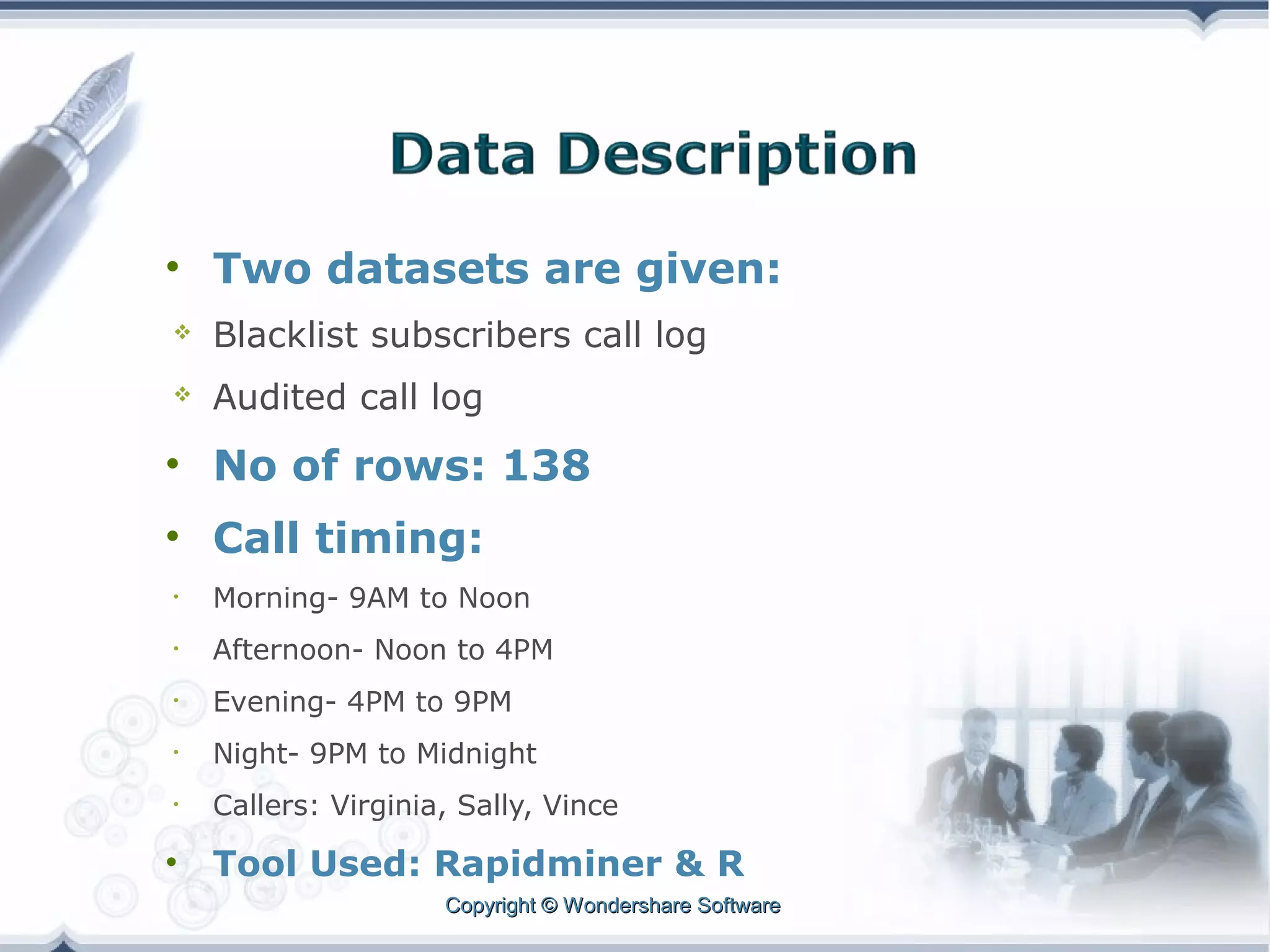
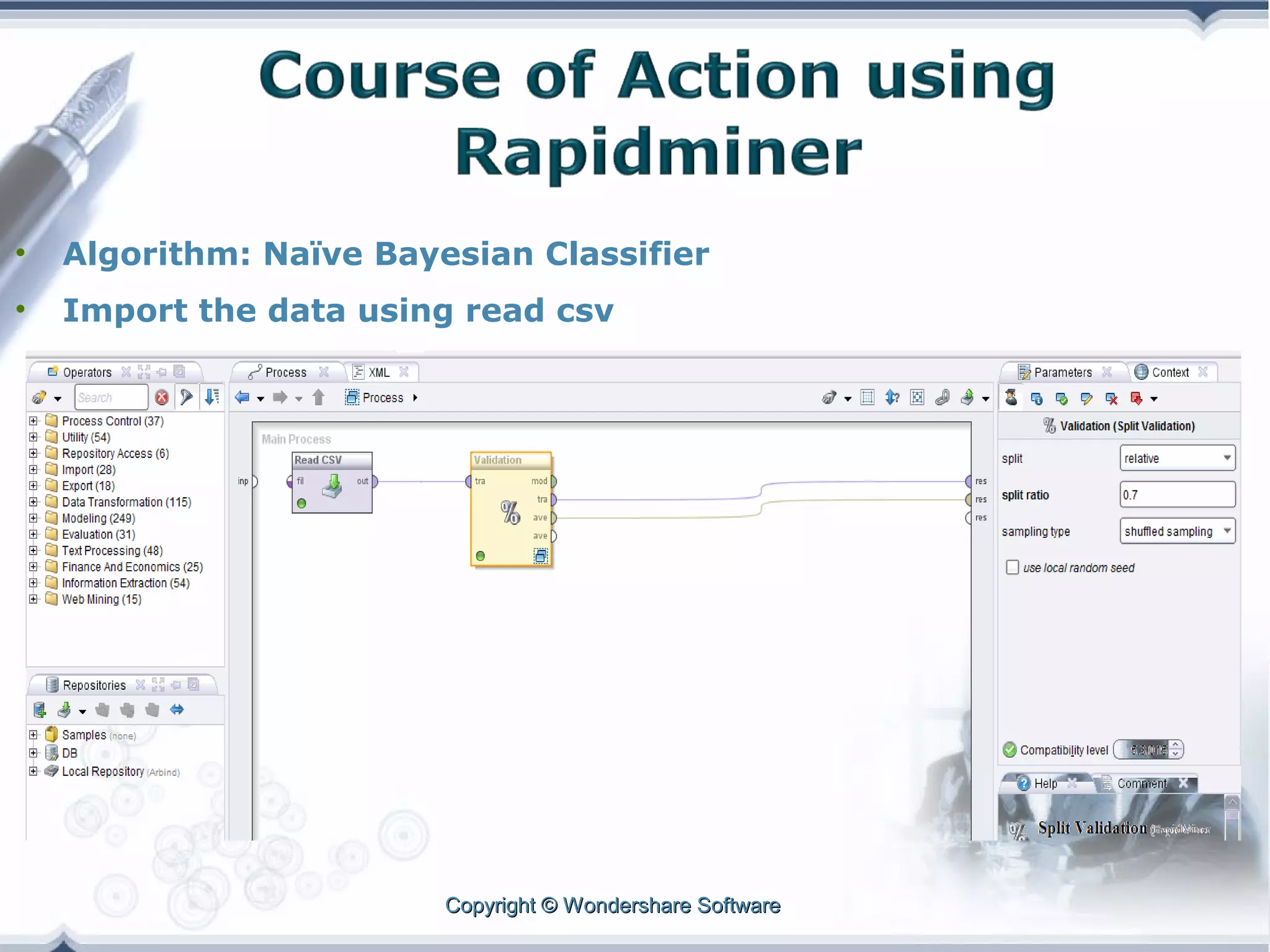
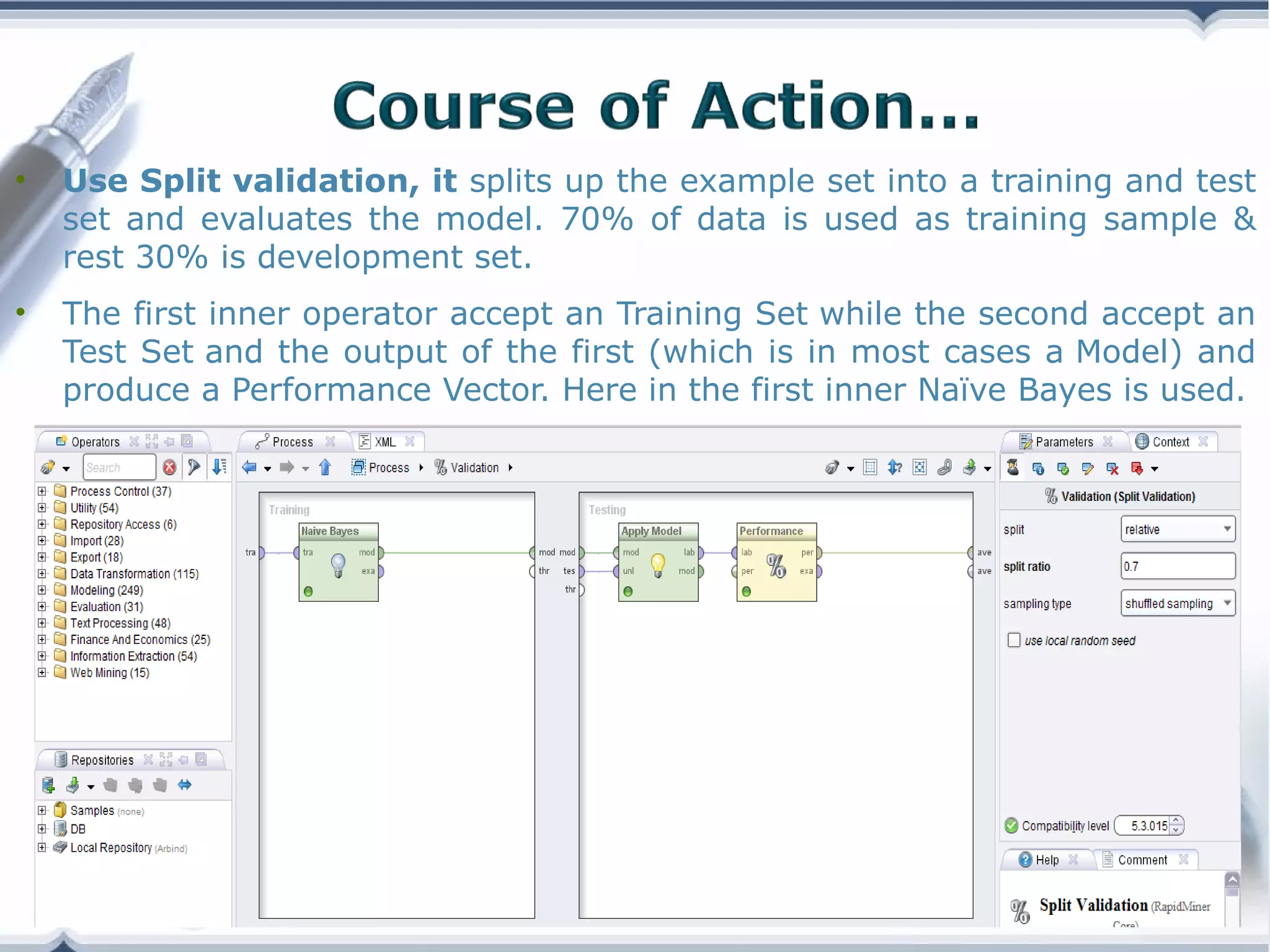
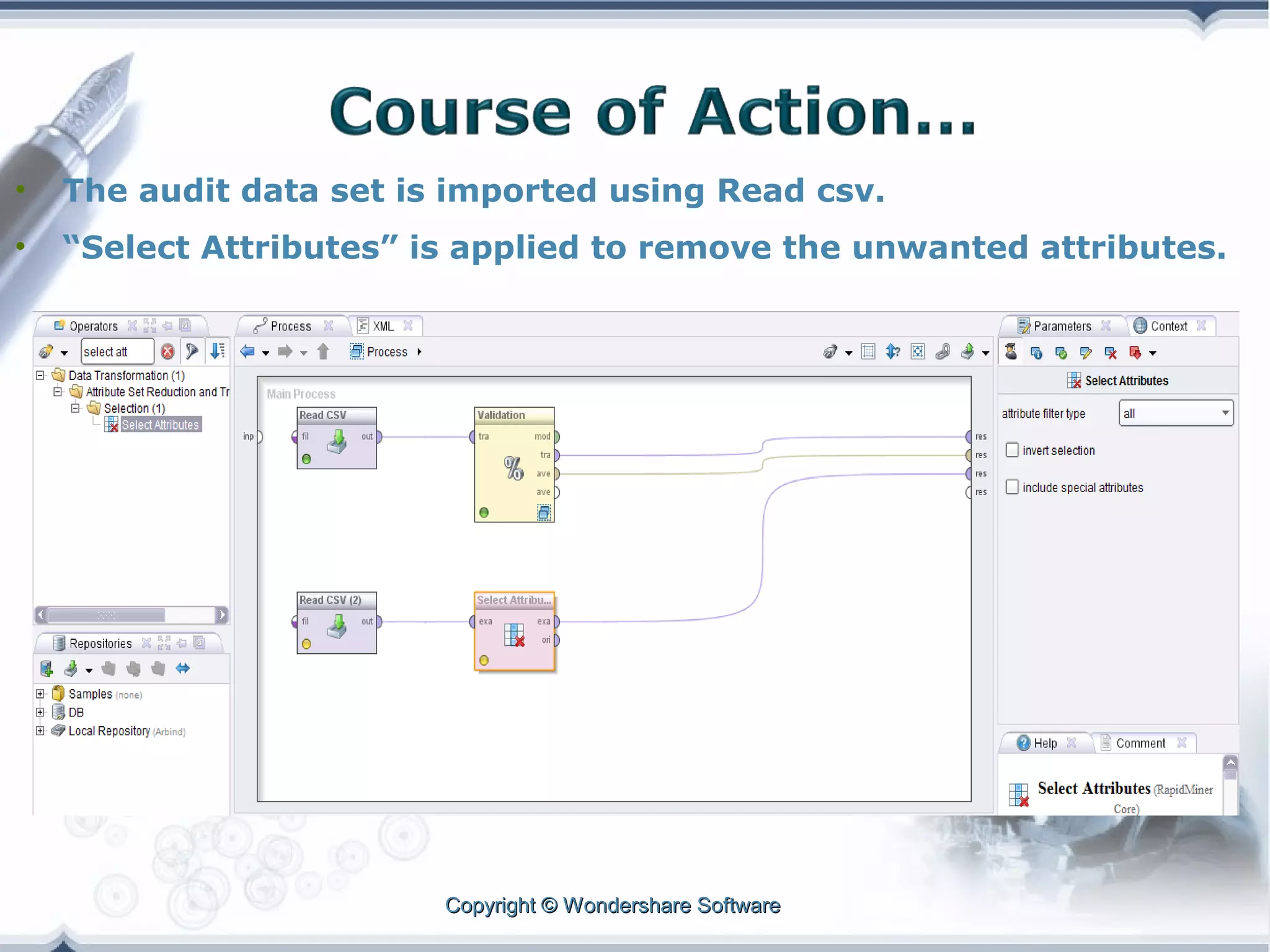
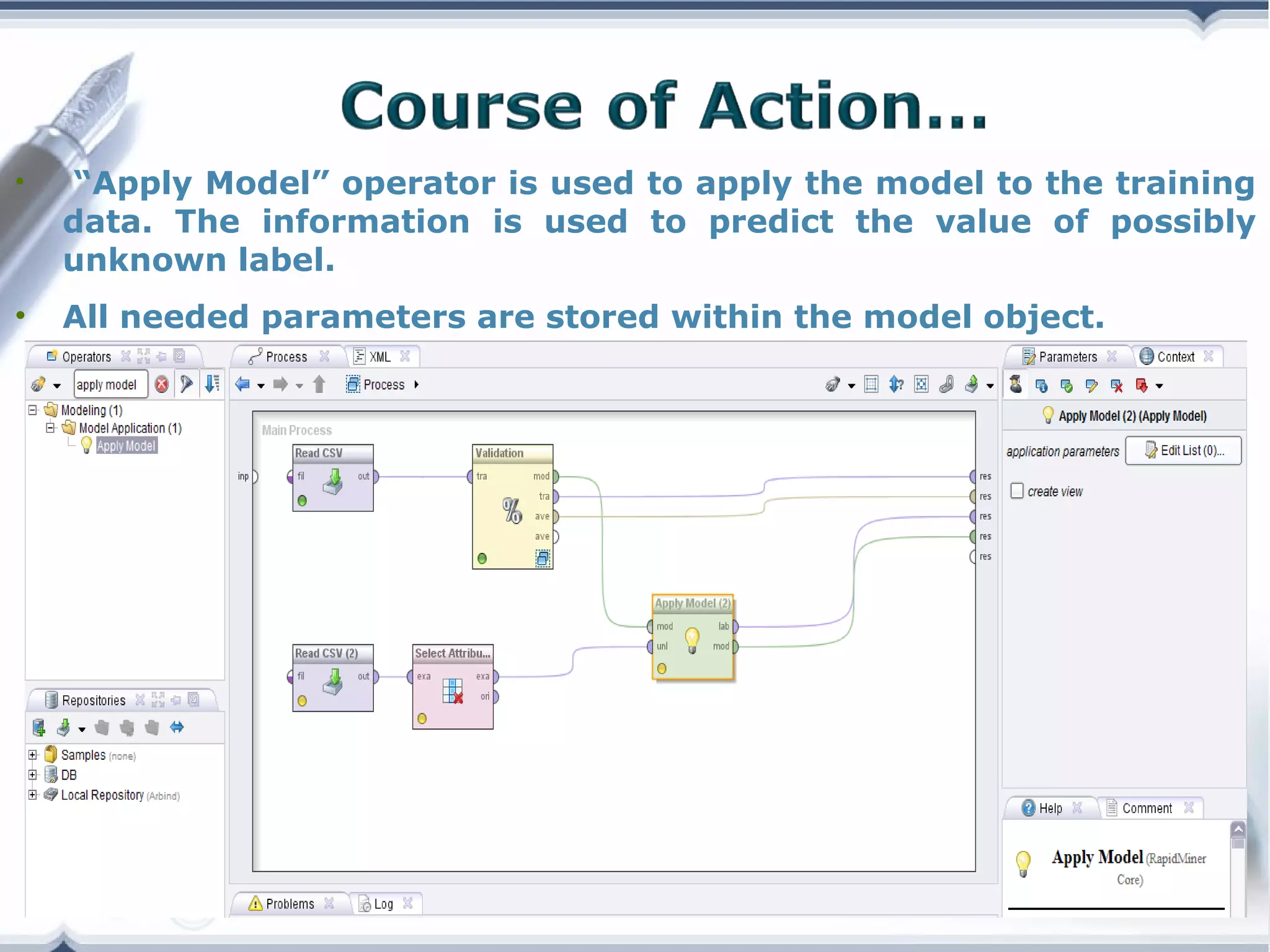
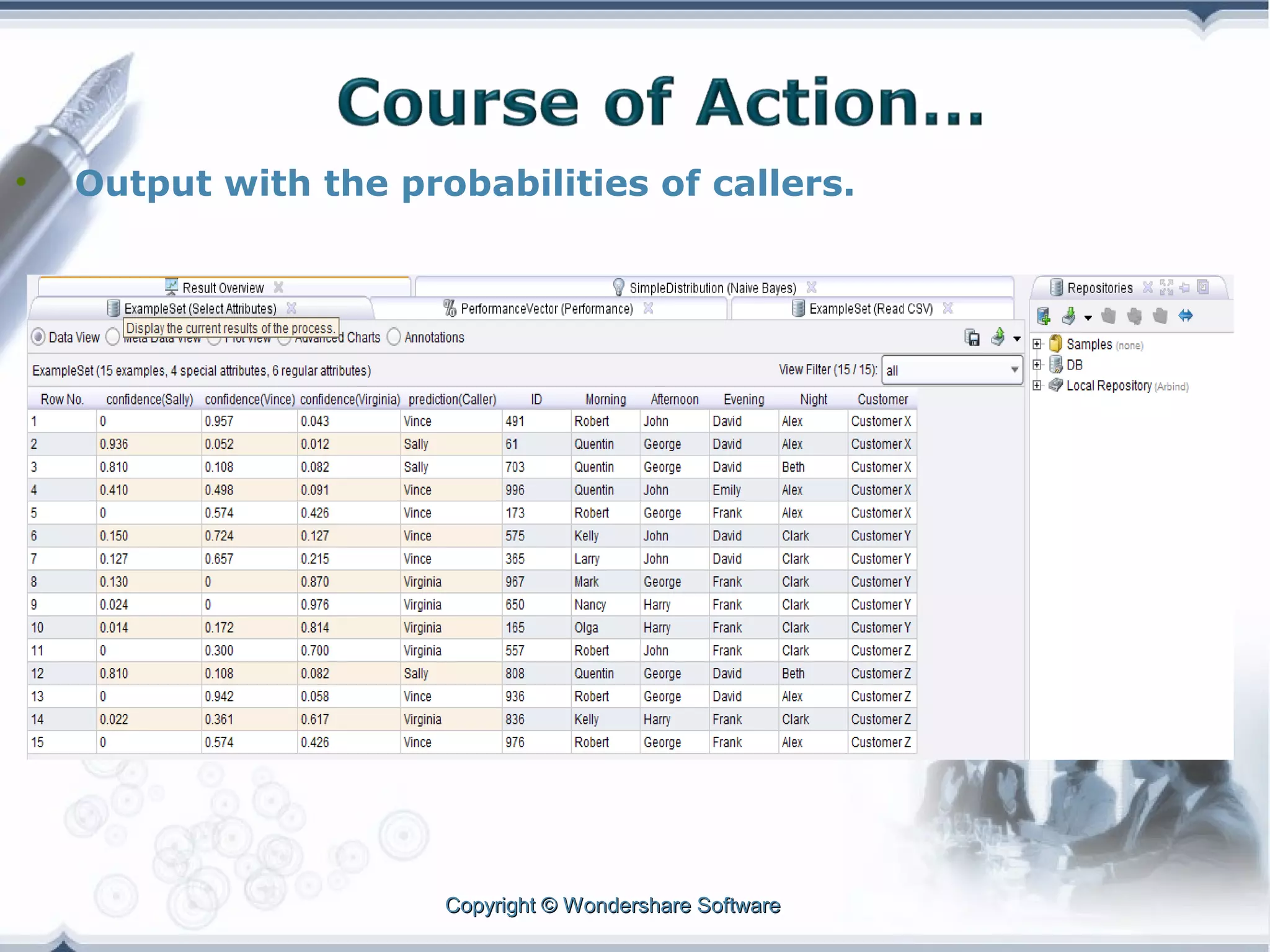
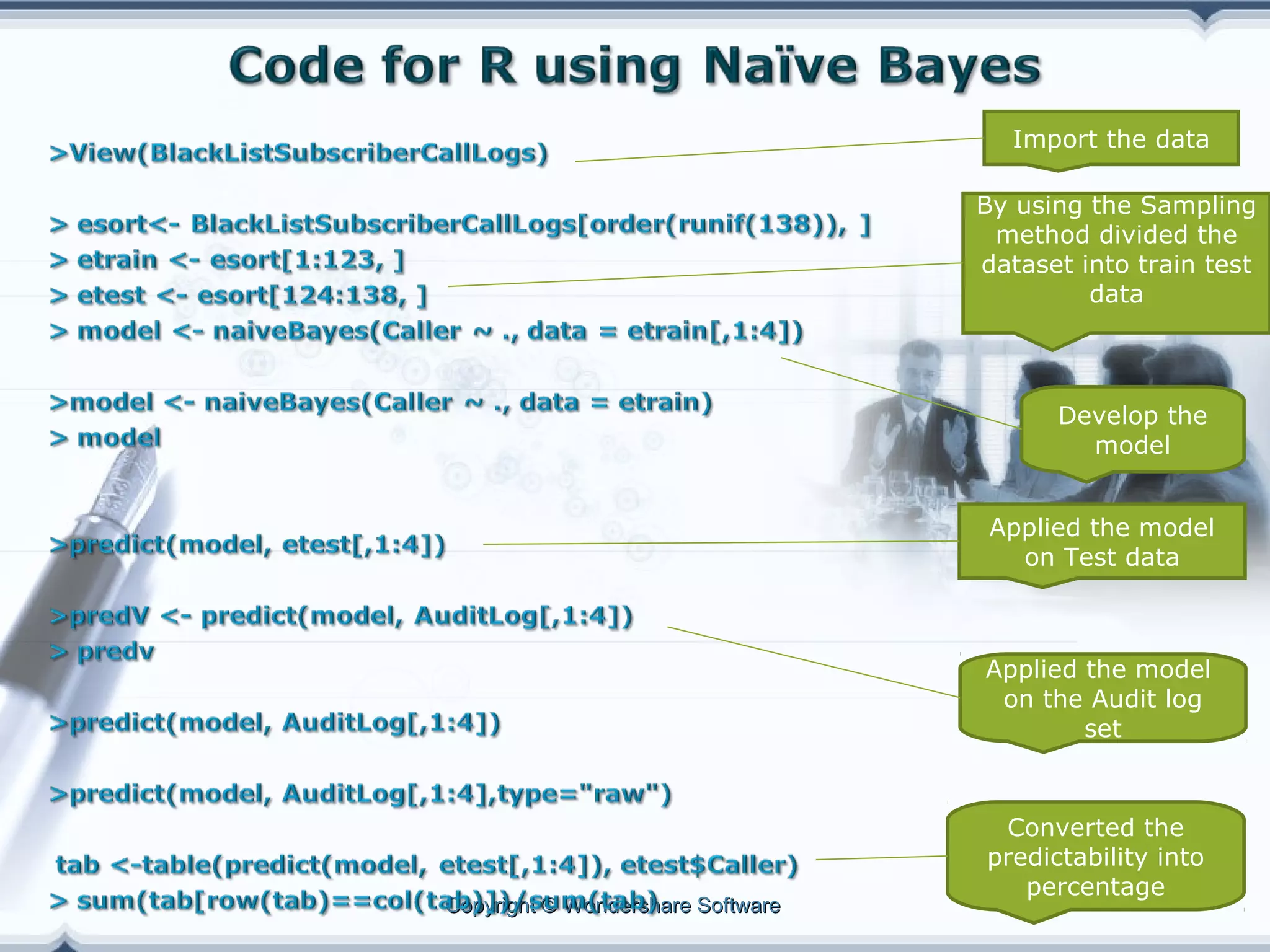
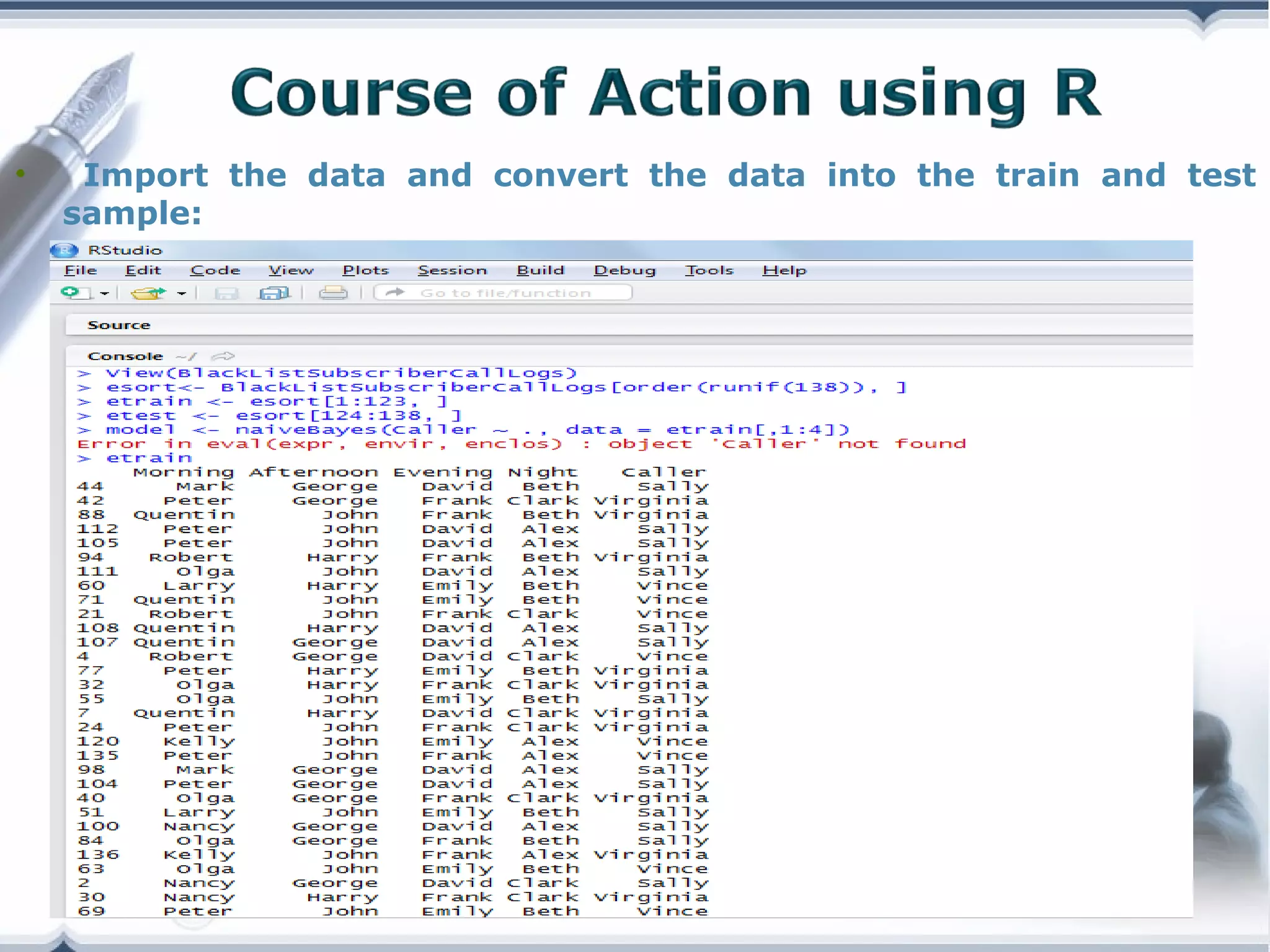
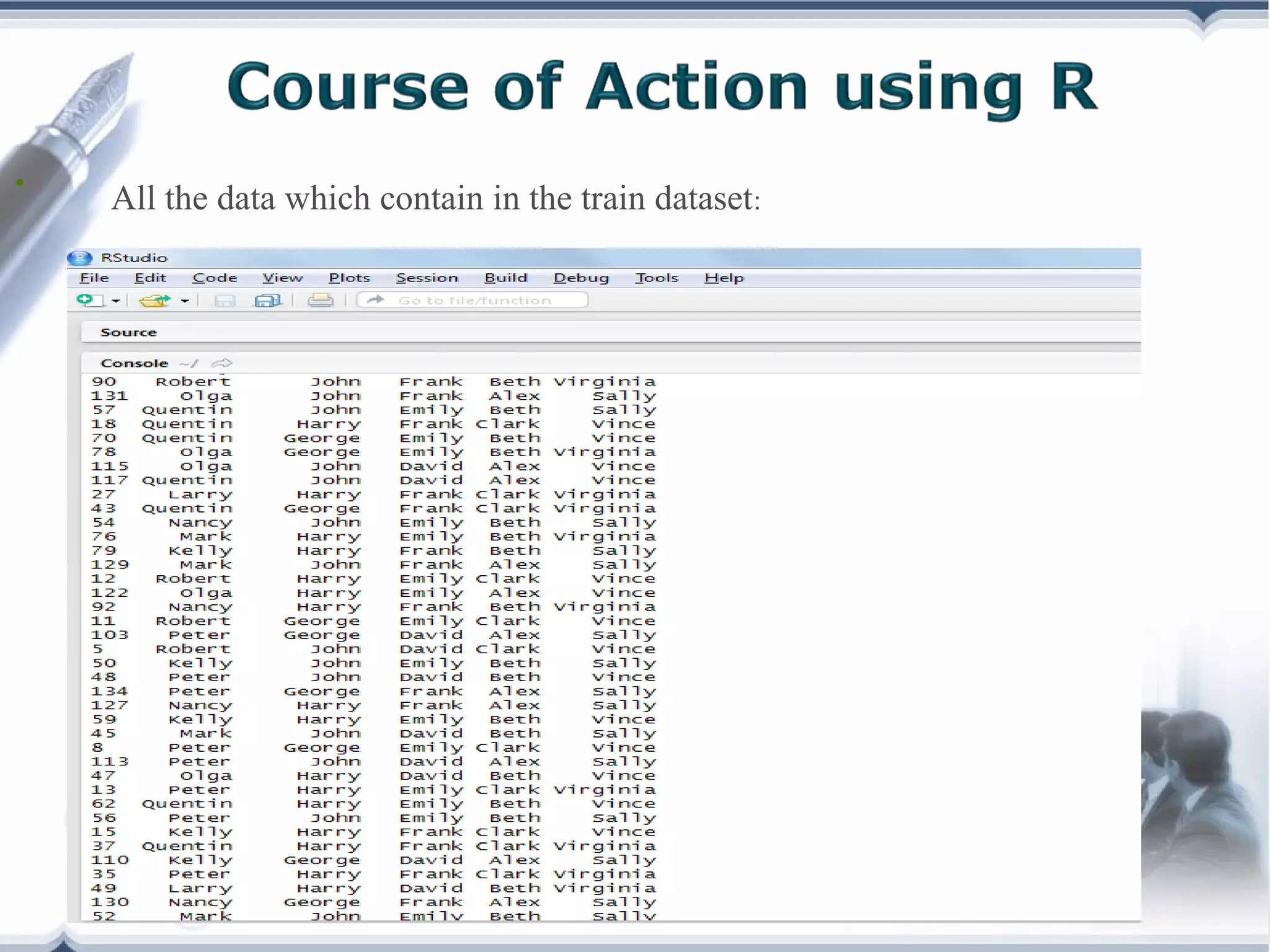
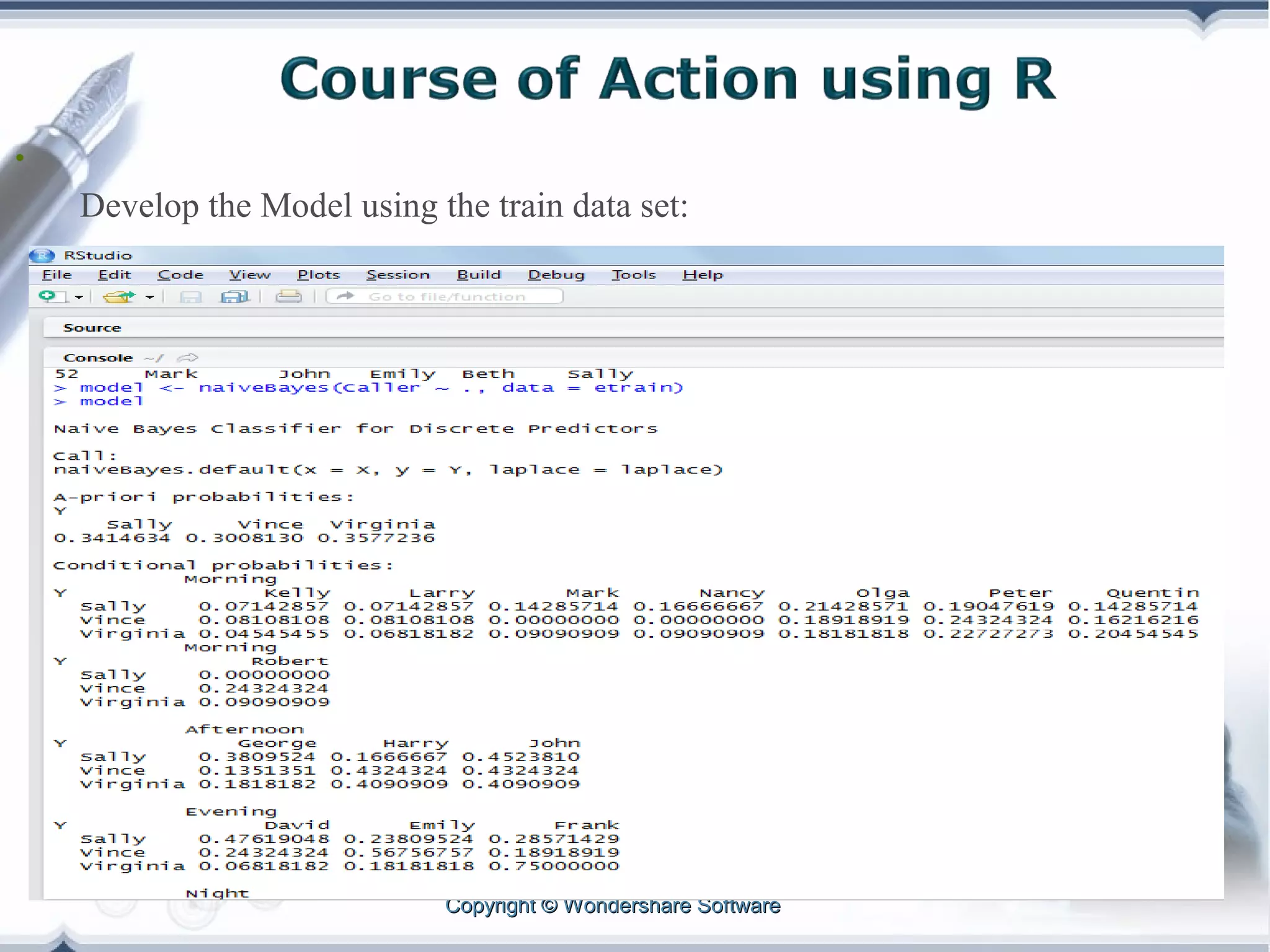
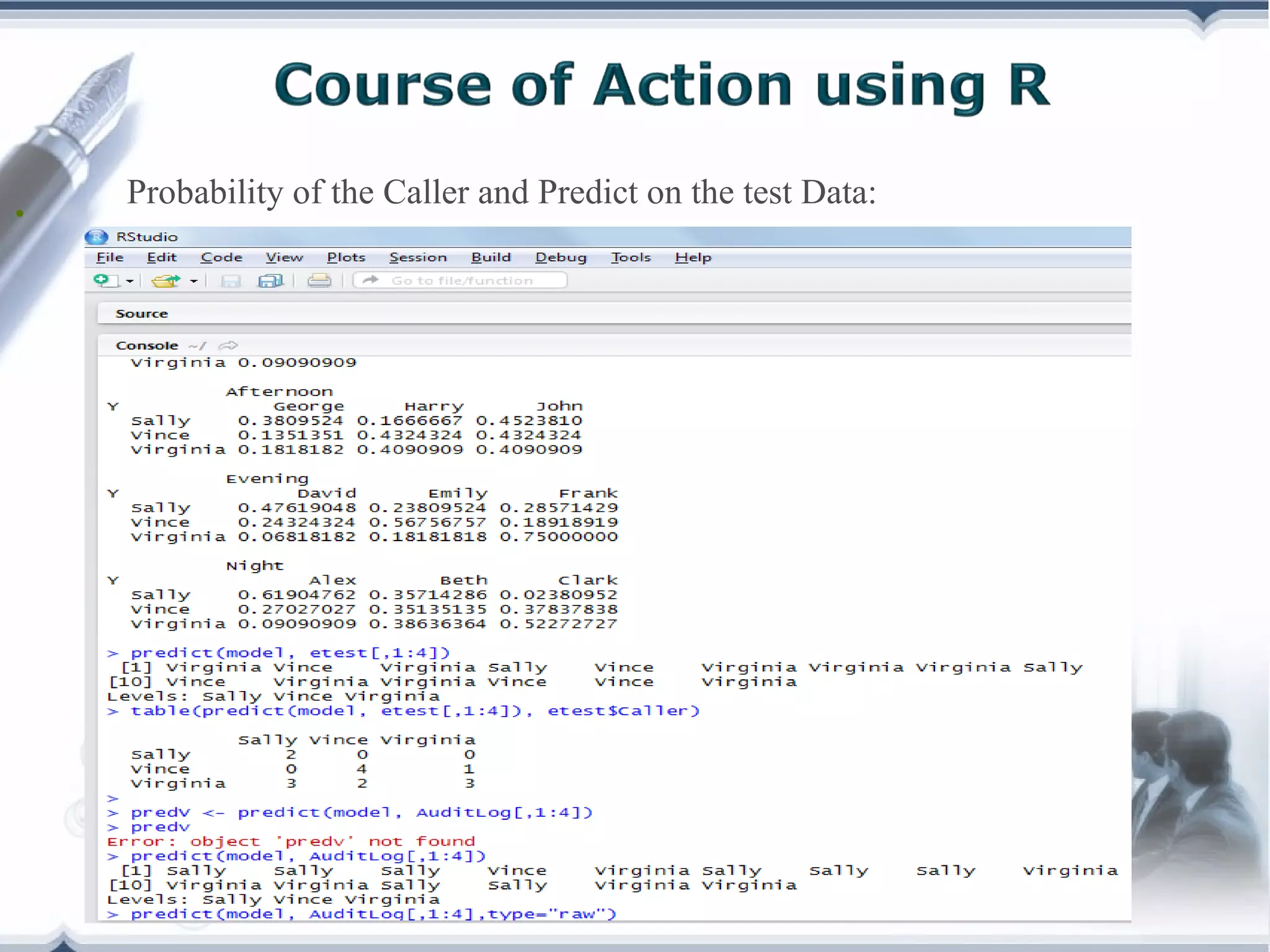
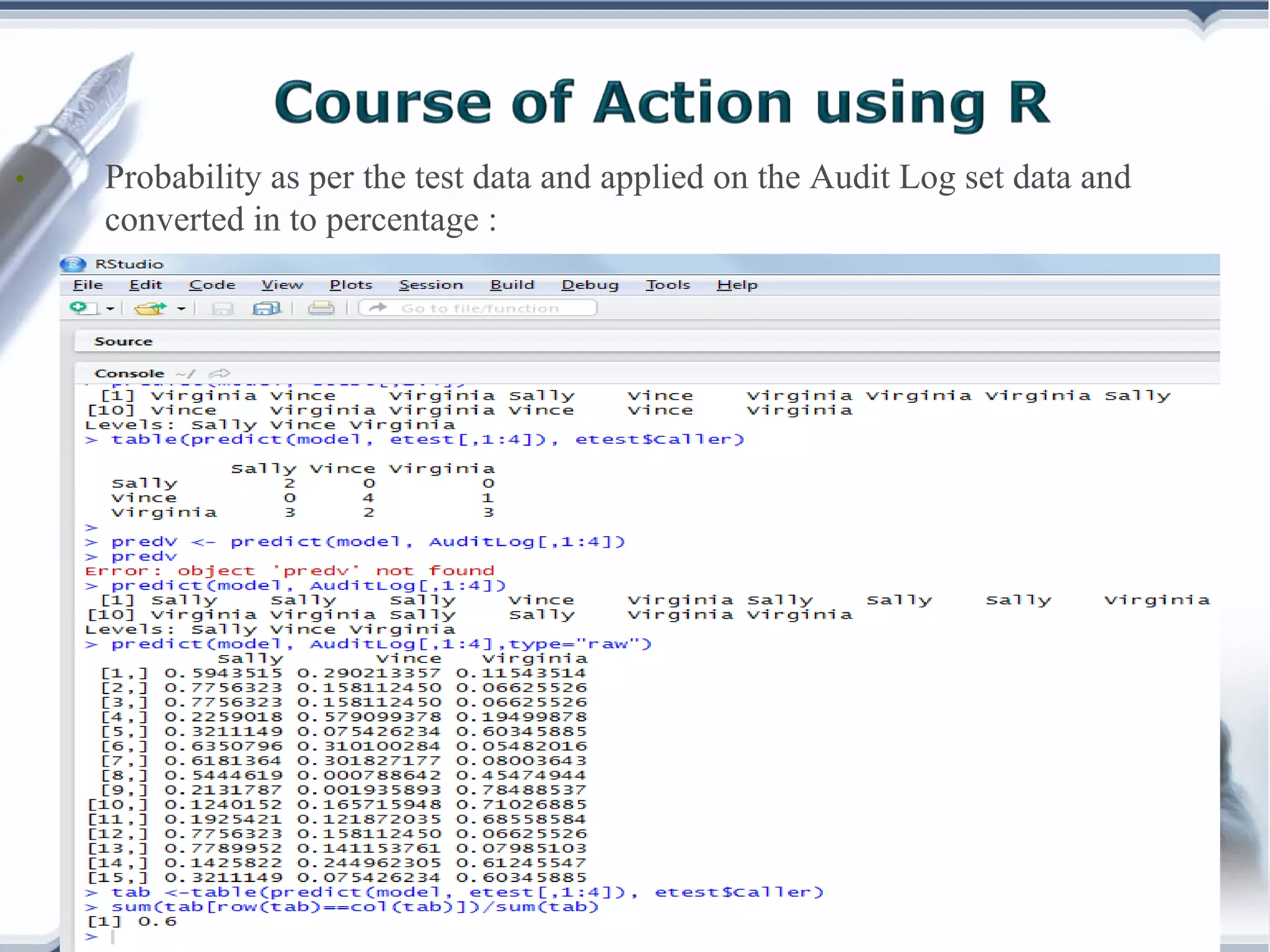
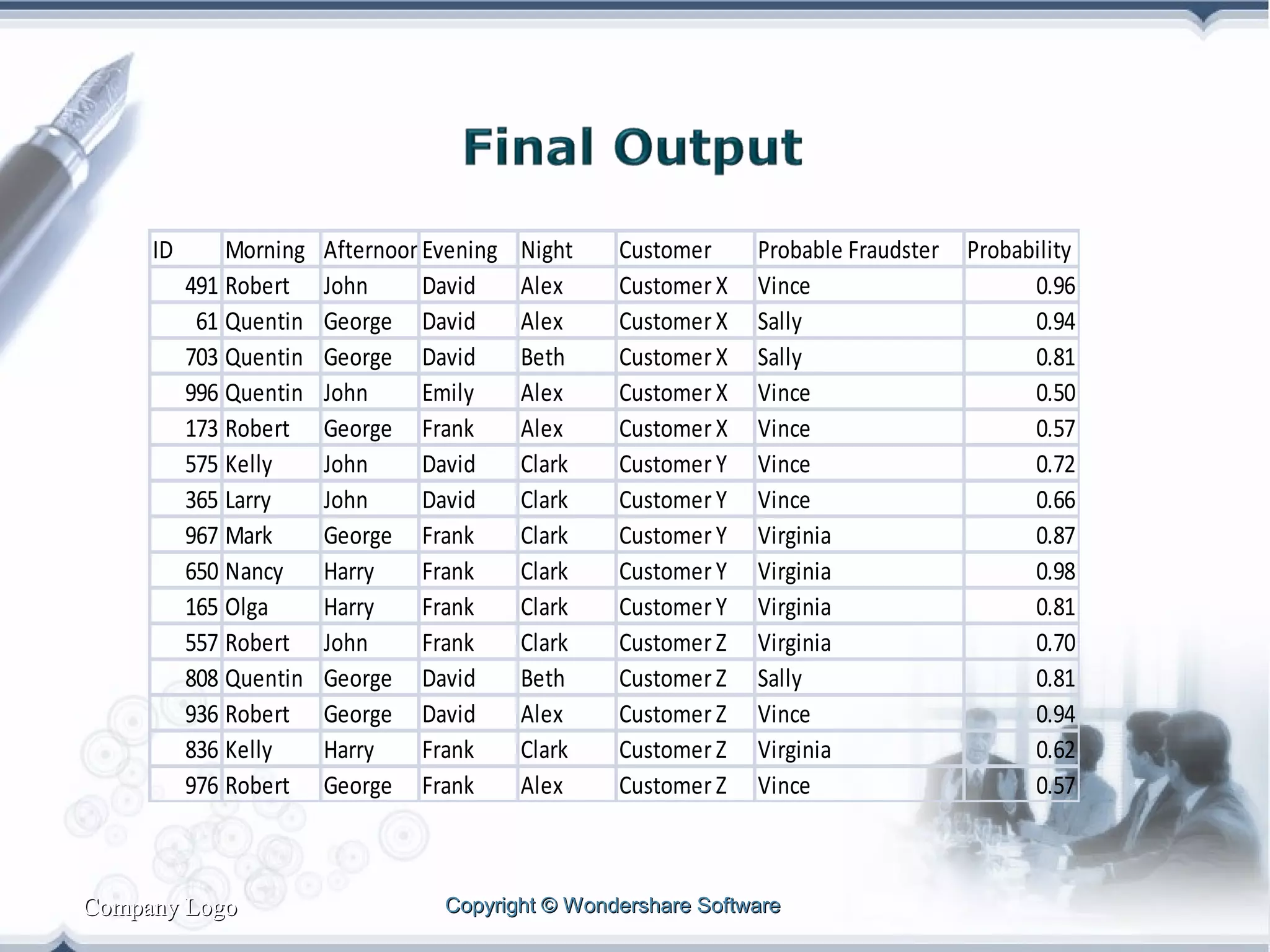
A telecom company, 'Bad Idea', is investigating potential fraud by three identified fraudsters using call logs and a unique rate plan limiting calls. The analysis employs a Naïve Bayesian classifier, splitting the data into training and test sets to evaluate potential fraudulent activity based on call patterns. The results yield probabilities indicating the likelihood of callers being fraudsters, informing the company's ongoing audit efforts.