Tools & Methods of Program Analysis (TMPA-2013)
Vladimir A. Zakharov, Associate Professor of Mathematical Cybernetics Department, Head of Laboratory of Mathematical Problems of Computer Security, Faculty of Computational Mathematics and Cybernetics, Moscow State University (MSU)
Mathematical Aspects of Program Obfuscation



















![ÑÒÎÉÊÎÑÒÜ ÎÁÔÓÑÊÀÖÈÈ Â ÌÎÄÅËÈ
ÂÈÐÒÓÀËÜÍÎÃÎ ¾×ÅÐÍÎÃÎ ßÙÈÊÀ¿
[Barak B., Goldreich O., Impagliazzo R., et al., 2001]
Âåðîÿòíîñòíûé àëãîðèòì O íàçûâàåòñÿ îáôóñêàòîðîì,
ñòîéêèì â ìîäåëè ¾÷åðíîãî ÿùèêà¿, åñëè îí
óäîâëåòâîðÿåò ñëåäóþùèì òðåáîâàíèÿì:
1. (ôóíêöèîíàëüíîñòü) äëÿ ëþáîé ìàøèíû Òüþðèíãà M
M ≈ O(M).
2. (ïîëèíîìèàëüíîå çàìåäëåíèå) Ñóùåñòâóåò òàêîé ïîëèíîì
p(·), ÷òî äëÿ ëþáîé ìàøèíû Òüþðèíãà M
size(O(M)) ≤ p(size(M)), time(O(M)) ≤ p(time(M)).
A
S
ν
3. (ñòîéêîñòü) Äëÿ ëþáîé PPT (ïðîòèâíèêà ) ñóùåñòâóåò
PPT (ñèìóëÿòîð ) è ïðåíåáðåæèìî ìàëàÿ ôóíêöèÿ ,
òàêèå ÷òî íåðàâåíñòâî
|Pr{A(O(M)) = 1} − Pr{SM (1size(M) ) = 1}| ≤ ν(size(M))
âûïîëíÿåòñÿ äëÿ ëþáîé ìàøèíû Òüþðèíãà M .](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-20-320.jpg)
![ÑÒÎÉÊÎÑÒÜ ÎÁÔÓÑÊÀÖÈÈ Â ÌÎÄÅËÈ
ÂÈÐÒÓÀËÜÍÎÃÎ ¾×ÅÐÍÎÃÎ ßÙÈÊÀ¿
Òåîðåìà [Barak B., Goldreich O.,
Impagliazzo R., et al., 2001]
Îáôóñêàòîðîâ, ñòîéêèõ â ìîäåëè
¾÷åðíîãî ÿùèêà¿, íå ñóùåñòâóåò .](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-21-320.jpg)




![ÑÒÎÉÊÎÑÒÜ ÎÁÔÓÑÊÀÖÈÈ Â ÌÎÄÅËÈ
ÂÈÐÒÓÀËÜÍÎÃÎ ¾×ÅÐÍÎÃÎ ßÙÈÊÀ¿
Äîêàçàòåëüñòâî.
Ïðåäïîëîæèì, ÷òî π ïðîãðàììà, âû÷èñëÿþùàÿ
ôóíêöèþ Hα,β,γ,δ , è O(π) ýòî îáôóñêàöèÿ ïðîãðàììû π.
Ðàñïîëàãàÿ ïðîãðàììîé O(π), òðåáóåòñÿ âûÿñíèòü, ïðàâäà
ëè, ÷òî α = γ è β = δ.
Åñëè òåêñò ïðîãðàììû O(π) íåäîñòóïåí, òî ýòî ìîæíî
ñäåëàòü òîëüêî ïîëíûì ïåðåáîðîì.
Åñëè òåêñò ïðîãðàììû O(π) äîñòóïåí, òî äîñòàòî÷íî
âû÷èñëèòü
O(π)[O(π)[·, 0], 1] .](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-26-320.jpg)

![ÑÒÎÉÊÎÑÒÜ ÎÁÔÓÑÊÀÖÈÈ Â ÌÎÄÅËÈ
ÂÈÐÒÓÀËÜÍÎÃÎ ¾ÑÅÐÎÃÎ ßÙÈÊÀ¿
Ðàññìîòðèì ñåìåéñòâî ðåàãèðóþùèõ ÌÒ (RMT), íà âõîä
êîòîðûõ ïîäàåòñÿ áåñêîíå÷íûé ïîòîê äàííûõ (çàïðîñîâ)
x1 , x2 , . . . , xn , . . . . RMT âû÷èñëÿåò áåñêîíå÷íûé ïîòîê âûõîäíûõ
äàííûõ (îòêëèêîâ) y1, y2, . . . , yn , . . . :
yn = Fn (x1 , x2 , . . . , xn ).
Òåîðåìà[Âàðíîâñêèé Í.Ï., 2002]
Åñëè ñóùåñòâóþò îäíîñòîðîííèå
ôóíêöèè, òî îáôóñêàòîðîâ, ñòîéêèõ â
ìîäåëè âèðòóàëüíîãî ¾ñåðîãî ÿùèêà ¿,
äëÿ ðåàãèðóþùèõ ÌÒ íå ñóùåñòâóåò .](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-28-320.jpg)





![ÎÁÔÓÑÊÀÖÈß ÄËß ÇÀÙÈÒÛ
ÀËÃÎÐÈÒÌÎÂ
Òåîðåìà [S. Goldwasser, G. N. Rothblum, 2007]
Ñóùåñòâóåò íàèëó÷øèé âîçìîæíûé
îáôóñêàòîð äëÿ OBDD ïîëèíîìèàëüíîãî
ðàçìåðà.](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-34-320.jpg)
![ÎÁÔÓÑÊÀÖÈß ÄËß ÇÀÙÈÒÛ
ÀËÃÎÐÈÒÌÎÂ
Òåîðåìà [S. Goldwasser, G. N. Rothblum, 2007]
Ñóùåñòâóåò íàèëó÷øèé âîçìîæíûé
îáôóñêàòîð äëÿ OBDD ïîëèíîìèàëüíîãî
ðàçìåðà.
Òåîðåìà
Åñëè äëÿ ñåìåéñòâà 3-CNF ñóùåñòâóåò
íàèëó÷øèé âîçìîæíûé îáôóñêàòîð, òî
Σ
= PSPACE .
poly
2](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-35-320.jpg)
![ÎÁÔÓÑÊÀÖÈß ÄËß ÇÀÙÈÒÛ
ÀËÃÎÐÈÒÌÎÂ
[Barak B., Goldreich O., Impagliazzo R., et al., 2001]
Âåðîÿòíîñòíûé àëãîðèòì O îáëàäàåò ñâîéñòâîì
íåîòëè÷èìîãî îáôóñêàòîðà, åñëè îí óäîâëåòâîðÿåò
ñëåäóþùèì òðåáîâàíèÿì:
1. (ôóíêöèîíàëüíîñòü) äëÿ ëþáîé ìàøèíû Òüþðèíãà M
M ≈ O(M).
2. (ïîëèíîìèàëüíîå çàìåäëåíèå) Ñóùåñòâóåò òàêîé ïîëèíîì
p(·), ÷òî äëÿ ëþáîé ìàøèíû Òüþðèíãà M
size(O(M)) ≤ p(size(M)), time(O(M)) ≤ p(time(M)).
3. (ñòîéêîñòü) Äëÿ ëþáîé PPT A (ïðîòèâíèêà ) ñóùåñòâóåò
òàêàÿ ïðåíåáðåæèìî ìàëàÿ ôóíêöèÿ ν , ÷òî äëÿ ëþáîé
ïàðû ìàøèí Òüþðèíãà M1, M2, åñëè M1 ∼ M2, òî
|Pr{A(O(M1 )) = 1}−Pr{A(O(M2 )) = 1}| ≤ ν(size(M1 ) + size(M2 )](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-36-320.jpg)

![ÎÁÔÓÑÊÀÖÈß, ÑÊÐÛÂÀÞÙÀß
ÊÎÍÑÒÀÍÒÓ
Ïóñòü M ýòî ïðîãðàììà ñ ïàðàìåòðîì (ïåðåìåííîé) x .
Îáîçíà÷èì Mc ïðèìåð ïðîãðàììû M , â êîòîðîé âìåñòî
ïàðàìåòðà x ïîäñòàâëåíà êîíñòàíòà c ∈ {0, 1}n .
Âåðîÿòíîñòíûé àëãîðèòì O íàçûâàåòñÿ îáôóñêàòîðîì,
ñêðûâàþùèì êîíñòàíòó, äëÿ ïàðàìåòðèçîâàííîãî ñåìåéñòâà
ïðîãðàìì F = {Mc : c ∈ {0, 1}n , n ≥ 1}, åñëè îí
óäîâëåòâîðÿåò ñëåäóþùèì òðåáîâàíèÿì:
1. (ôóíêöèîíàëüíîñòü)
2. (ïîëèíîìèàëüíîå çàìåäëåíèå)
3. (ñòîéêîñòü) Äëÿ ëþáîé PPT A (ïðîòèâíèêà) ñóùåñòâóåò
PPT S (ñèìóëÿòîð) è ïðåíåáðåæèìî ìàëàÿ ôóíêöèÿ ν ,
òàêèå ÷òî íåðàâåíñòâî
|Pr{A[O(Mc0 ), Mc ] = 1} − Pr{SMc0 [1size(Mc0 ) , Mc ] = 1} ≤ ν(n)
âåðíî äëÿ ëþáîé ïàðû êîíñòàíò c0 ∈ {0, 1}n è c ∈R {0, 1}n .](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-38-320.jpg)

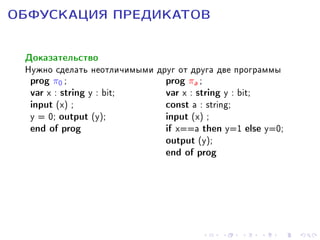
![ÎÁÔÓÑÊÀÖÈß ÏÐÅÄÈÊÀÒÎÂ
Âåðîÿòíîñòíûé àëãîðèòì O íàçûâàåòñÿ îáôóñêàòîðîì
ïðåäèêàòà π, çàäàííîãî íà ñåìåéñòâå ìàøèí Òüþðèíãà F ,
åñëè îí óäîâëåòâîðÿåò ñëåäóþùèì òðåáîâàíèÿì:
1. (ôóíêöèîíàëüíîñòü)
2. (ïîëèíîìèàëüíîå çàìåäëåíèå)
3. (ñòîéêîñòü) Äëÿ ëþáîé PPT A (ïðîòèâíèêà) ñóùåñòâóåò
PPT S (ñèìóëÿòîð) è ïðåíåáðåæèìî ìàëàÿ ôóíêöèÿ ν ,
òàêèå ÷òî íåðàâåíñòâî
|Pr{A[O(M)] = π(M)} − Pr{SM [1size(M) ] = π(M)}| ≤ neg(size(M))
âåðíî äëÿ êàæäîé ÌÒ M èç F è åå îáôóñêàöèè O(M).](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-40-320.jpg)
![ÎÁÔÓÑÊÀÖÈß ÏÐÅÄÈÊÀÒÎÂ
Òî÷å÷íîé íàçûâàåòñÿ ôóíêöèÿ fa : {0, 1}n → {0, 1}, a ∈ {0, 1}n ,
óäîâëåòâîðÿþùàÿ óñëîâèþ
1, åñëè x = a,
fa (x) =
0, åñëè x = a.
Ðàññìîòðèì ñåìåéñòâî Fn , ñîñòîÿùåå èç òî÷å÷íûõ ôóíêöèé
{fu : u ∈ {0, 1}n } è ôóíêöèè, òîæäåñòâåííî ðàâíîé 0. Íà ýòîì
ñåìåéñòâå îïðåäåëåí ïðåäèêàò P(f ) = (f ≡ 0).
Òåîðåìà [Çàõàðîâ Â.À., Âàðíîâñêèé Í.Ï., 2003]
Åñëè ñóùåñòâóþò îäíîñòîðîííèå ïåðåñòàíîâêè, òî
ïðåäèêàò P , îïðåäåëåííûé íà ñåìåéñòâå ïðîãðàìì,
âû÷èñëÿþùèõ ôóíêöèè ñåìåéñòâà Fn , èìååò ñòîéêóþ
îáôóñêàöèþ.](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-41-320.jpg)







![ÄÎÑÒÈÆÅÍÈß ÏÎÑËÅÄÍÈÕ ËÅÒ
 èþëå 2013 ã. áûëà îïóáëèêîâàíà ñòàòüÿ
Candidate Indistinguishability Obfuscation and Functional
Encryption for All Circuits
S. Garg, C. Gentry, S. Halevi, M. Raykova, A. Sahai, B. Waters
â êîòîðîé àâòîðû ïîêàçàëè, ÷òî âåðíà
Òåîðåìà [S. Carg, C. Gentry, et al, 2013]
Íåîòëè÷èìàÿ îáôóñêàöèÿ âîçìîæíà äëÿ
ïðîèçâîëüíûõ ïðîãðàìì
(ïðè íåêîòîðûõ ïðåäïîëîæåíèÿõ î òðóäíîñòè
ðåøåíèÿ çàäà÷ òåîðèè ãðóïï)](https://image.slidesharecdn.com/tmpazakharovobfuscation-131012065237-phpapp02/85/TMPA-2013-Keynote-Zakharov-Obfuscation-50-320.jpg)

