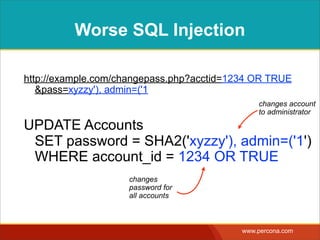
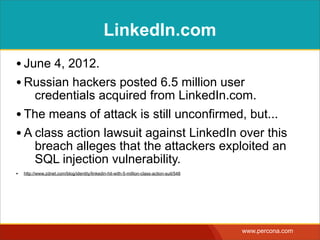
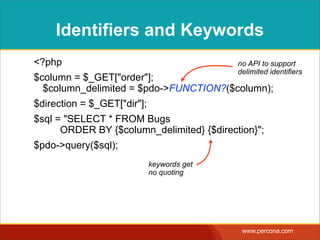
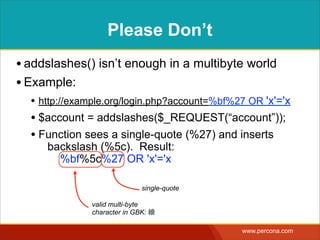
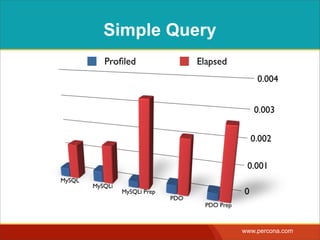
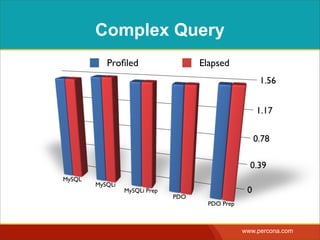
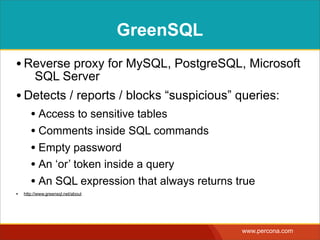
The document discusses various myths and misconceptions surrounding SQL injection vulnerabilities, emphasizing that such issues remain relevant and can lead to significant security breaches, as seen in real-world cases. It details common fallacies, such as the belief that escaping input alone prevents SQL injection, and highlights that effective defenses require comprehensive strategies that combine various methodologies. Ultimately, it warns against relying too heavily on any single solution, advocating for a thorough understanding of SQL security practices.


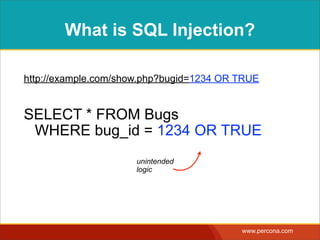
![WHAT IS SQL INJECTION?
http://example.com/show.php?bugid=1234
SELECT * FROM Bugs
WHERE bug_id = $_GET['bugid']
user input](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-3-320.jpg)
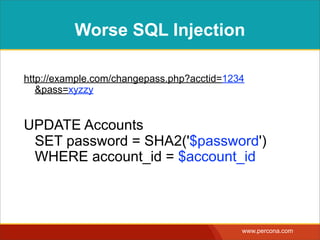






![ESCAPING & FILTERING
FUNCTIONS
<?php
$password = $_POST["password"];
$password_escaped = mysqli_real_escape_string($password);
$id = (int) $_POST["account"];
$sql = "UPDATE Accounts
SET password = SHA2(‘{$password_escaped}’)
WHERE account_id = {$id}";
mysql_query($sql);](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-14-320.jpg)
![ESCAPING & FILTERING
FUNCTIONS
<?php
$password = $_POST["password"];
$password_quoted = $pdo->quote($password);
$id = filter_input(INPUT_POST, "account",
FILTER_SANITIZE_NUMBER_INT);
$sql = "UPDATE Accounts
SET password = SHA2( {$password_quoted} )
WHERE account_id = {$id}";
$pdo->query($sql);](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-15-320.jpg)
![IDENTIFIERS AND KEYWORDS
<?php
$column = $_GET["order"];
$column_delimited = $pdo->FUNCTION?($column);
$direction = $_GET["dir"];
$sql = "SELECT * FROM Bugs
ORDER BY {$column_delimited} {$direction}";
$pdo->query($sql);
no API to support
delimited identifiers
keywords get no
quoting](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-16-320.jpg)
![OVERKILL?
<?php
function sanitize($string){
$string = strip_tags($string);
$string = htmlspecialchars($string);
$string = trim(rtrim(ltrim($string)));
$string = mysql_real_escape_string($string);
return $string;
}
$password = sanitize( $_POST["password"] );
real function from
a user’s project](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-18-320.jpg)

![JUSTTHE ONE WILL DO
<?php
$password = mysqli_real_escape_string(
$_POST["password"] );
mysqli_query("UPDATE Users
SET password = '$password'
WHERE user_id = $user_id");](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-20-320.jpg)







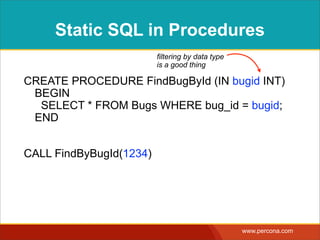
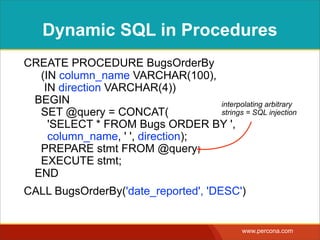
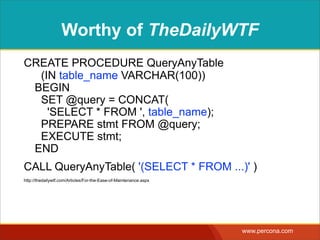



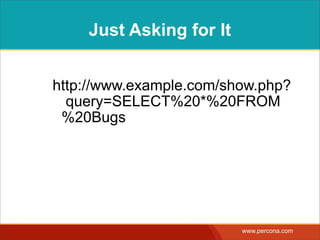


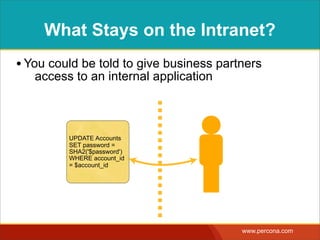
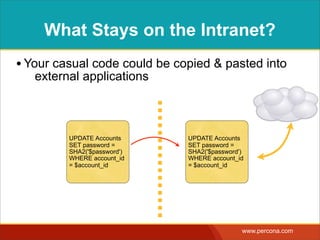
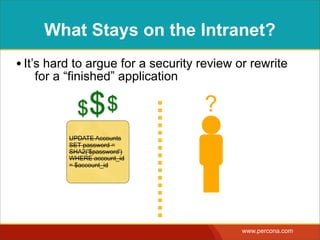



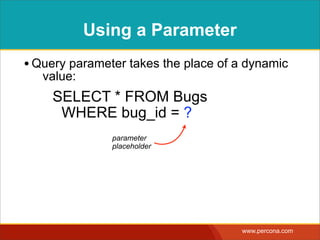
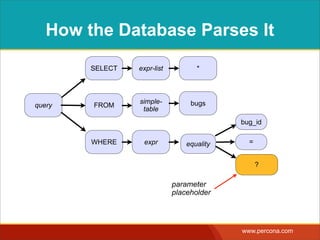
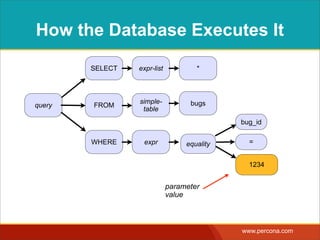
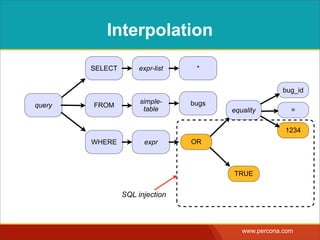
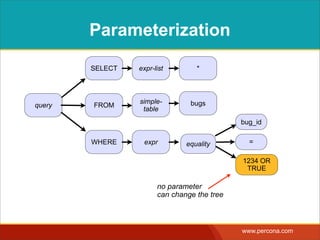
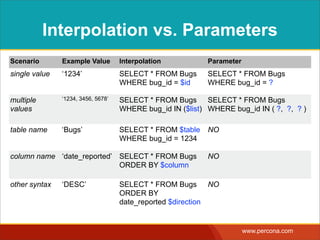
![INTERPOLATING DYNAMIC
VALUES
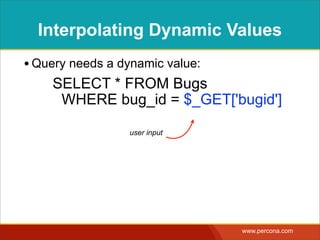
• Query needs a dynamic value:
SELECT * FROM Bugs
WHERE bug_id = $_GET['bugid']
user input](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-44-320.jpg)
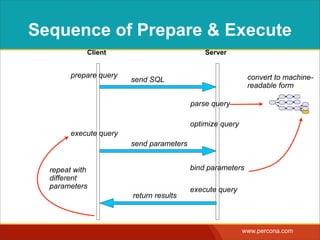





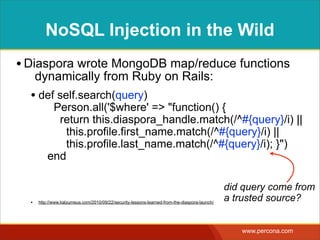
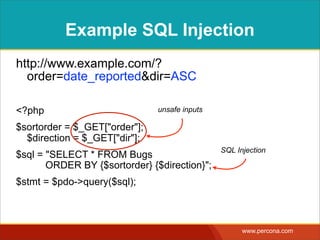
![EXAMPLE SQL INJECTION
http://www.example.com/?order=date_reported&dir=ASC
<?php
$sortorder = $_GET["order"];
$direction = $_GET["dir"];
$sql = "SELECT * FROM Bugs
ORDER BY {$sortorder} {$direction}";
$stmt = $pdo->query($sql);
unsafe inputs
SQL Injection](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-59-320.jpg)
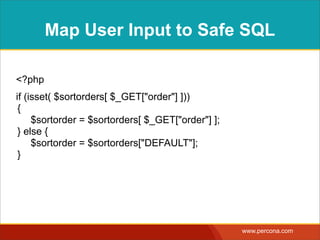
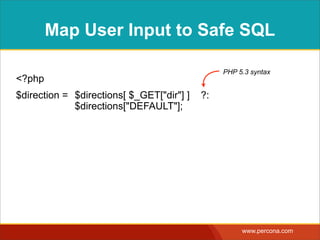
![MAP USER INPUTTO SAFE
SQL
<?php
$direction = $directions[ $_GET["dir"] ] ?: $directions["DEFAULT"];](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-61-320.jpg)





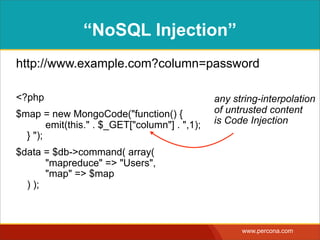
![“NOSQL INJECTION”
http://www.example.com?column=password
<?php
$map = new MongoCode("function() {
emit(this." . $_GET["column"] . ",1);
} ");
$data = $db->command( array(
"mapreduce" => "Users",
"map" => $map
) );
any string-interpolation of
untrusted content
is Code Injection](https://image.slidesharecdn.com/sqlinjectionmyths-100414230731-phpapp01/85/Sql-Injection-Myths-and-Fallacies-73-320.jpg)