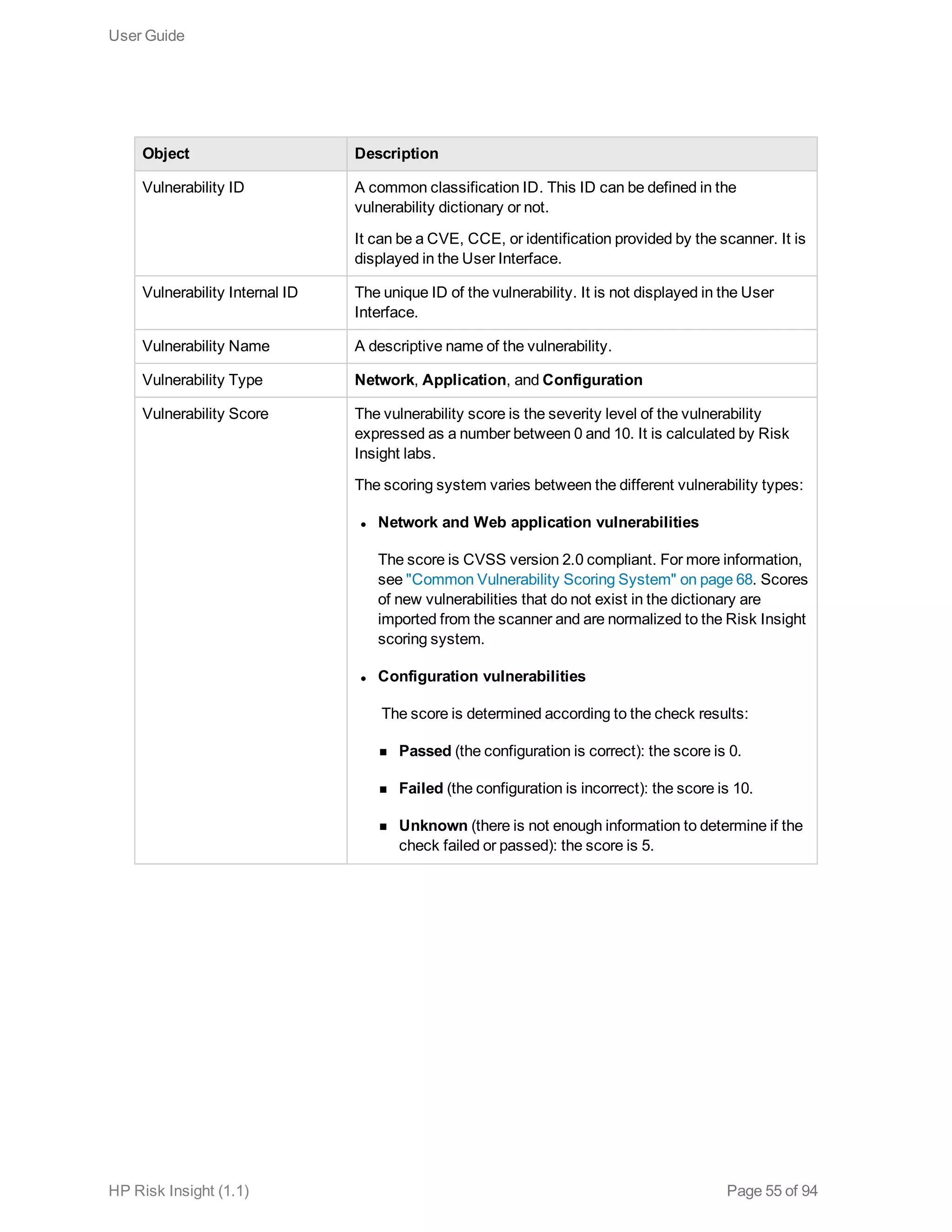
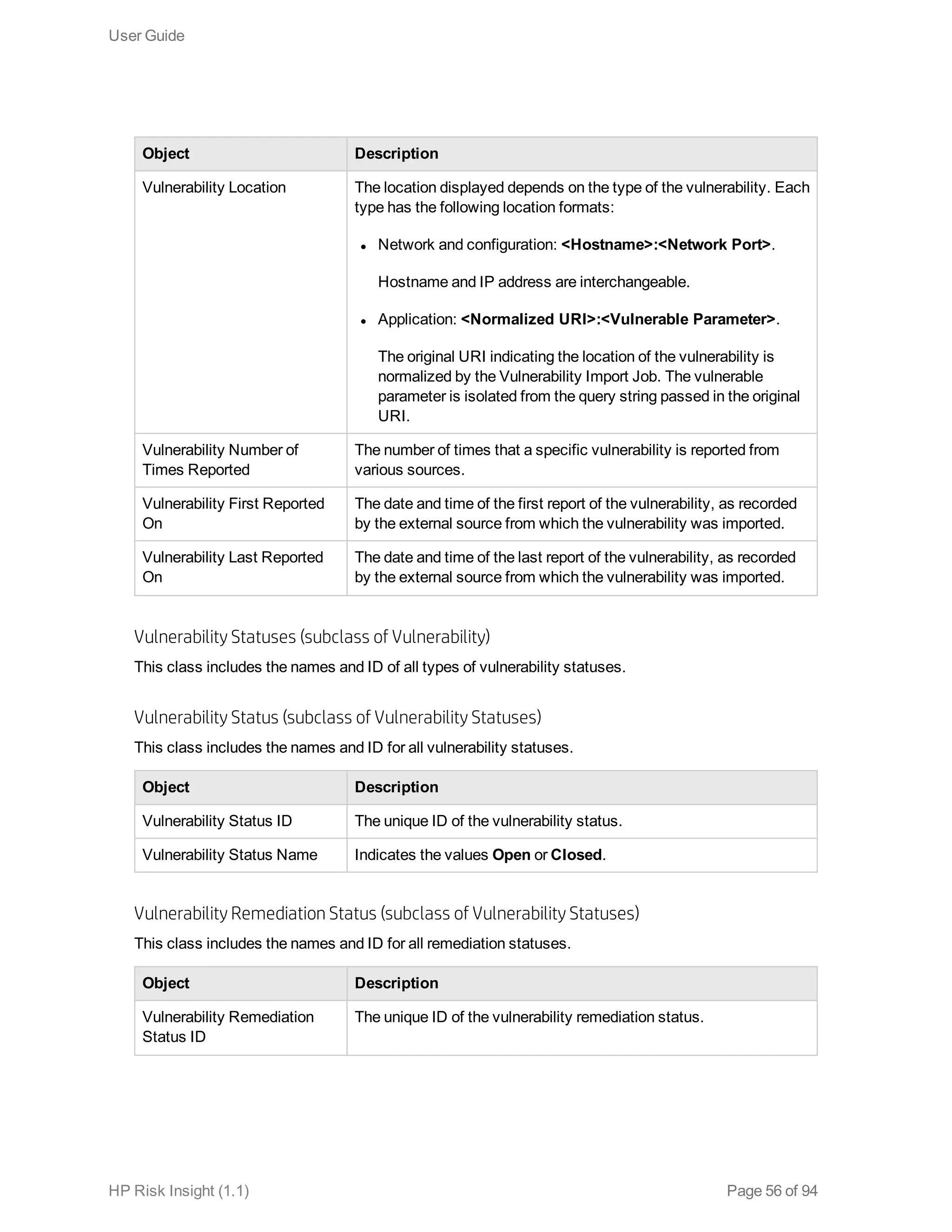
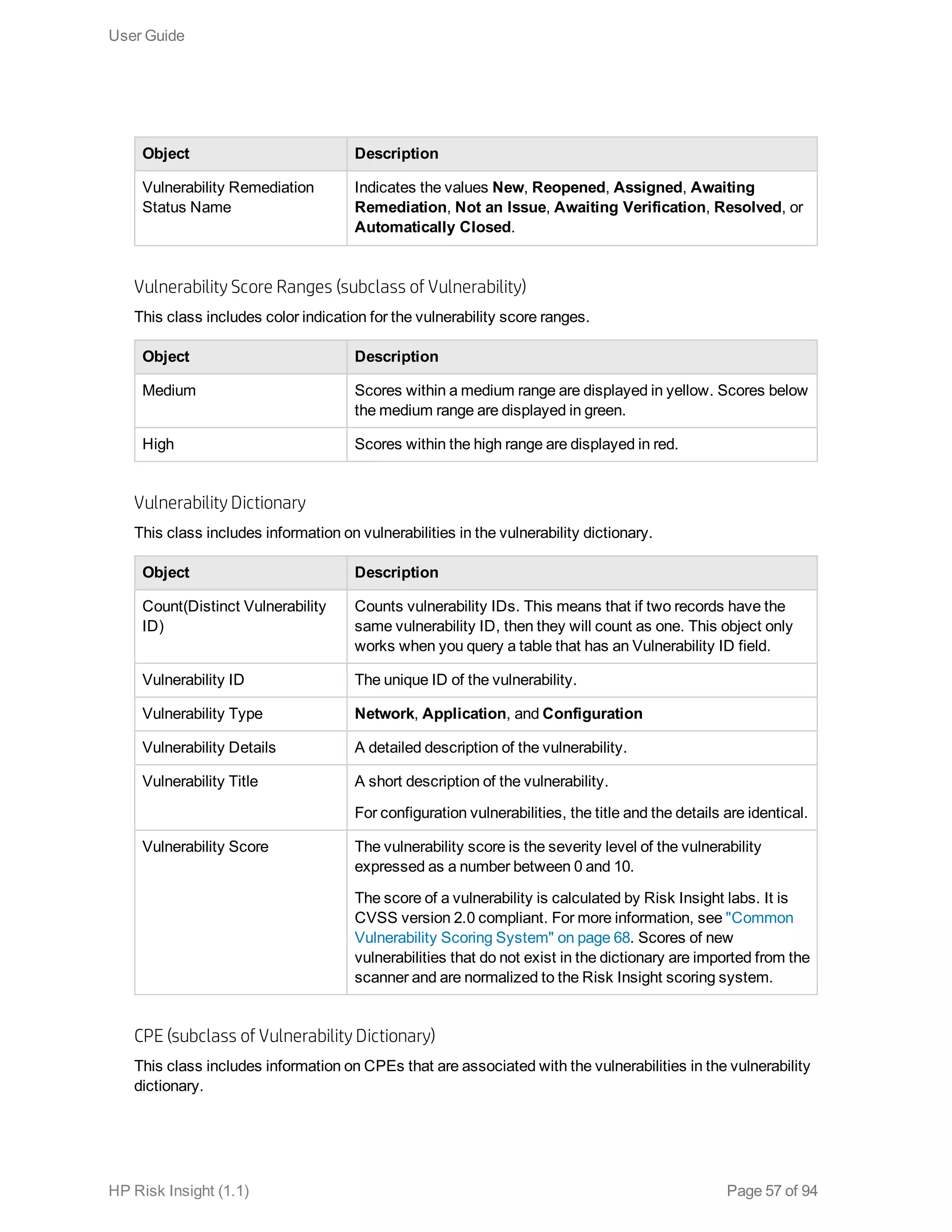
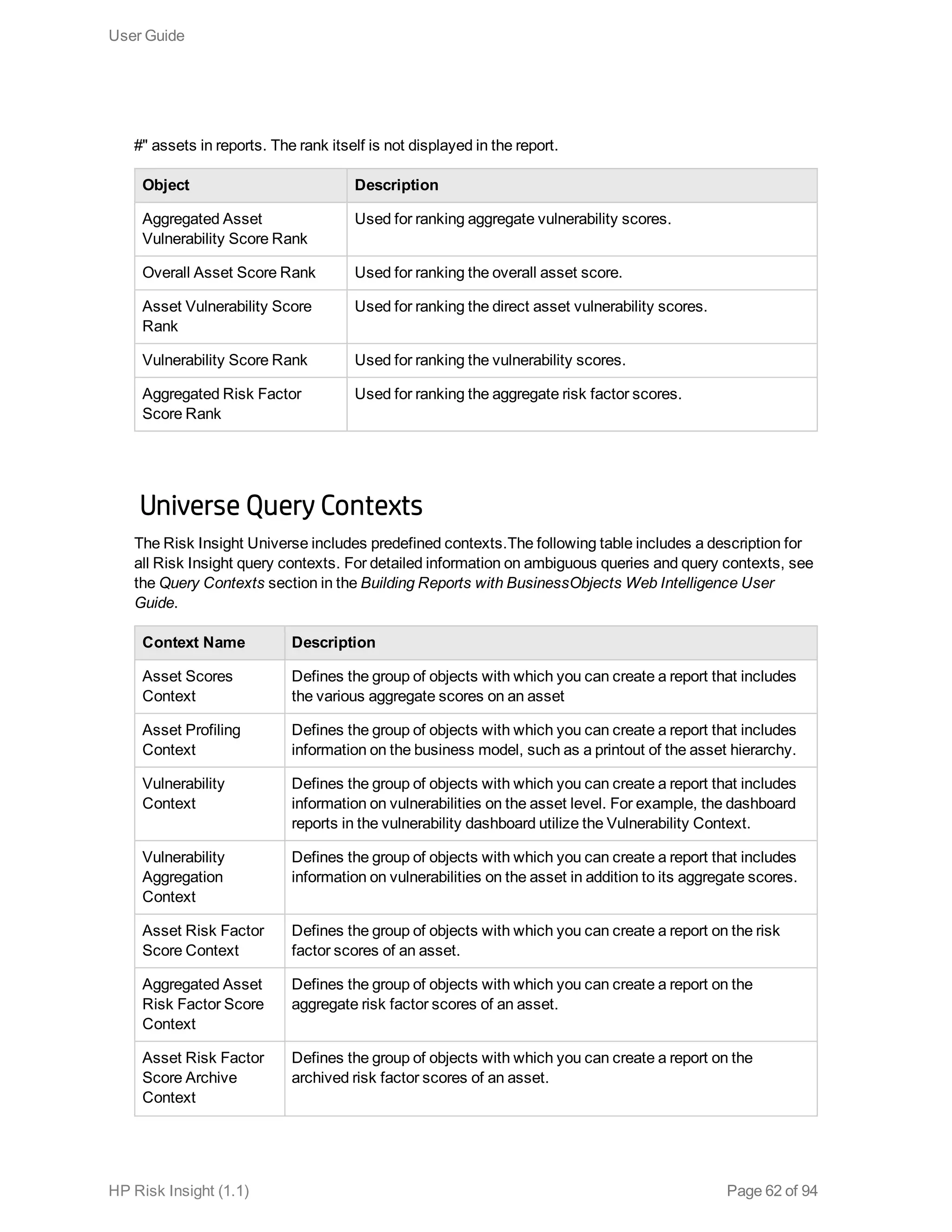
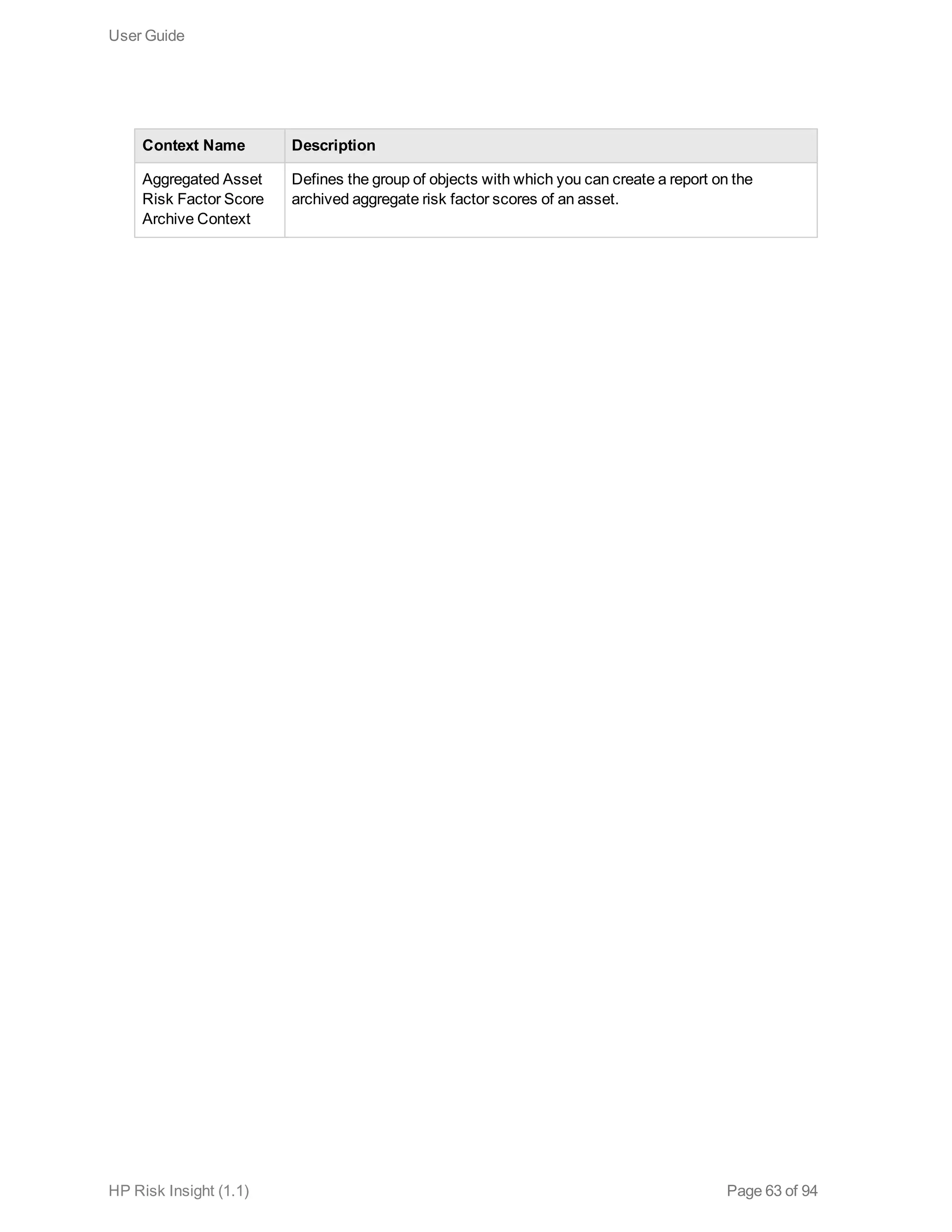
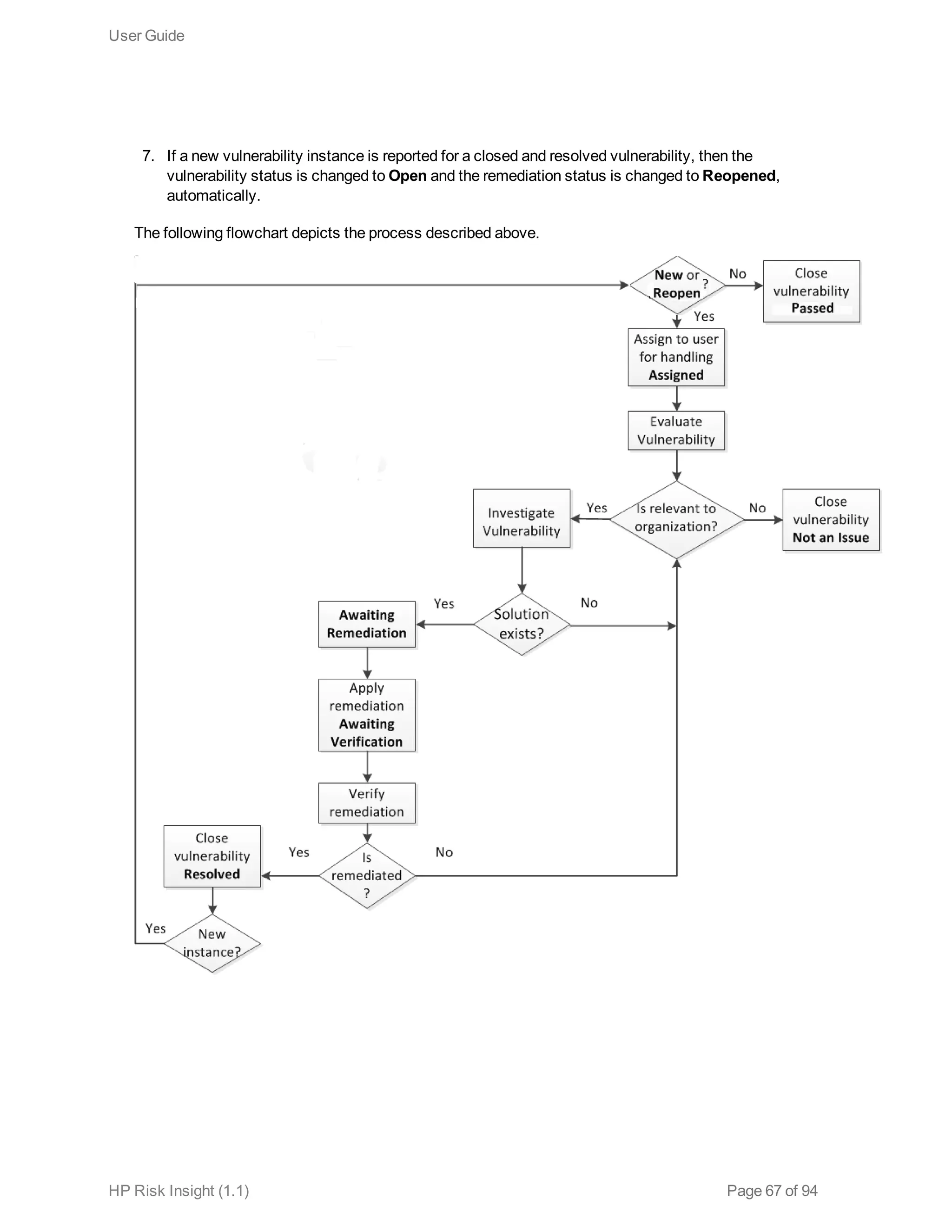
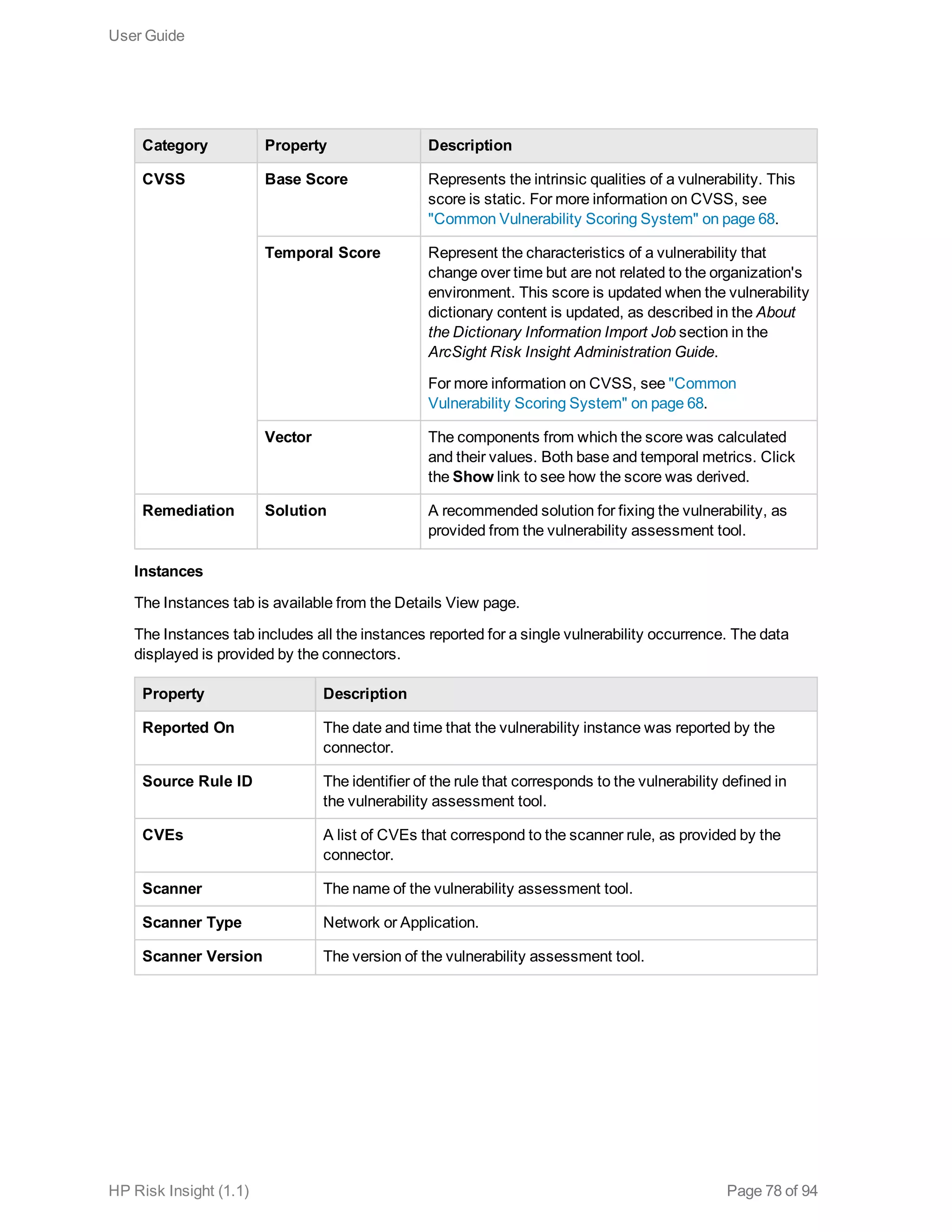
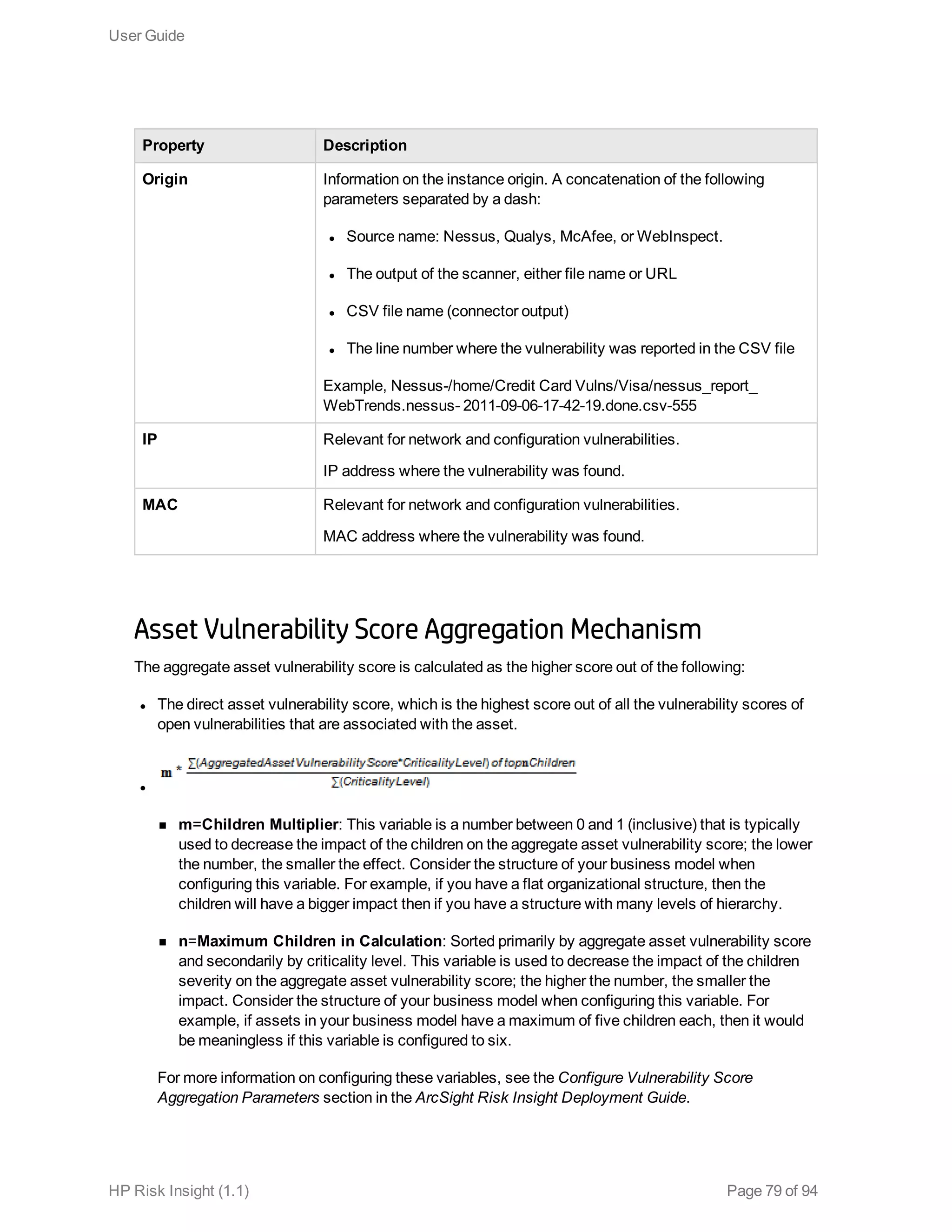
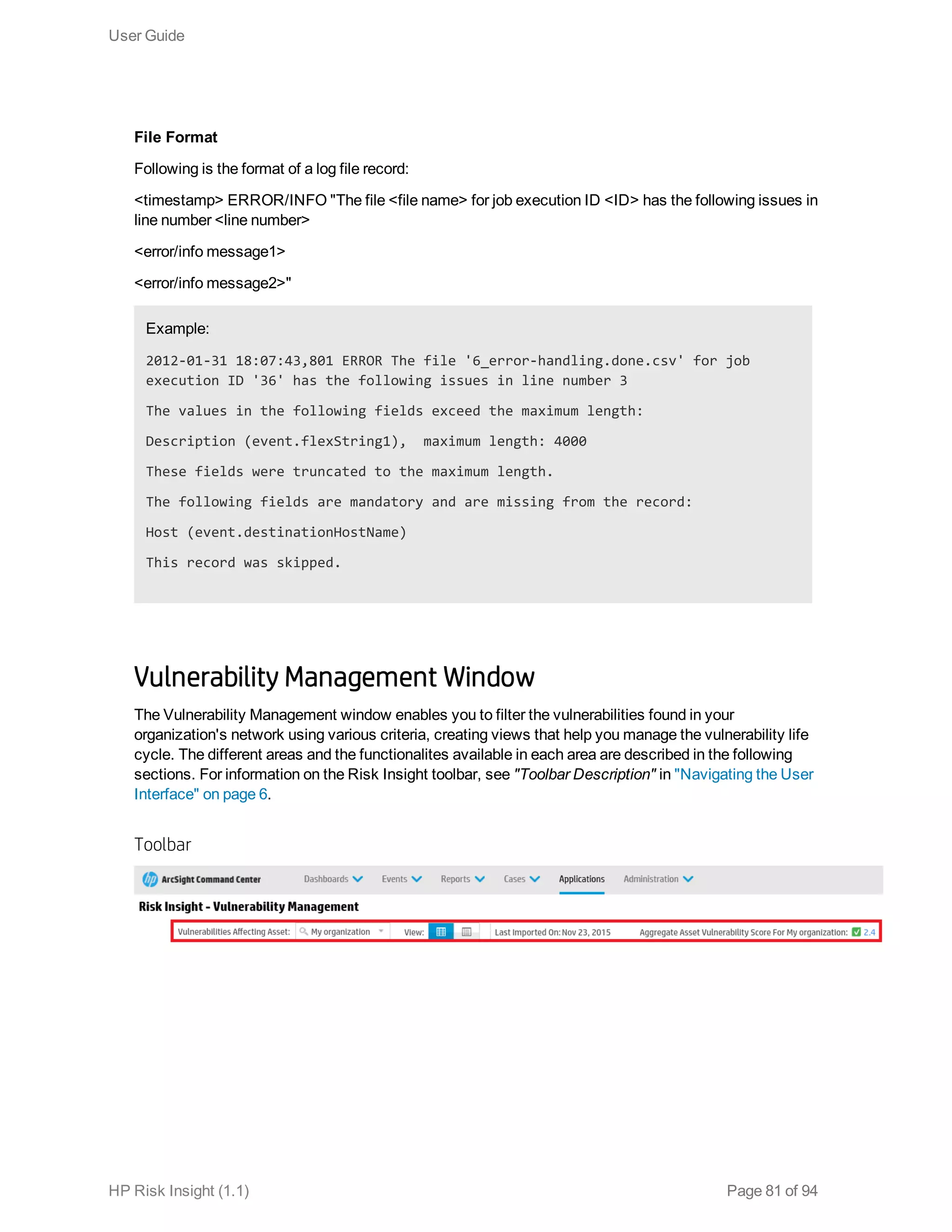
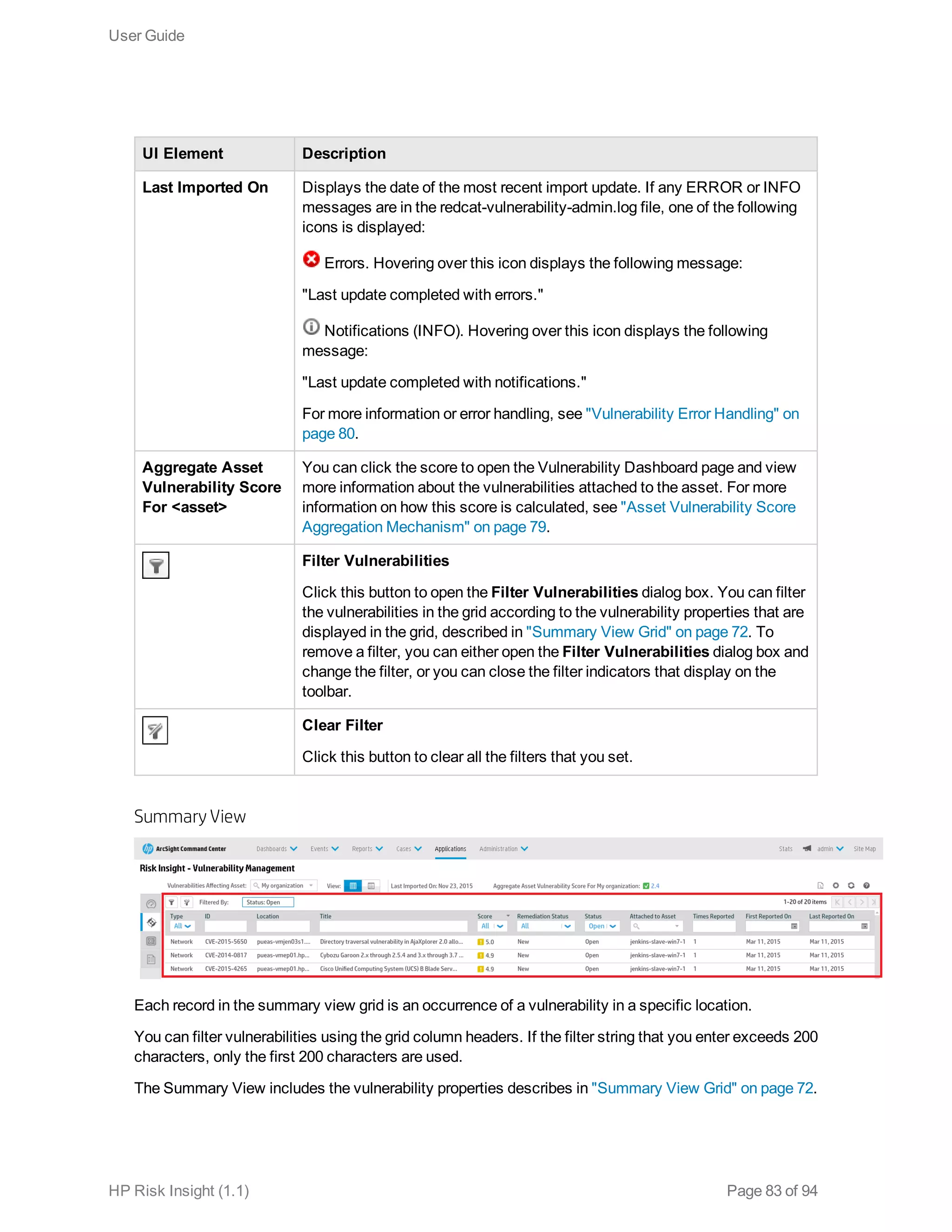
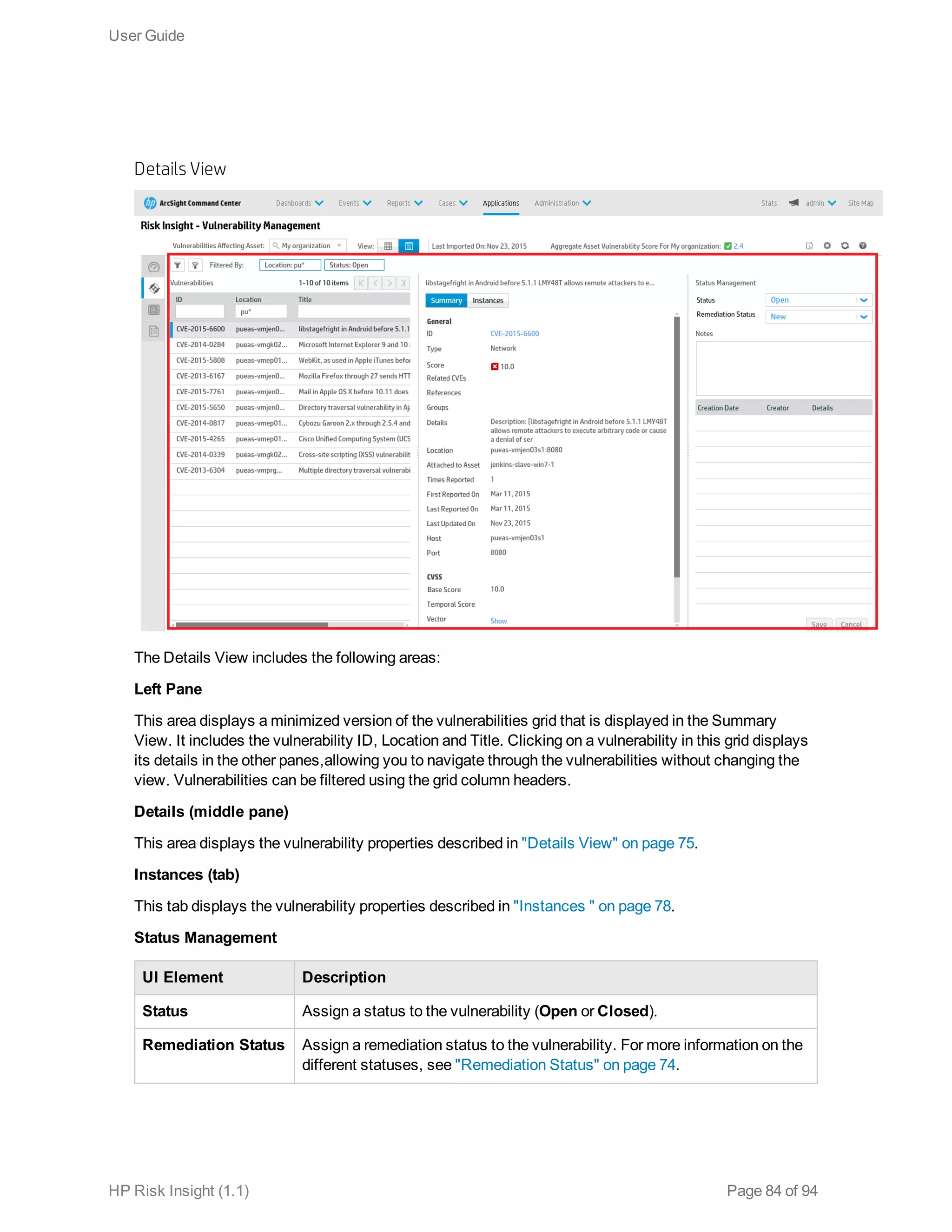
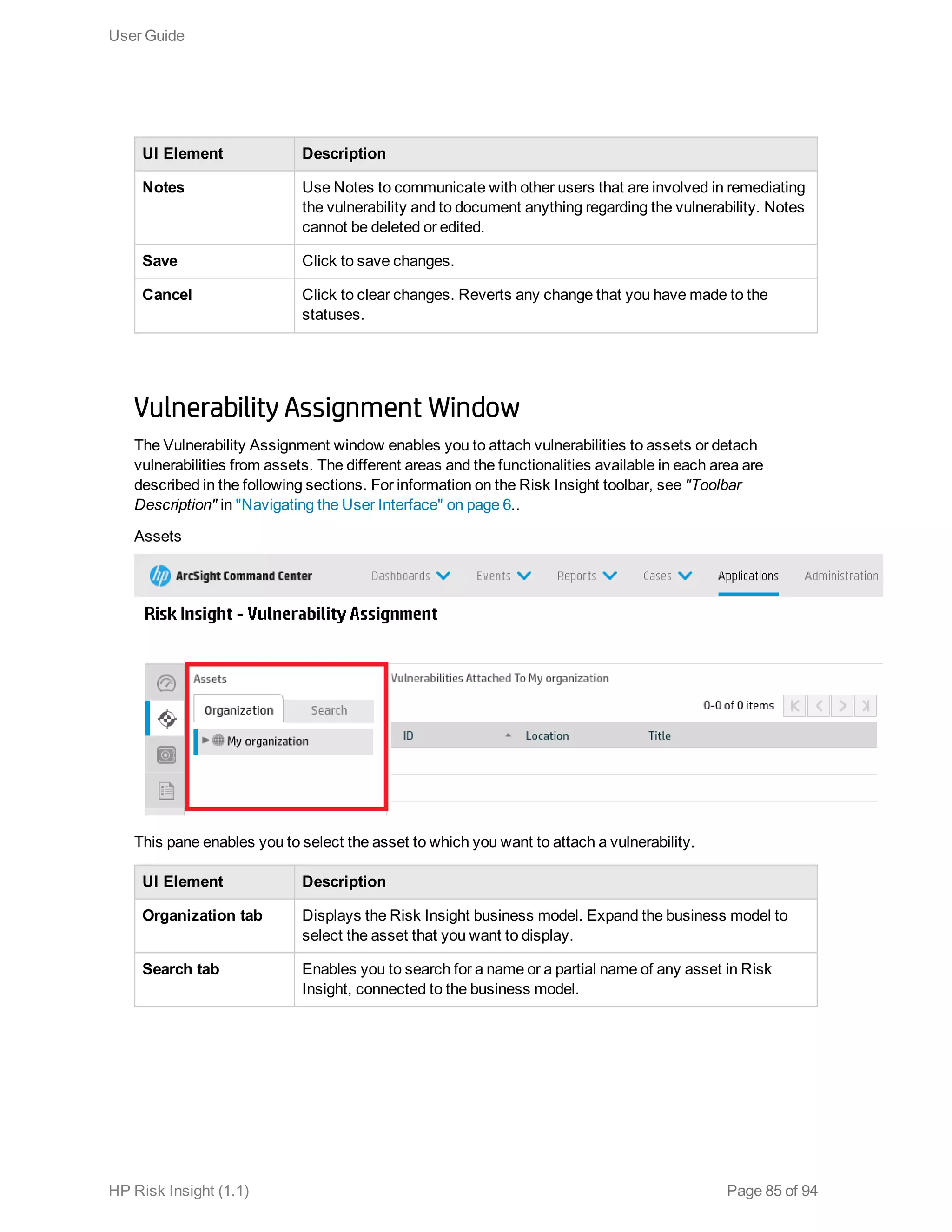
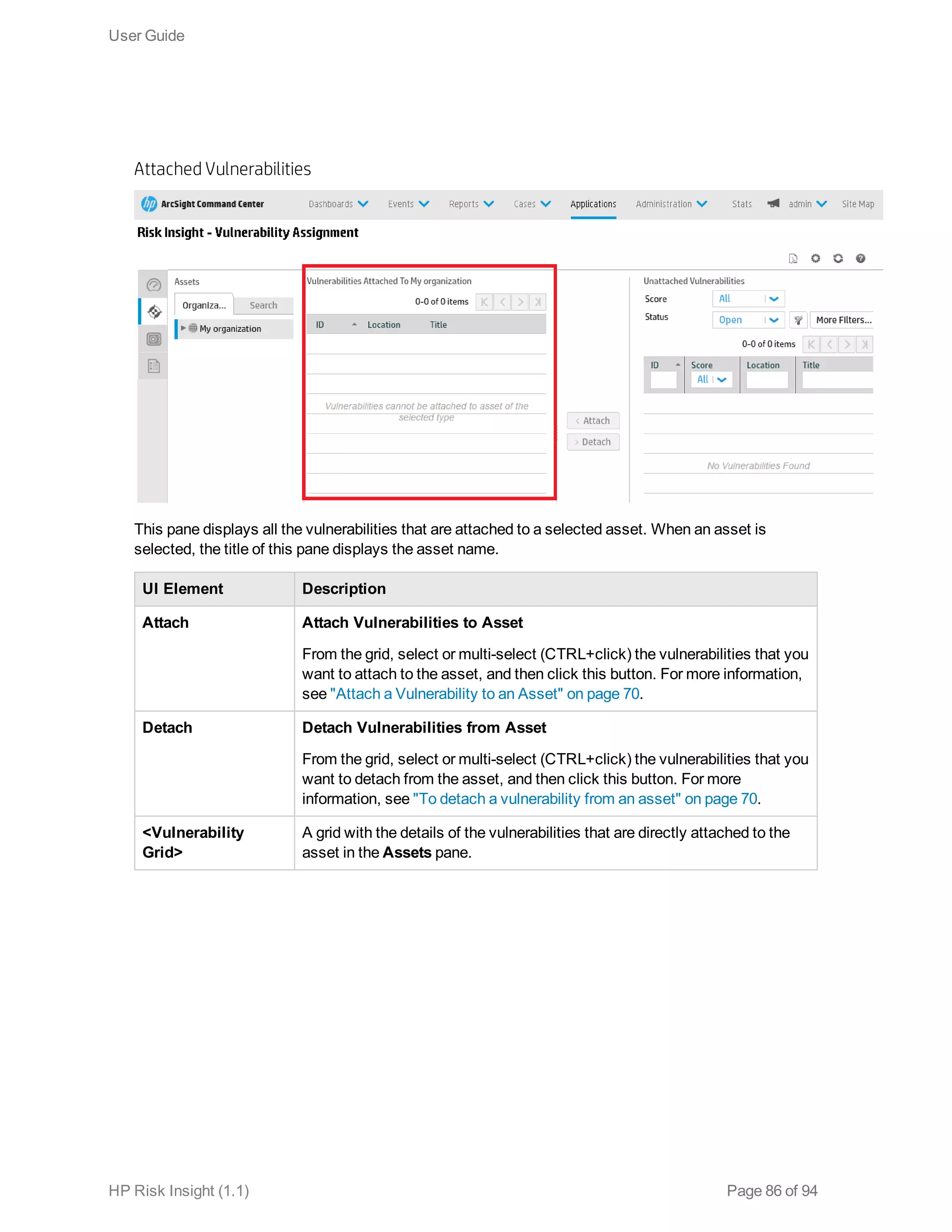
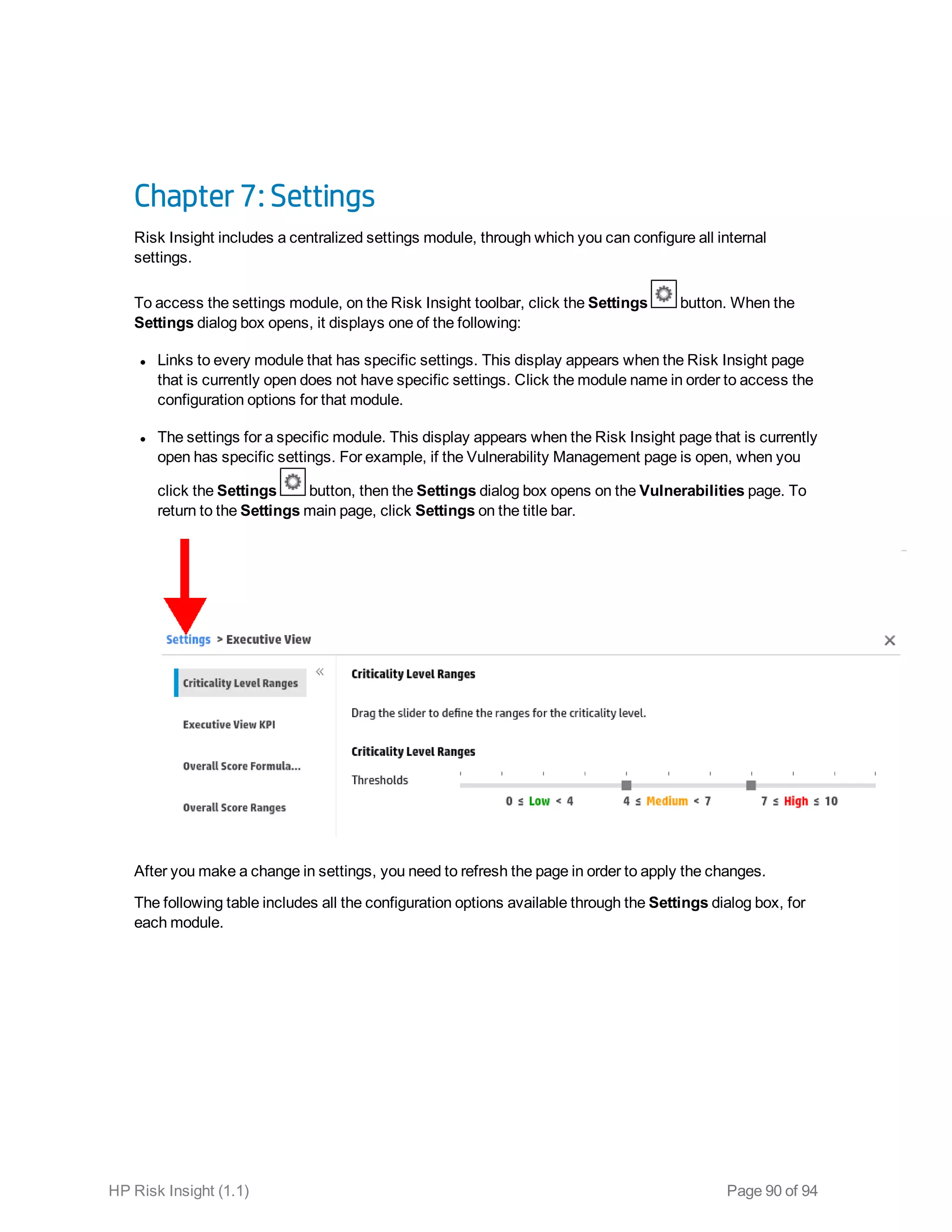
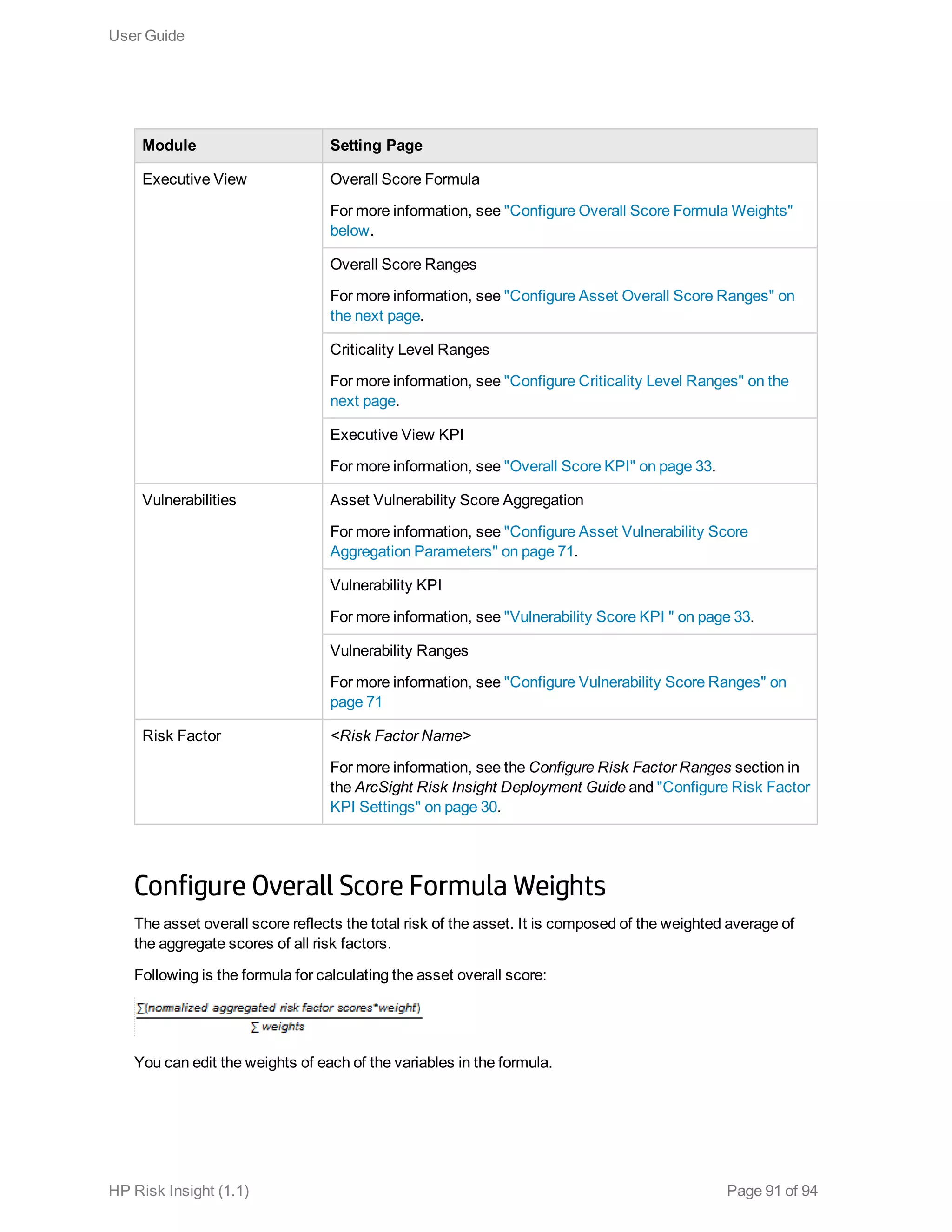
This document is the user guide for HP ArcSight Risk Insight version 1.1. It provides information on navigating the user interface and describes the key modules for asset profiling, risk factors, key performance indicators, dashboards and reports, vulnerability management, and settings configuration. The guide includes chapters on building a business model to represent an organization's assets in a hierarchical structure, defining risk factors and KPIs, using executive dashboards to analyze security risks, and managing vulnerabilities.