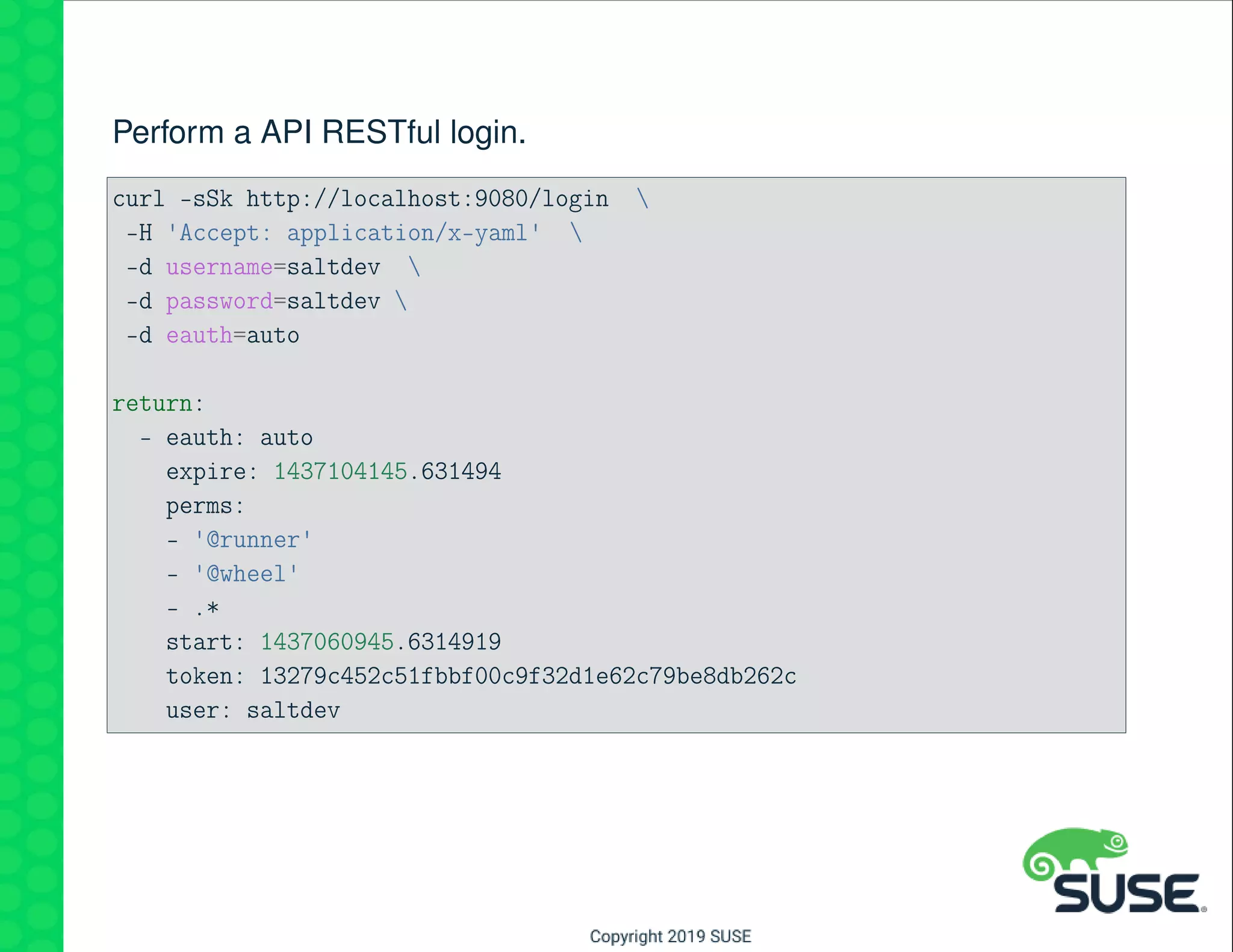
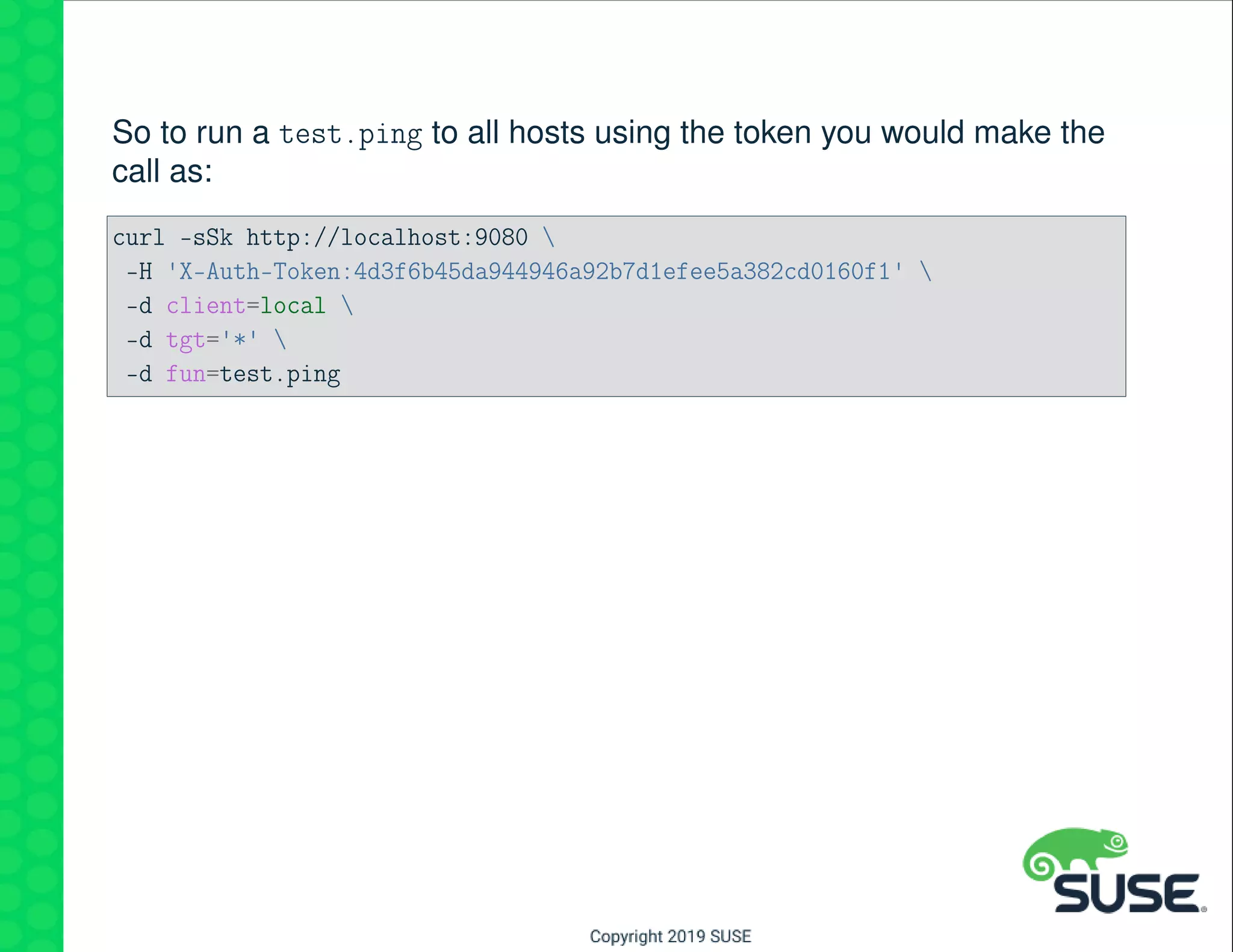
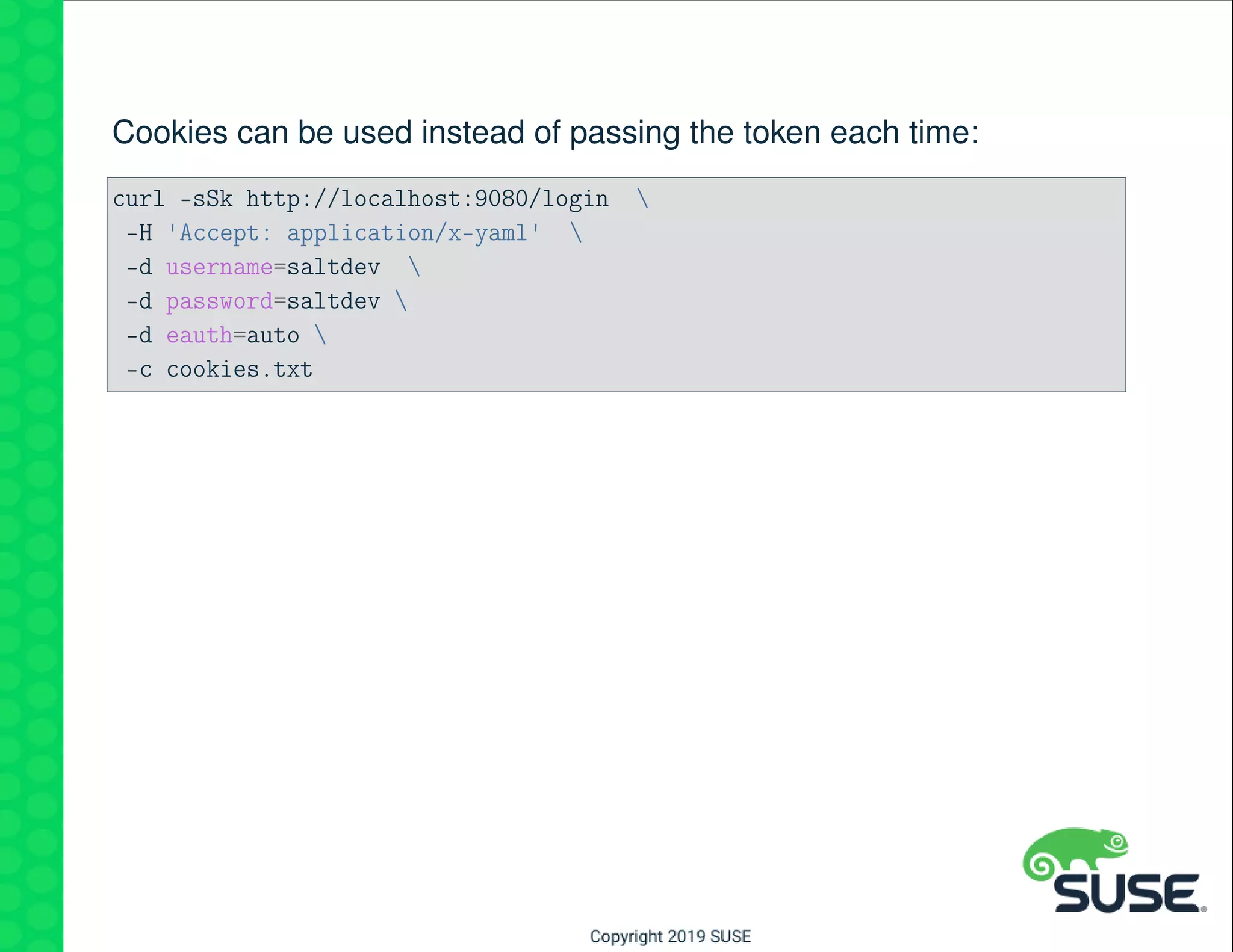
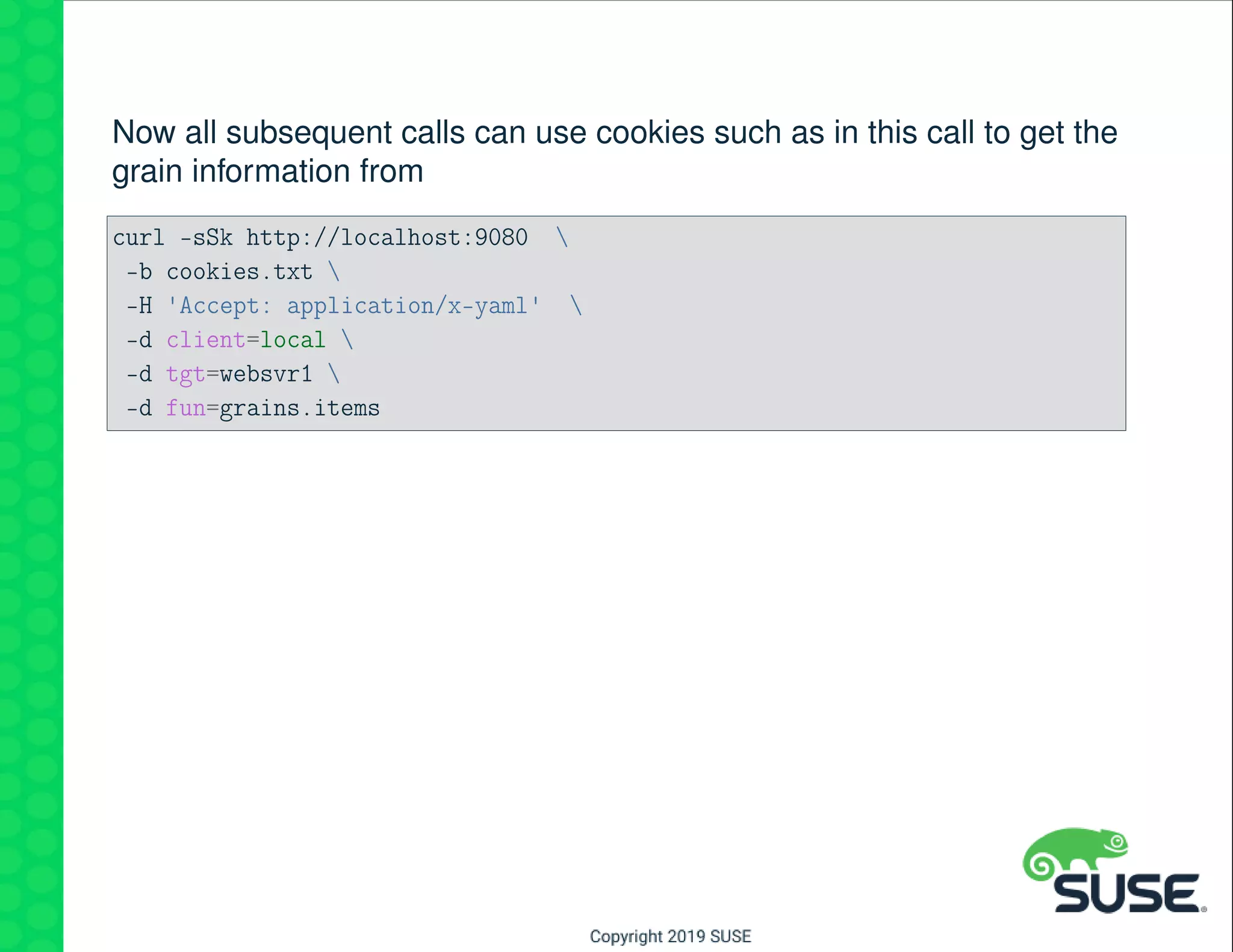
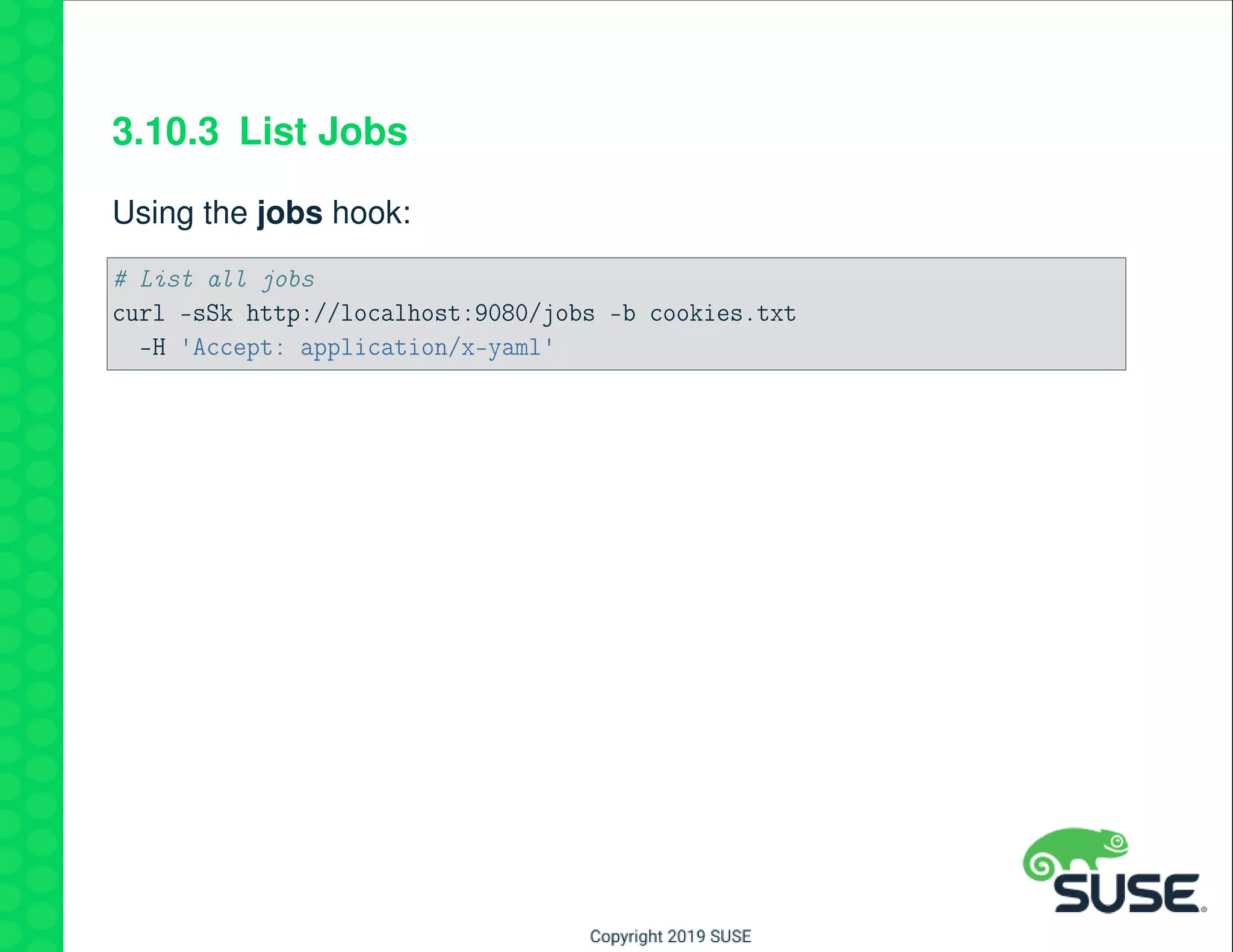
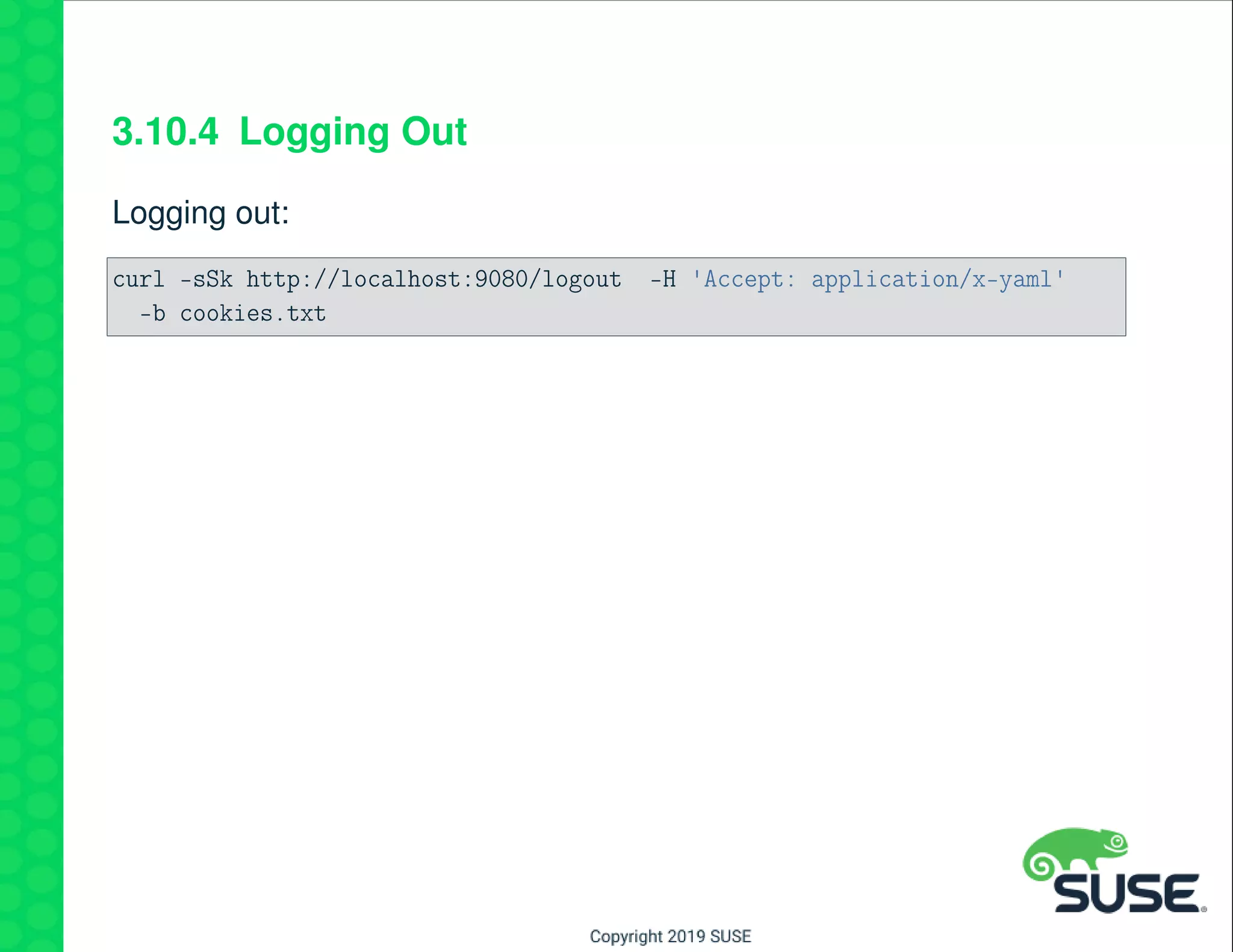
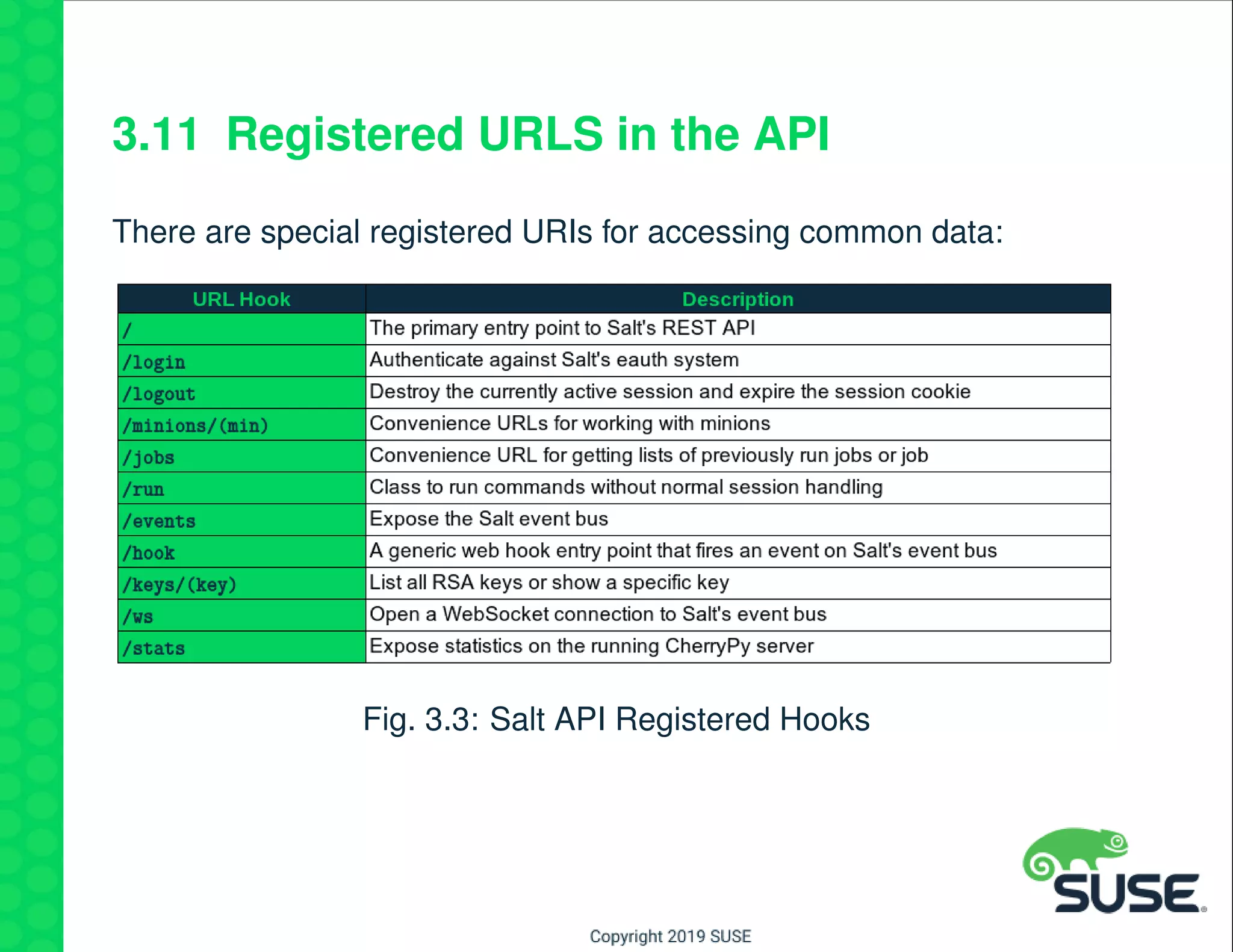
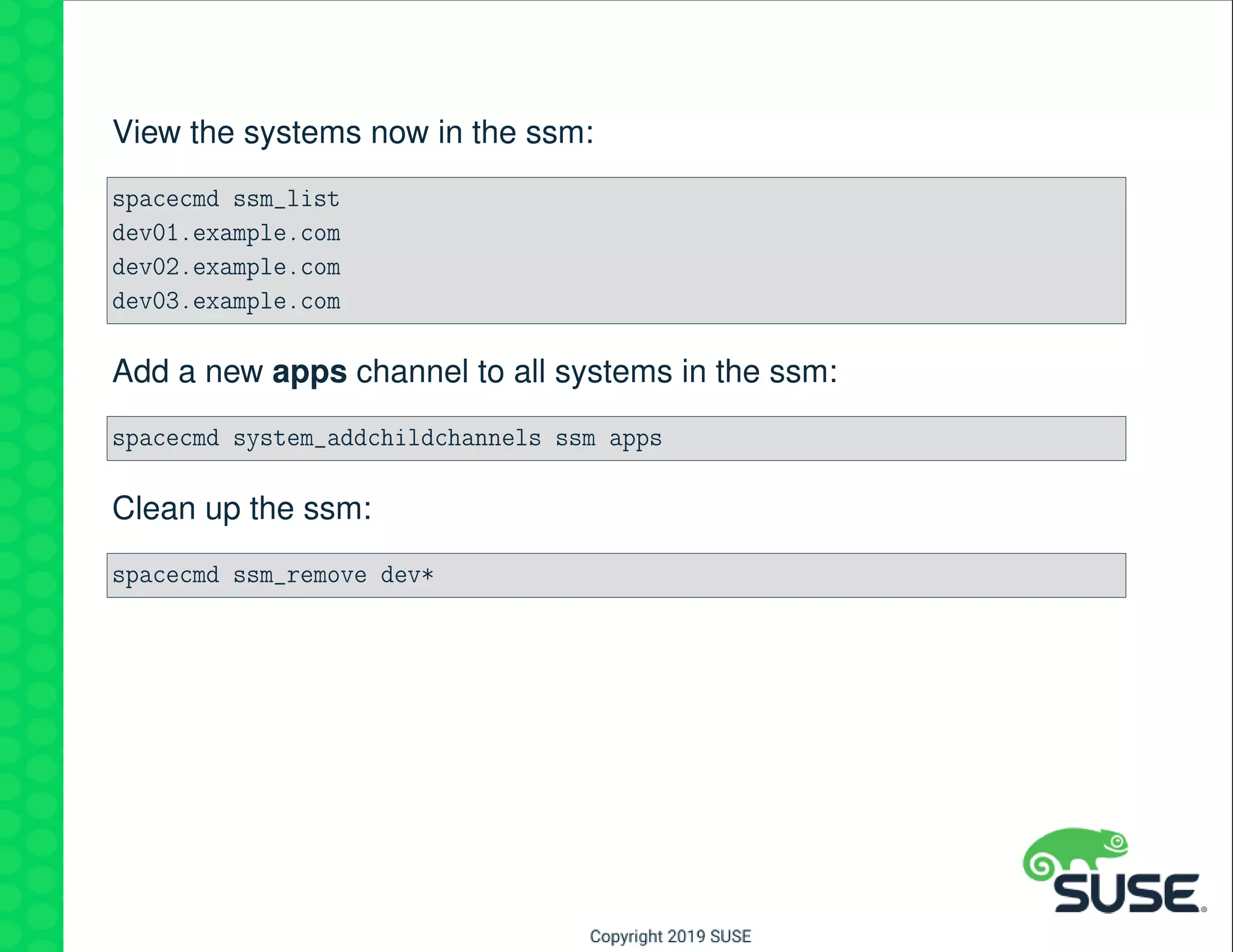
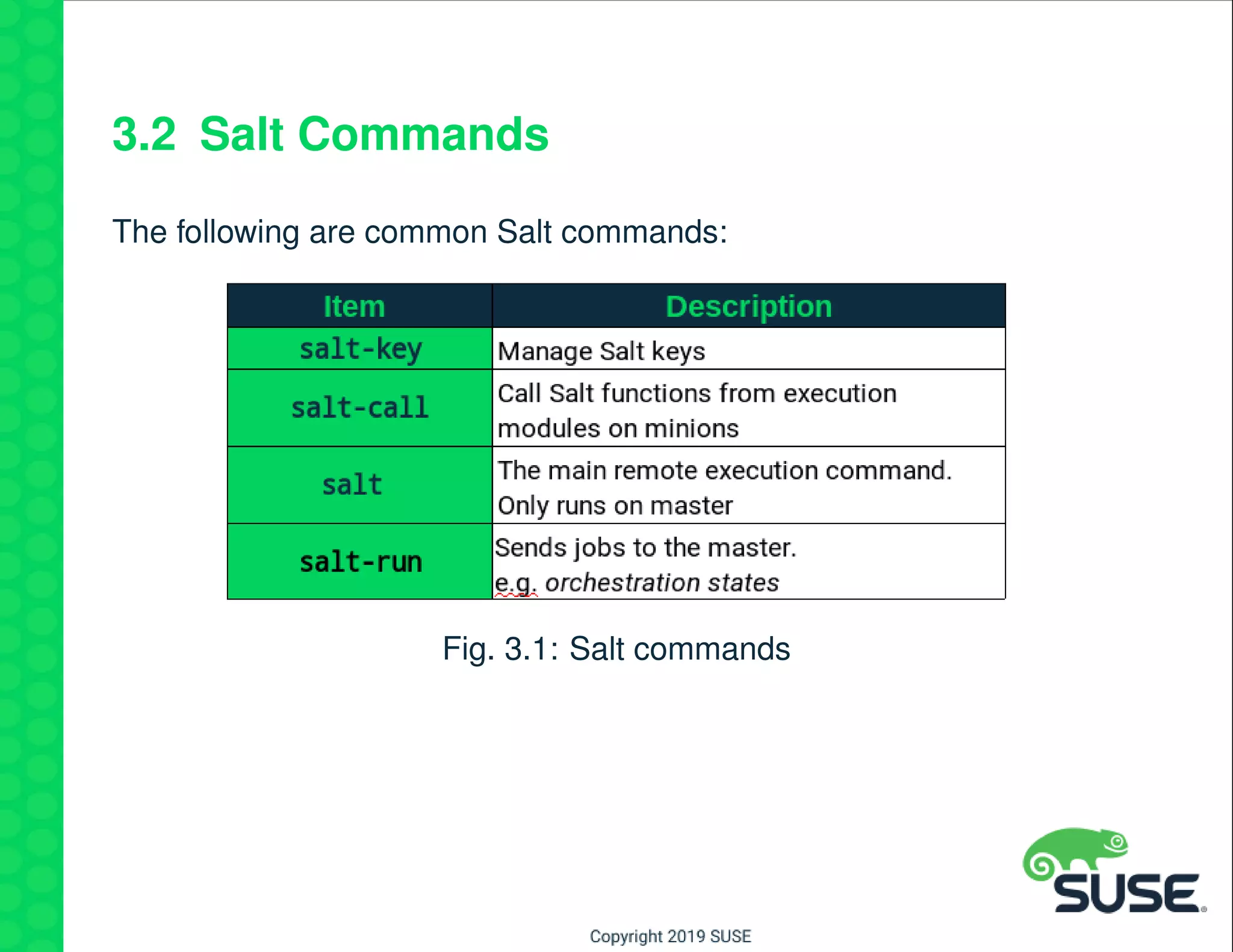
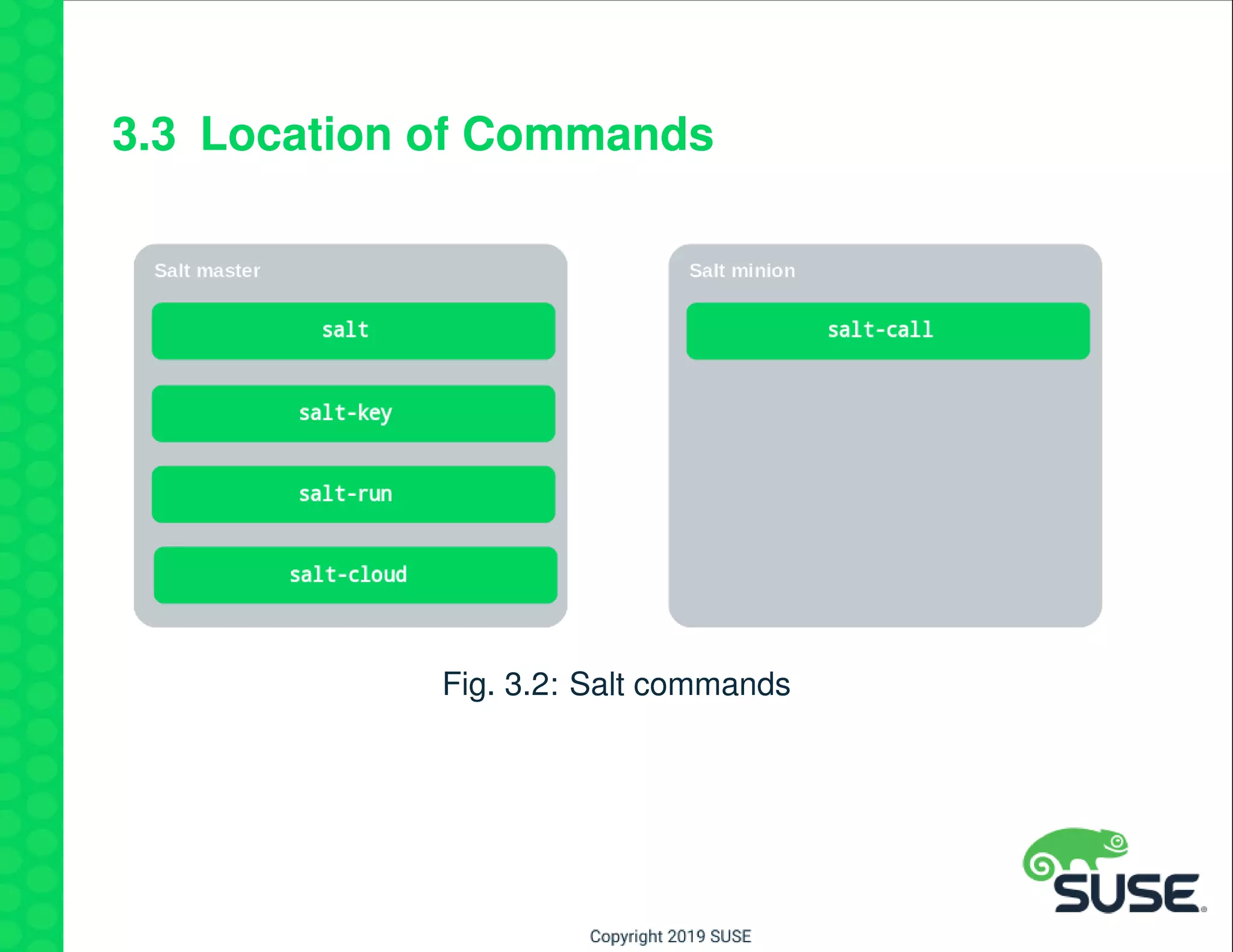
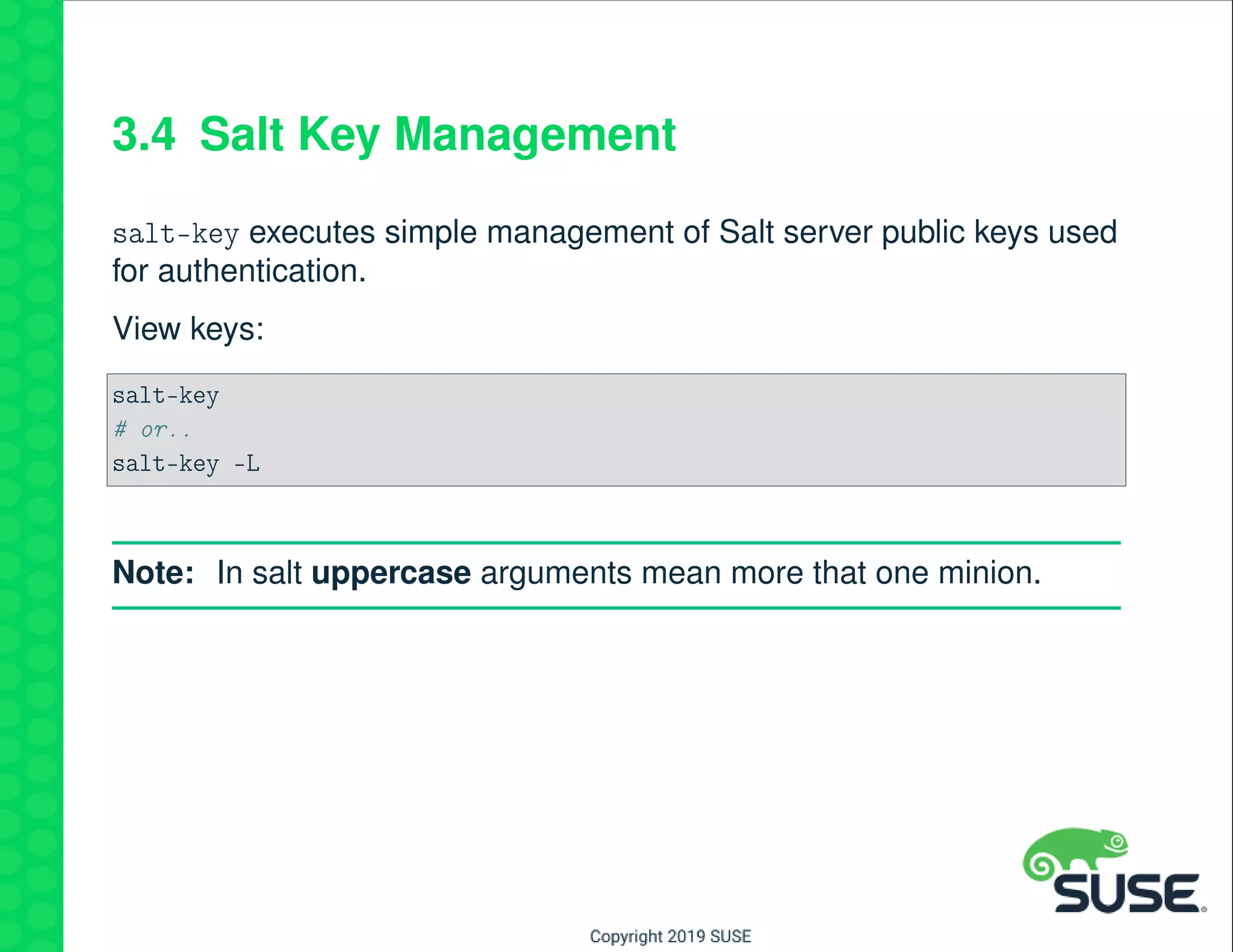
The document outlines best practices for managing a software-defined datacenter using SUSE Manager and Salt, emphasizing automated maintenance and configuration management. Key topics include patching lifecycle management, API usage, state channels, and the Salt REST API for enhanced automation. It provides practical examples of command-line operations for managing systems and emphasizes the importance of organized software channel management.








![3.5 Sending Commands to Minions
Instead of logging to to each system, a salt module may be run on
many systems simultaneously from the Salt master.
Remote execution in salt is performed with the salt command.
The syntax is:
salt [options] '<target>' <module.function> [arguments|keyword arguments]
An example of targeting minions:
salt '*' cmd.run 'cat /etc/resolv.conf'](https://image.slidesharecdn.com/cas1172softwaredefineddatacentermaintenancenomoresleeplessnightsandlongweekendswhendoingmaintenance-190628093029/75/Software-defined-Datacenter-Maintenance-No-More-Sleepless-Nights-and-Long-Weekends-When-Doing-Maintenance-25-2048.jpg)