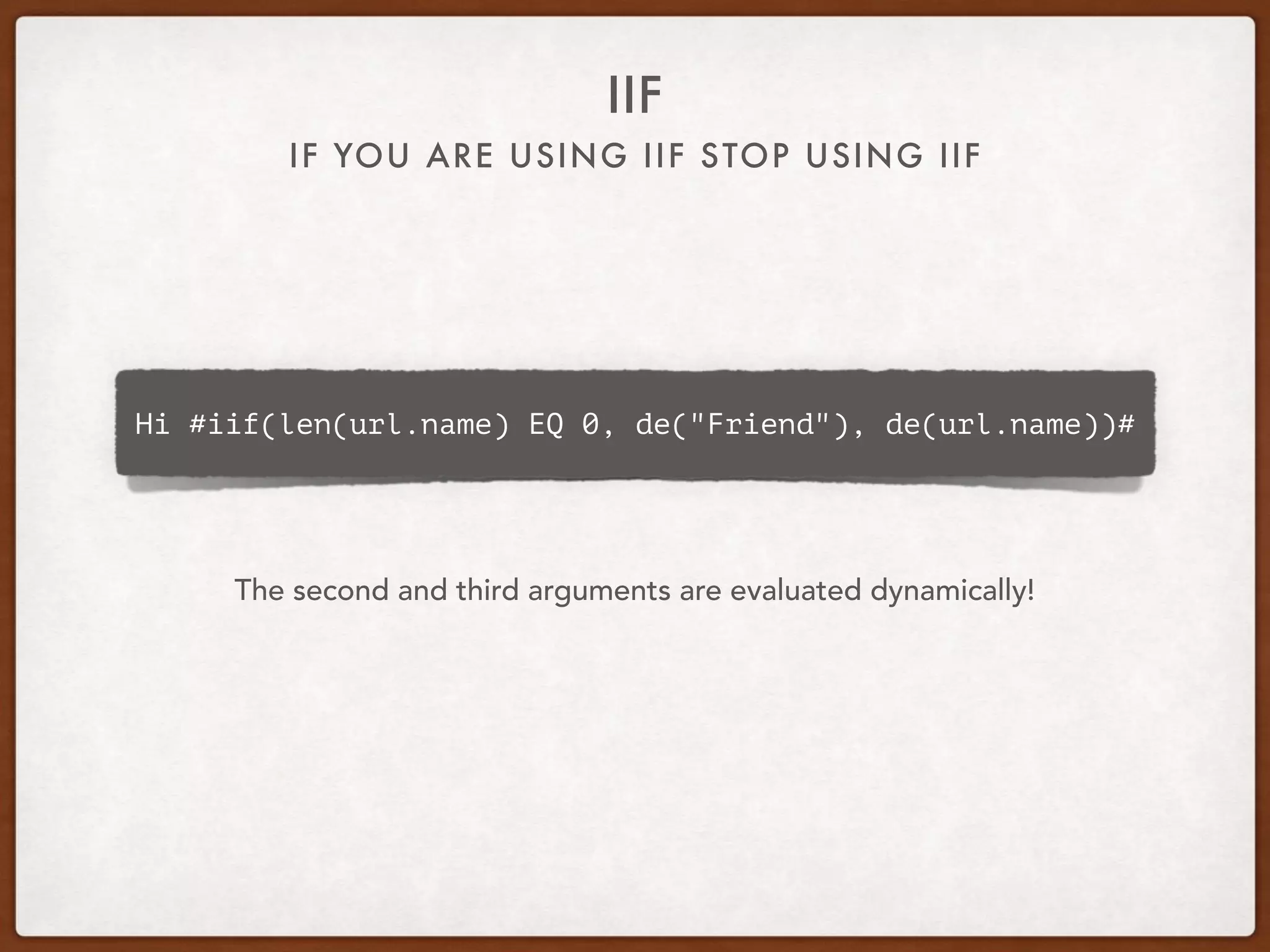
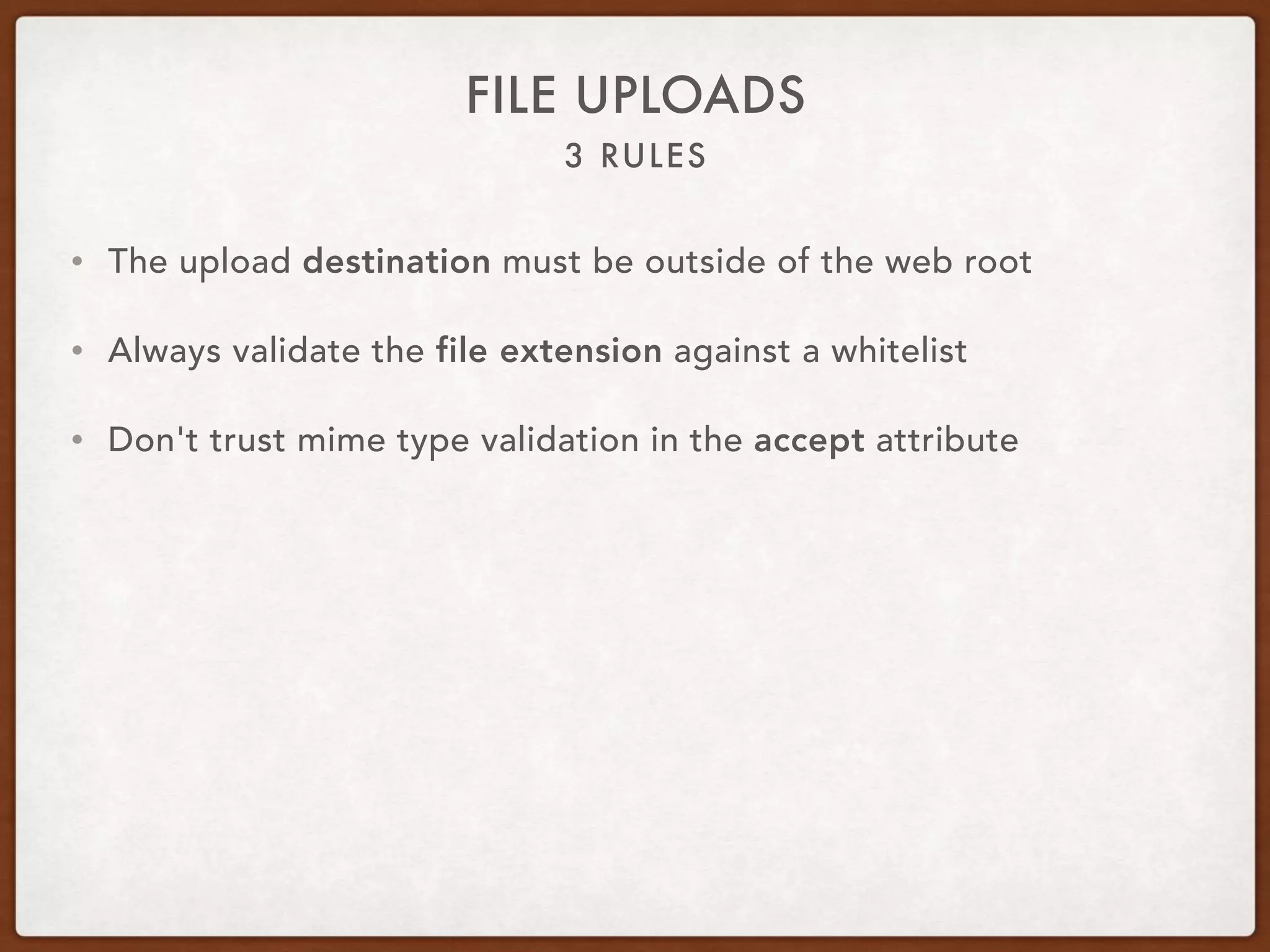
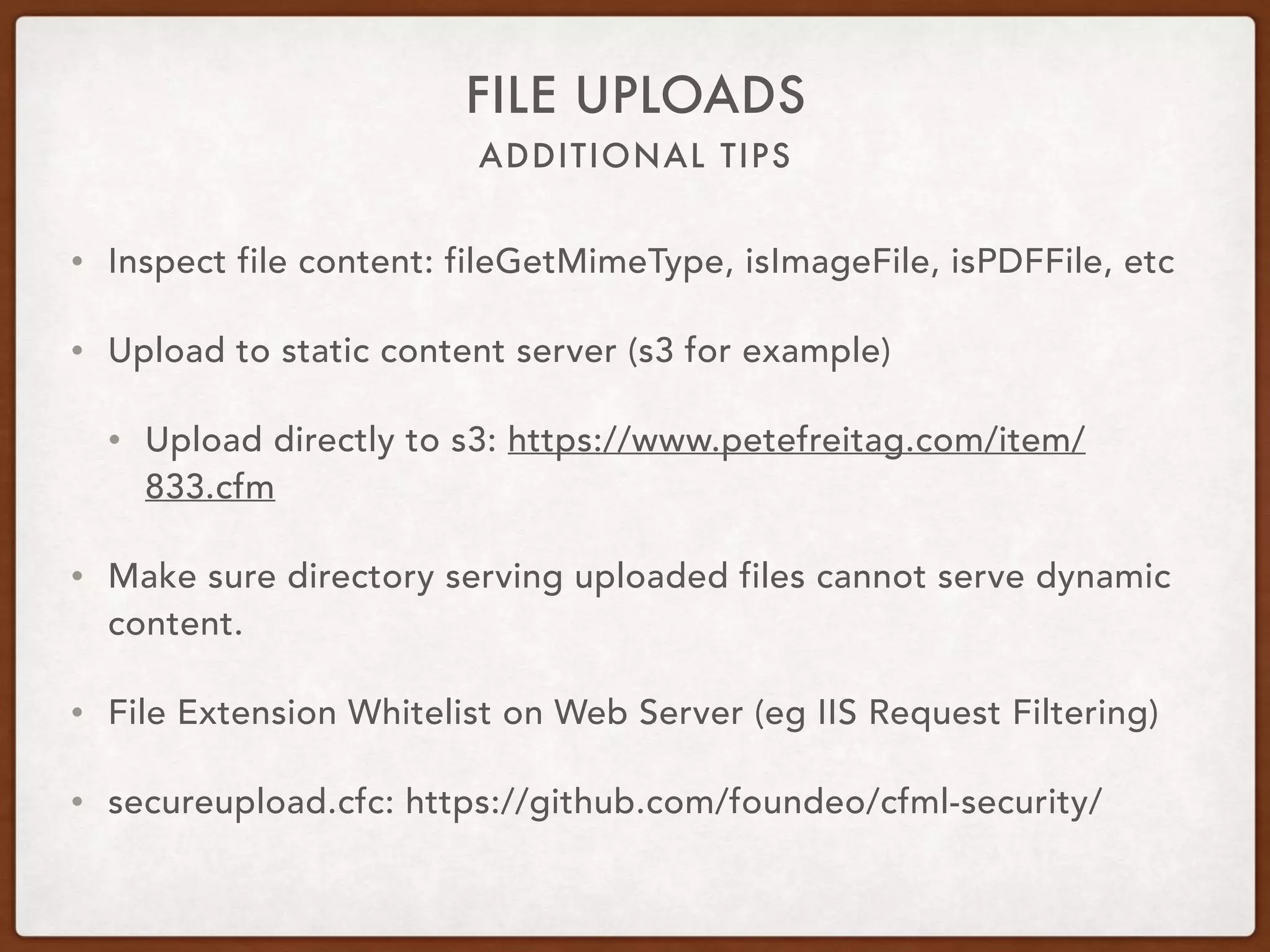
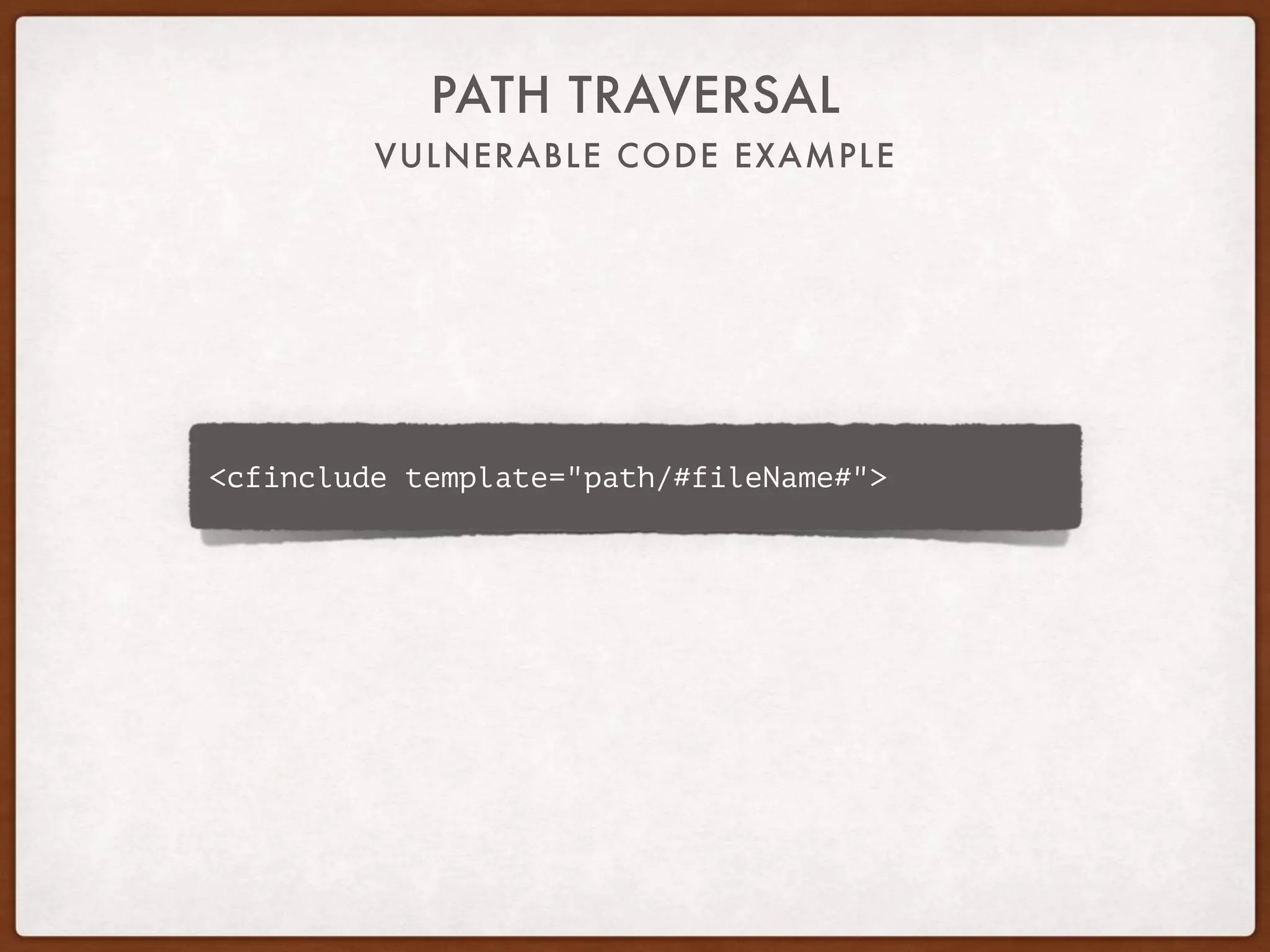
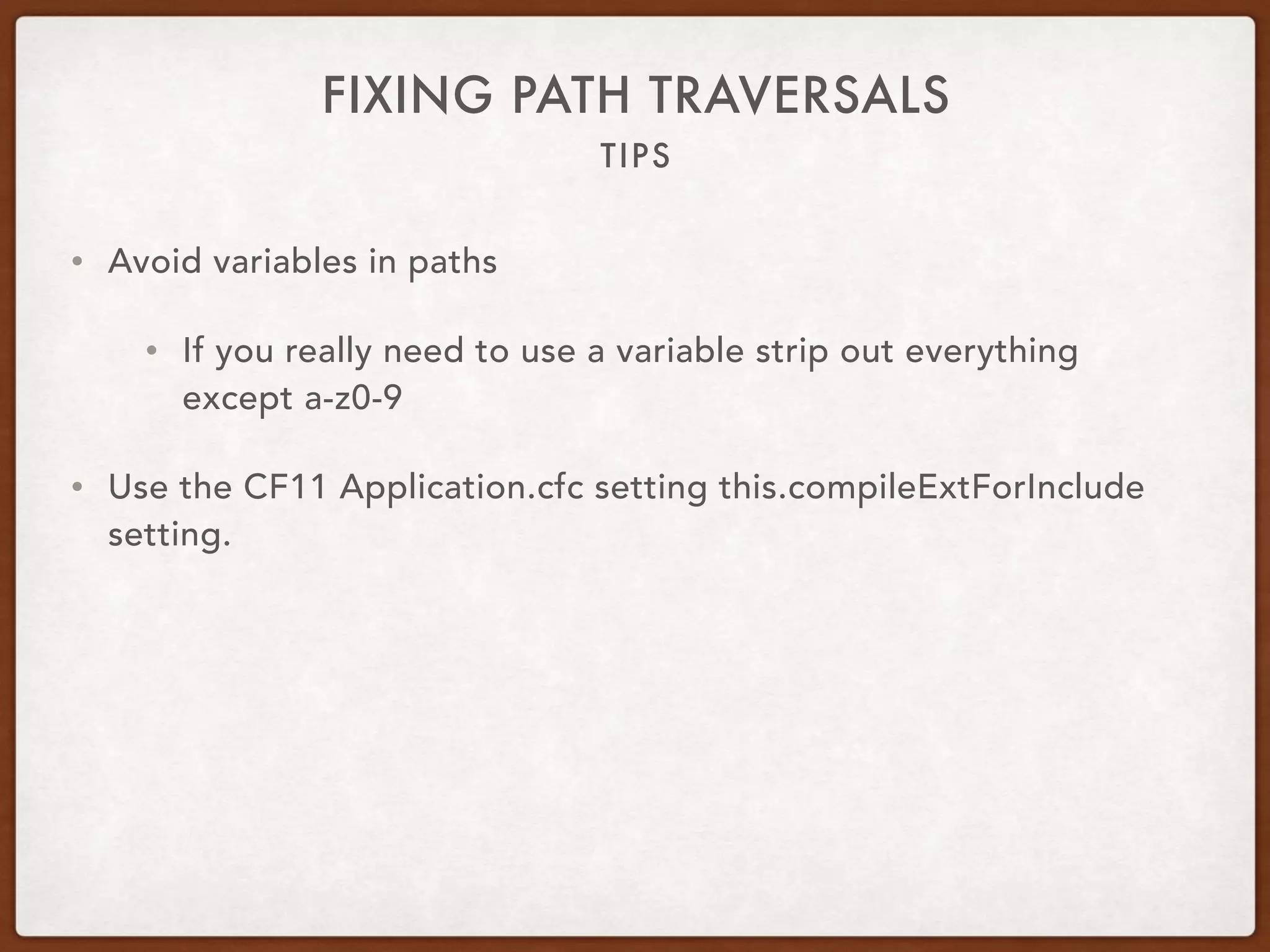
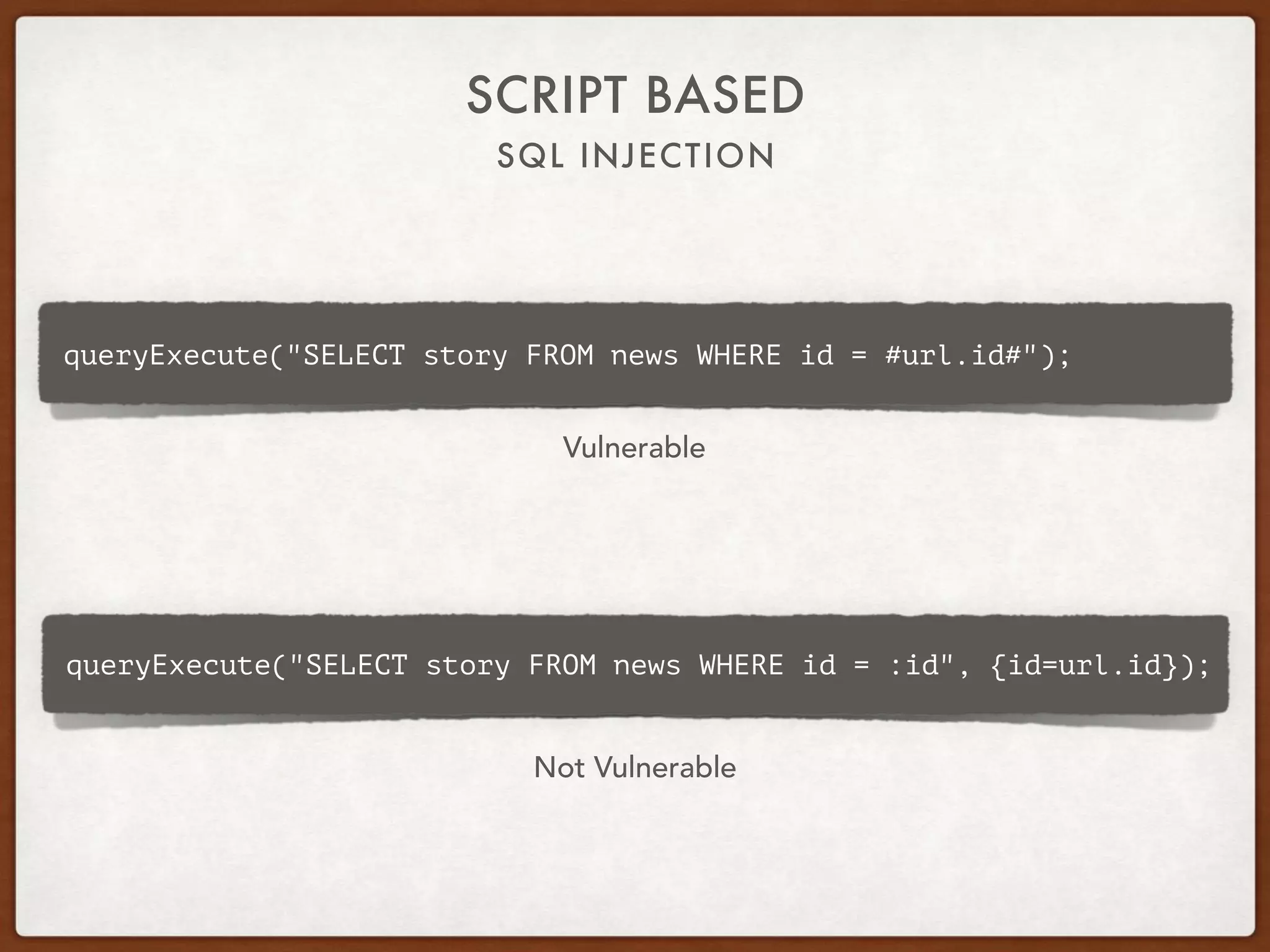
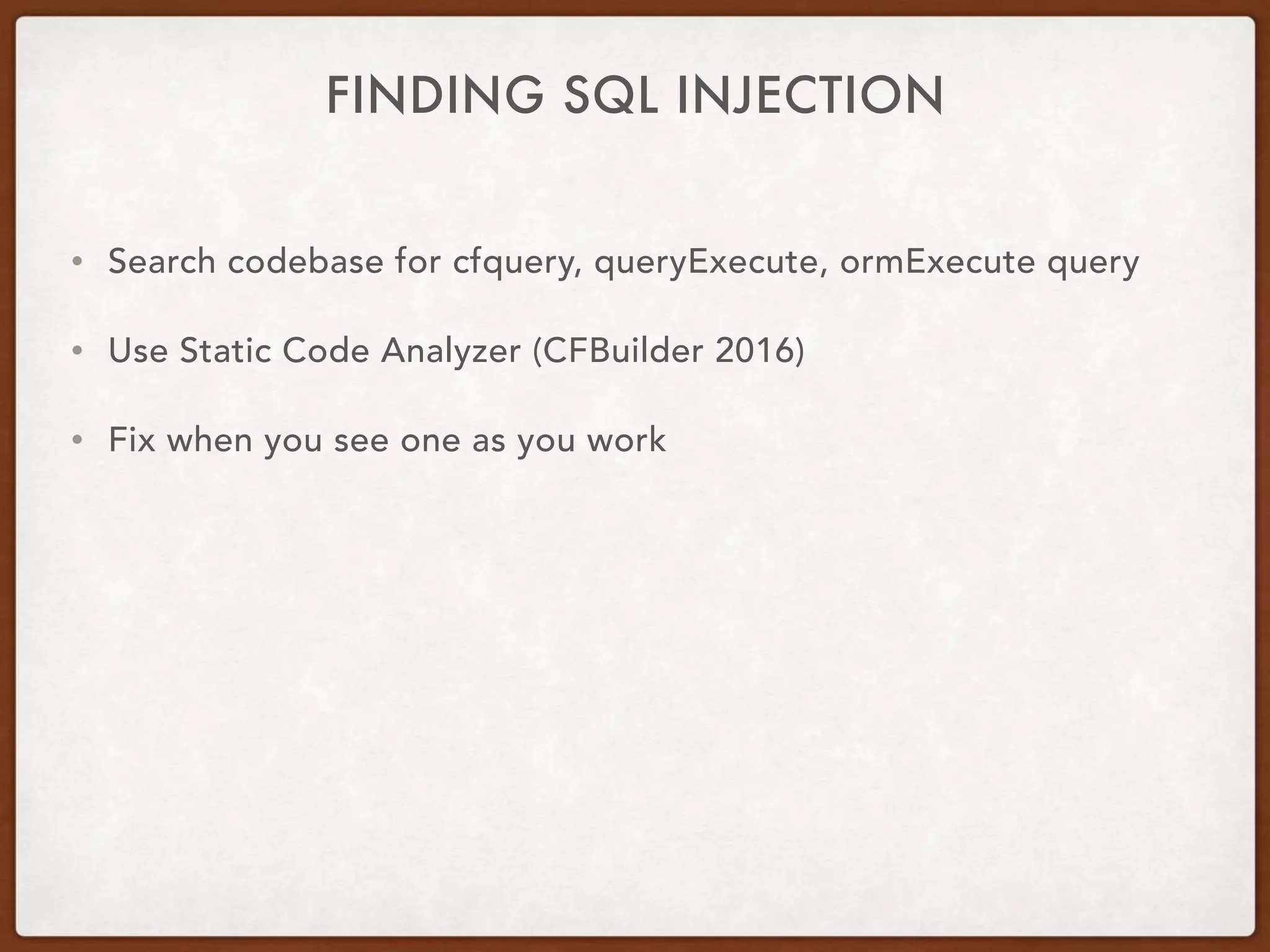
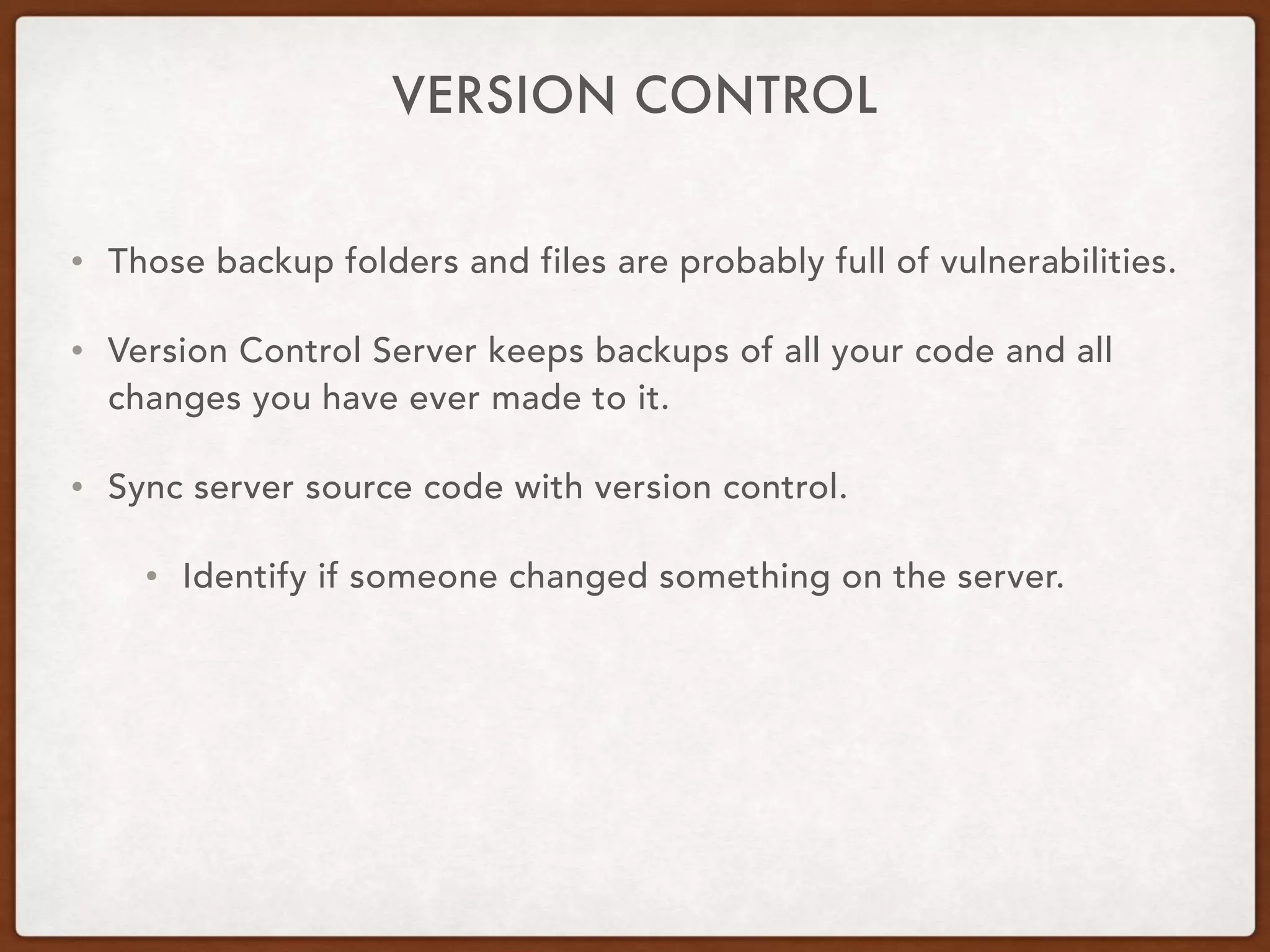
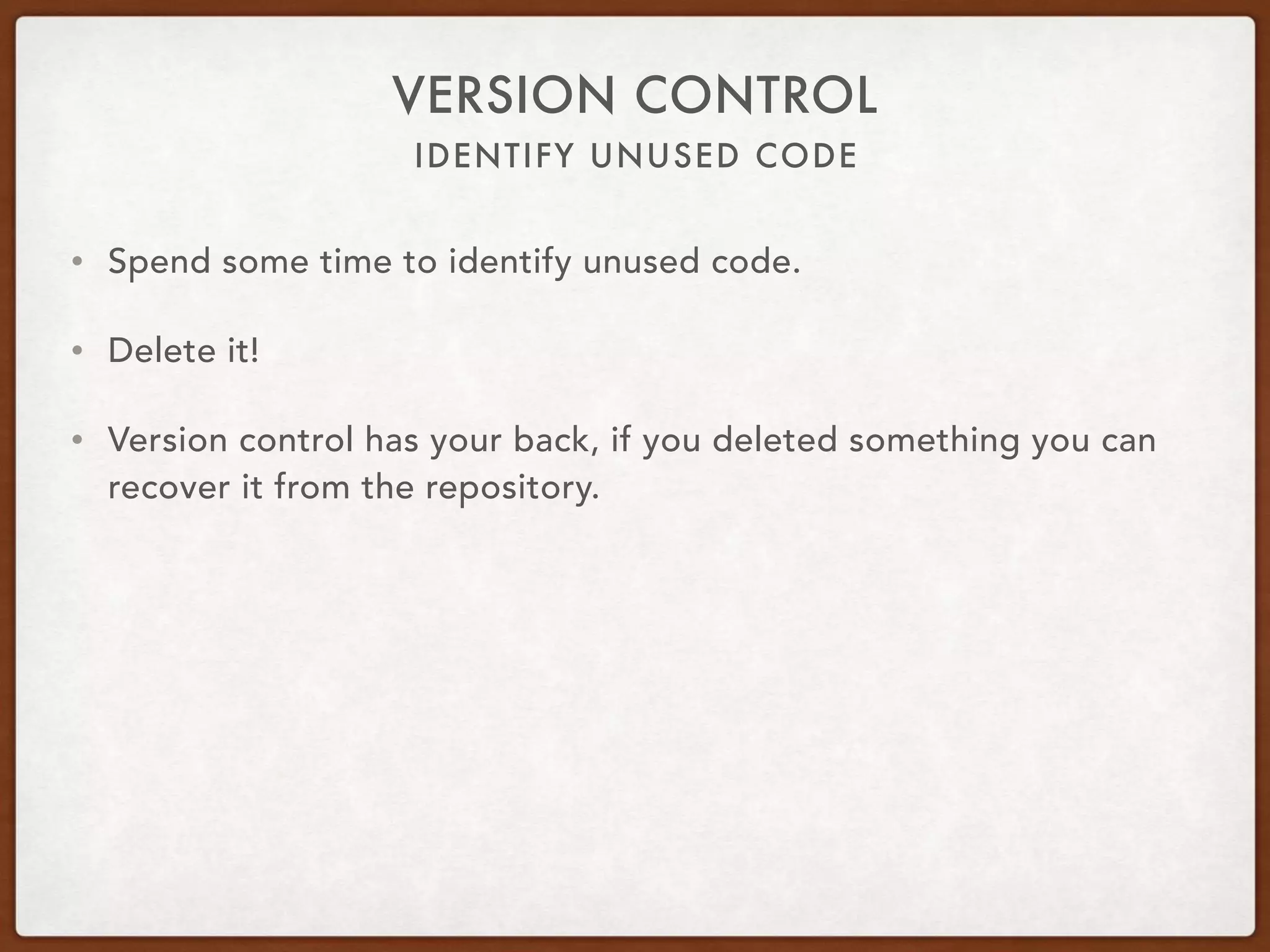
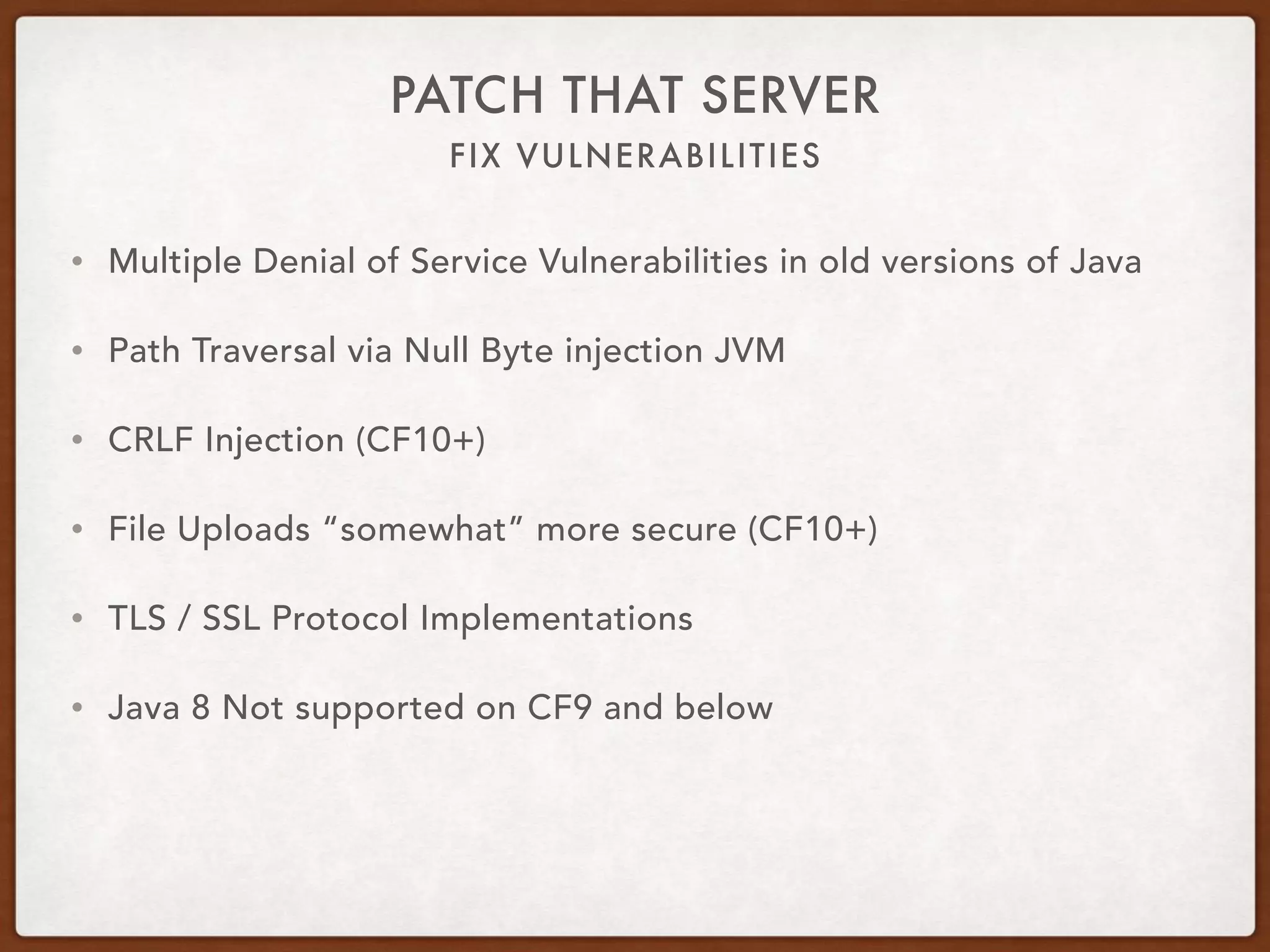
This document provides guidance on securing existing ColdFusion applications with large codebases. It recommends beginning the process by deleting unused code and implementing version control. It then advises patching the ColdFusion server, locking down server permissions, and implementing a web application firewall. The document outlines prioritizing the fixing of high risk vulnerabilities like file uploads, dynamic evaluation, SQL injection, and file system access. It provides code examples and tips for finding and fixing issues related to evaluate, IIF, file uploads, path traversals, and SQL injection. Finally, it mentions additional areas to review like session handling, scope injection, authentication, and cross-site scripting.














![USE BRACKET NOTATION
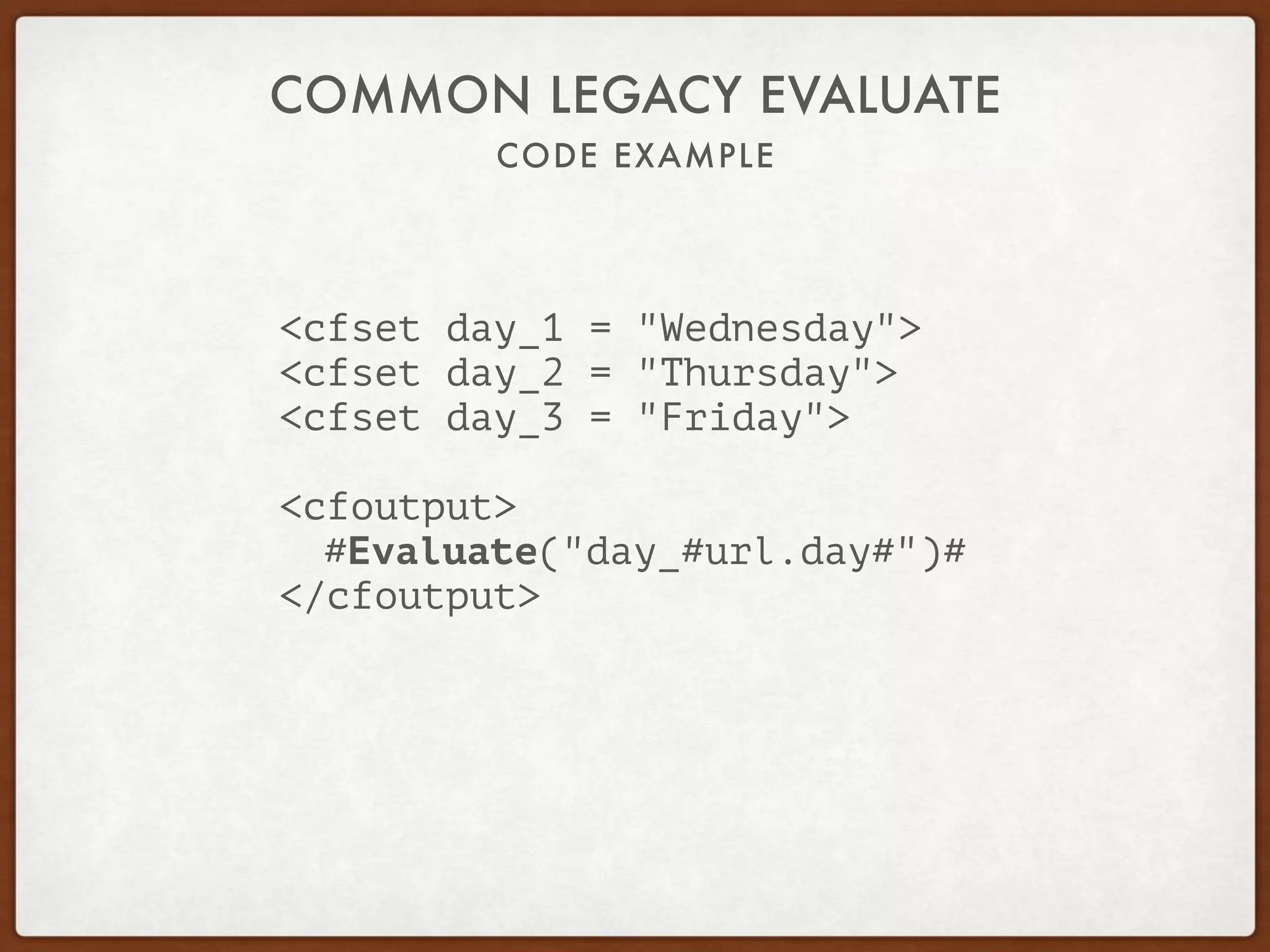
FIXING LEGACY EVALUATE EXAMPLE
<cfset day_1 = "Wednesday">
<cfset day_2 = "Thursday">
<cfset day_3 = "Friday">
<cfoutput>
#variables["day_#url.day#"]#
</cfoutput>](https://image.slidesharecdn.com/2cqav2j3shy5b74lov0m-signature-18098009b6e0b23319985220ee2f052e1eafe96a14816e4ea0b91f07f924c10e-poli-161018175045/75/Securing-applications-22-2048.jpg)
![SEARCH CODE FOR EVALUATE
FIXING EVALUATE ISSUES
• Search Code for "Evaluate"
• In most cases you should not need to use Evaluate at all, use
brackets.
• If the variable is a query you may need to use
queryName[row][columnName] notation.
• Not all cases are super simple to fix, but most are.
• Remove all Evaluate calls from your code.
• Also look at PrecisionEvaluate](https://image.slidesharecdn.com/2cqav2j3shy5b74lov0m-signature-18098009b6e0b23319985220ee2f052e1eafe96a14816e4ea0b91f07f924c10e-poli-161018175045/75/Securing-applications-23-2048.jpg)