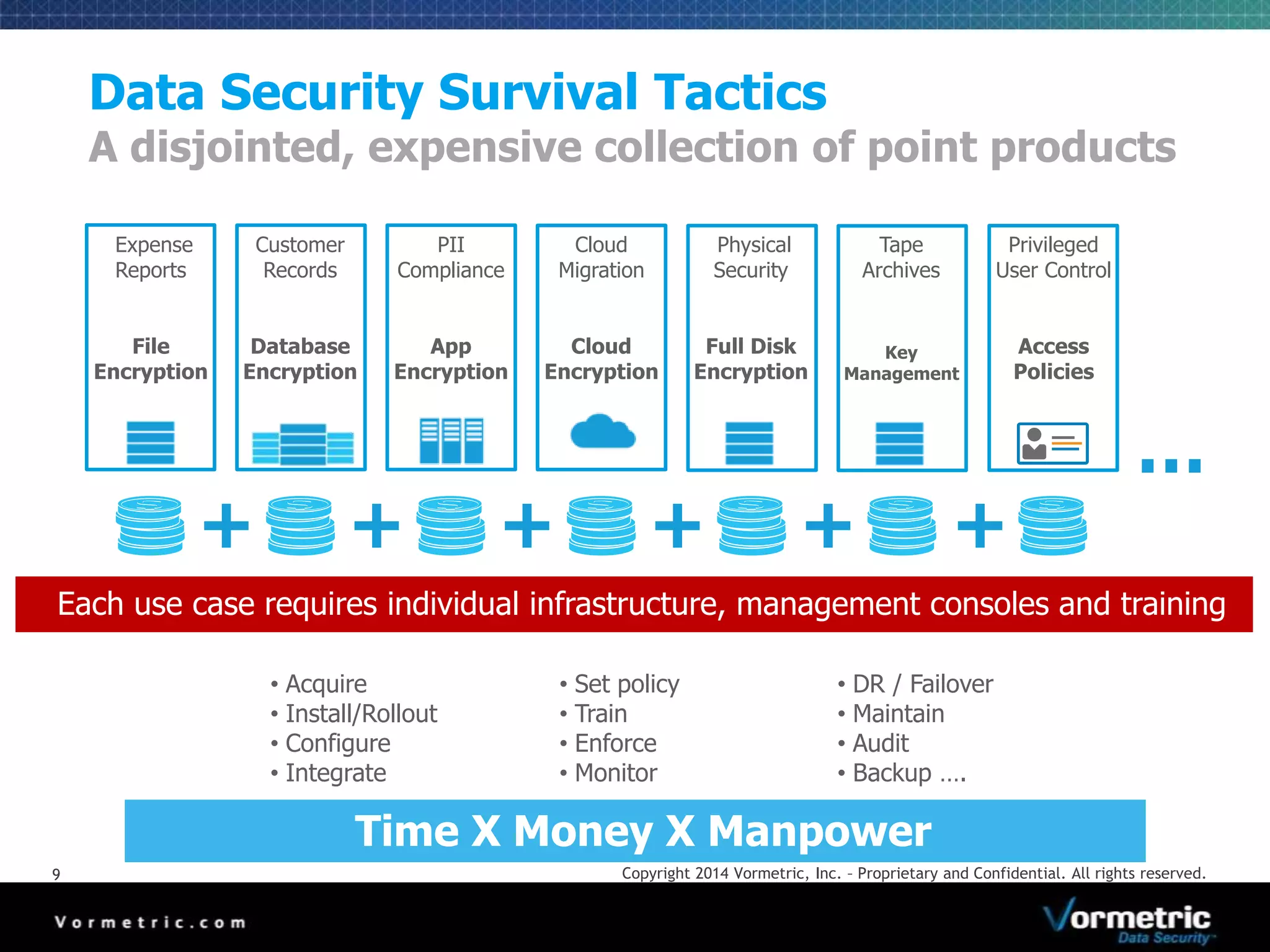
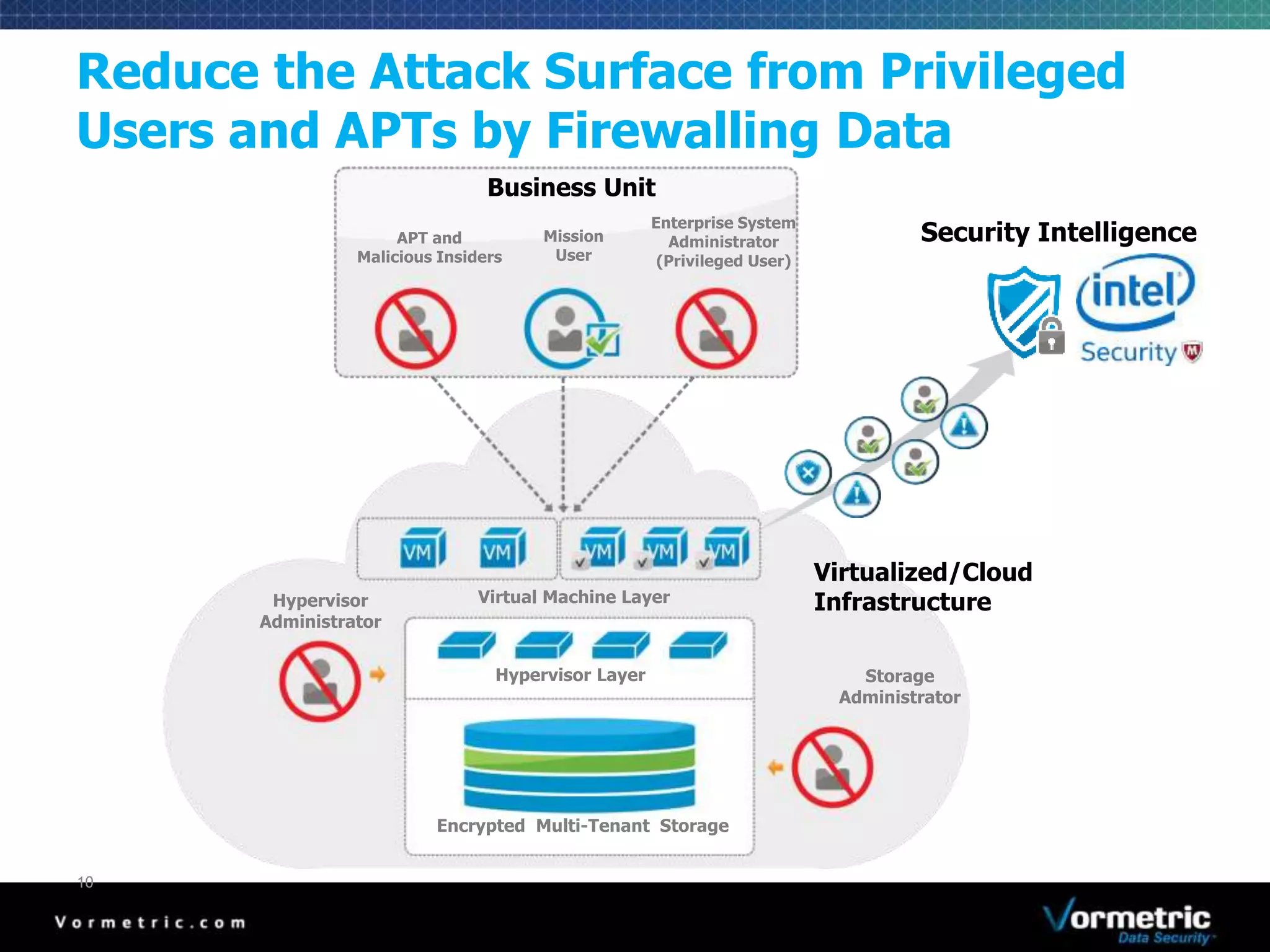
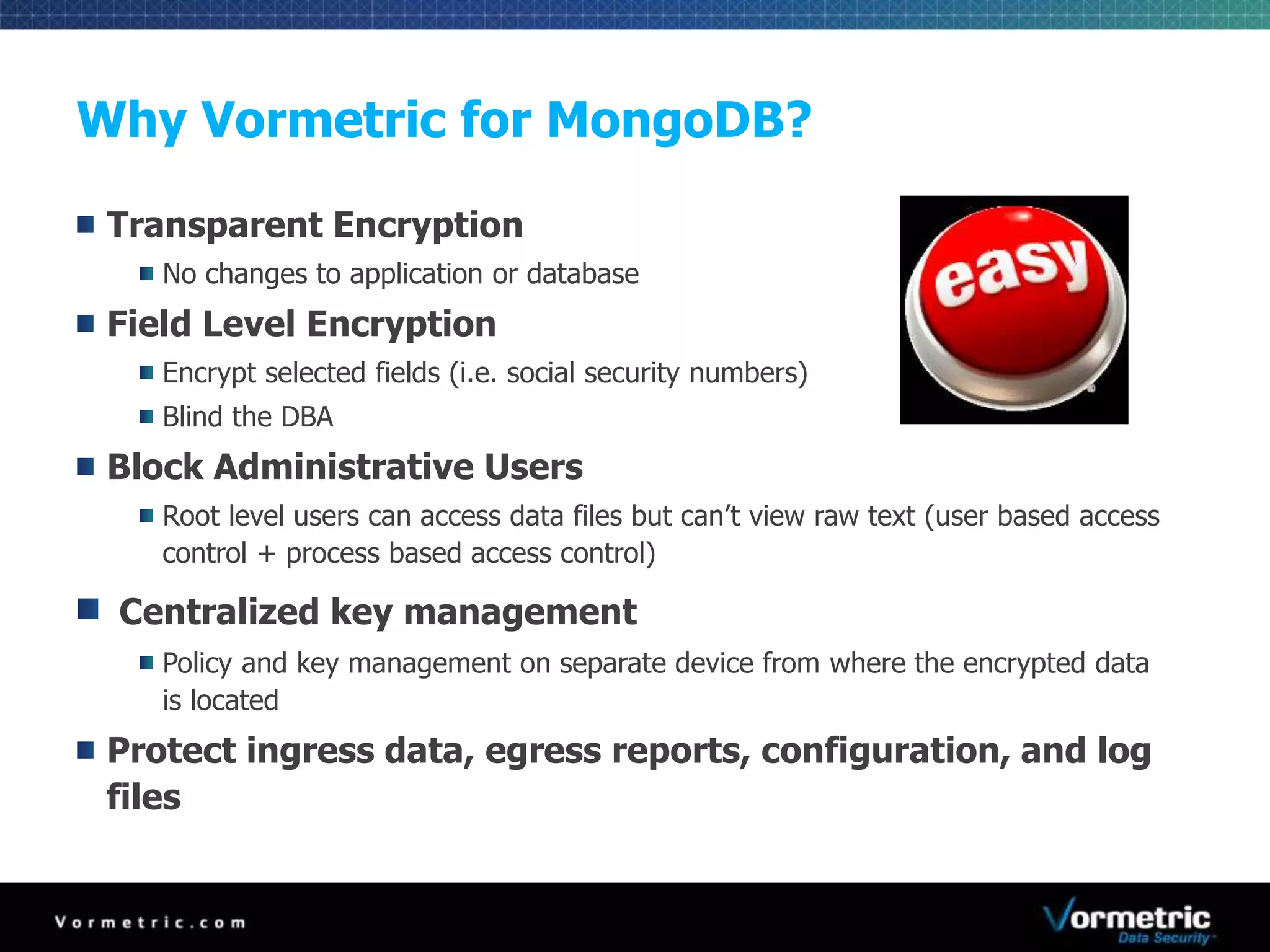
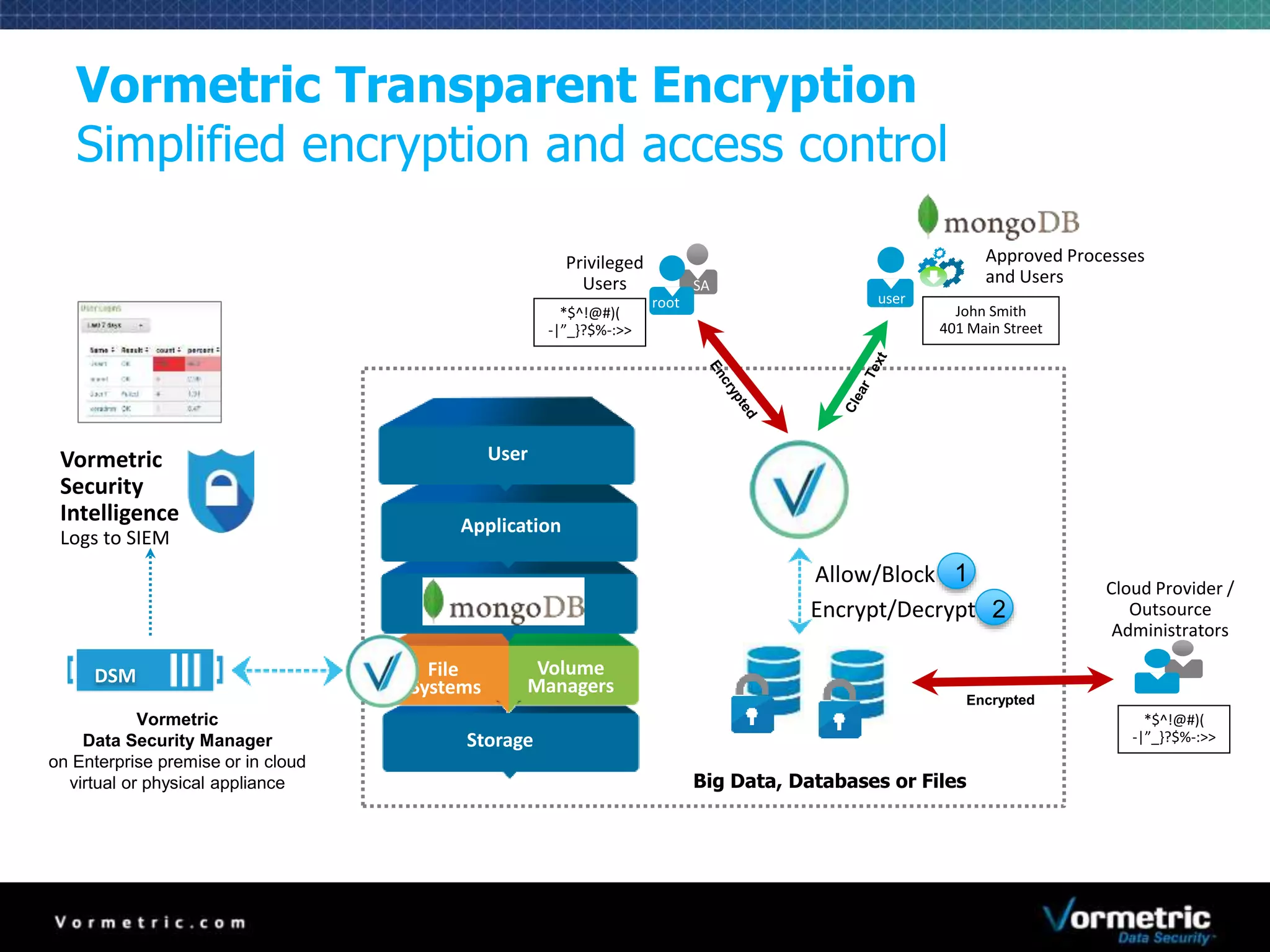
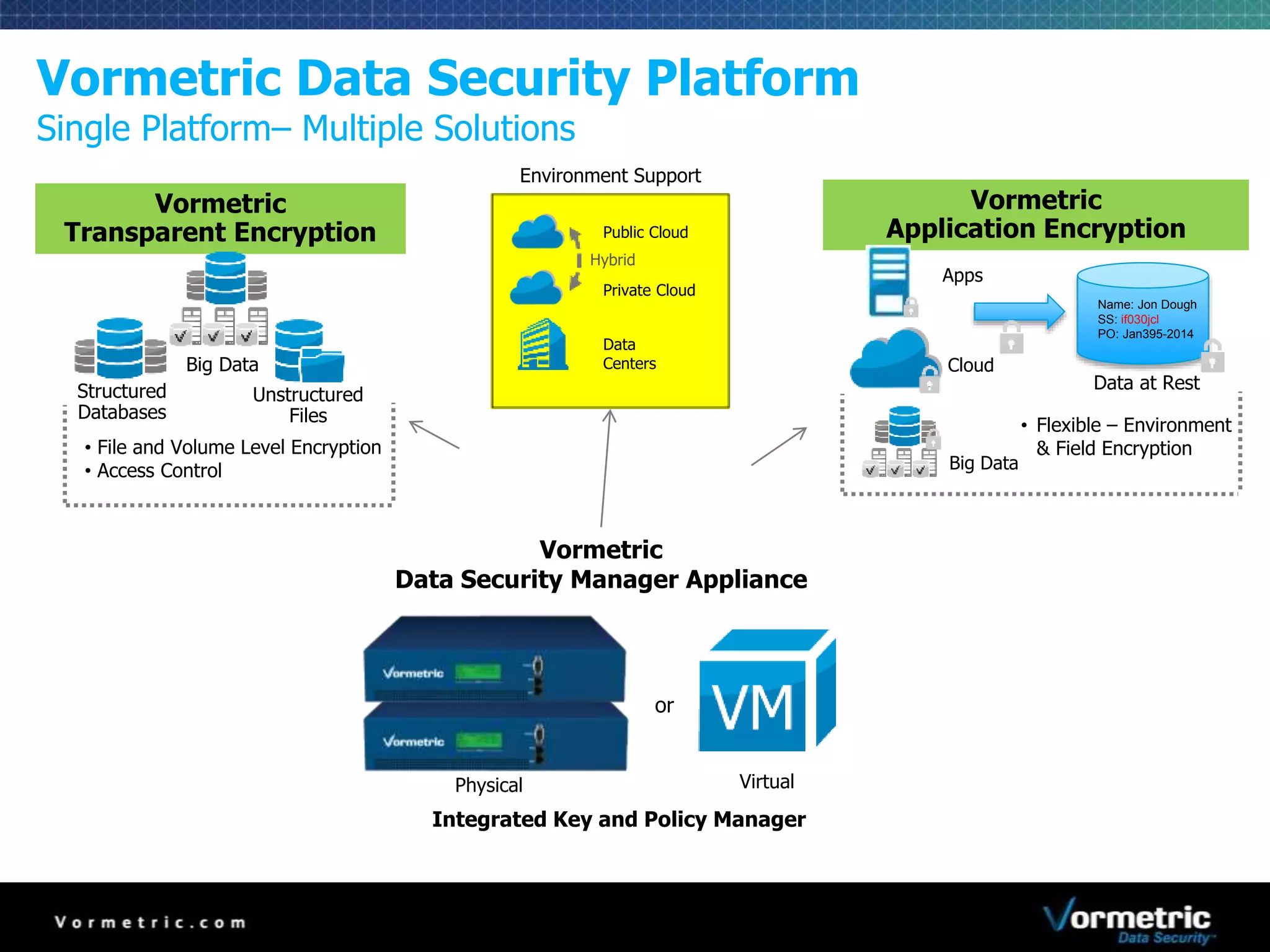
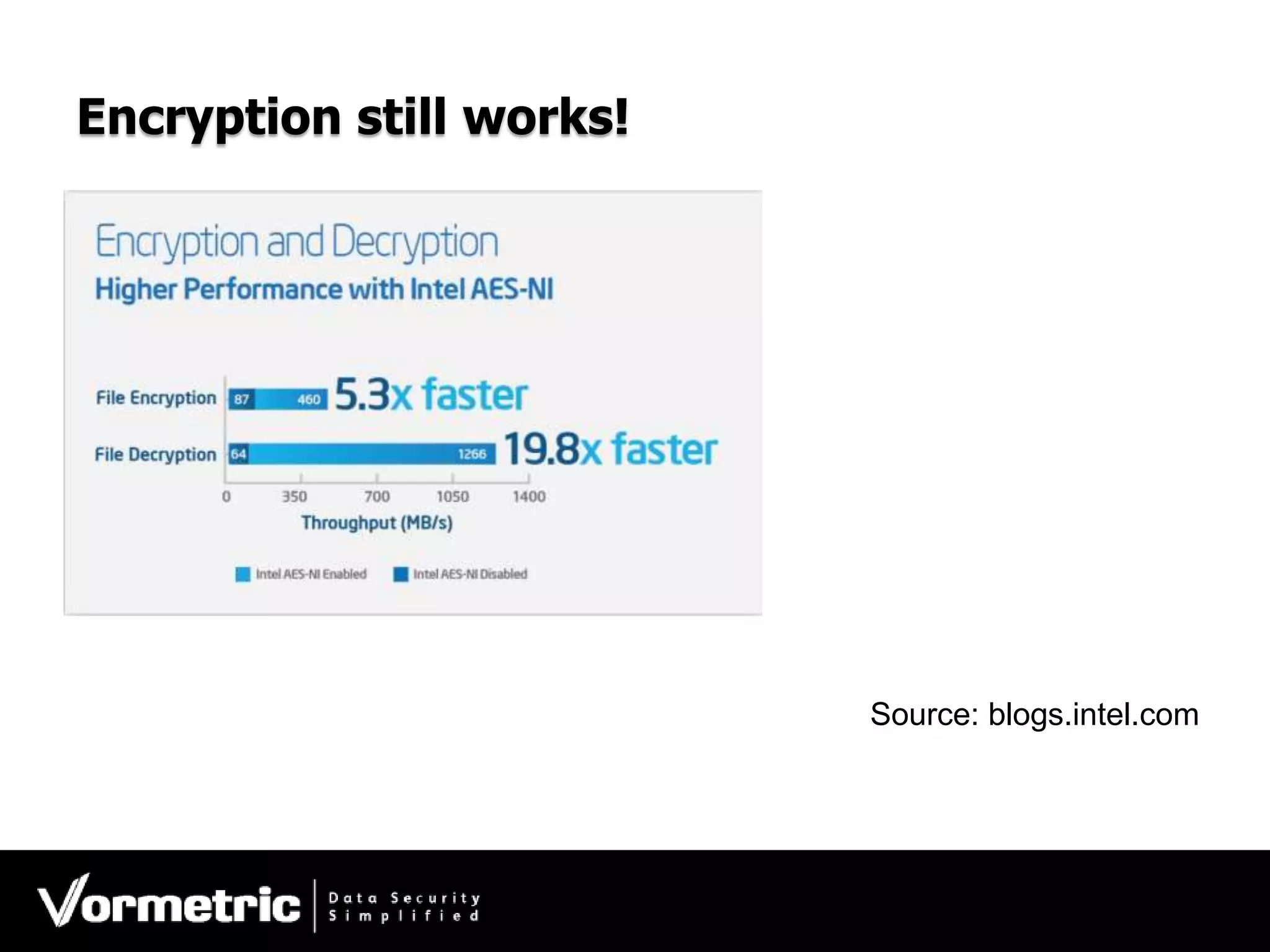
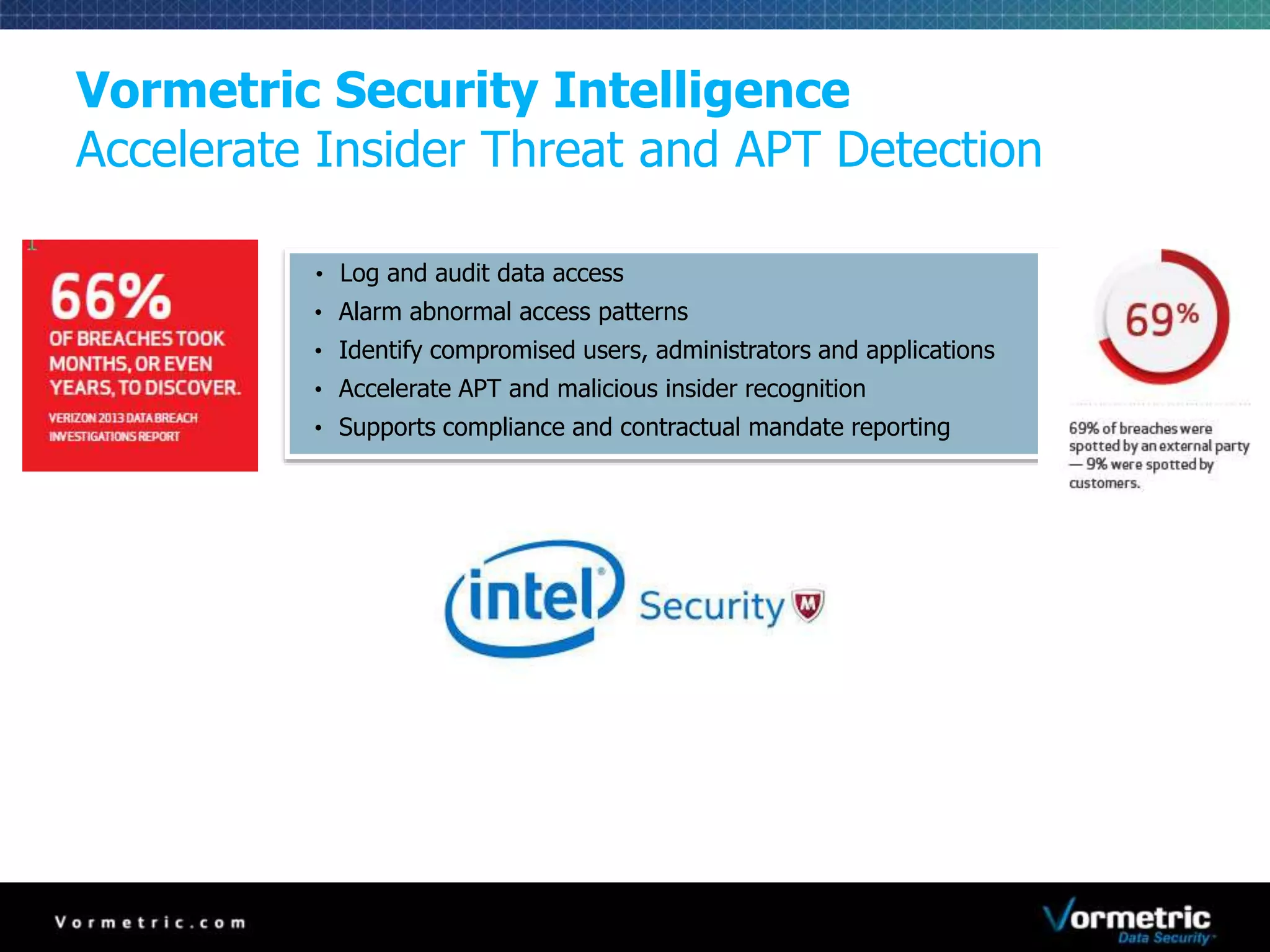
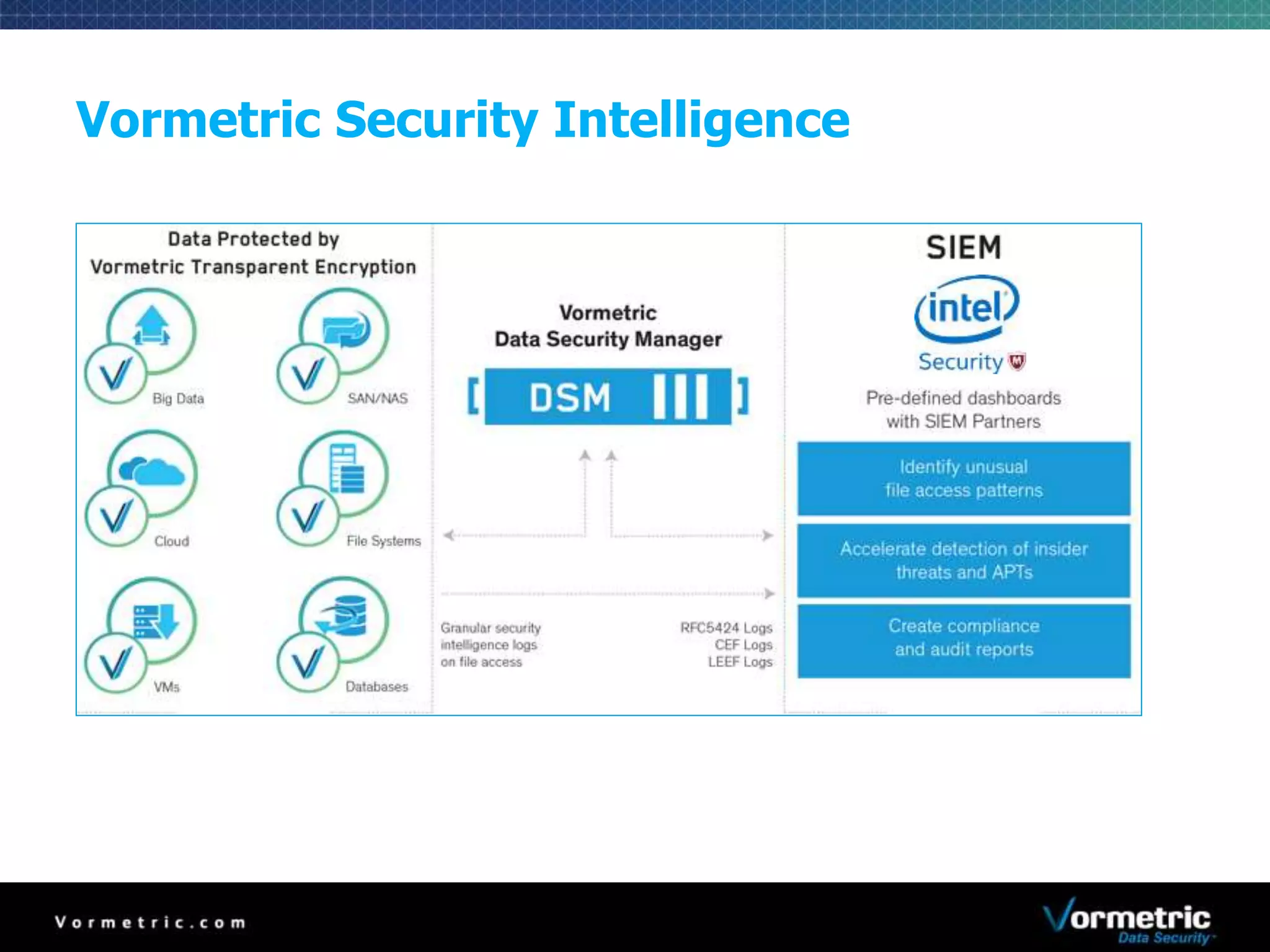
The document discusses protecting databases from insider threats using MongoDB encryption. It describes how insider threats are on the rise and how privileged users can bypass traditional security to access sensitive data. The solution presented is using Vormetric transparent encryption to encrypt MongoDB databases, which applies encryption and access controls without changes to applications or the database. Key benefits include field-level encryption, blocking administrative users' access to raw data, and centralized key management on a separate device from encrypted data.