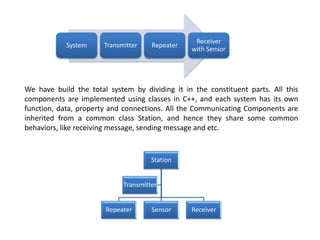
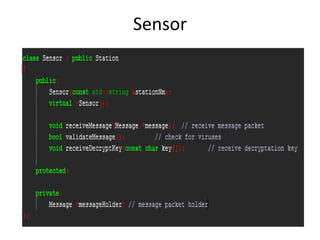
The document describes a prototype for a secure military communication system. It divides the system into different components: a transmitter that encrypts messages and sends them to a repeater, which checks for vulnerabilities before passing messages to a sensor. The sensor verifies messages are safe before decrypting and passing them to a receiver. Each component is implemented as a C++ class, with messages encapsulated in packets. The system aims to prevent sensitive information leaks during transmission by resending corrupted messages until the sensor confirms one was safely received.