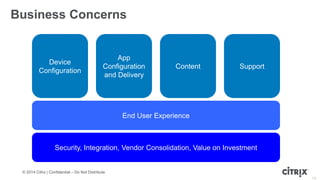
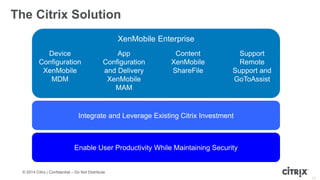
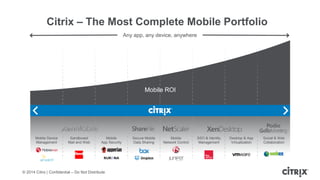
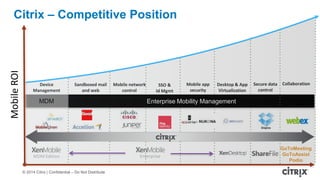
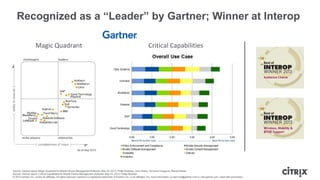
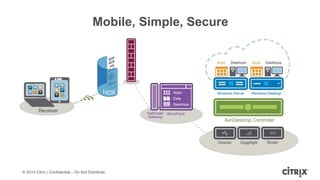
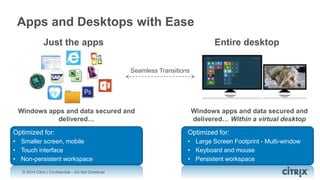
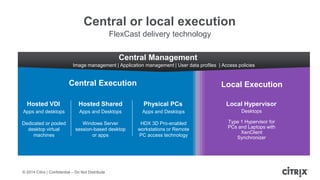
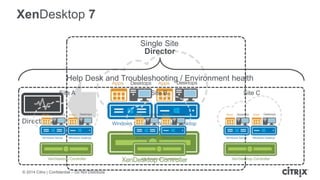
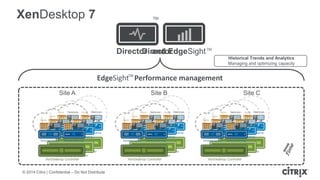
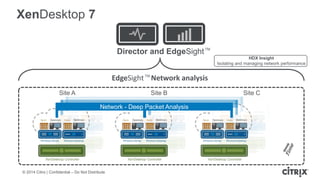
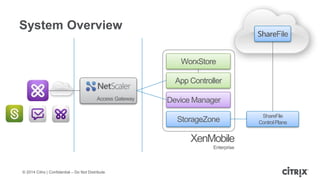
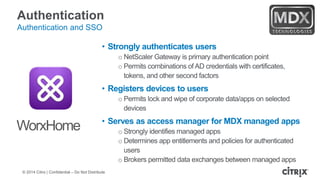
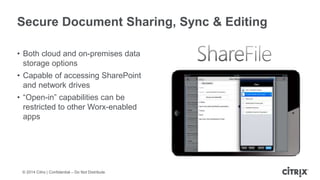
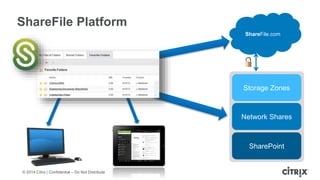
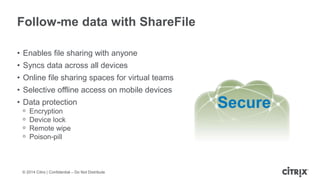
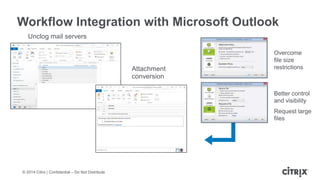
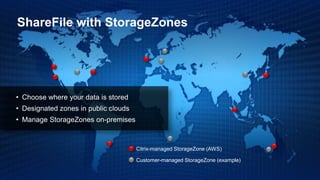
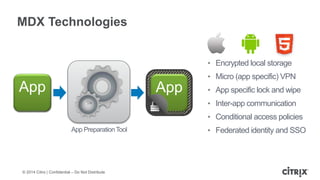
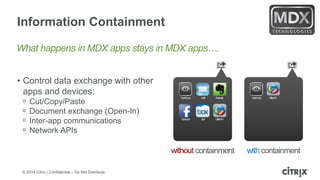
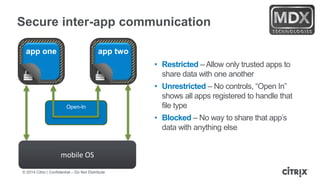
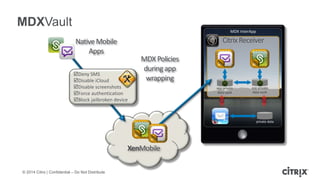
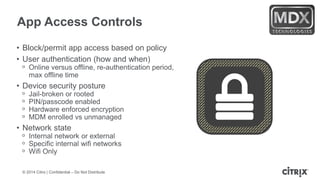
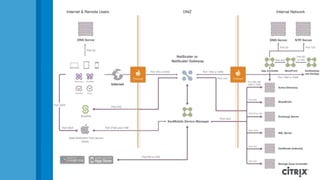
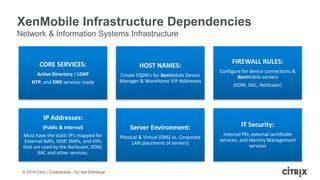
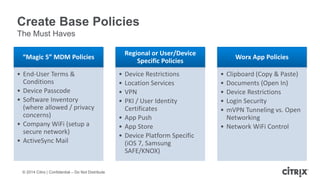
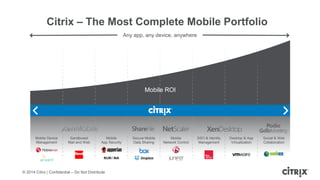
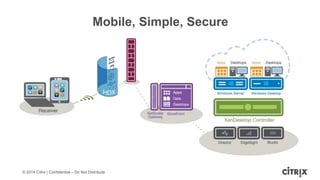
This document is a presentation by Todd Smith from Citrix about taking businesses and users to the cloud. It discusses how mobility trends like BYOD and the rise of tablets are changing the workplace. It also covers challenges of managing security and complexity across many devices and apps. The presentation promotes Citrix's mobile solutions including XenMobile for mobile device management, secure apps and data sharing with ShareFile, and single sign-on capabilities. It positions Citrix as providing the most comprehensive mobile portfolio to enable secure productivity from any device.