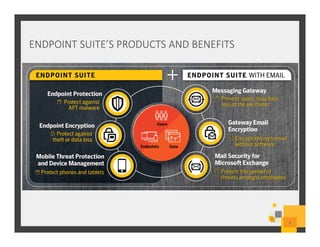
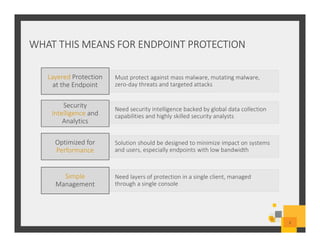
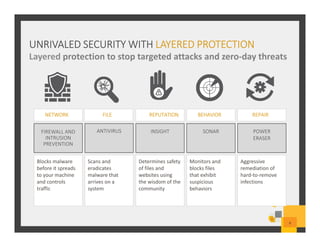
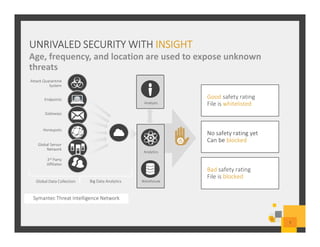
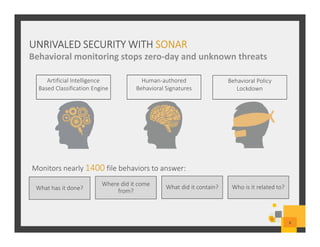
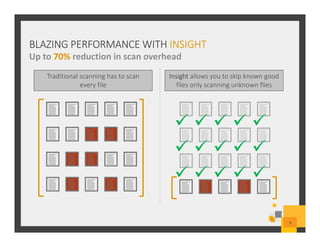
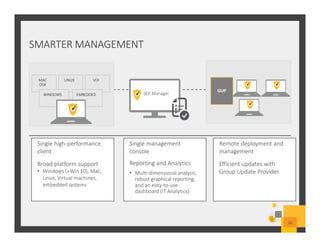
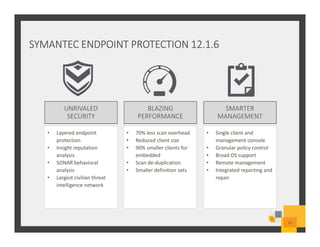
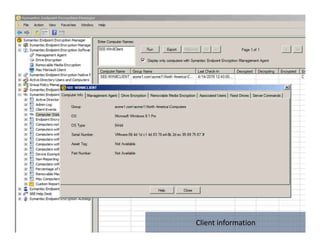
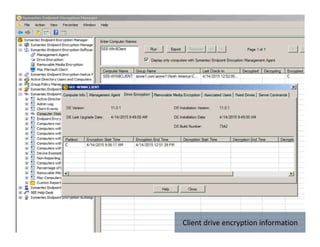
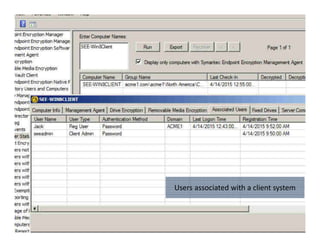
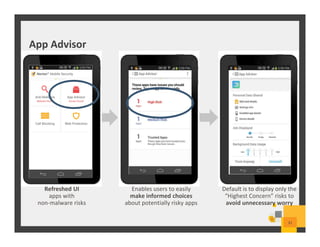
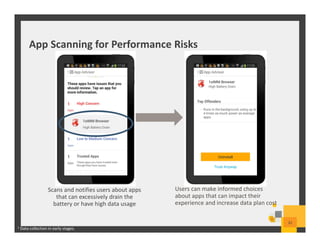
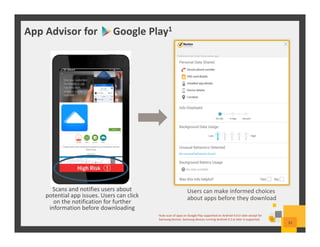
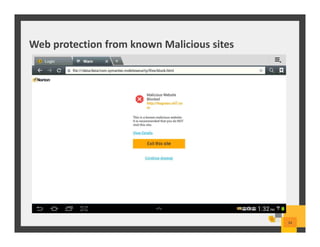
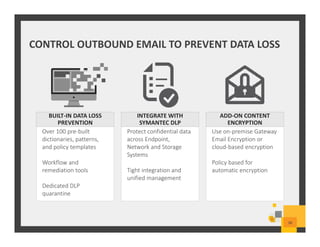
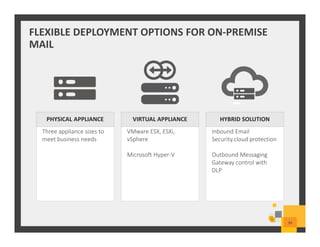
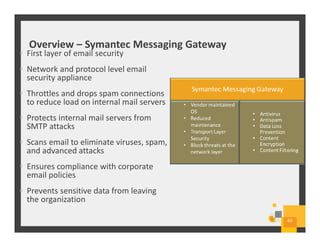
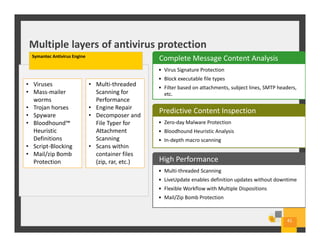
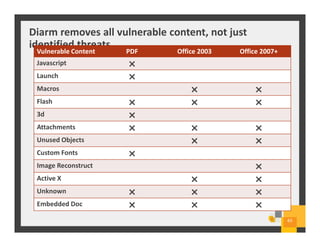
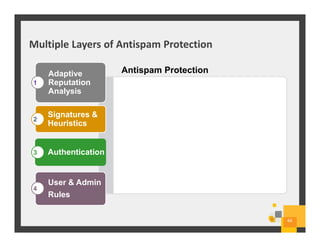
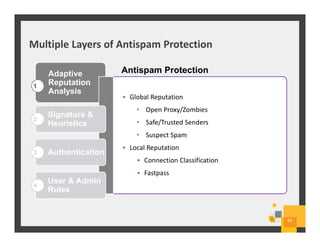
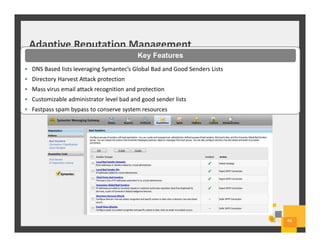
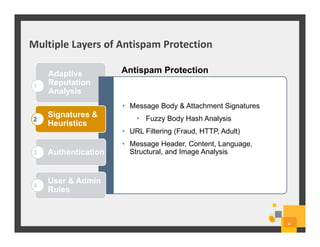
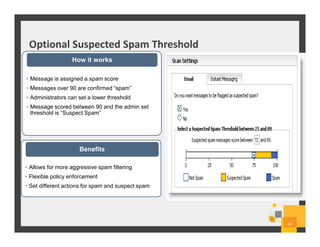
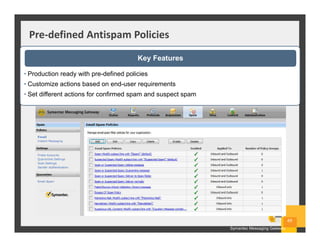
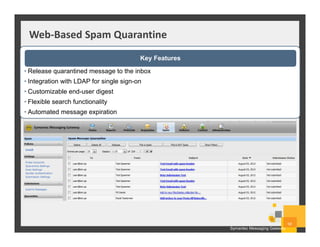
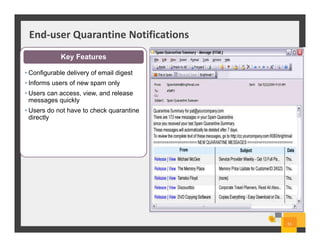
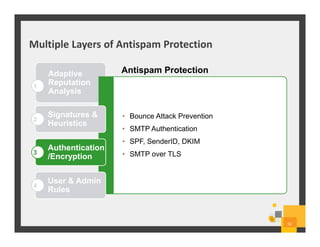
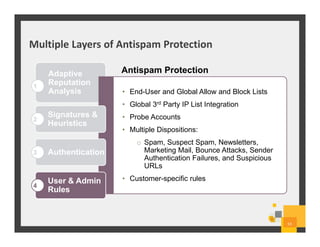
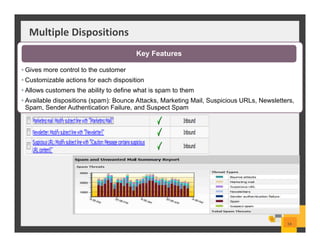
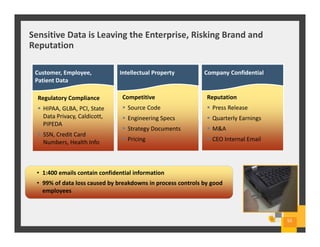
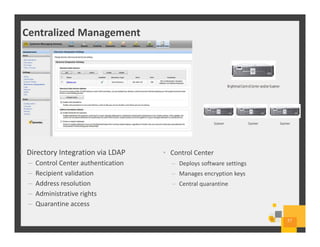
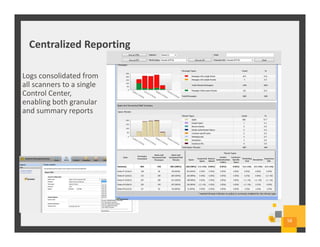
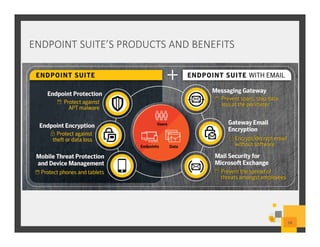
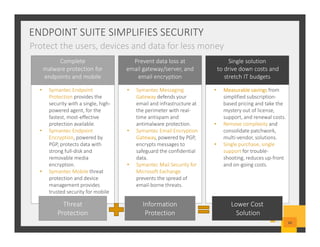
The document summarizes Symantec Endpoint Suite, which includes several security products that provide layered protection for endpoints, email, and mobile devices. It discusses Symantec Endpoint Protection for antivirus and antimalware on endpoints, Symantec Endpoint Encryption for data encryption, Symantec Mobile Threat Protection and Management for mobile security, and Symantec Messaging Gateway for email security. The suite aims to simplify security management and reduce costs through an integrated platform that protects against threats, data loss, and reduces complexity.