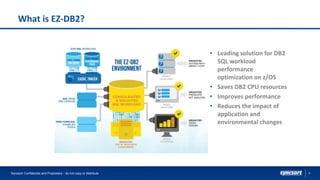
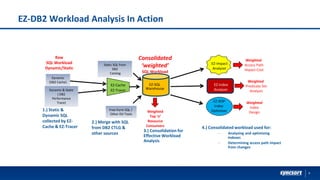
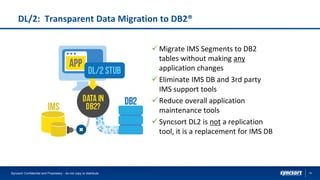
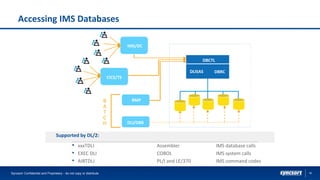
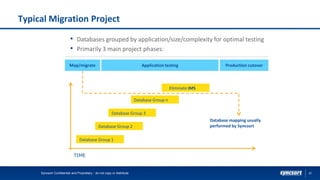
The document highlights Syncsort's solutions for optimizing DB2 systems and migrating IMS data to DB2 without rewriting applications. It discusses the challenges faced by DBAs and how products like ez-DB2 and DL/2 provide performance improvements, reduce costs, and ensure seamless migration. Key benefits include increased system efficiency, minimized risk during migrations, and support for modernizing legacy applications.