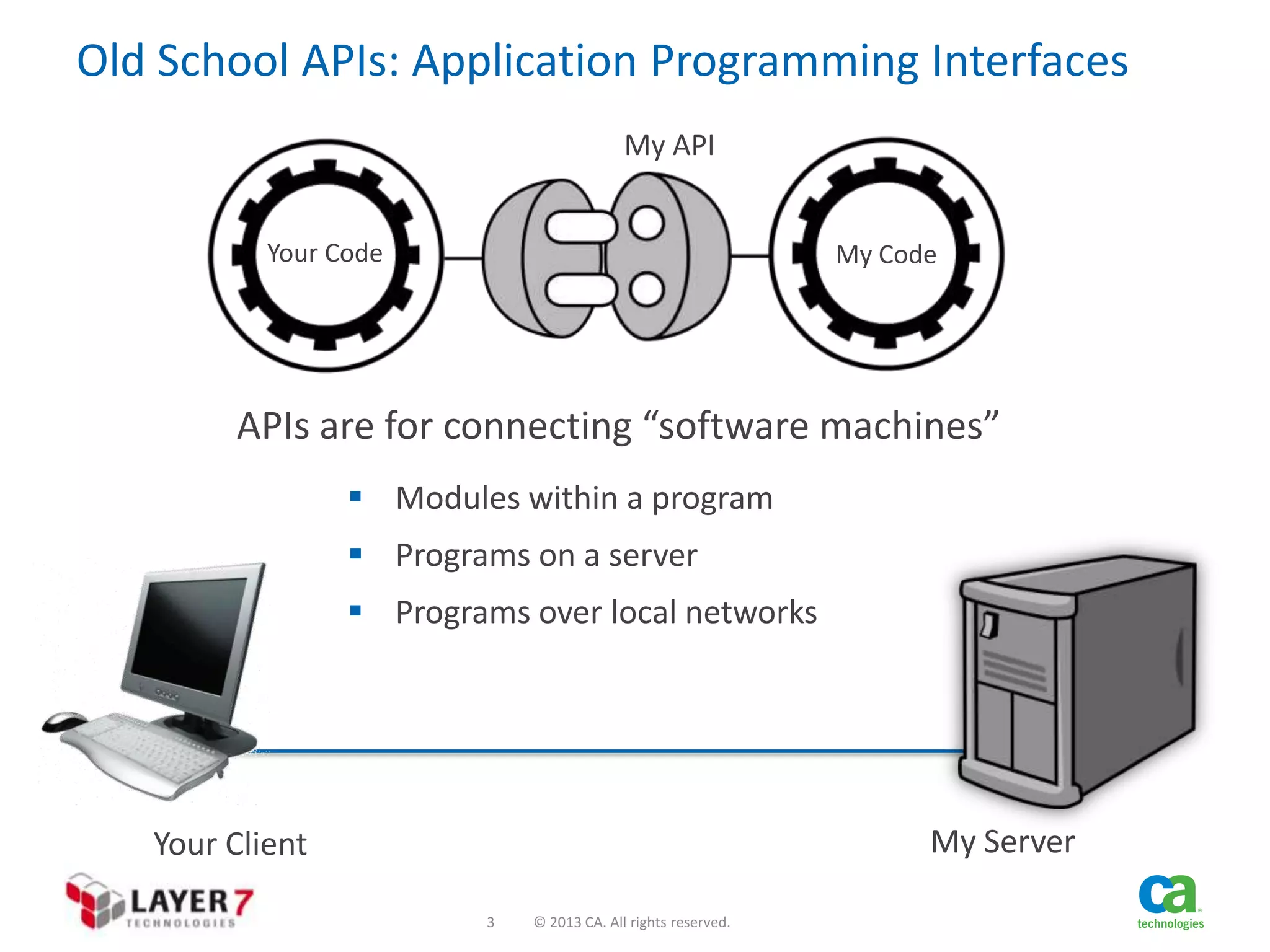
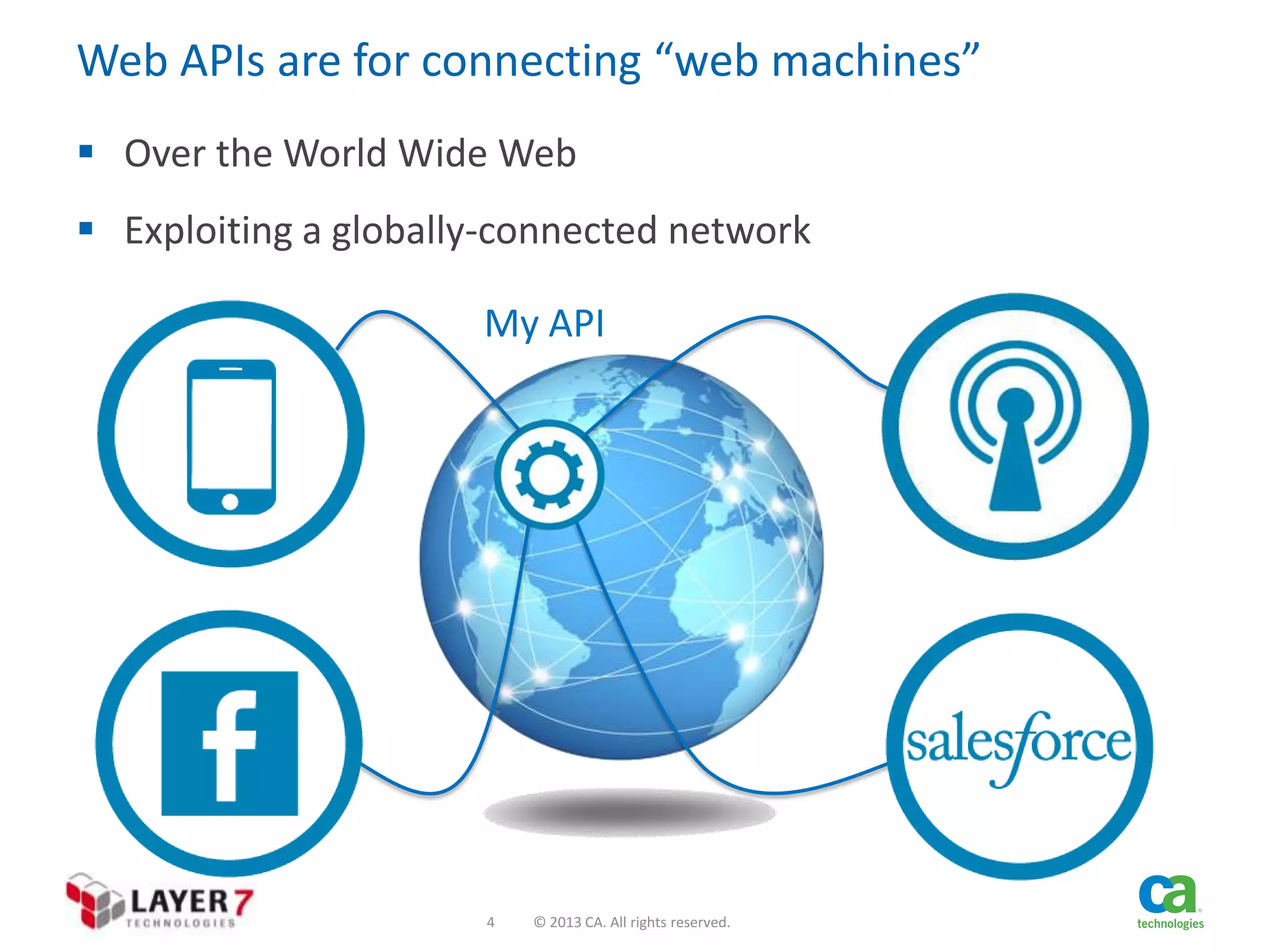
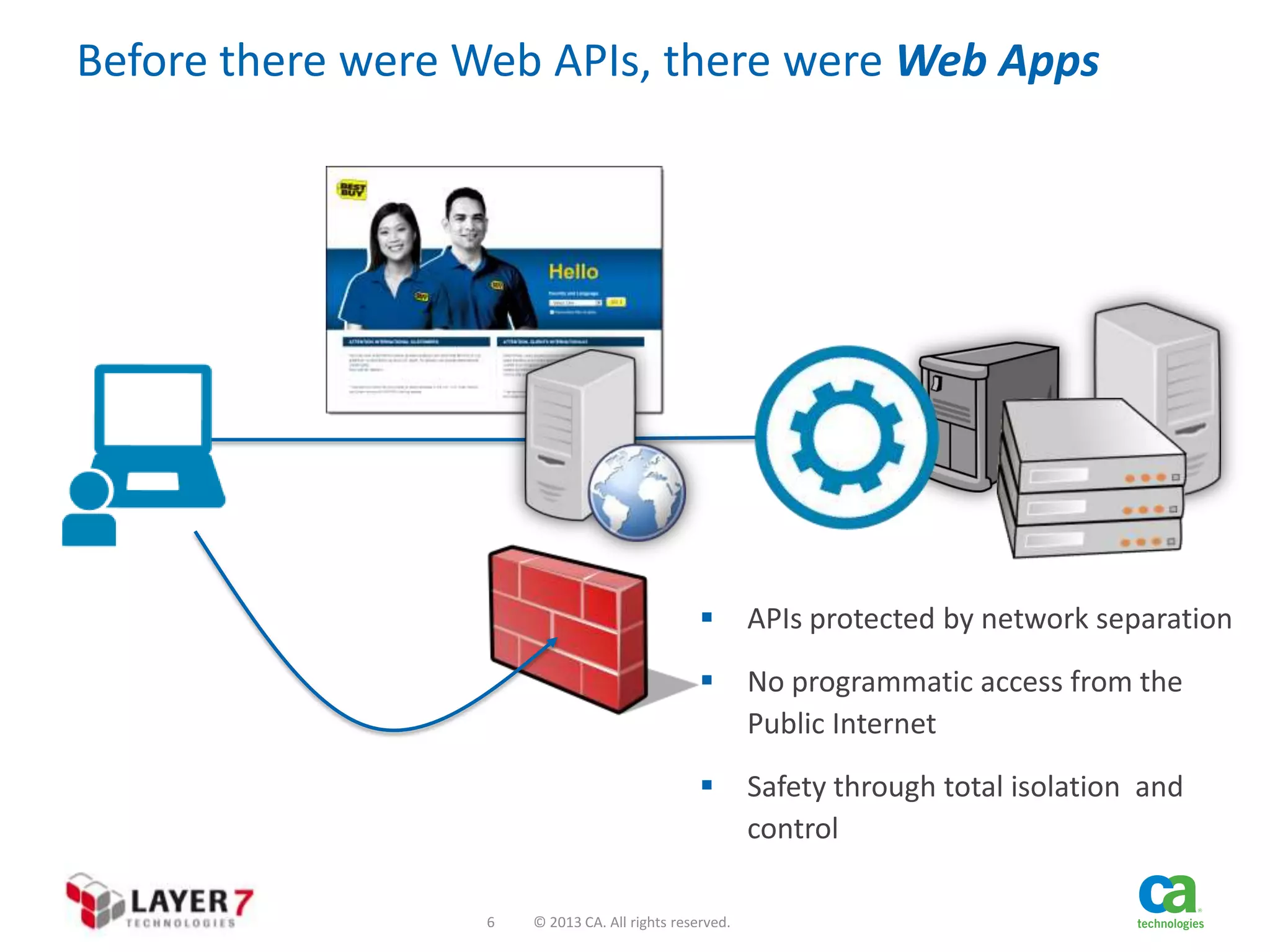
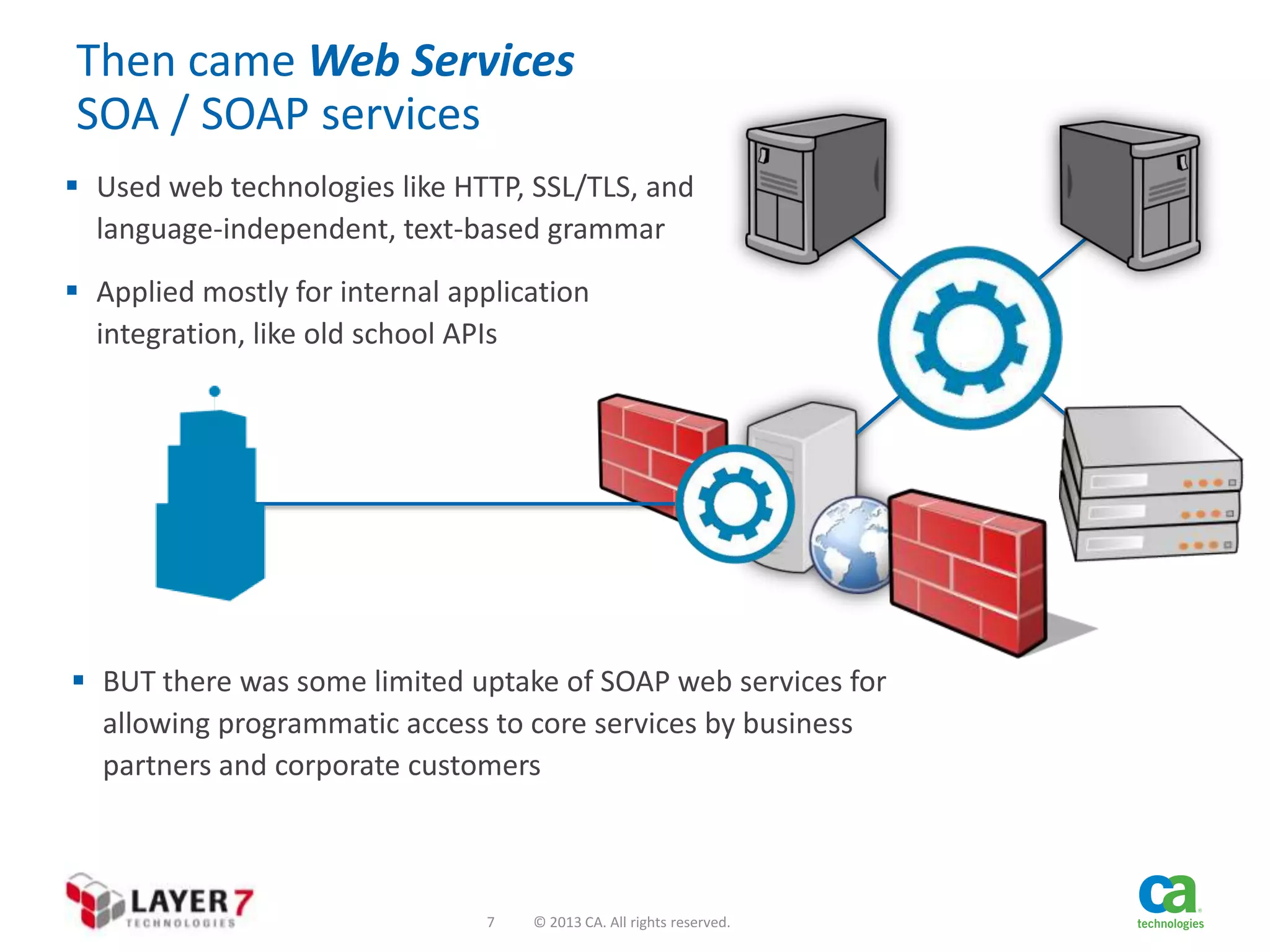
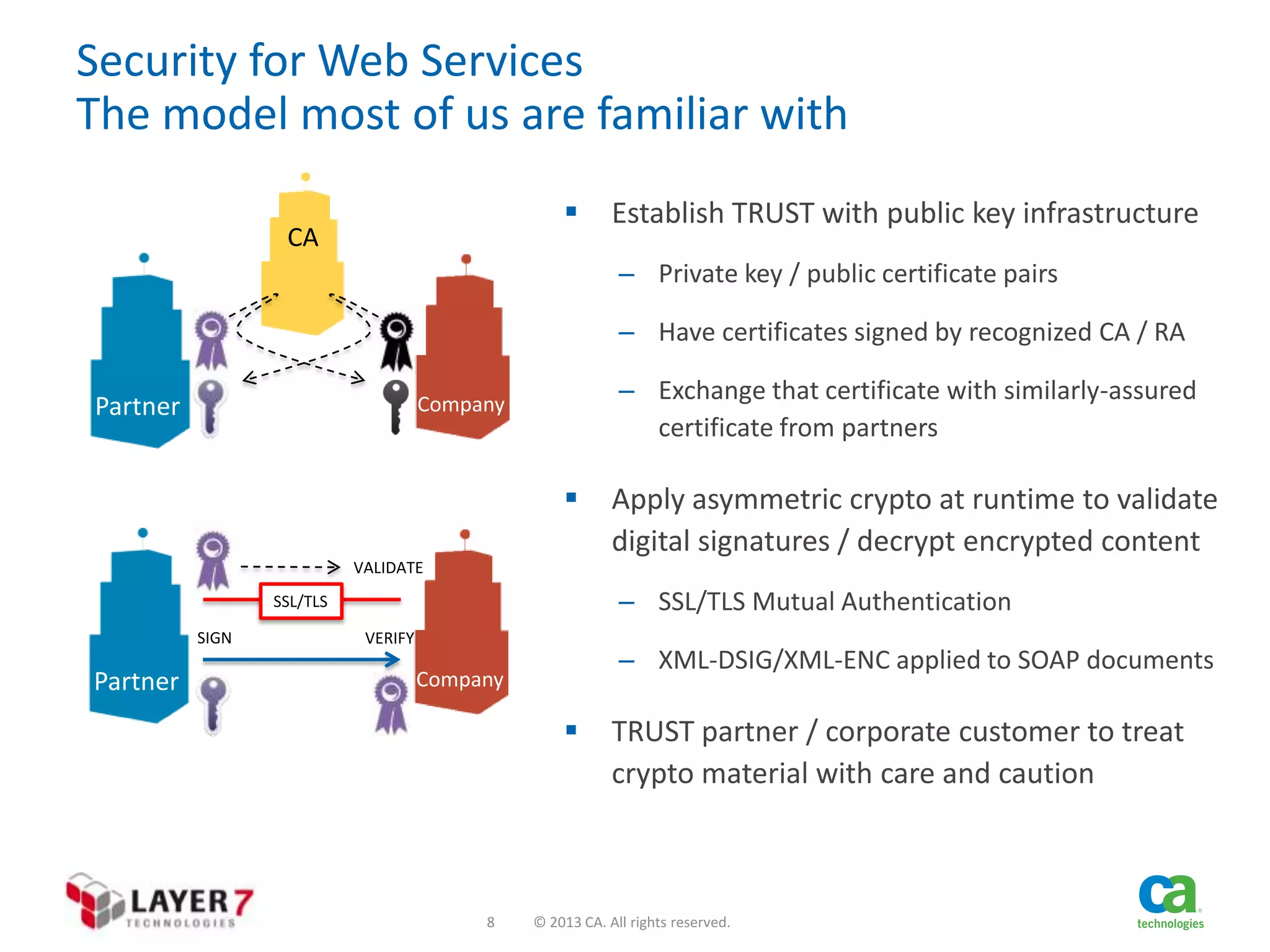
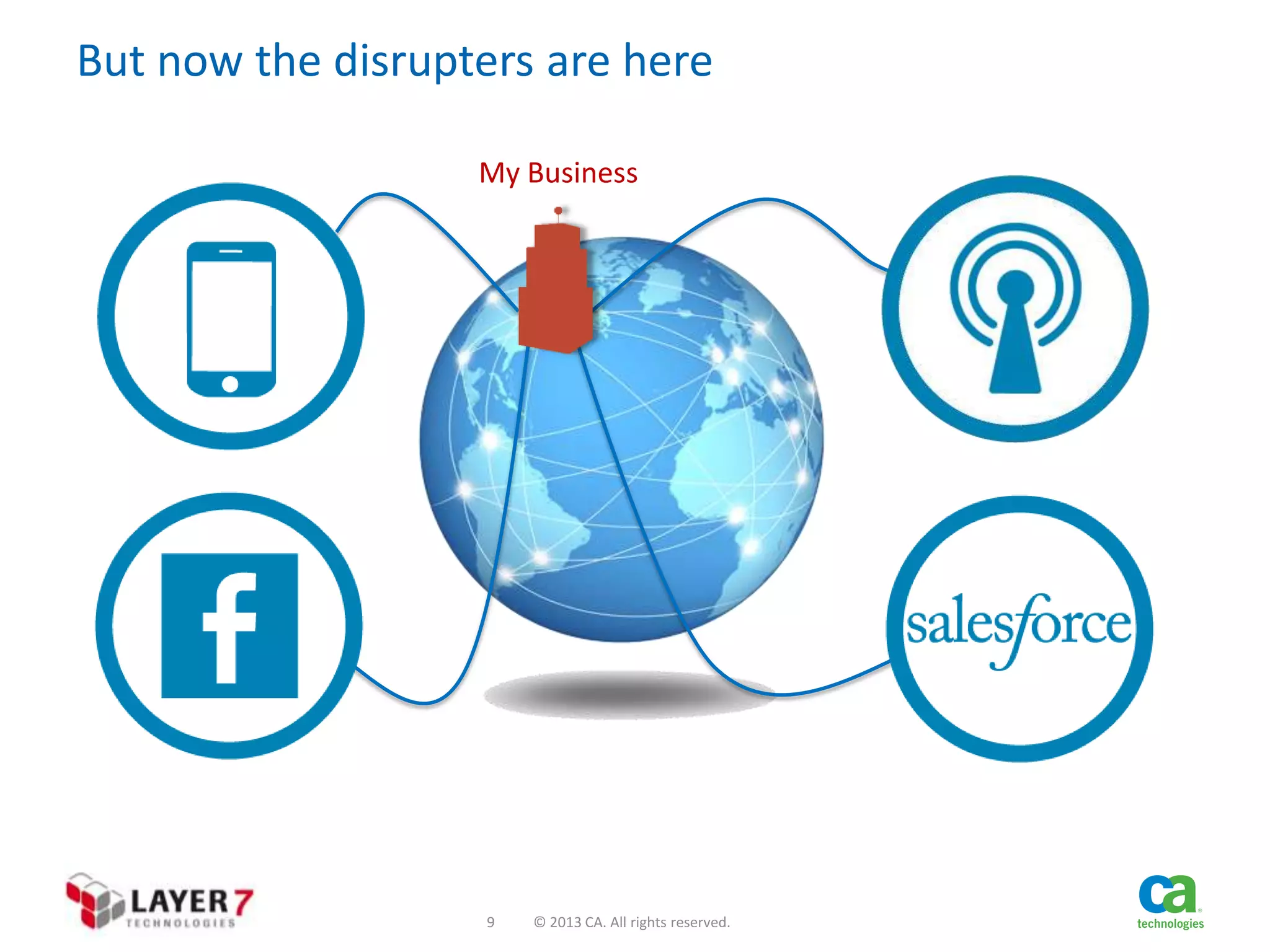
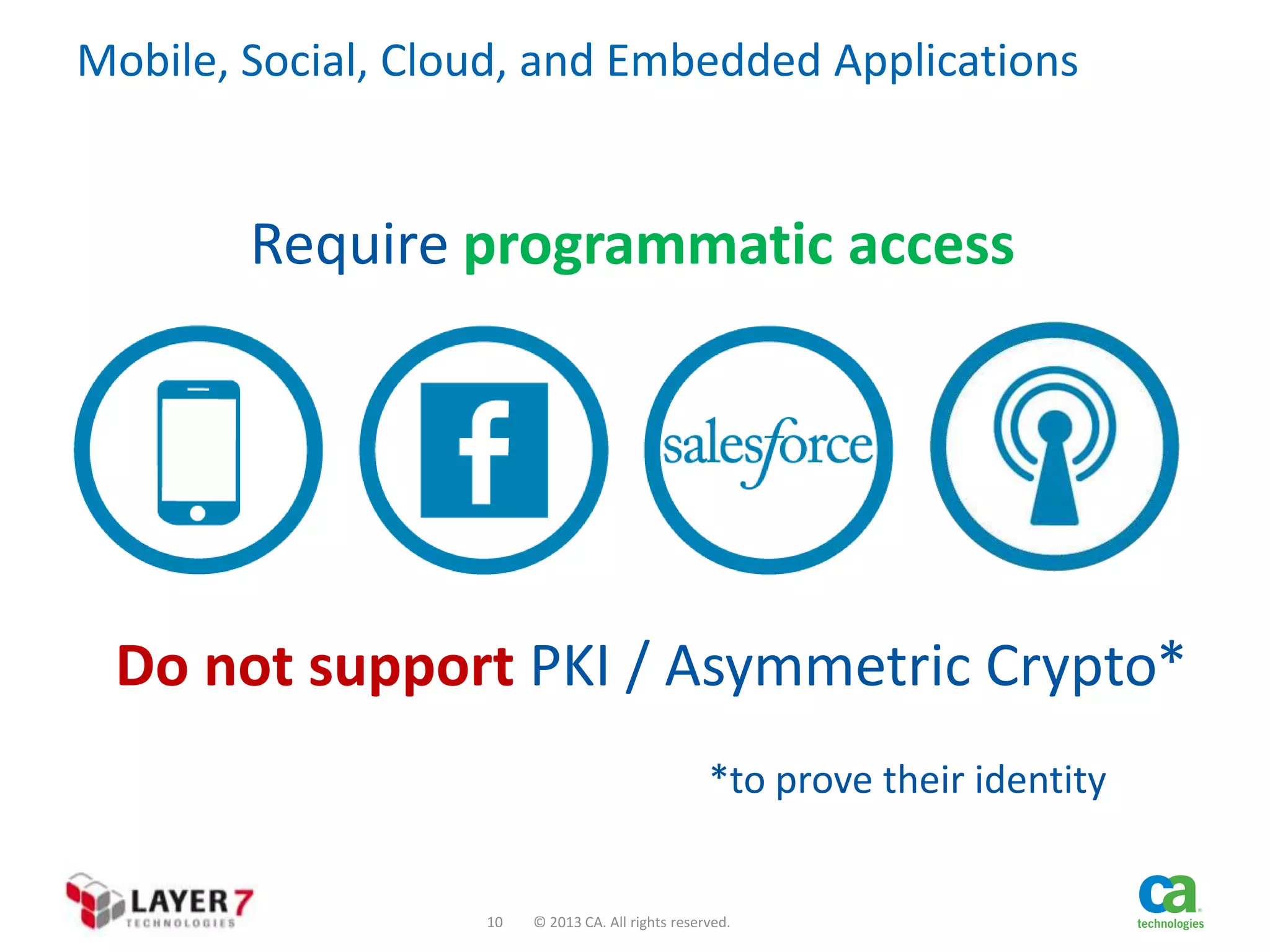
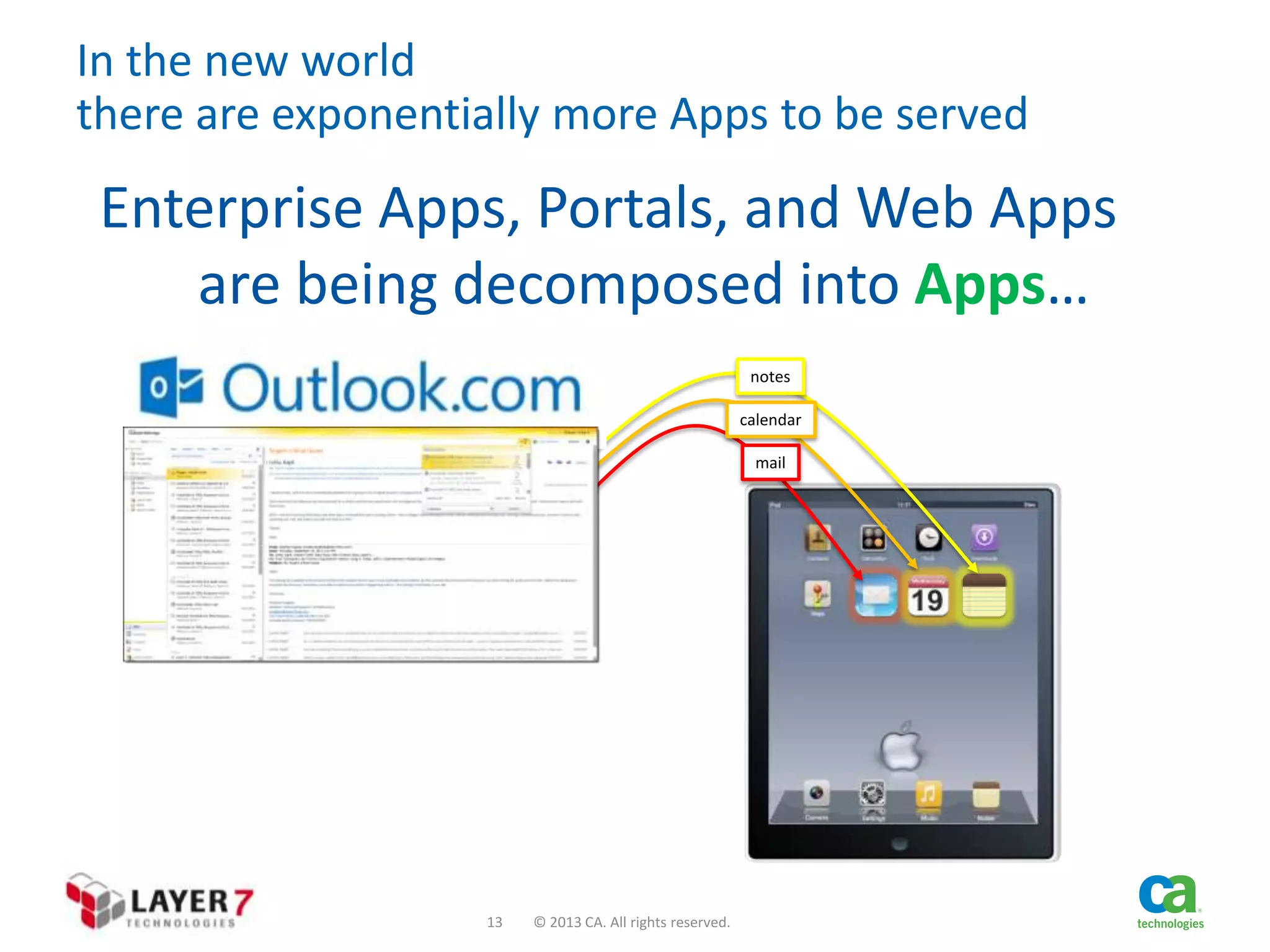
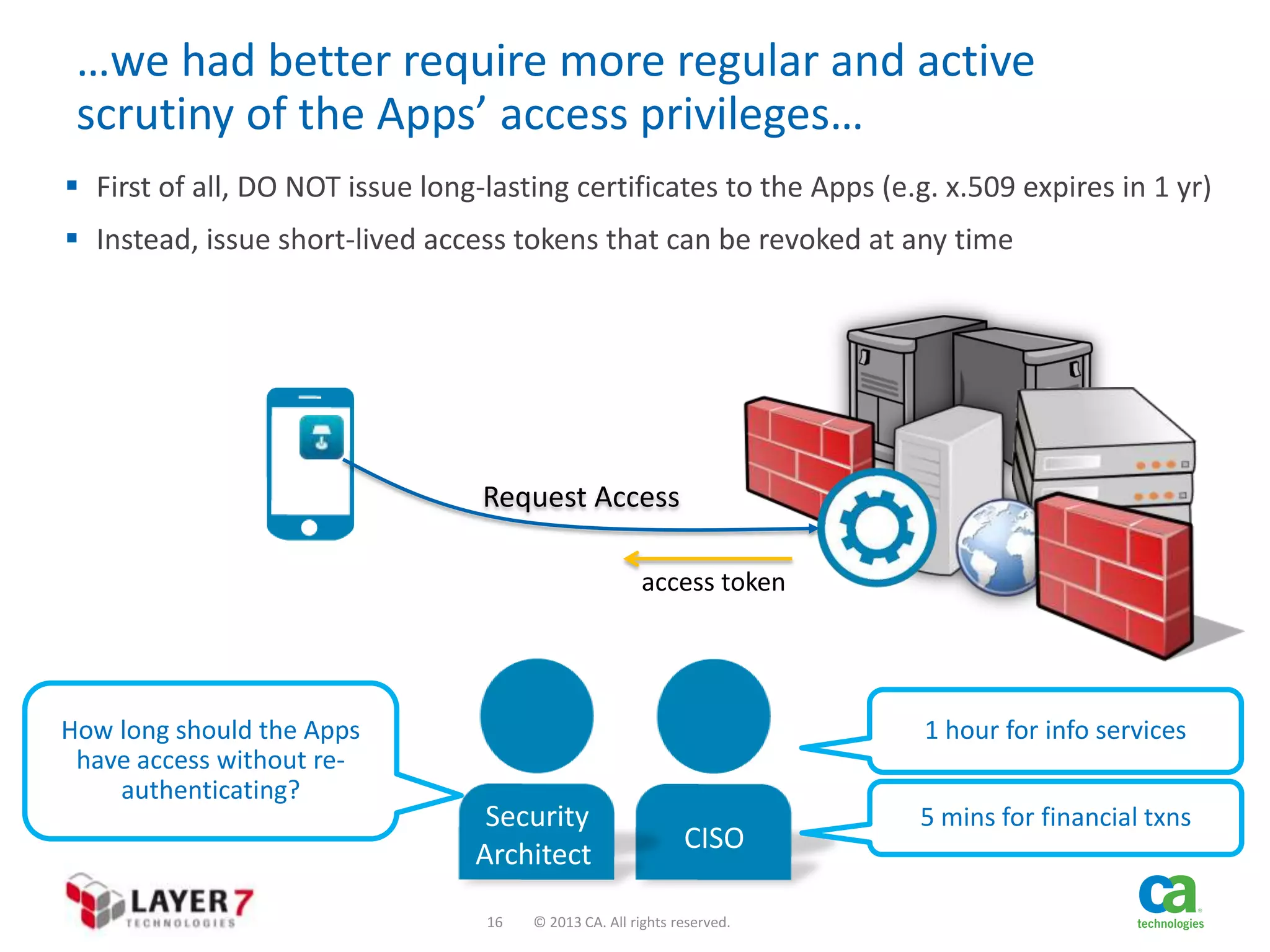
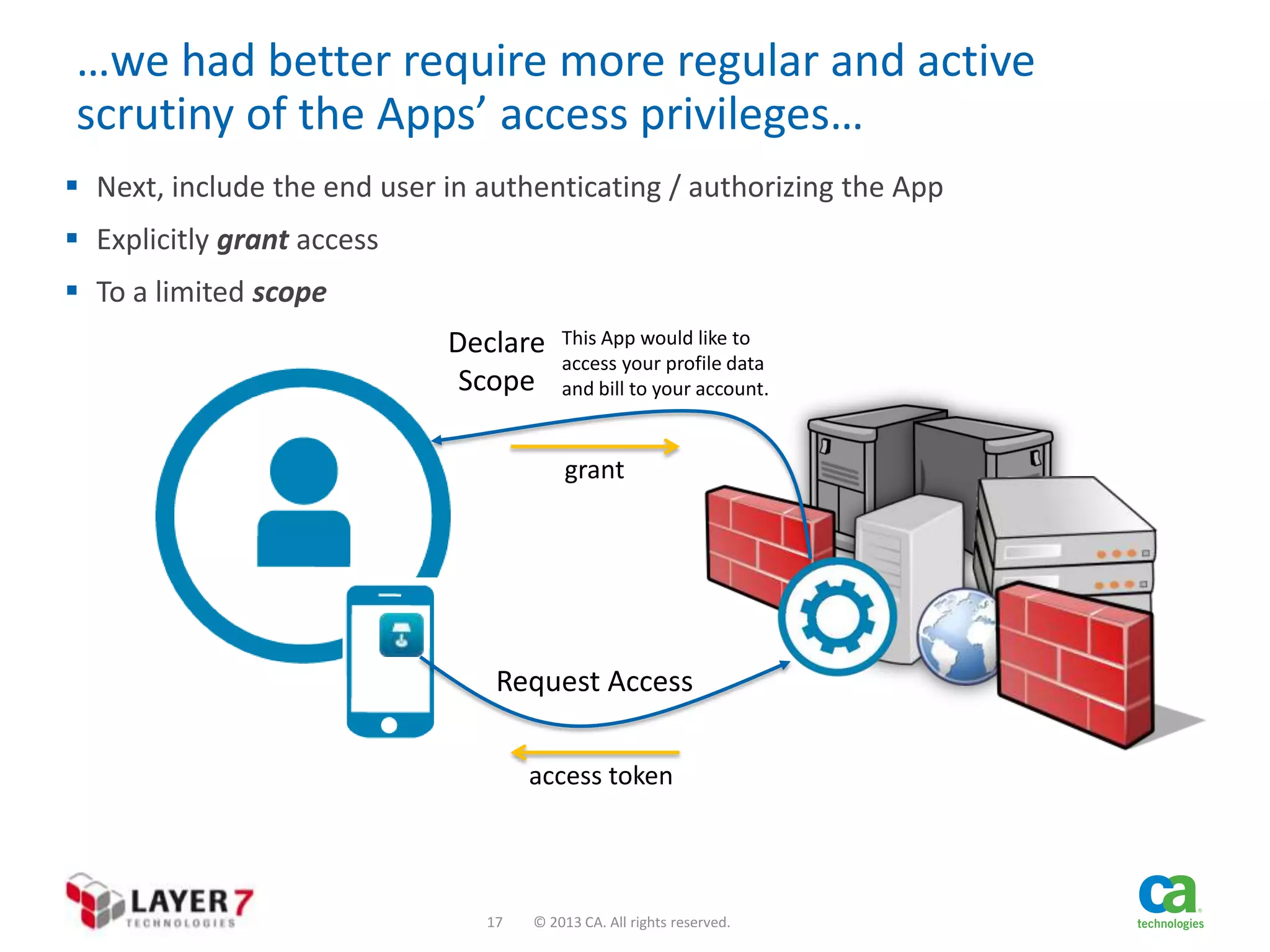
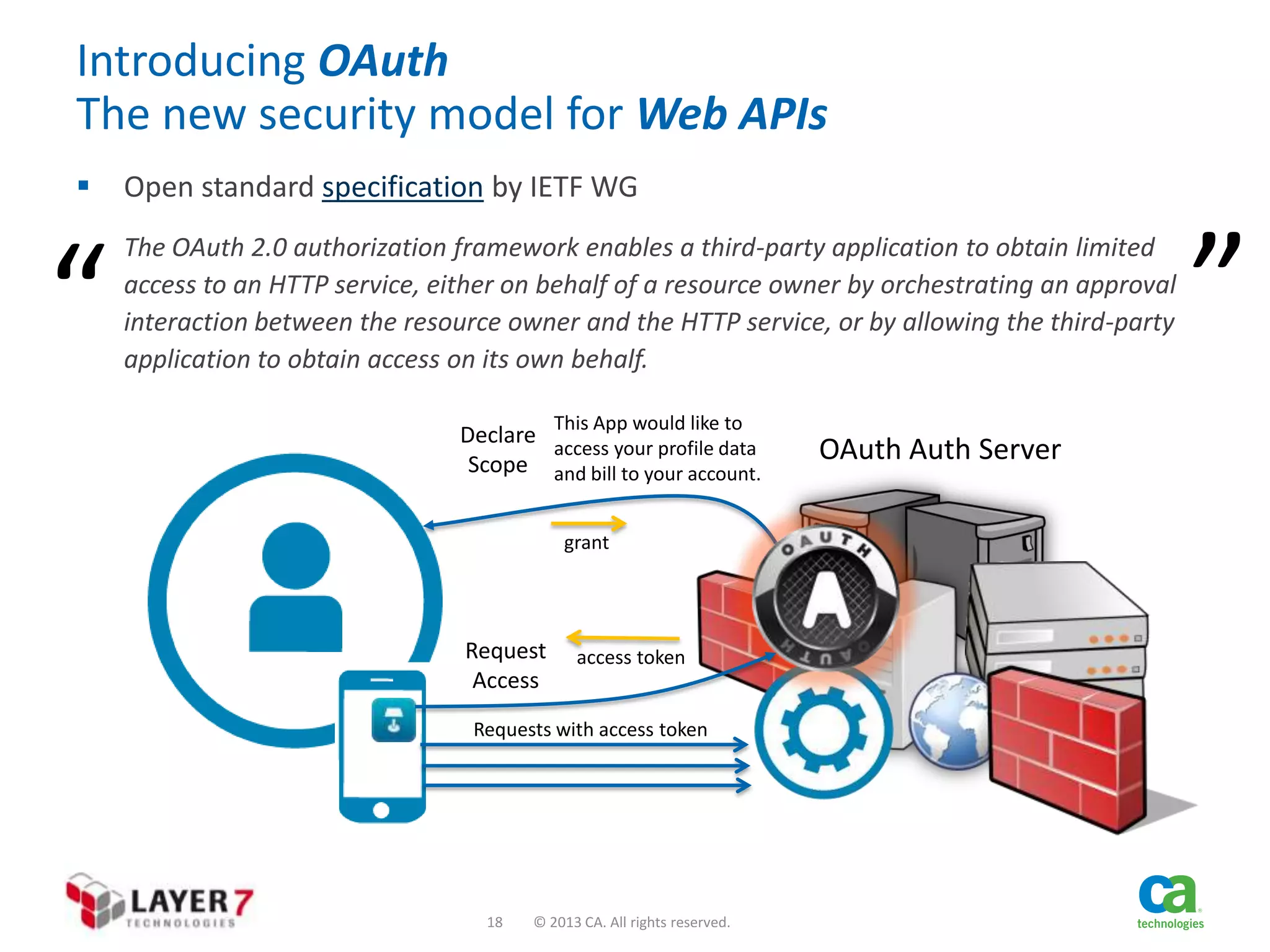
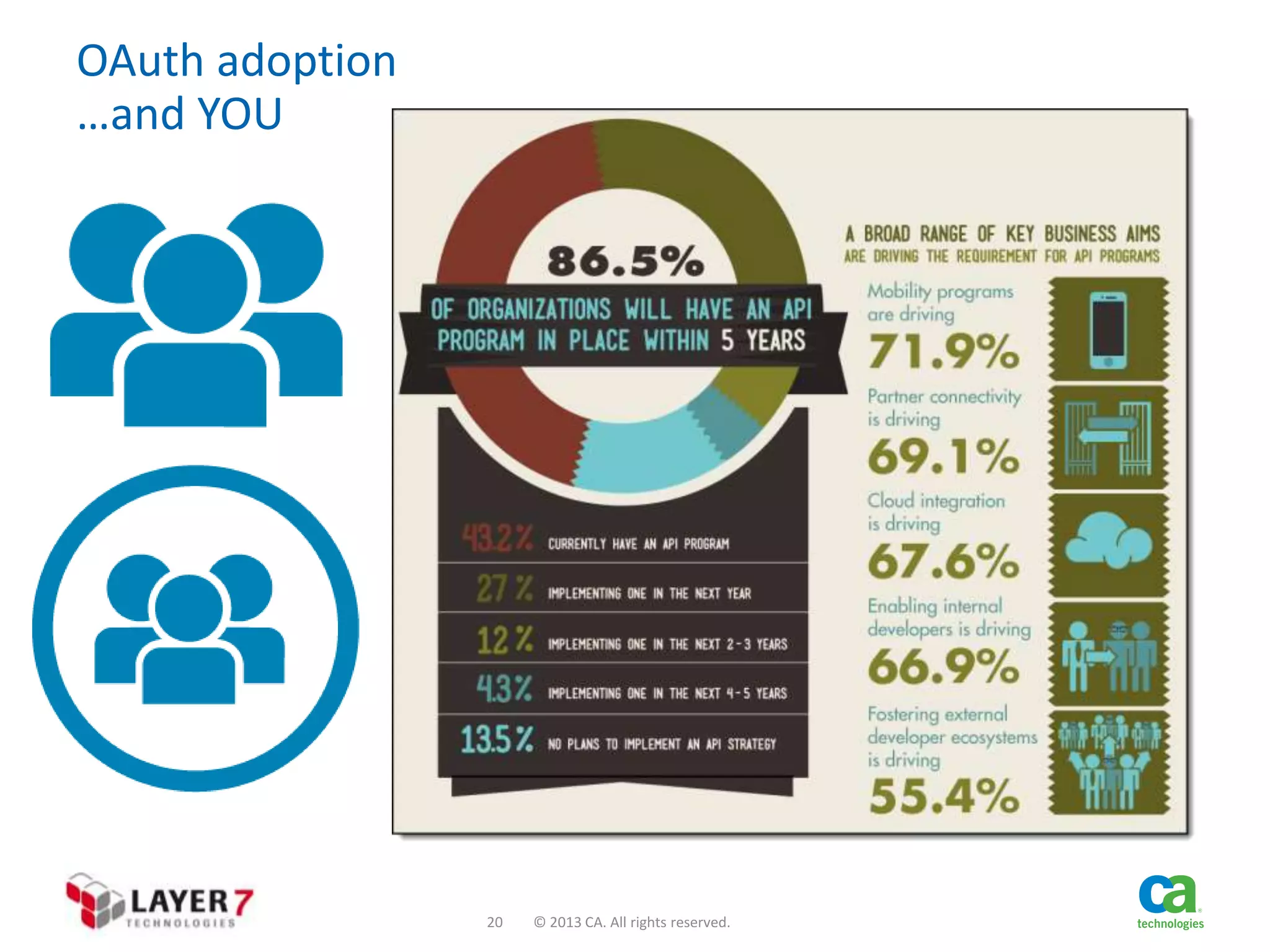
The document discusses the evolution and security challenges of web APIs, outlining the shift from traditional APIs to web APIs that interact over the internet. It emphasizes the need for a new security model that includes short-lived access tokens and involves user participation in the authentication process, primarily through OAuth 2.0. The document also highlights the importance of regular scrutiny of app access privileges to ensure safer web API exposure.