The document discusses the security risks associated with social media, particularly focusing on the context of Sri Lanka. It highlights key statistics regarding internet penetration, active Facebook users, and various security threats such as malware and privacy concerns. Recommendations for individuals and organizations on defending against these risks, including best practices for privacy settings and monitoring, are also provided.







![TMI
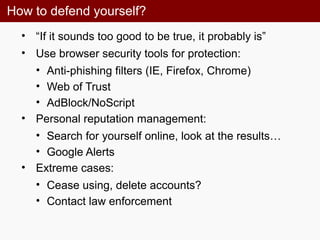
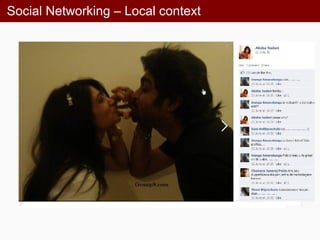
• Lack of common sense: it’s very difficult to delete
information after it’s been posted online
• Indiscreet information can adversely affect college
employment, your personal life, etc.
“Connor Riley: “Cisco just offered me a job! Now I have to weigh
the utility of a [big] paycheck against the daily commute to San
Jose and hating the work.”
• Location services, be careful when you check-in
• URL shortner services
• E.g. bit.ly](https://image.slidesharecdn.com/socialmediaandsecurityrisks-150224050918-conversion-gate01/85/Social-media-and-Security-risks-21-320.jpg)