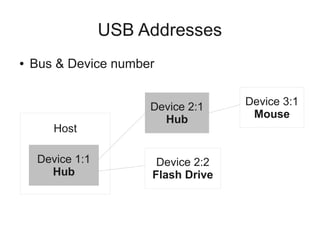
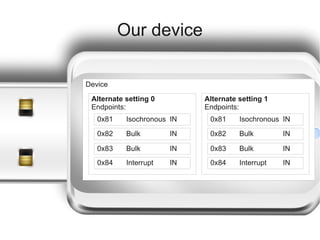
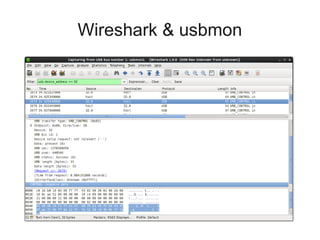
The document discusses reverse engineering a Linux driver for an unknown USB video capture device. The key steps taken were:
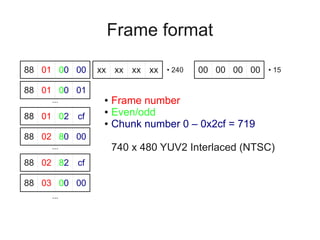
1) Capturing traffic from the device when used in Windows to understand the frame format and endpoints. This revealed the device provides YUV video data over isochronous endpoints.
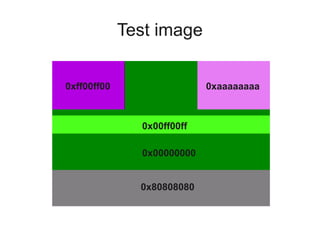
2) Developing a userspace program using libusb to replay the USB traffic and extract test image data to validate the frame format.
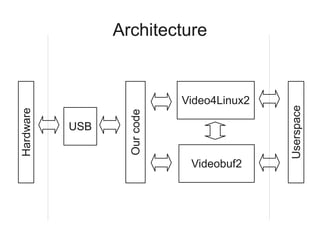
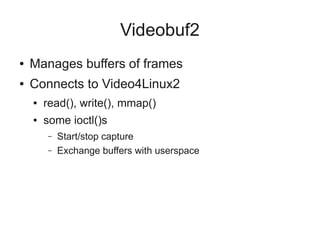
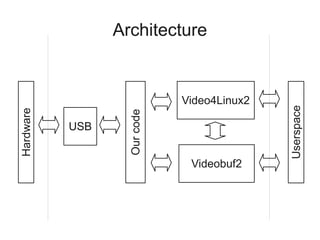
3) Creating a Linux kernel driver that interfaces with the USB and Video4Linux2 frameworks to provide the captured video as a video device to userspace programs through Videobuf2 buffers.