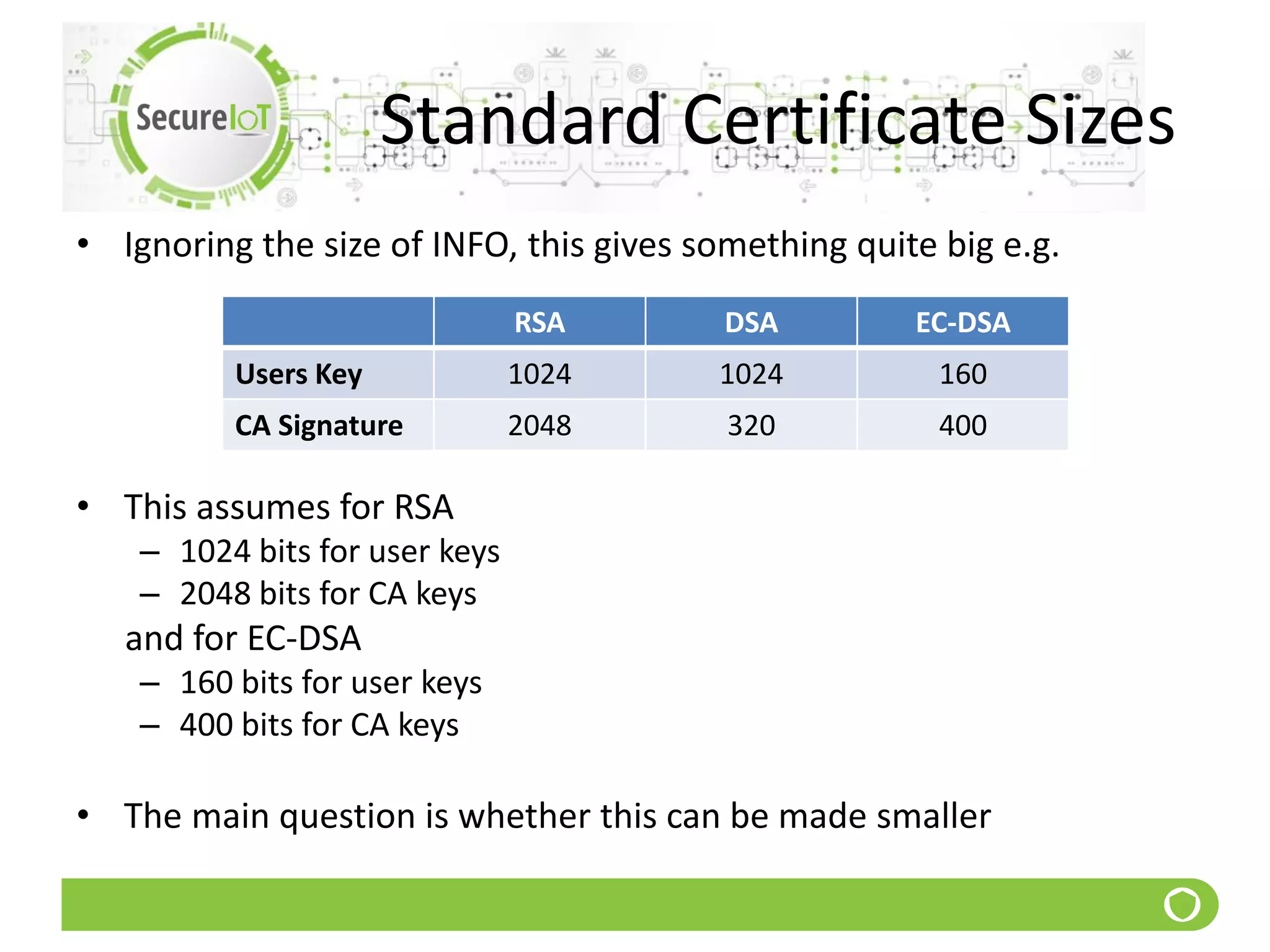
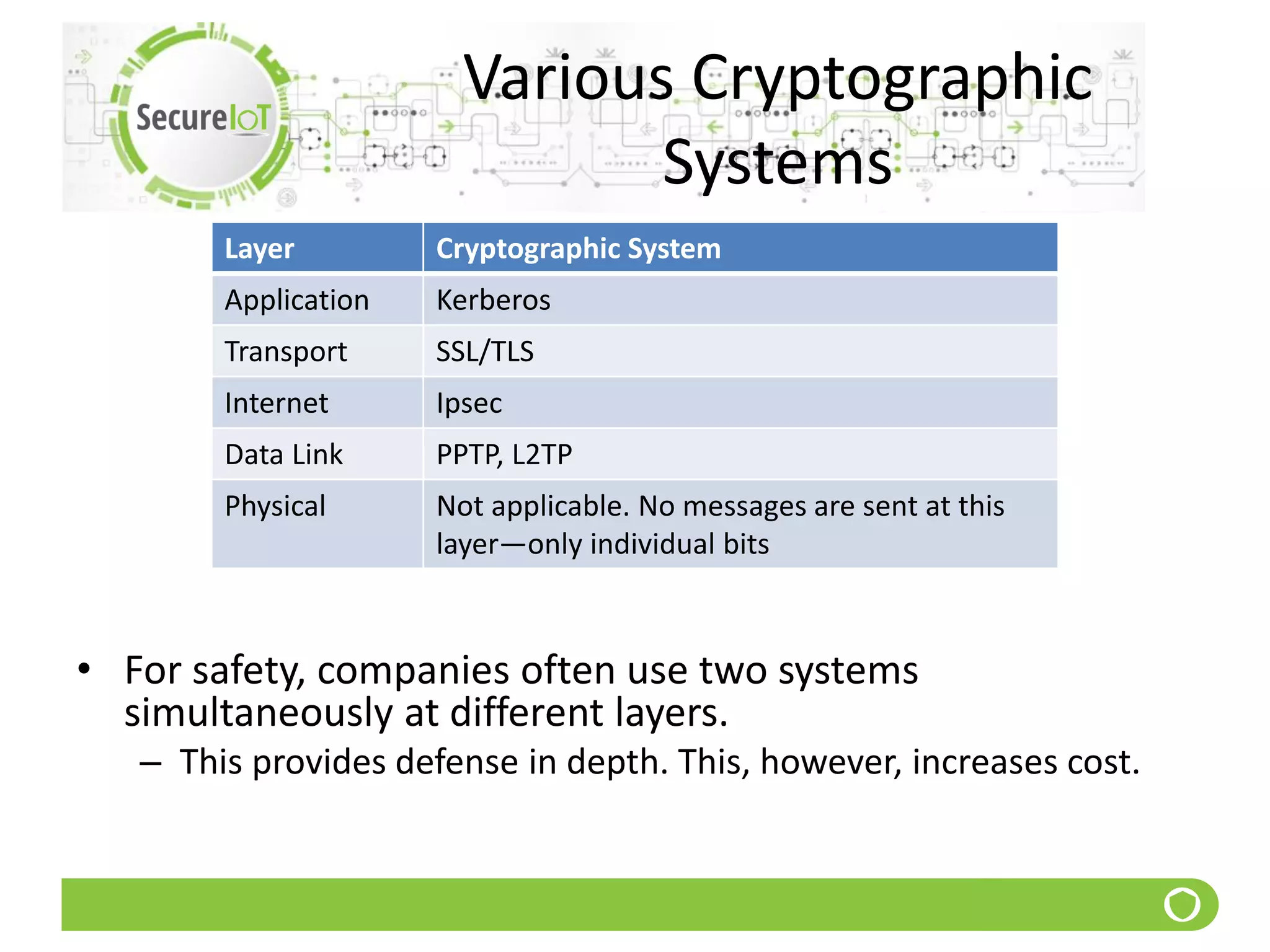
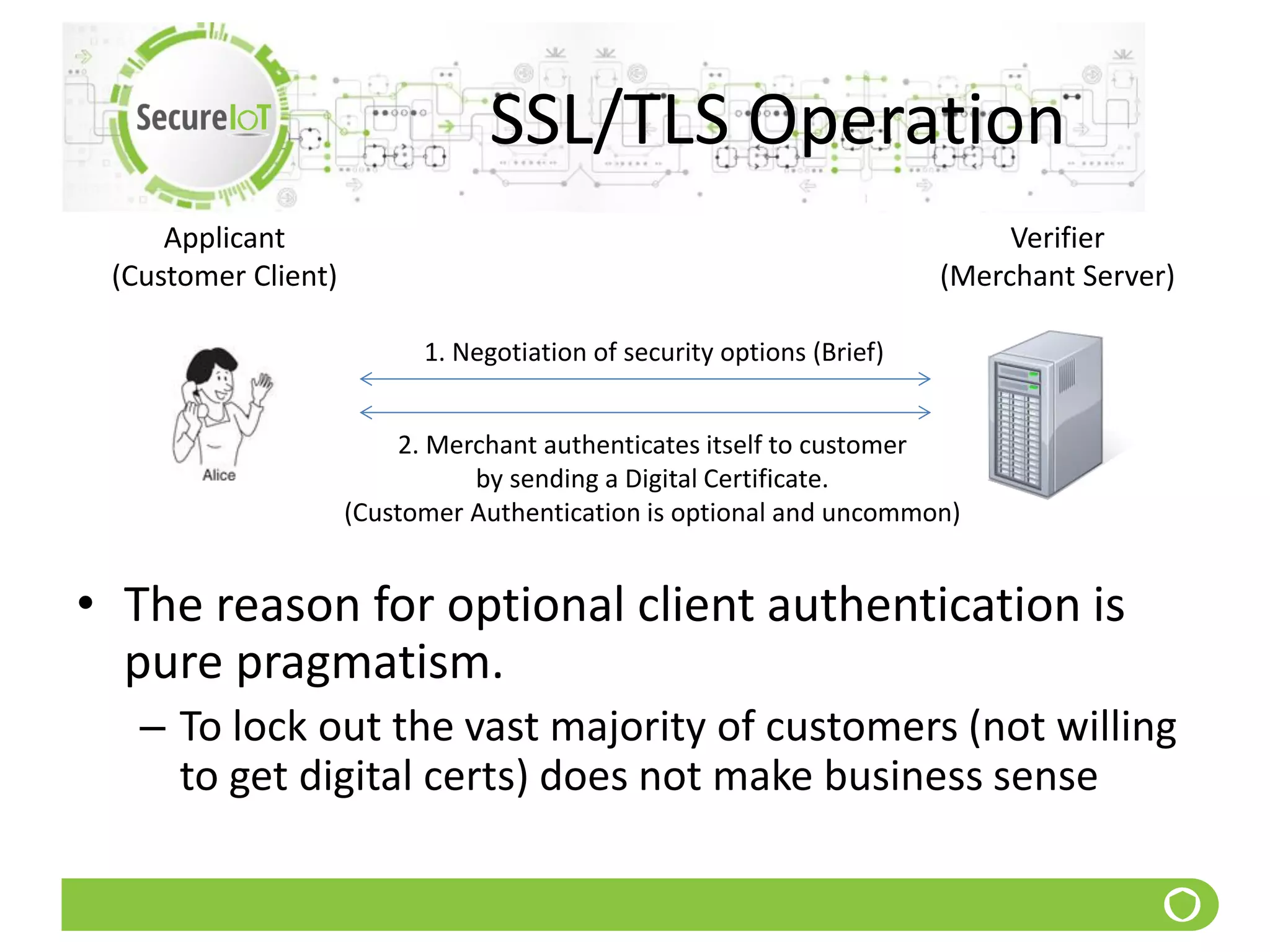
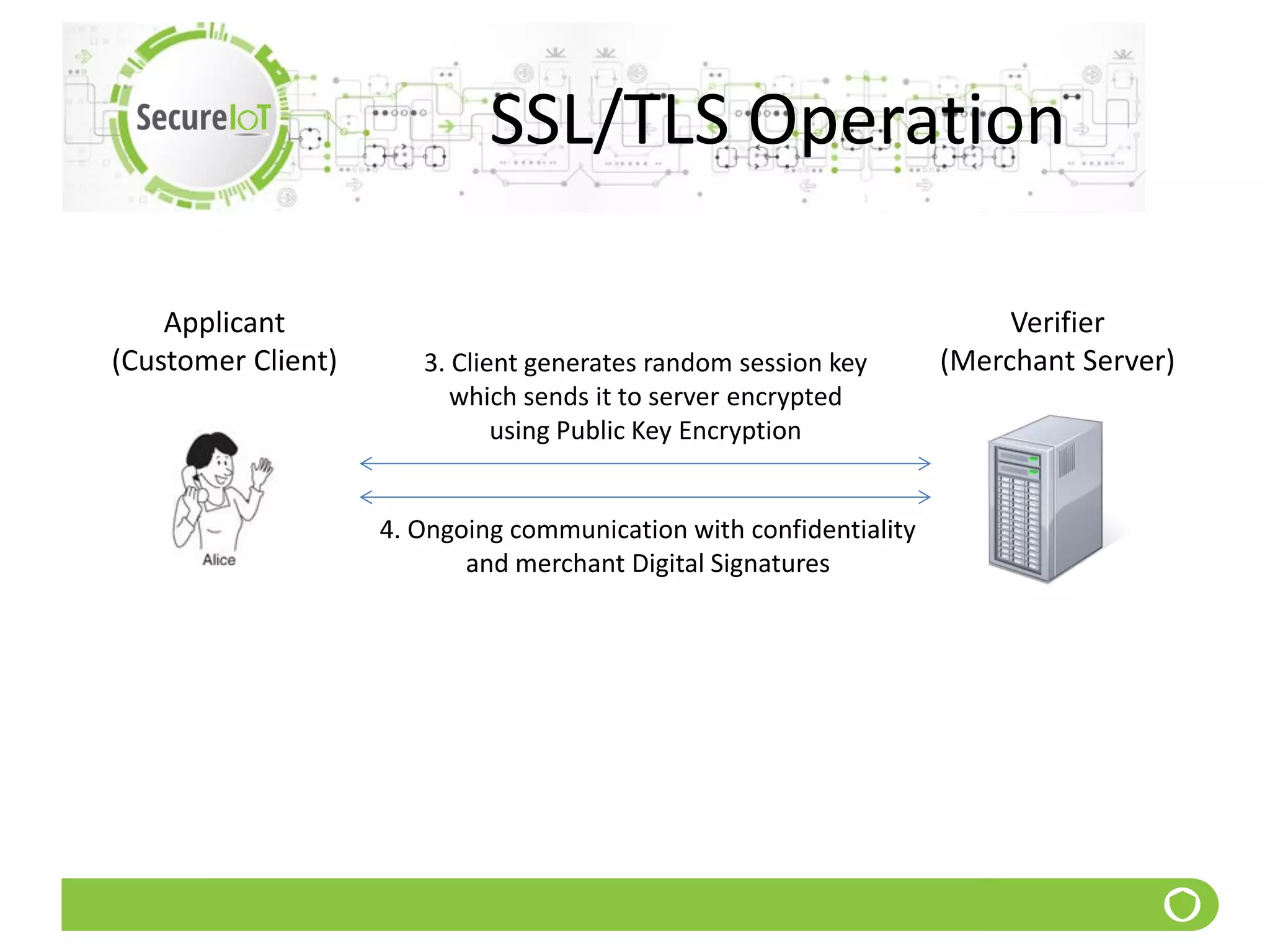
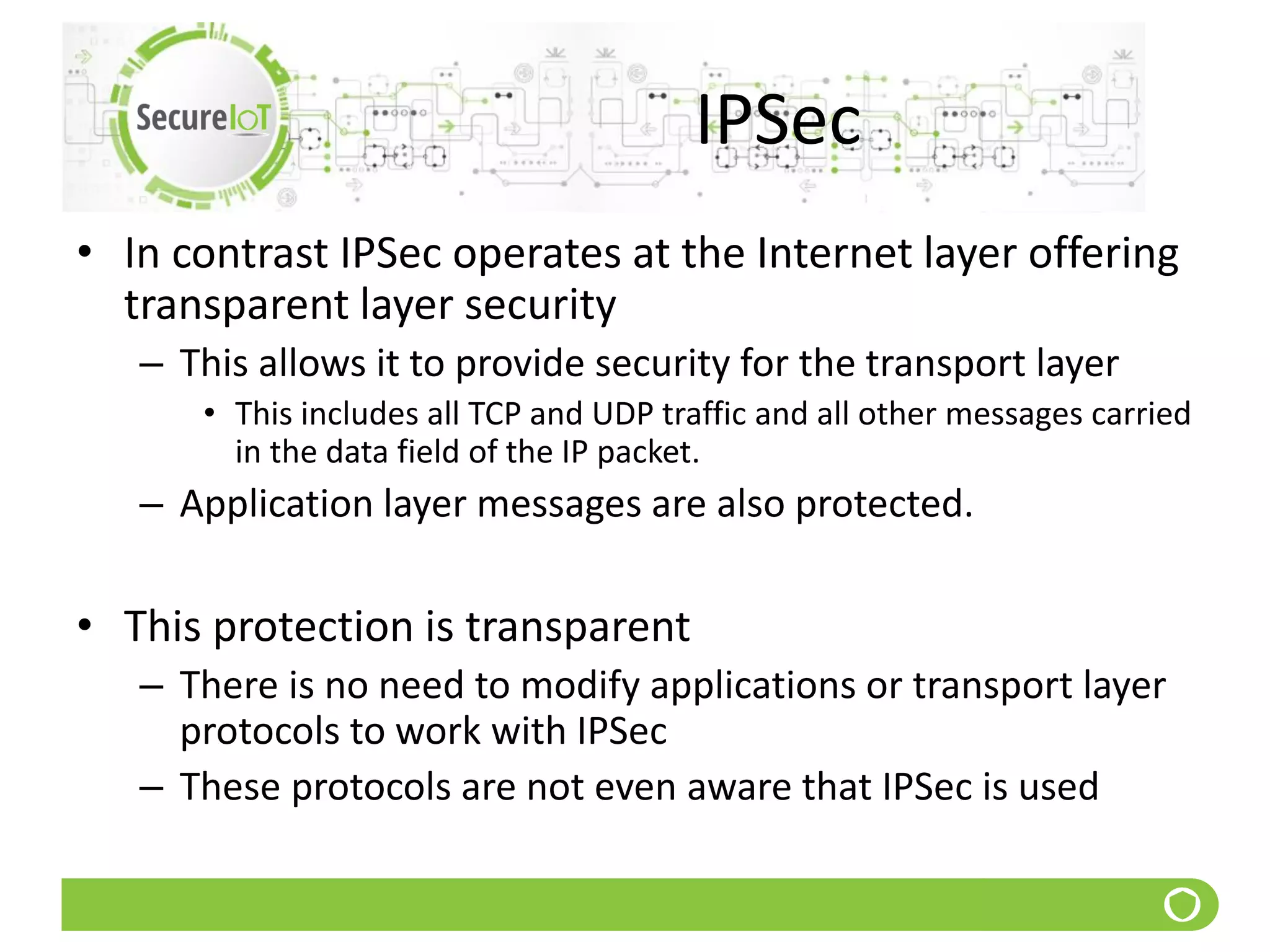
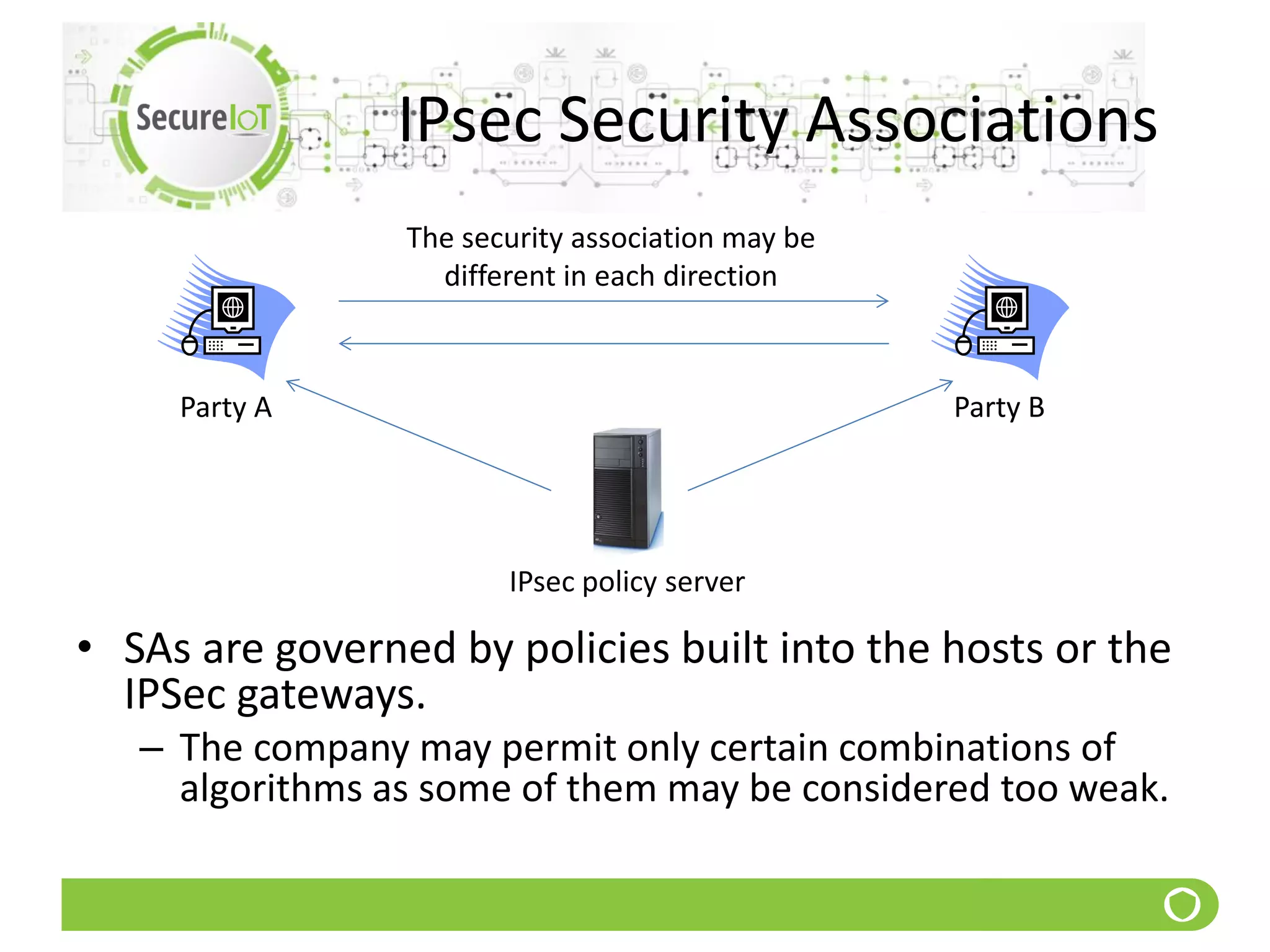
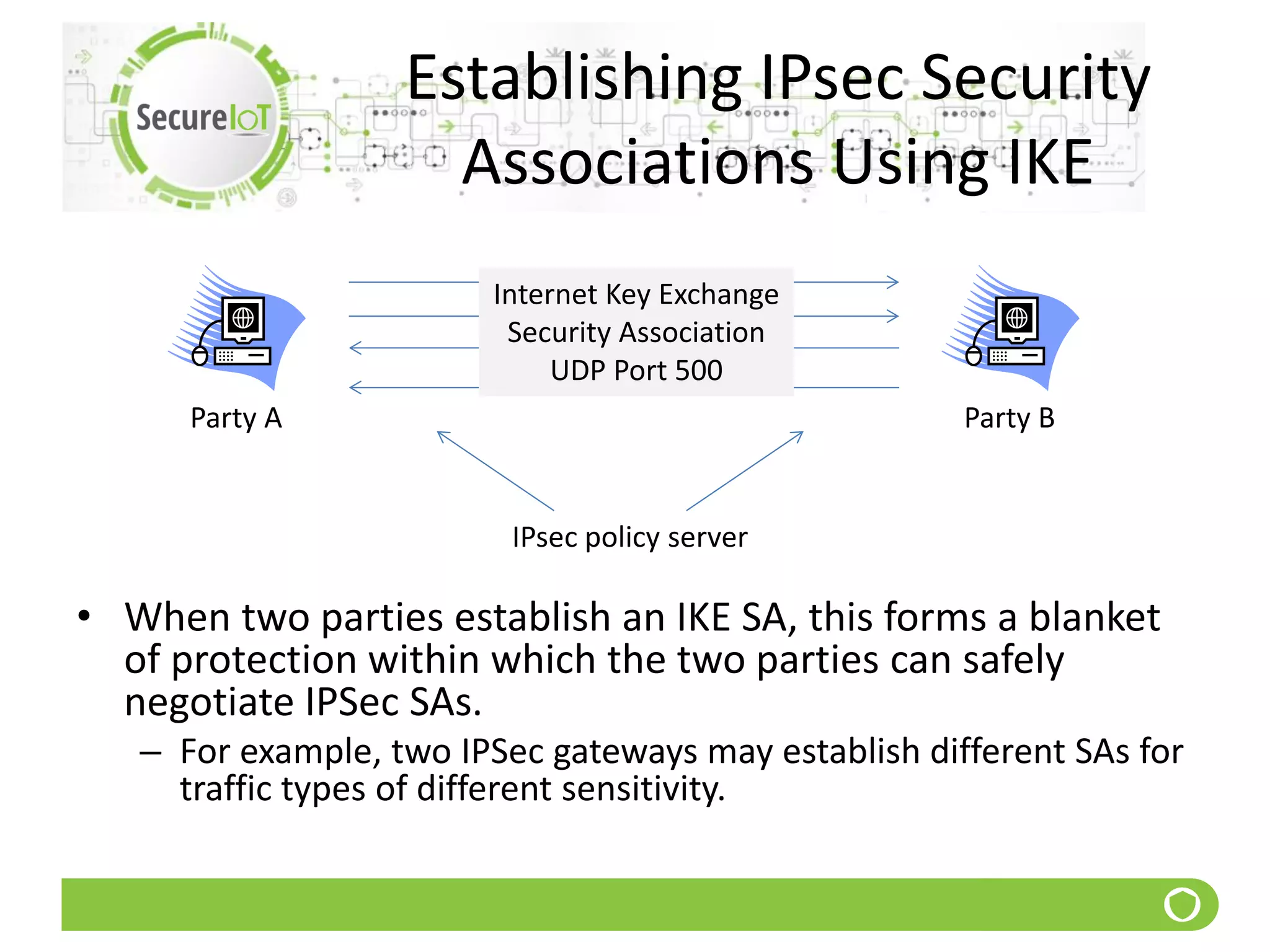
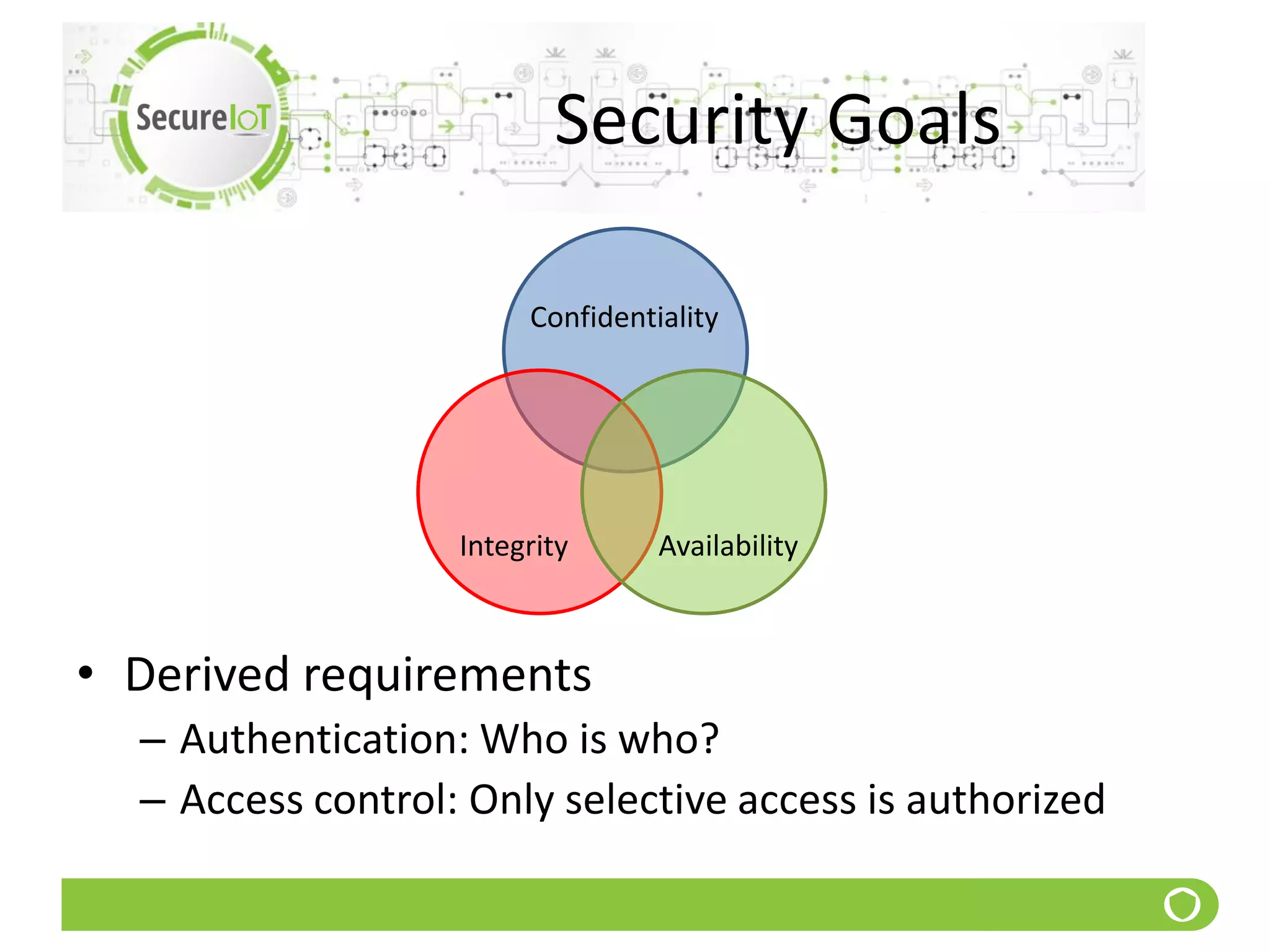
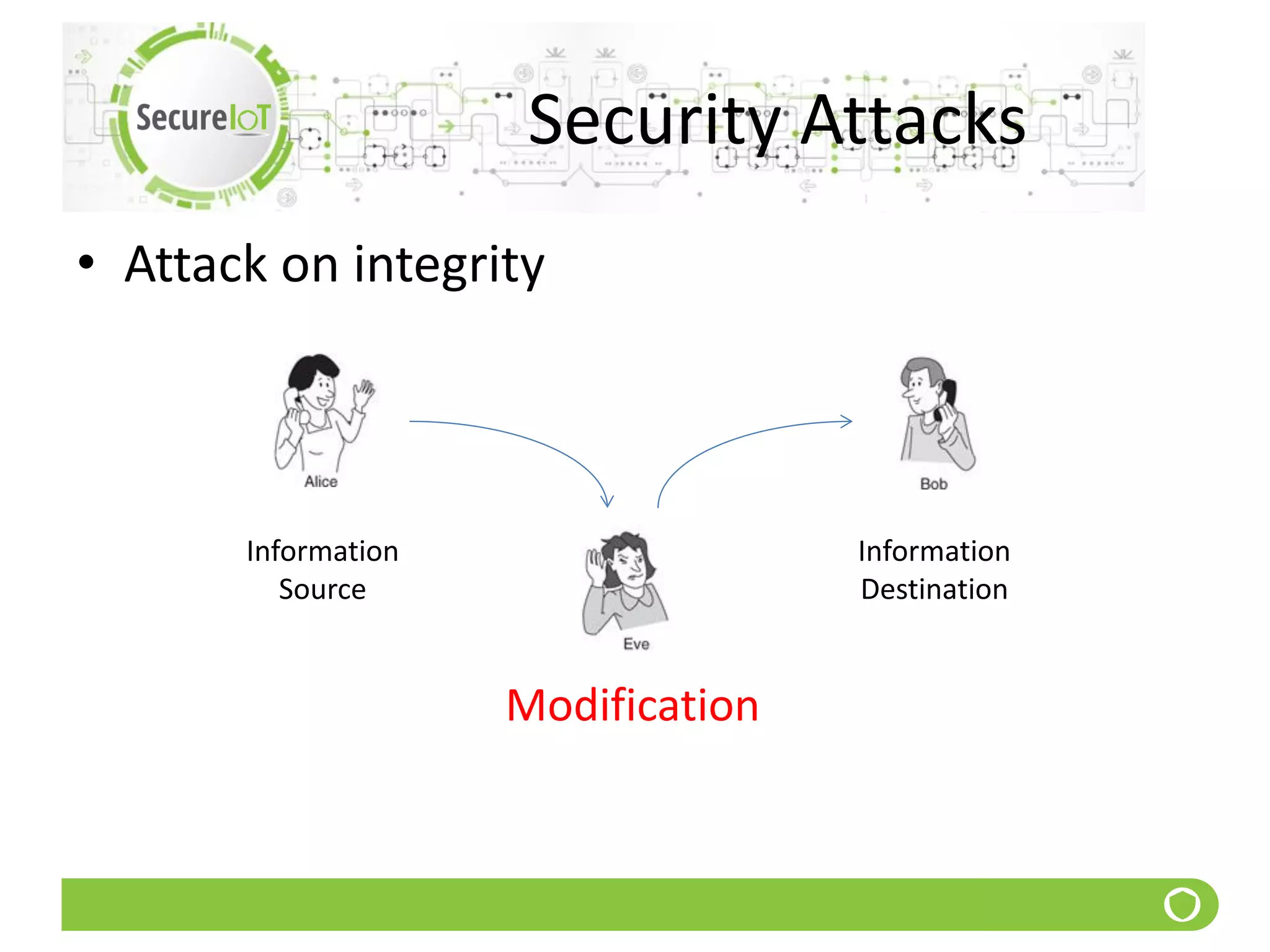
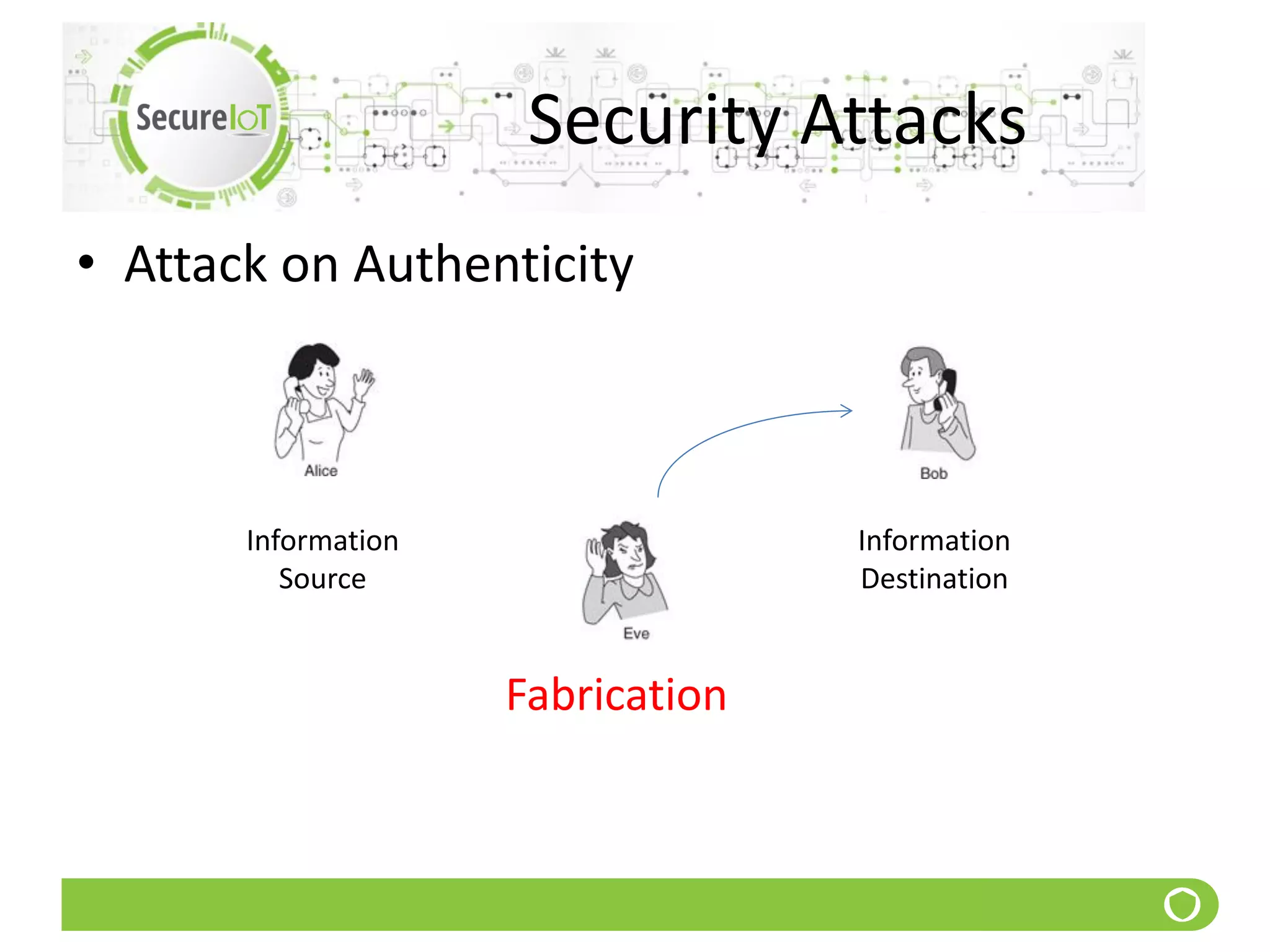
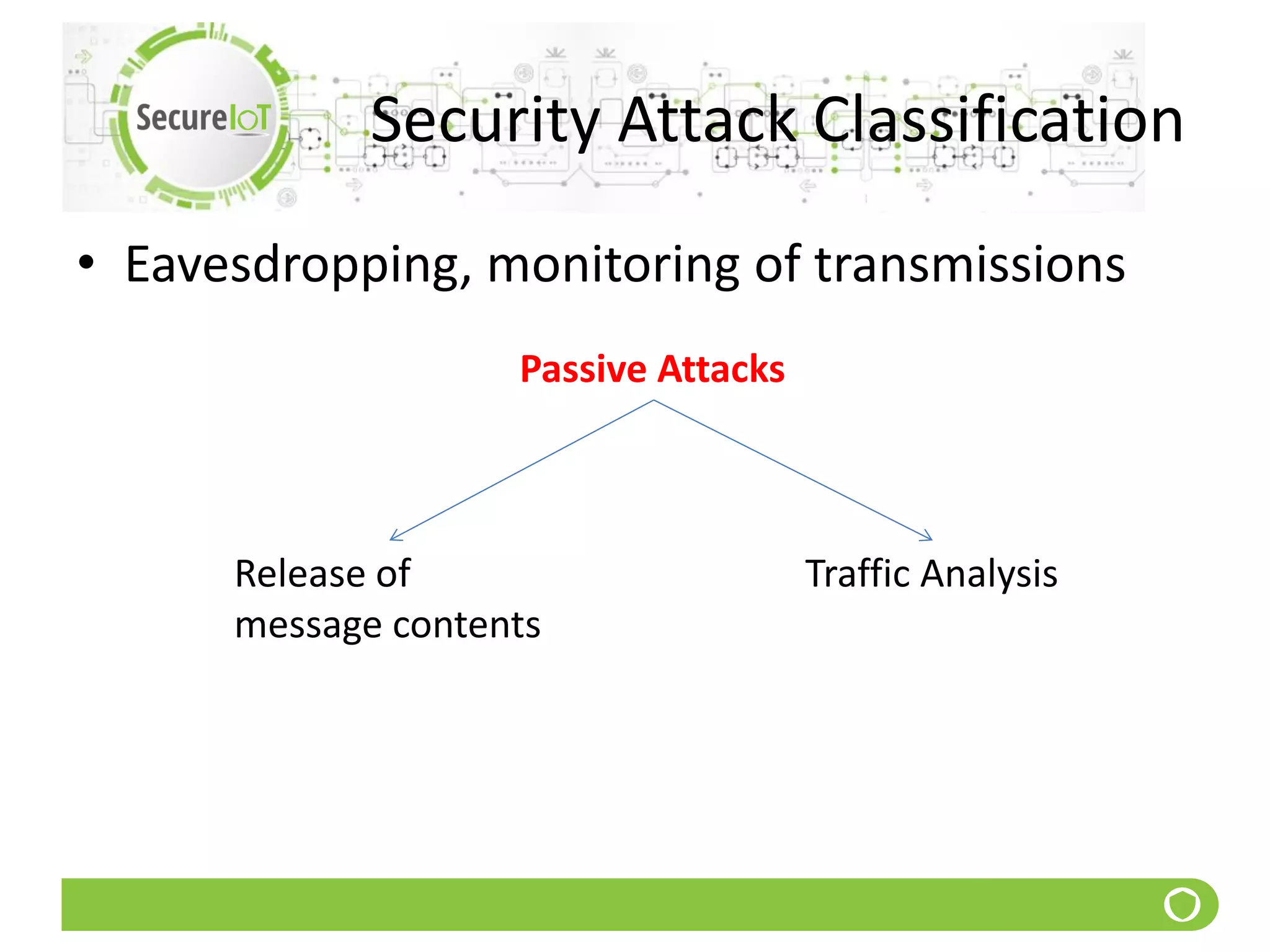
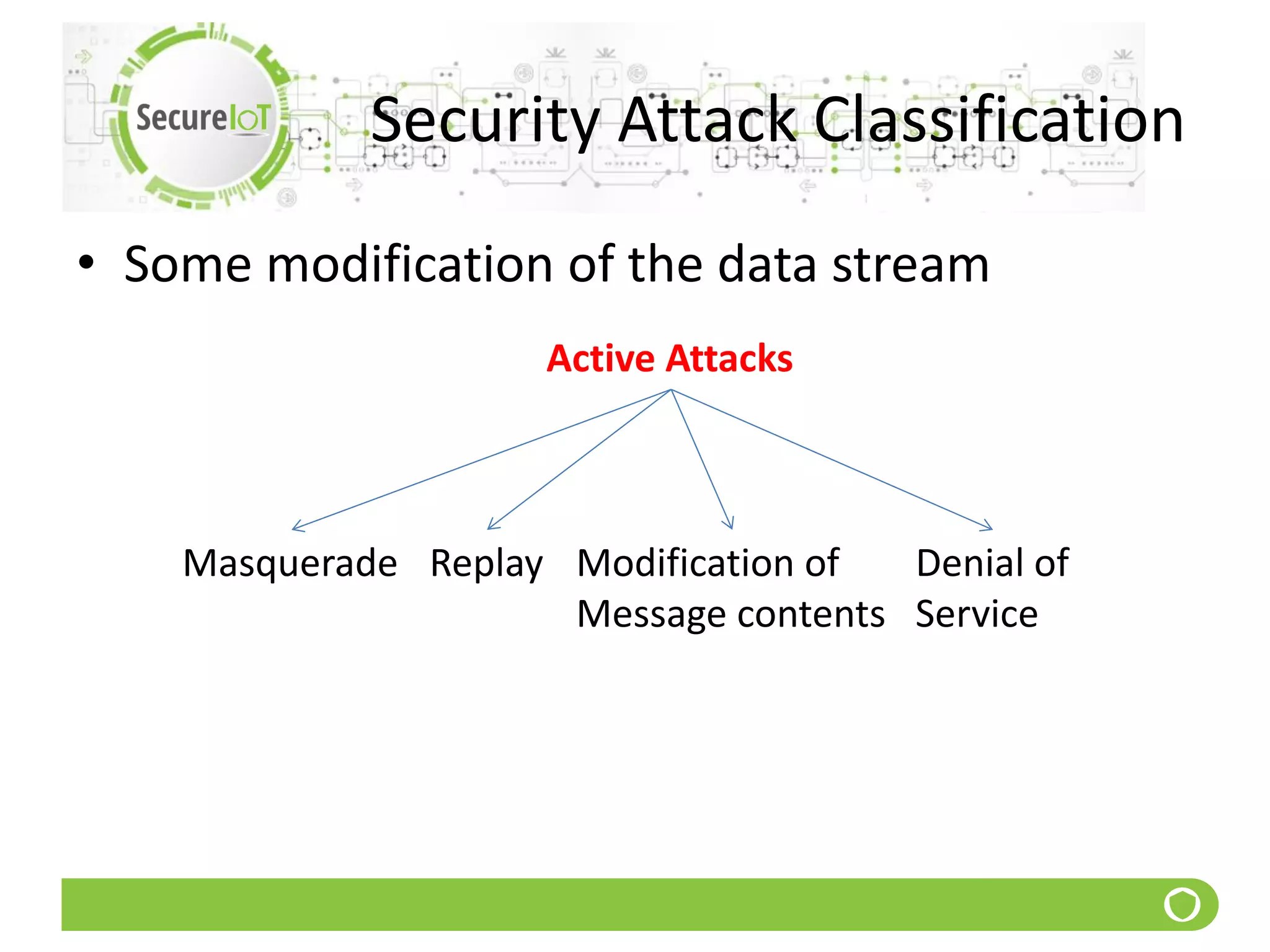
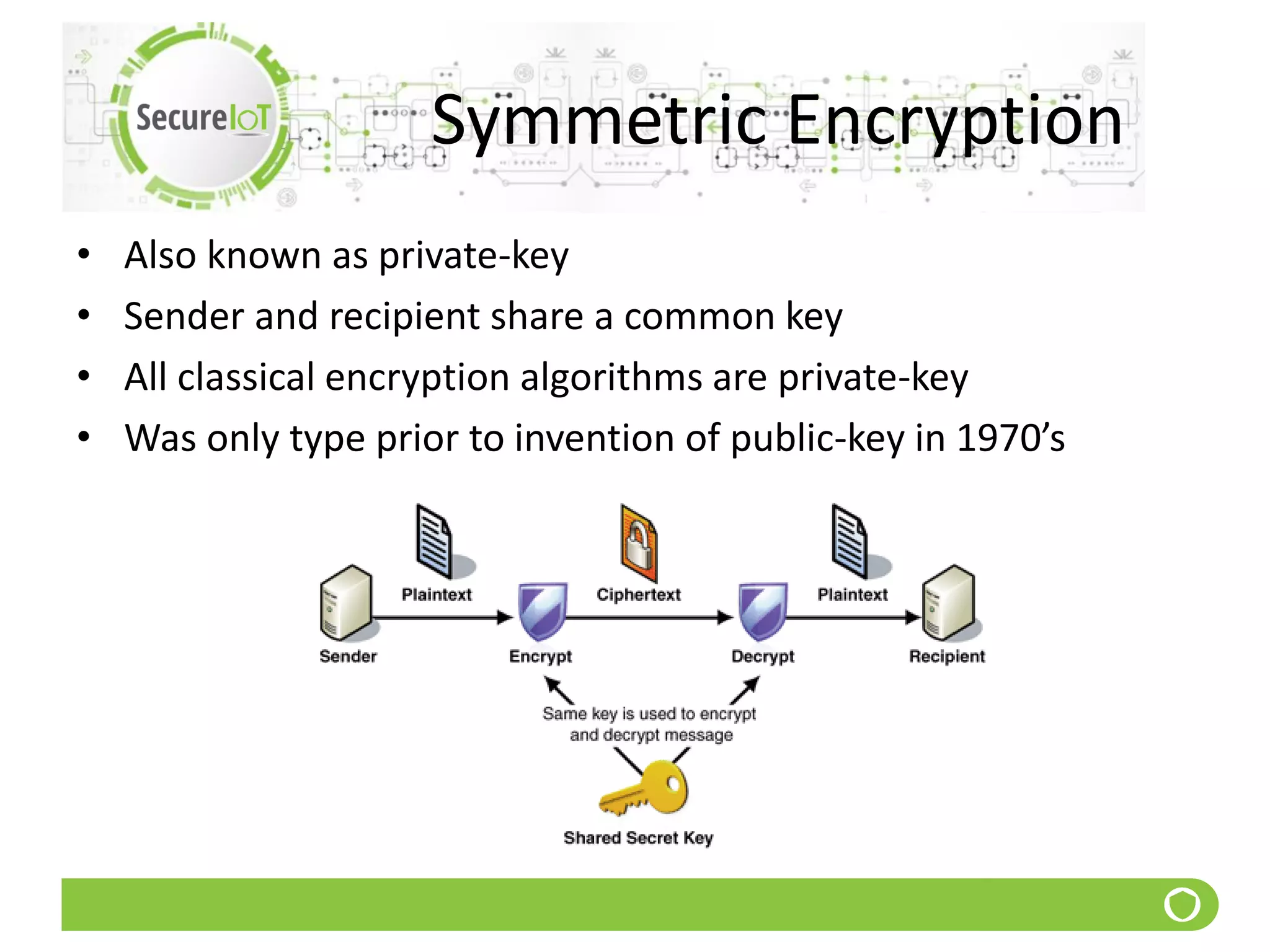
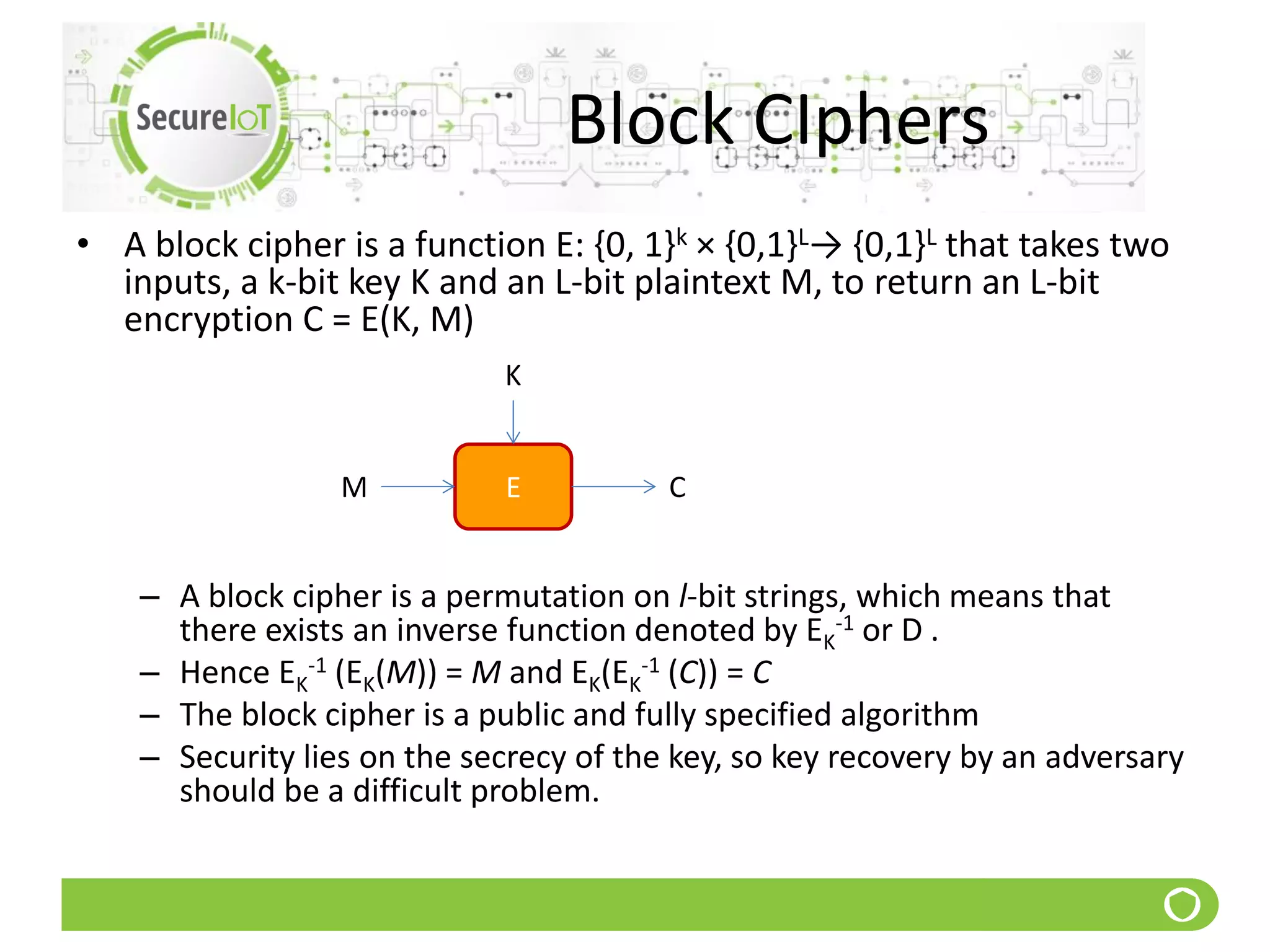
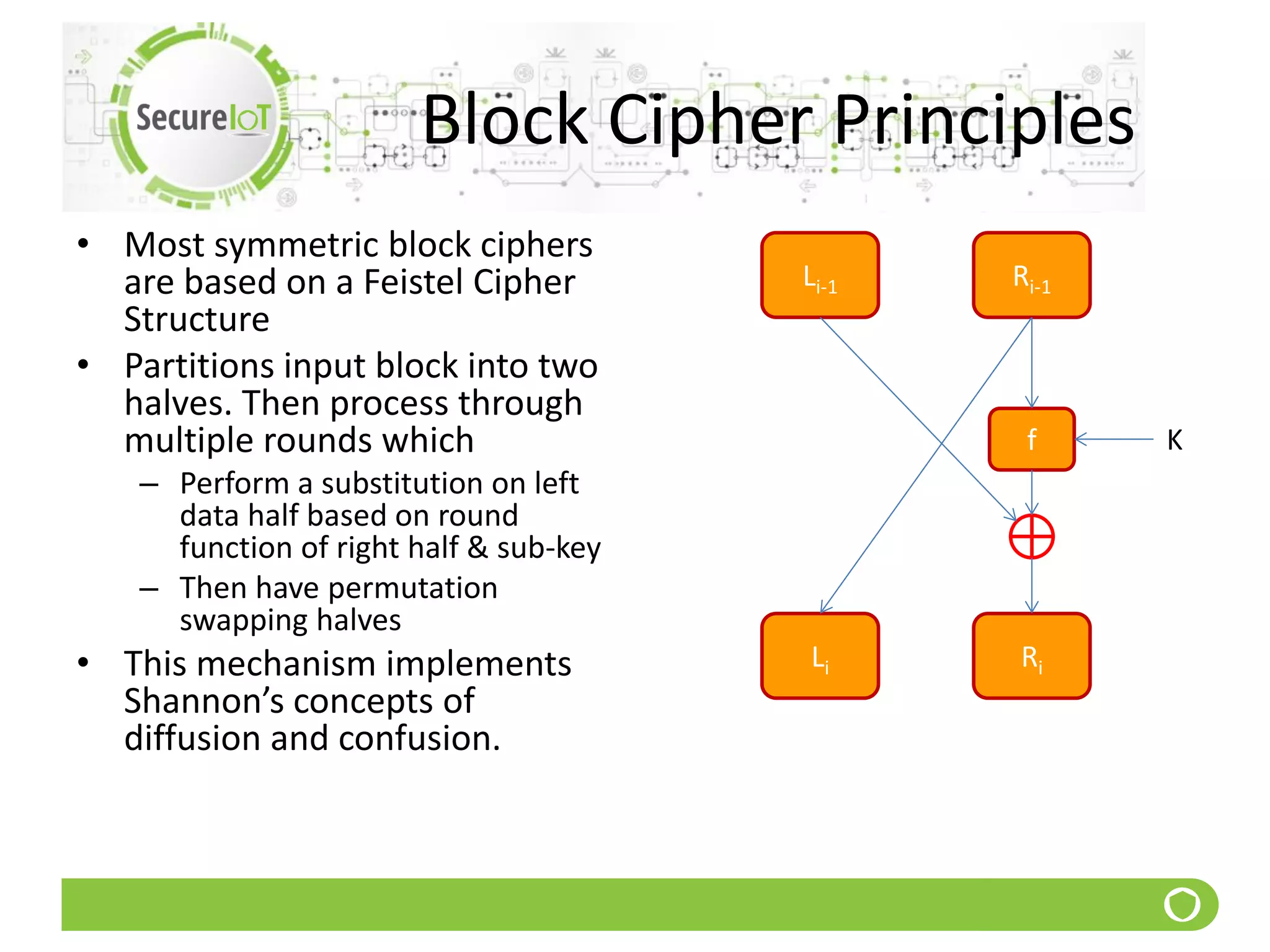
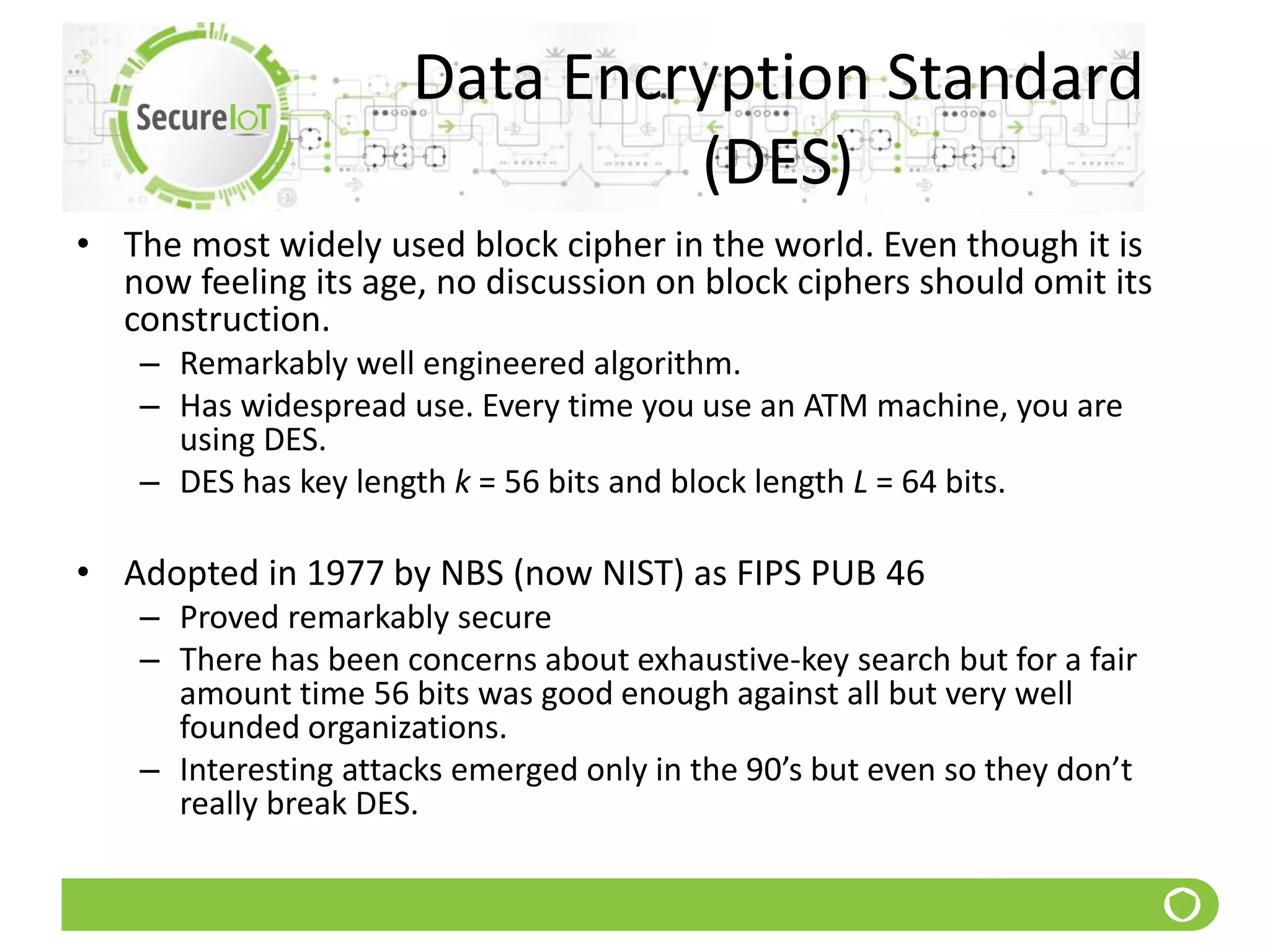
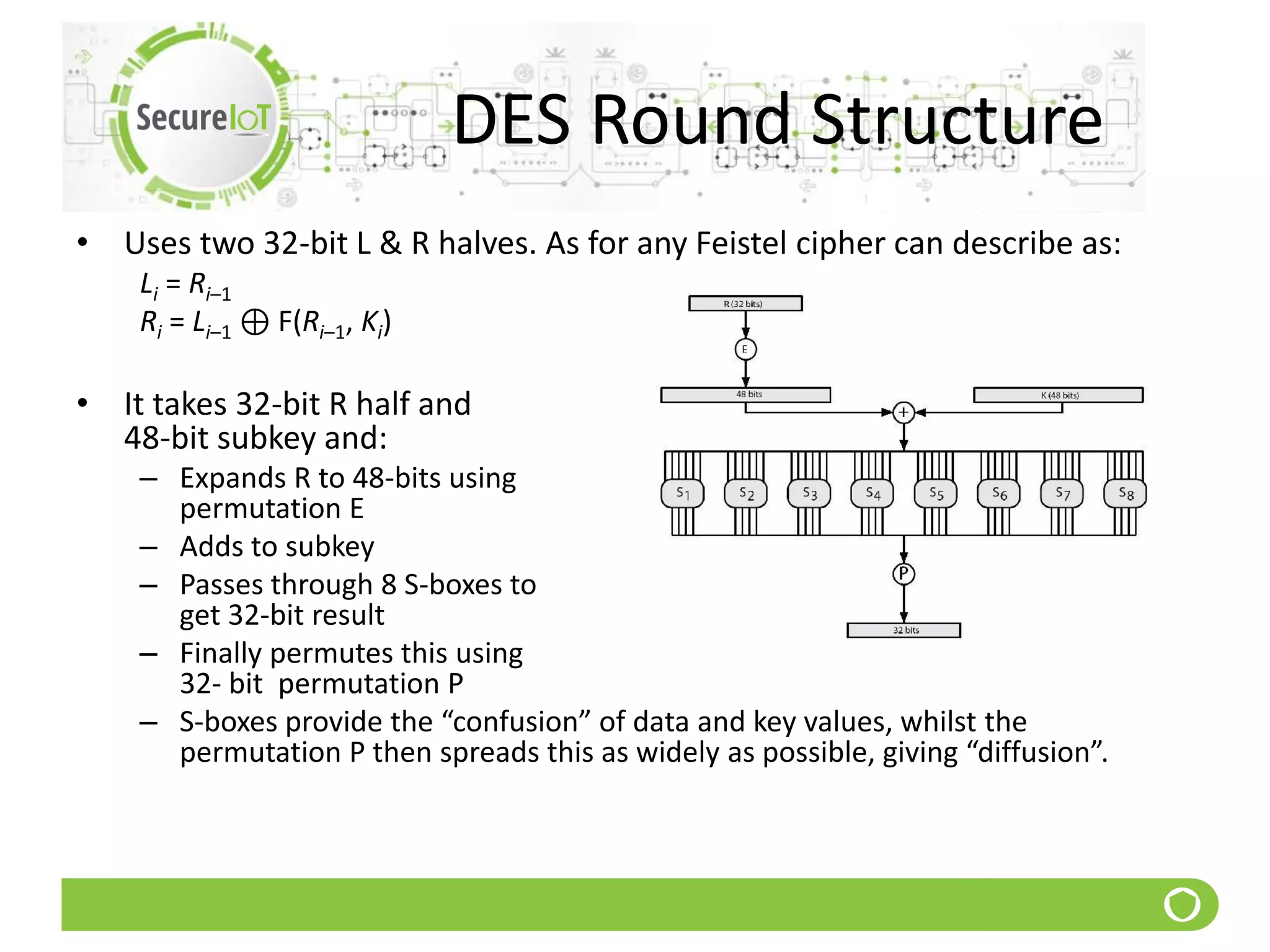
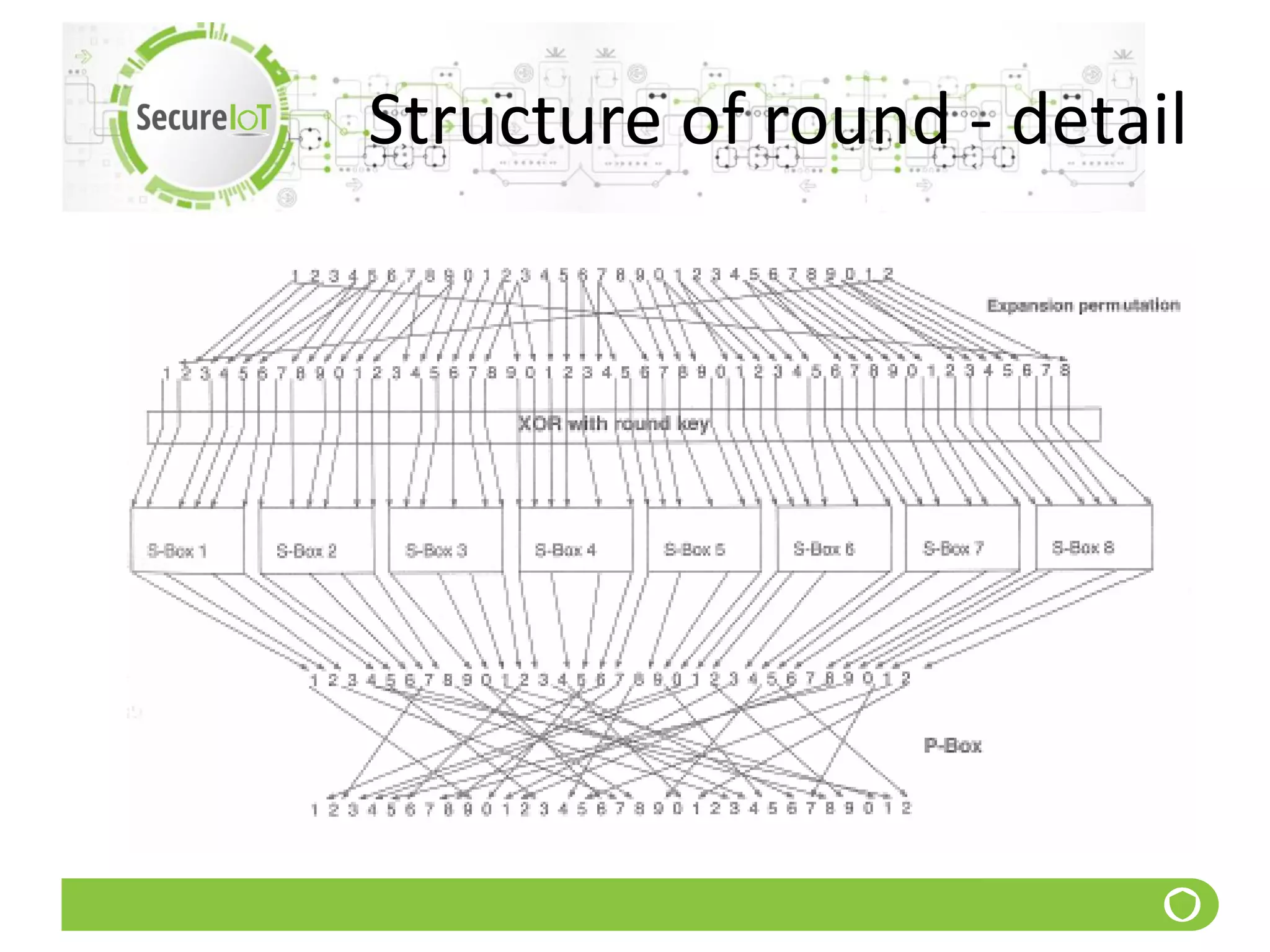
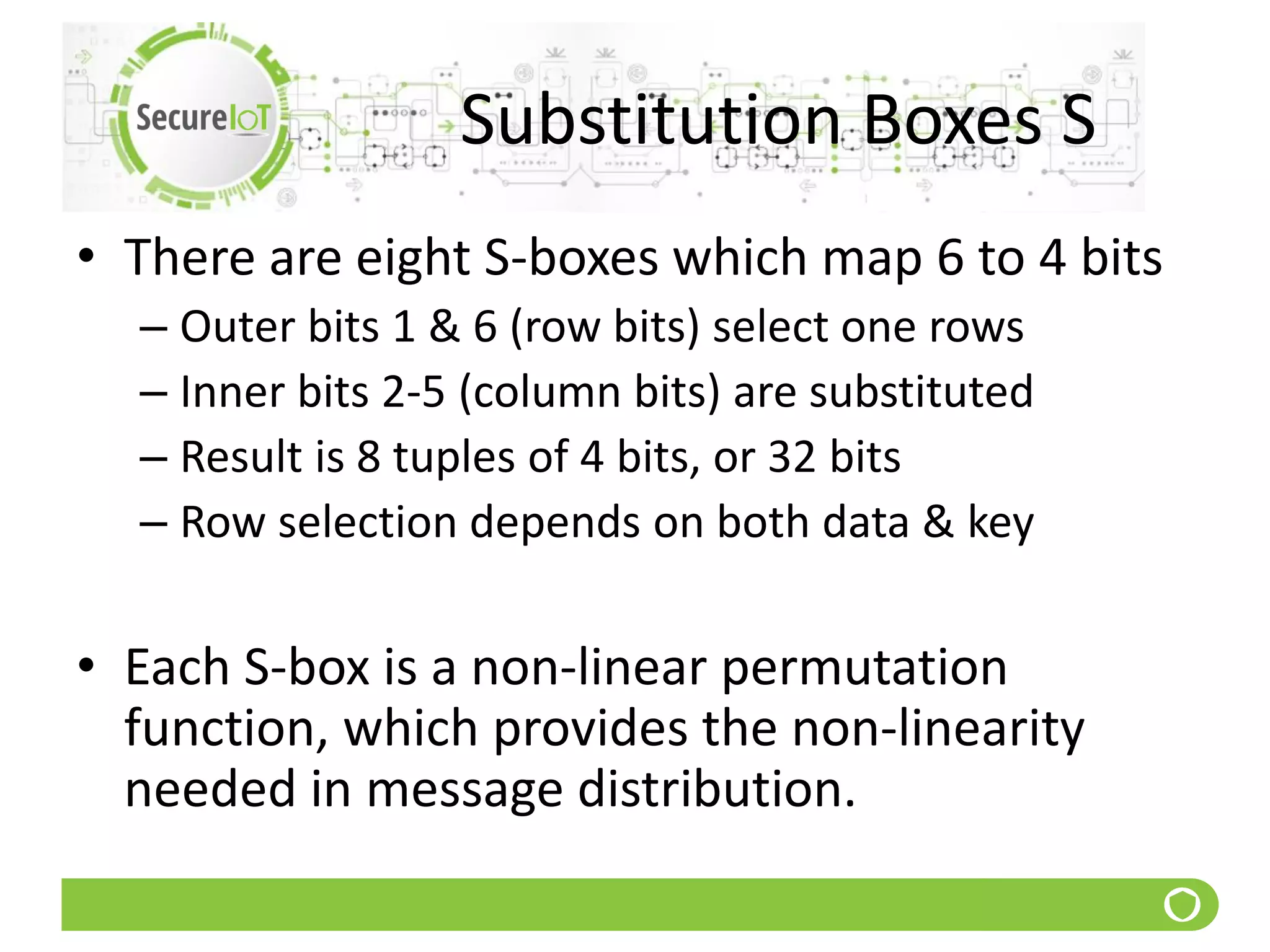
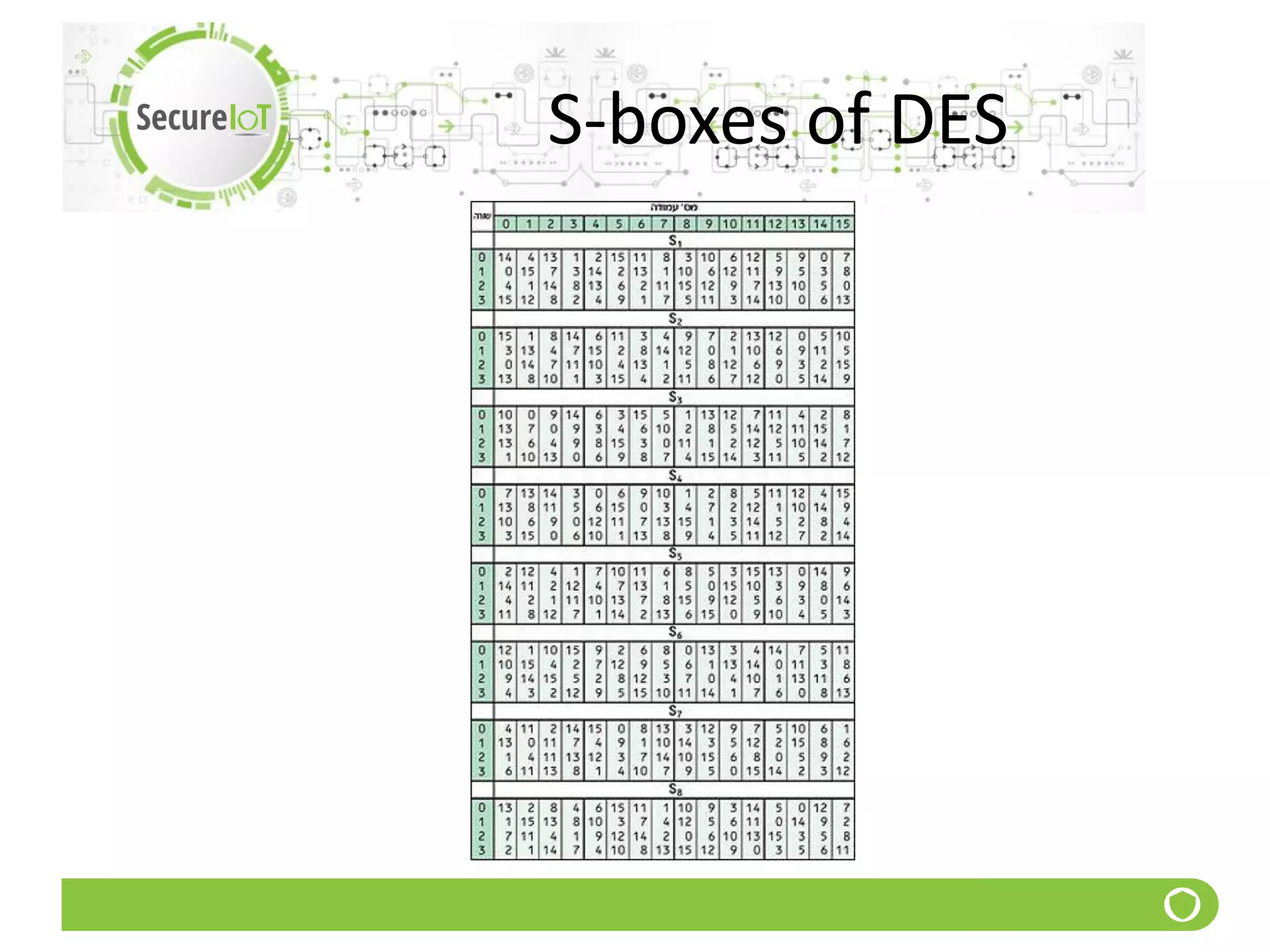
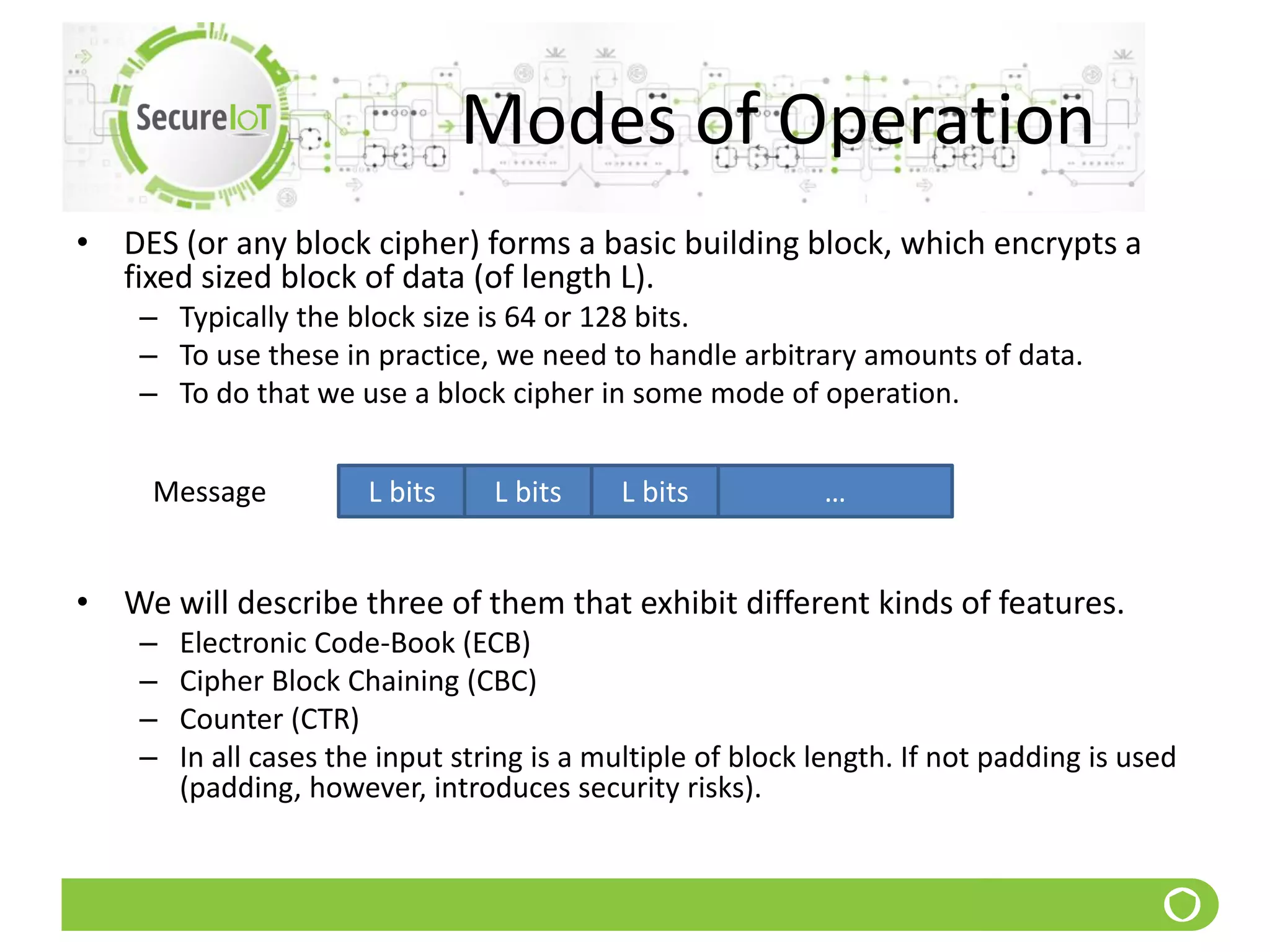
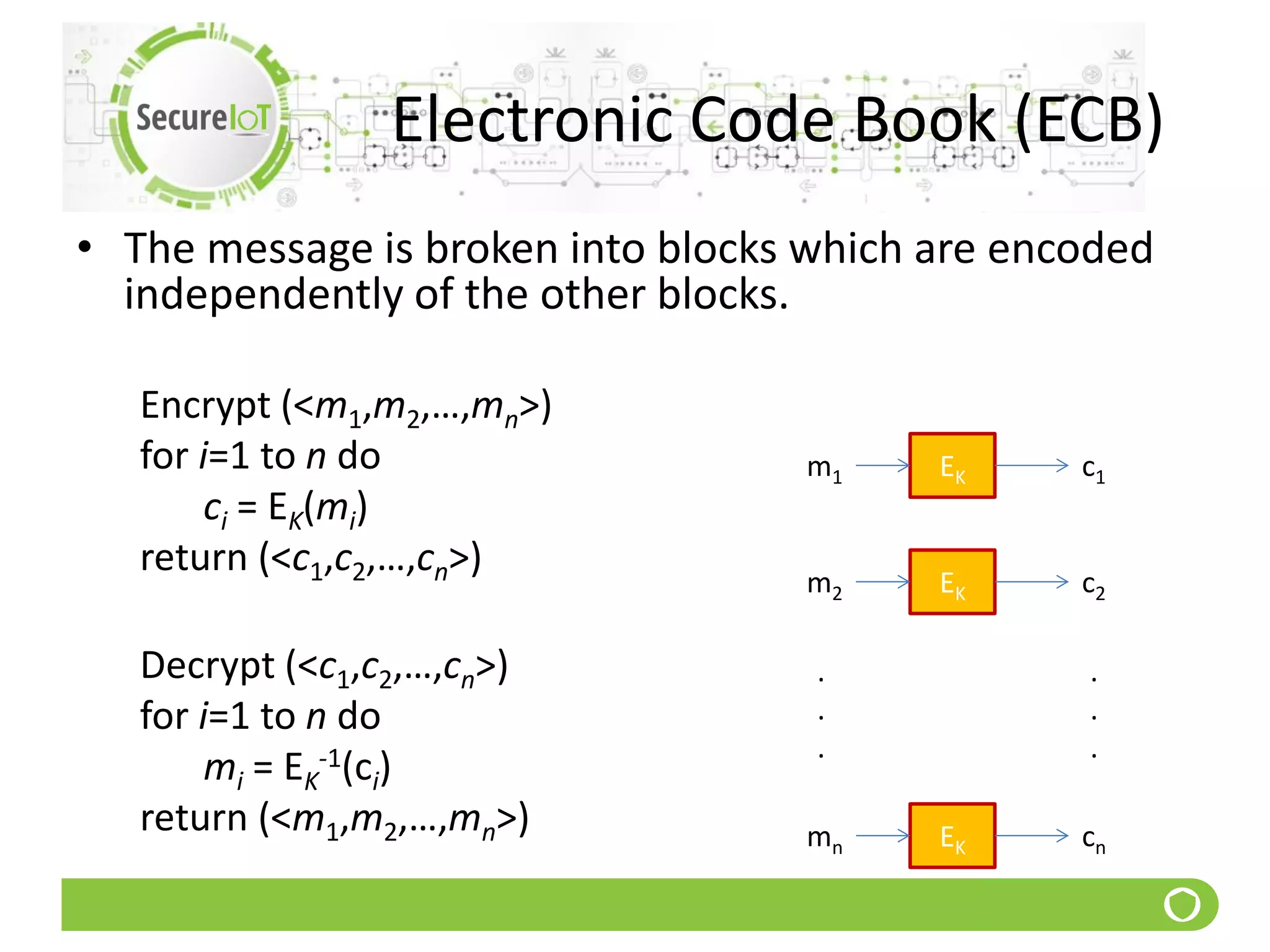
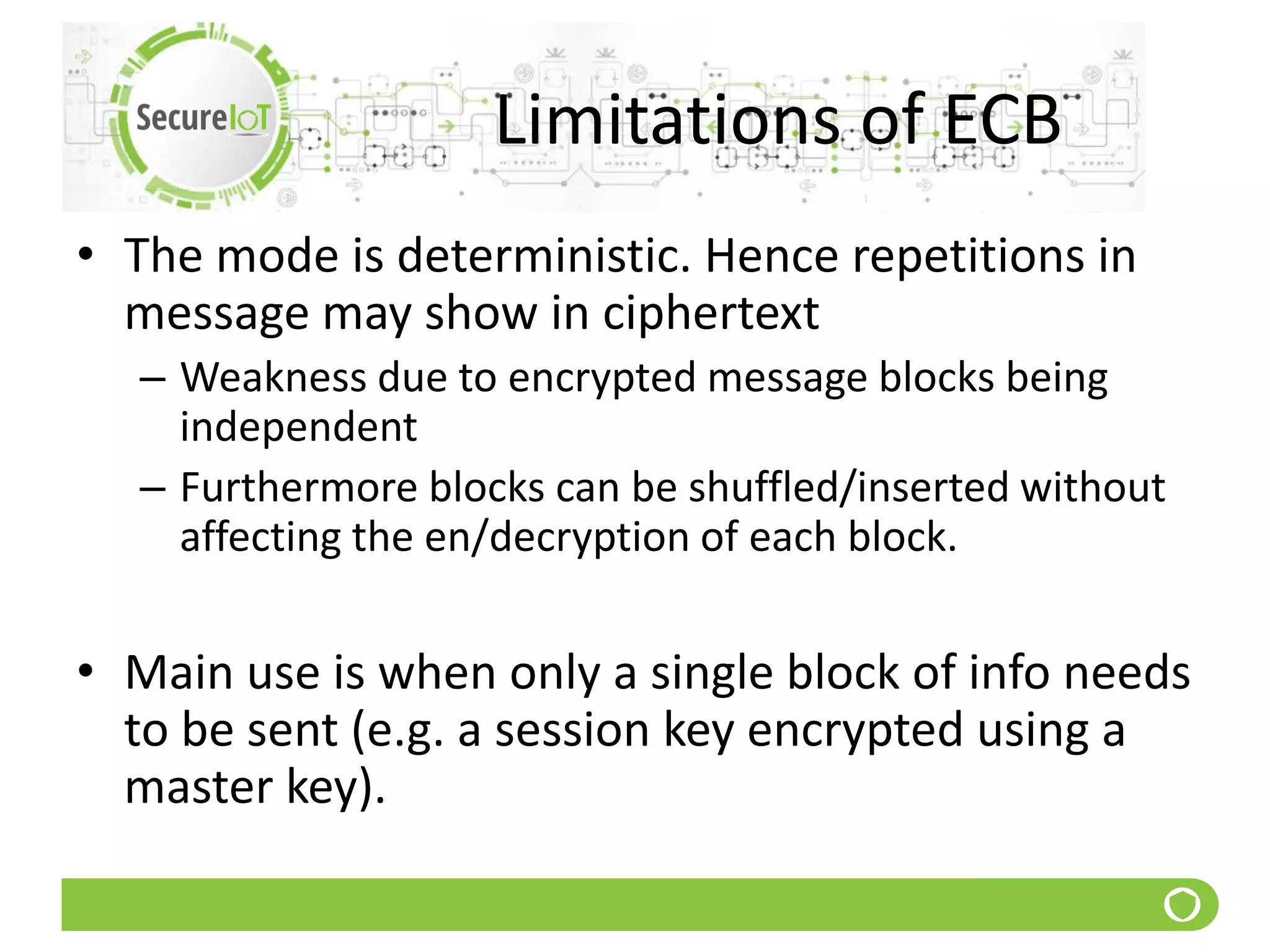
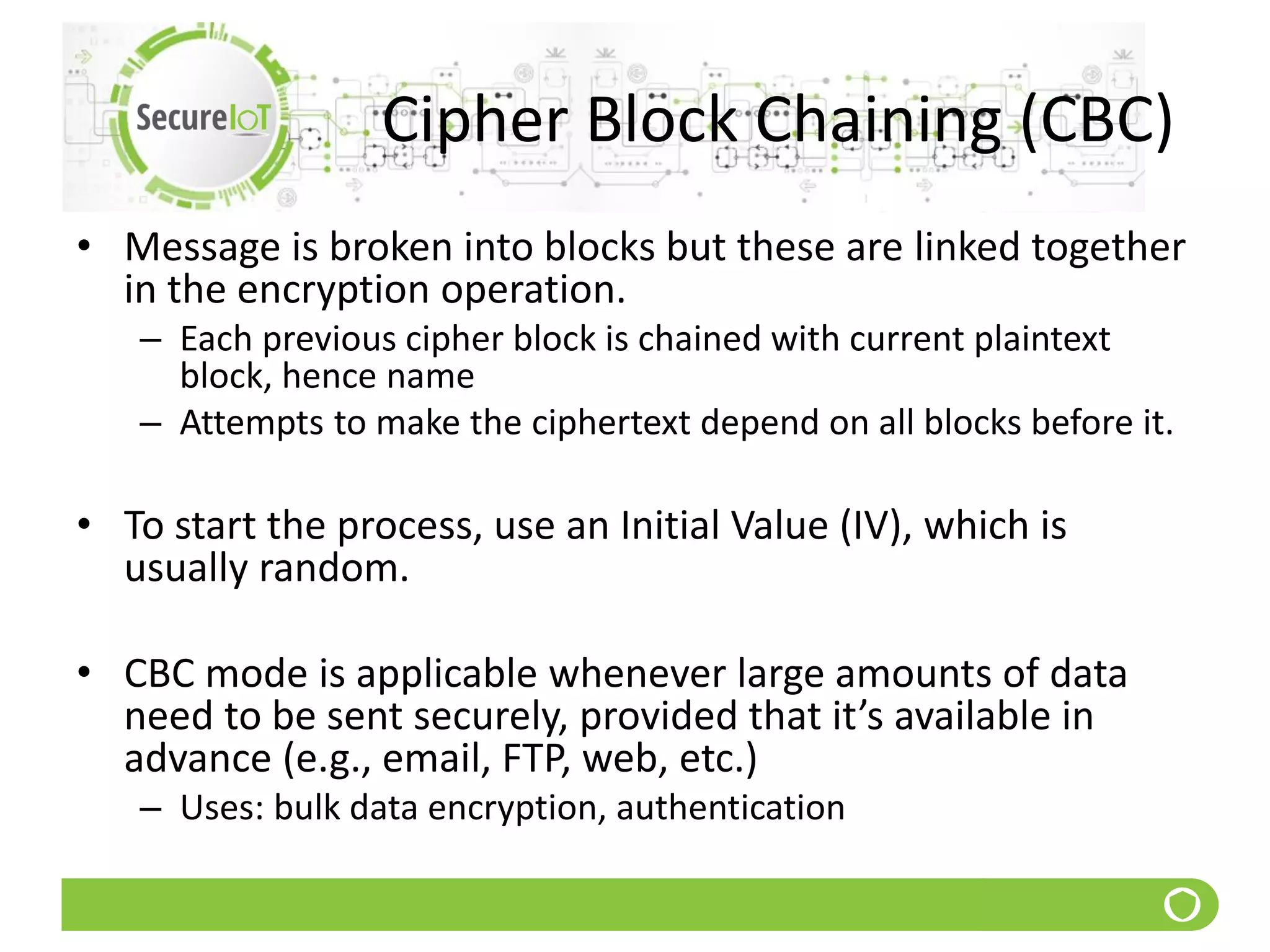
The document discusses security fundamentals and classical ciphers. It defines computer and network security, and lists common security problems. It then covers security goals like authentication, access control, confidentiality and integrity. It discusses security services, mechanisms, and attacks. Finally, it provides examples of classical ciphers like the Shift Cipher, Substitution Cipher, Vigenere Cipher, Vernam Cipher, and Transposition Ciphers. It explains how to analyze and break some of these classical ciphers.





















![Triple-DES with Two-Keys
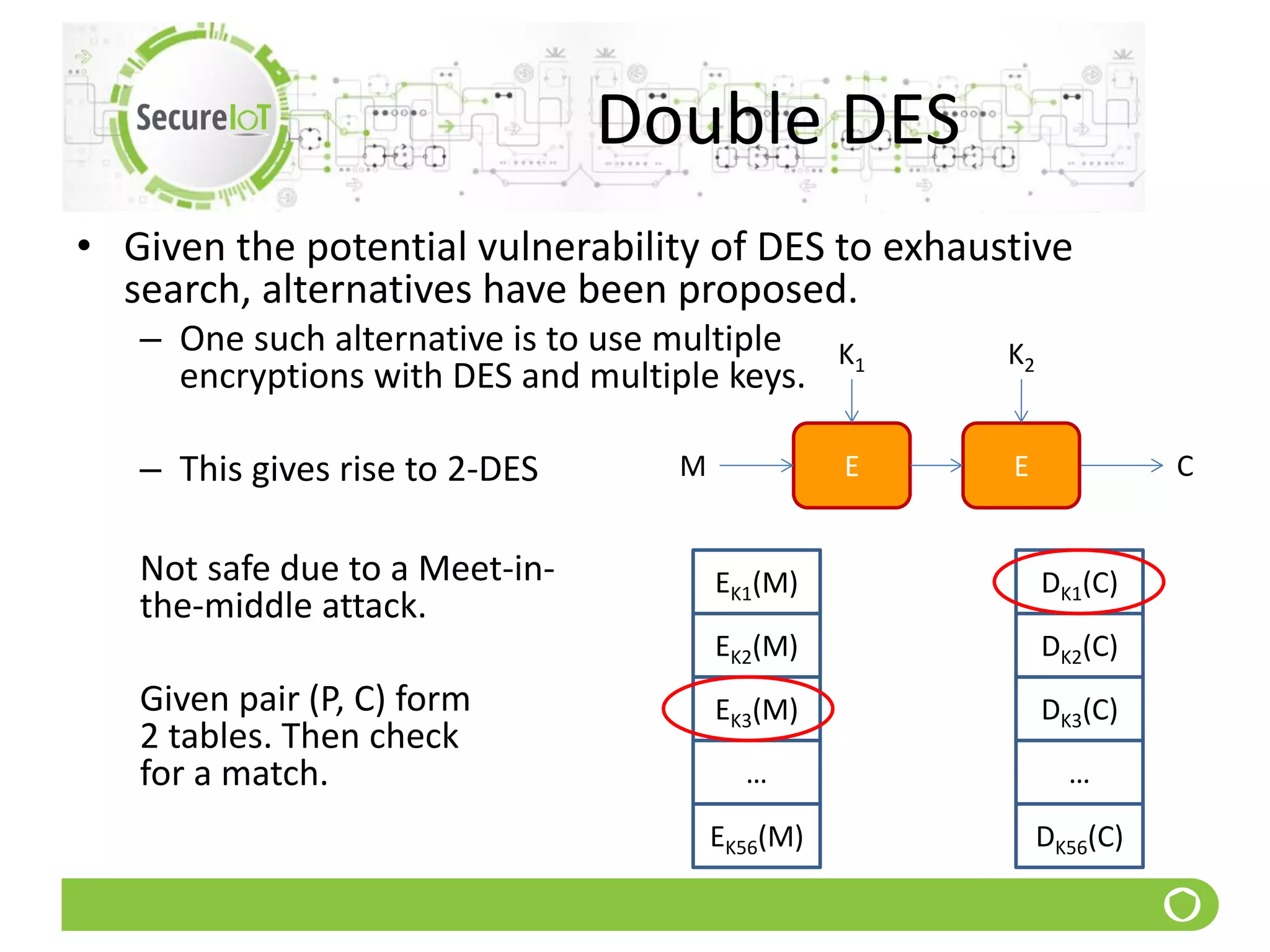
• To withstand the meet-in-the-middle attack one can
use 2 stages of encryption with 3 different keys.
• One alternative is to use 2 keys with E-D-E sequence
(also known as EDE DES)
– C = EK1[DK2[EK1[P]]]
– Encrypt & decrypt equivalent in security
– What is the significance of using D in the middle??
• No current known practical attacks
– The cost of exhaustive key search is of the order 2112](https://image.slidesharecdn.com/5securityfundamentals-190911180912/75/Security-fundamentals-69-2048.jpg)














![Properties of hash functions
easy
hard
One-way property
y
x
x’
[Strong] Collision resistance](https://image.slidesharecdn.com/5securityfundamentals-190911180912/75/Security-fundamentals-99-2048.jpg)


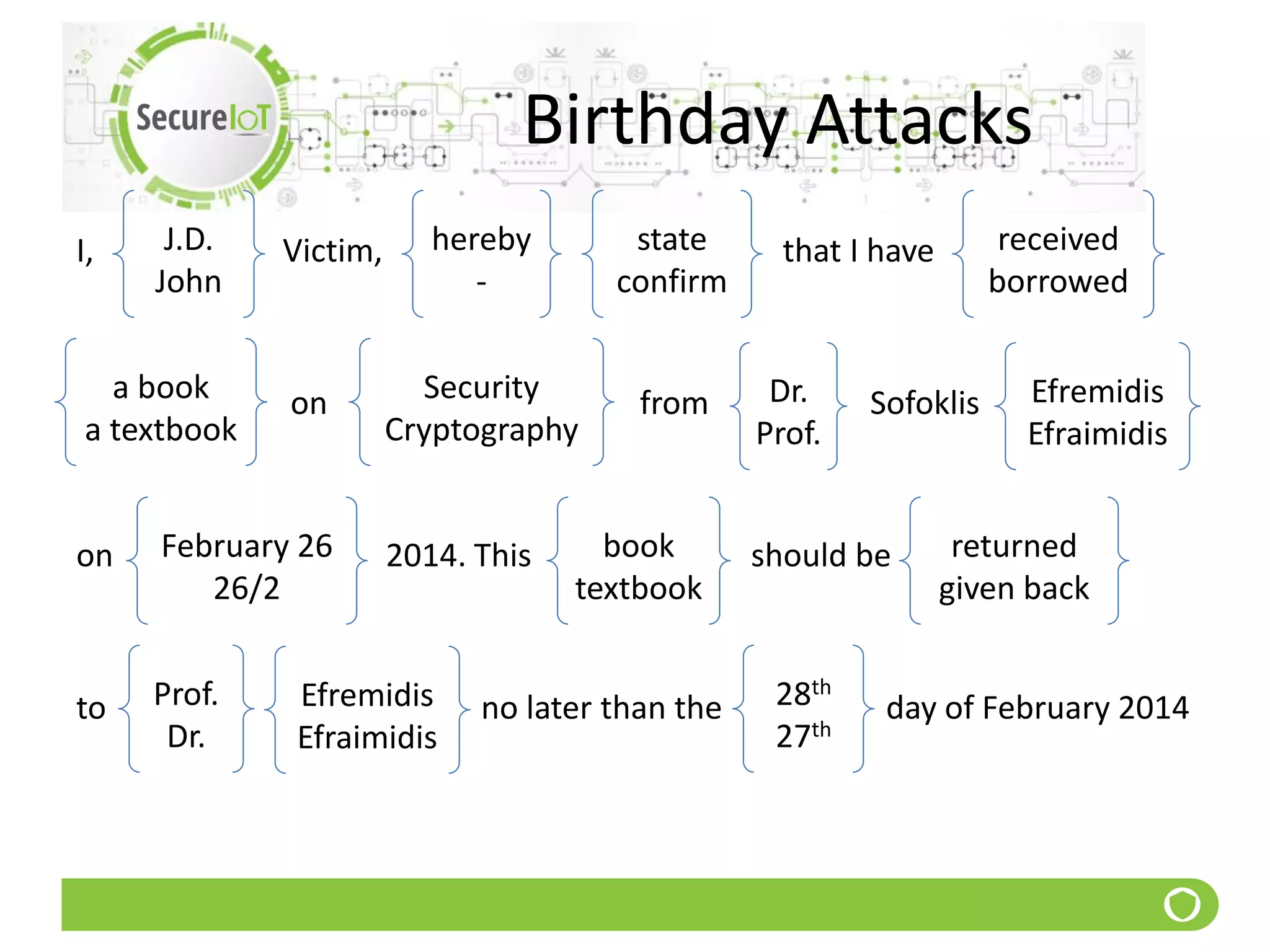
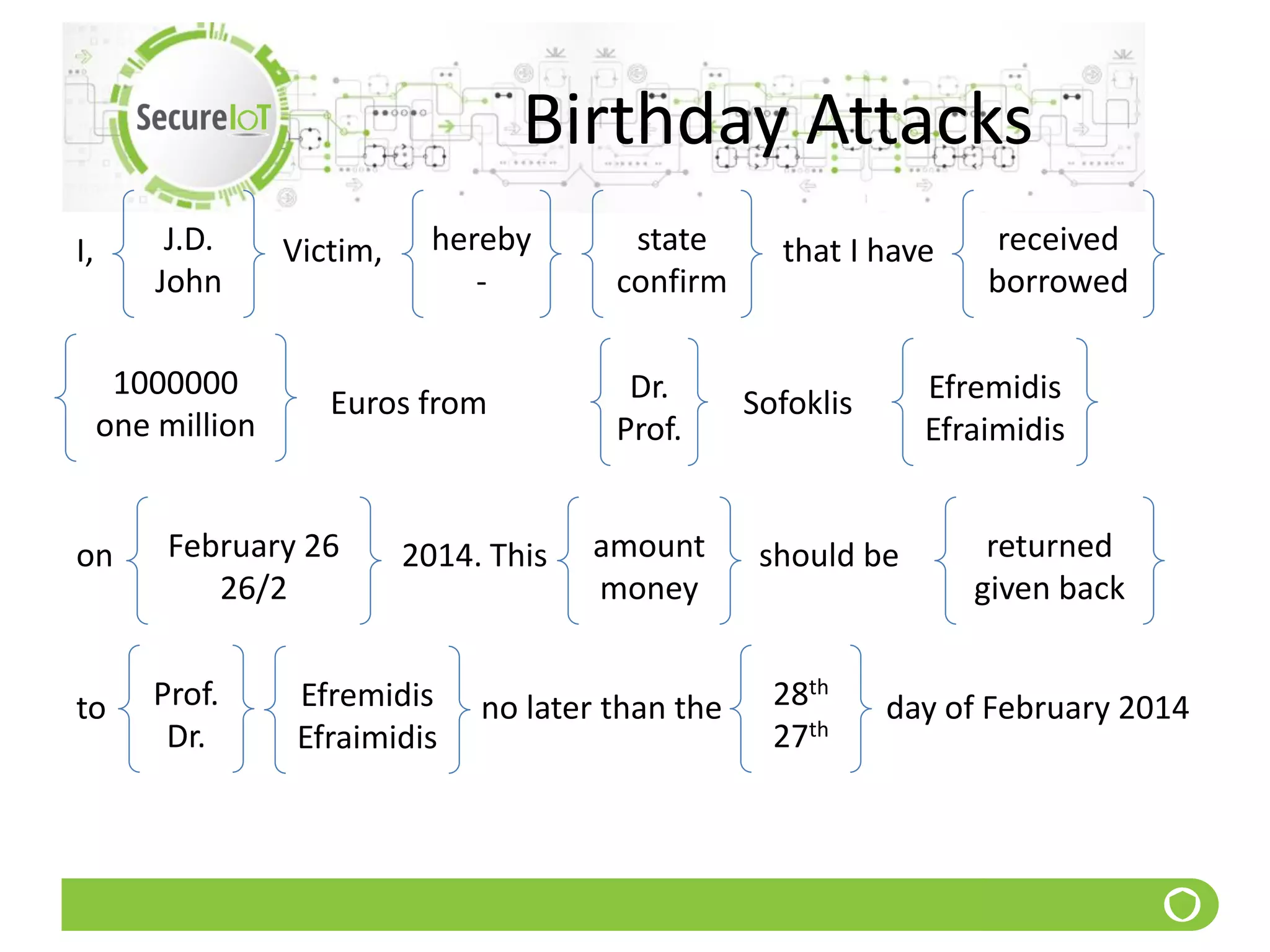
![Birthday Attacks
q Pr[2 have same birthdate]
15 0.253
18 0.347
20 0.411
21 0.444
23 0.507
25 0.569
27 0.627
30 0.796
35 0.818
40 0.891
50 0,970](https://image.slidesharecdn.com/5securityfundamentals-190911180912/75/Security-fundamentals-105-2048.jpg)



























![PGP Operation – Summary
X file
Signature
required?
Generate signature
X signature || X
Compress
X Z(X)
Confidentiality
required?
Encrypt key, X
X EKUb[KS] || EKs[X]
Convert to radix 64
X R64(X)
Y
Y
N
N
Convert from radix 64
X R64-1(X)
Confidentiality
required?
Decrypt key, X
K DKRb[EKUb[KS]]
X DK[X]
Decompress
X Z-1(X)
Signature
required?
Strip signature from X
Verify signature
Y
Y
N
N
Generic Transmission Diagram Generic Reception Diagram](https://image.slidesharecdn.com/5securityfundamentals-190911180912/75/Security-fundamentals-177-2048.jpg)