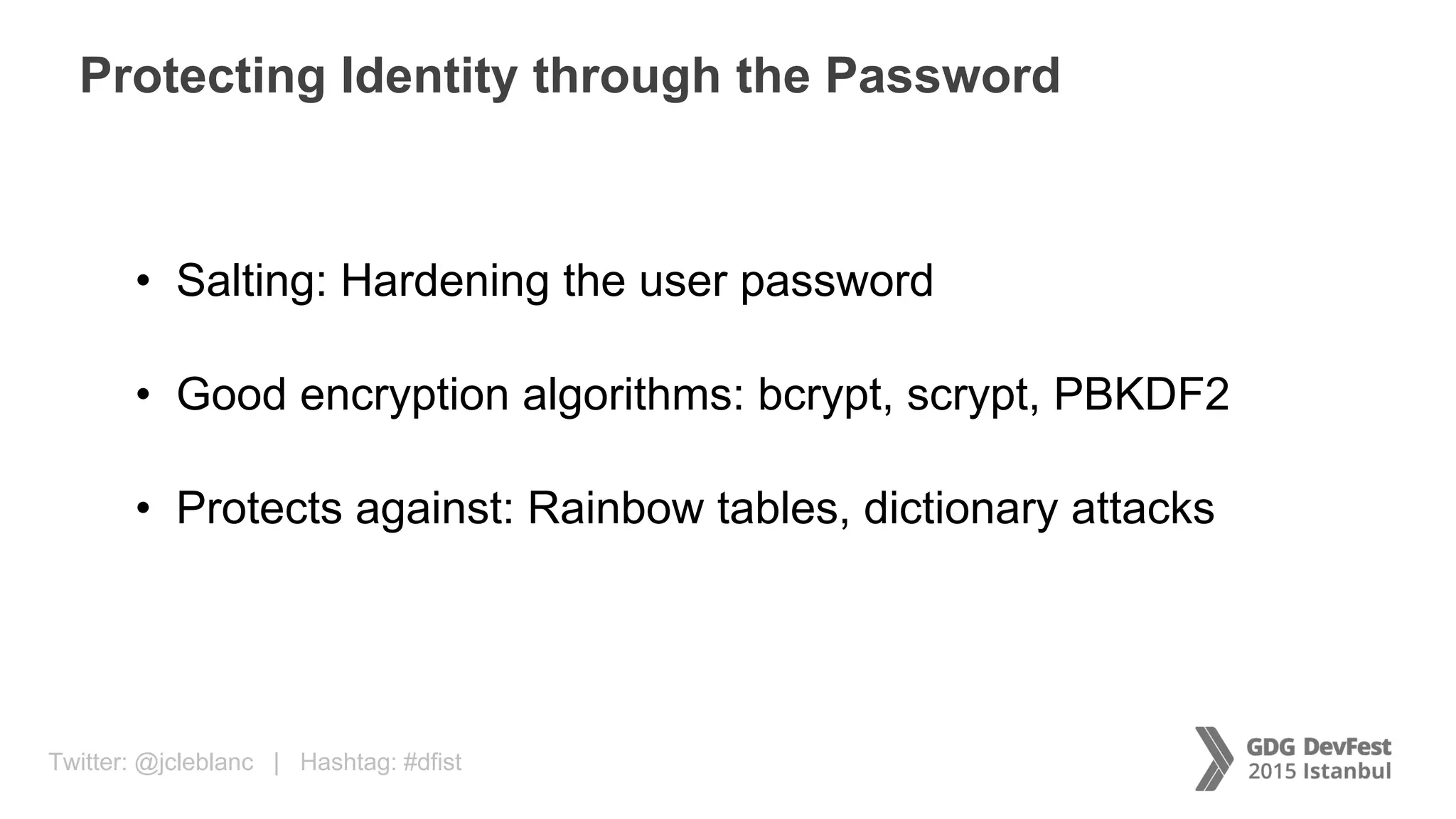
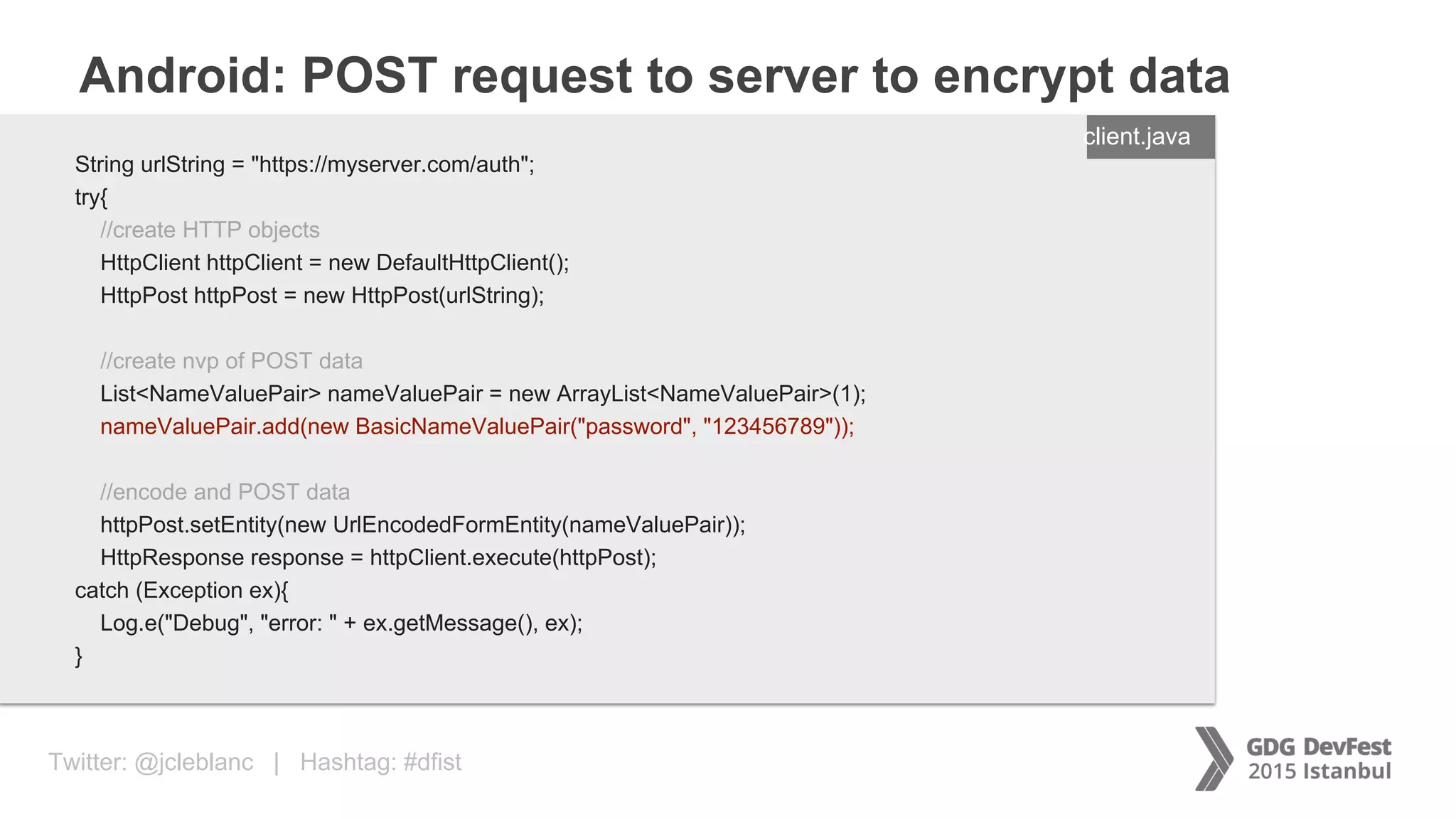
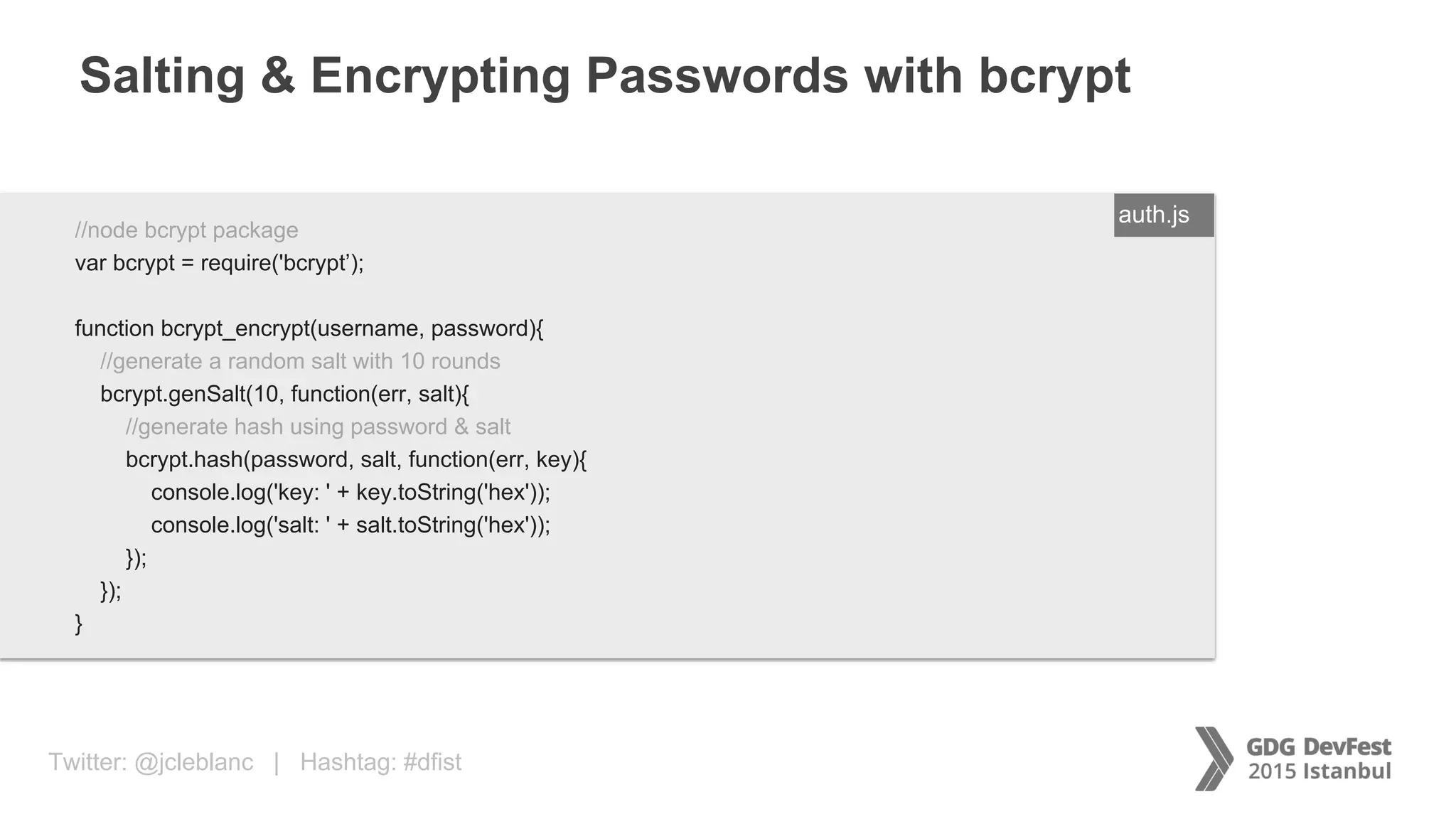
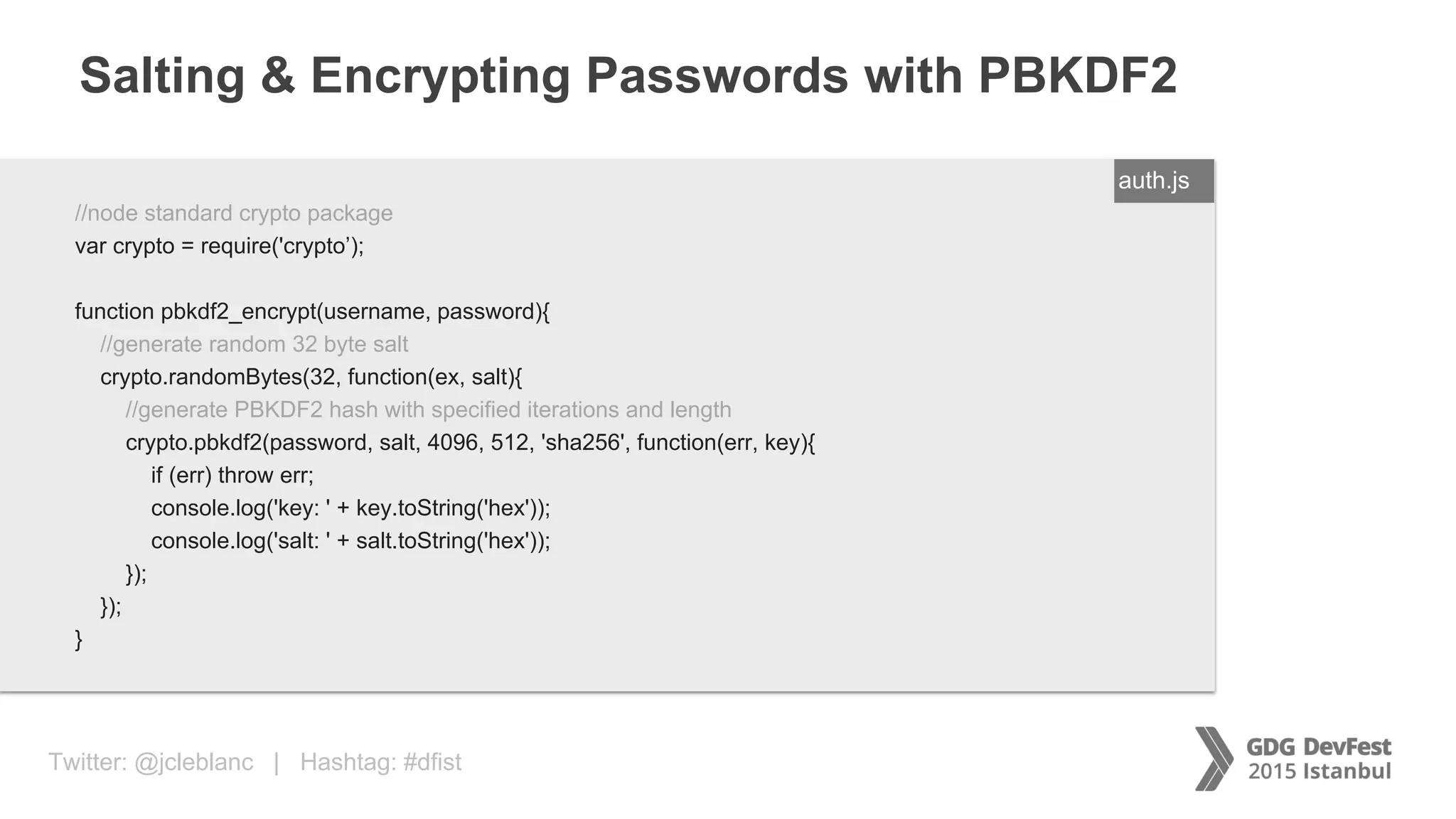
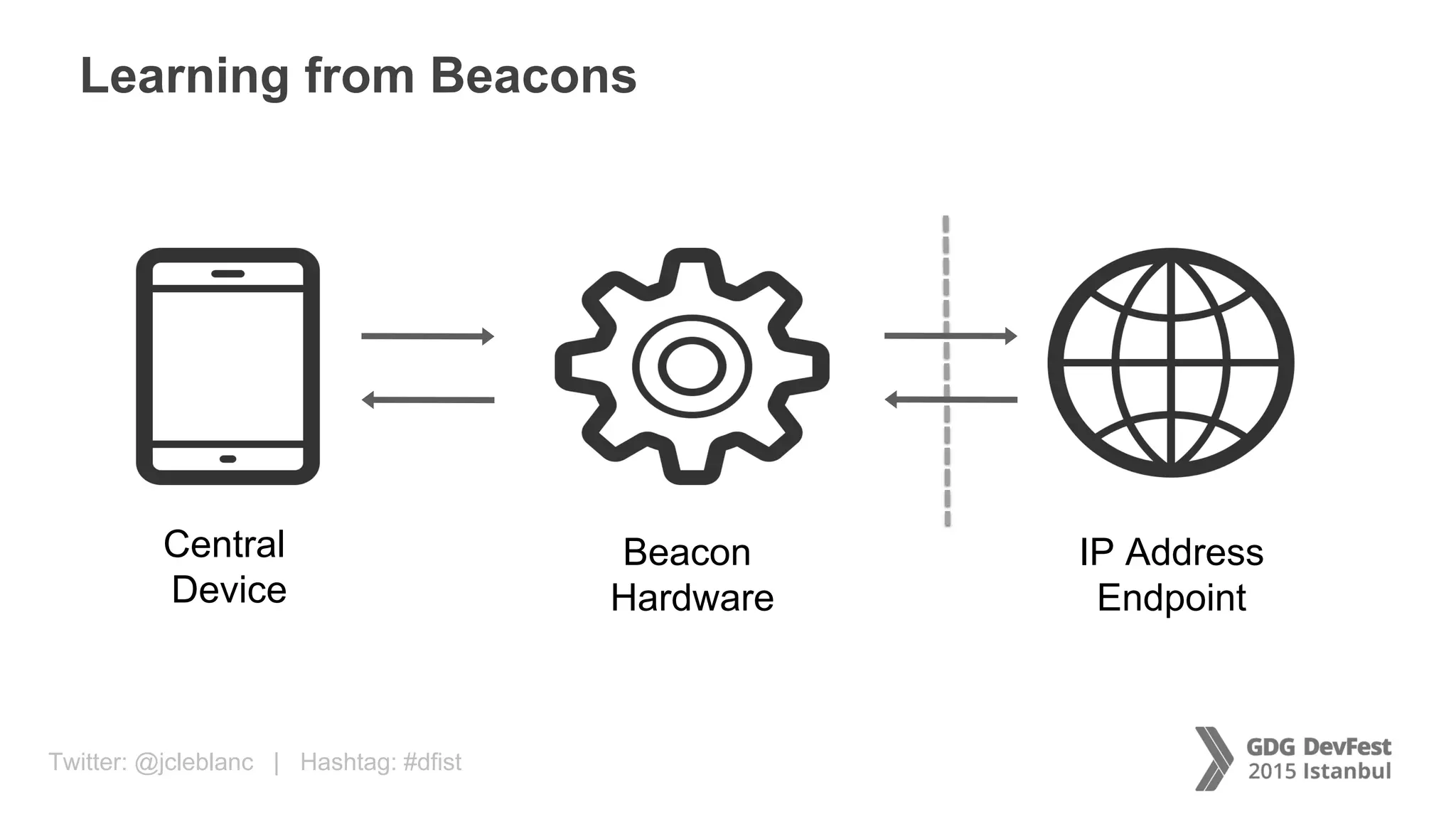
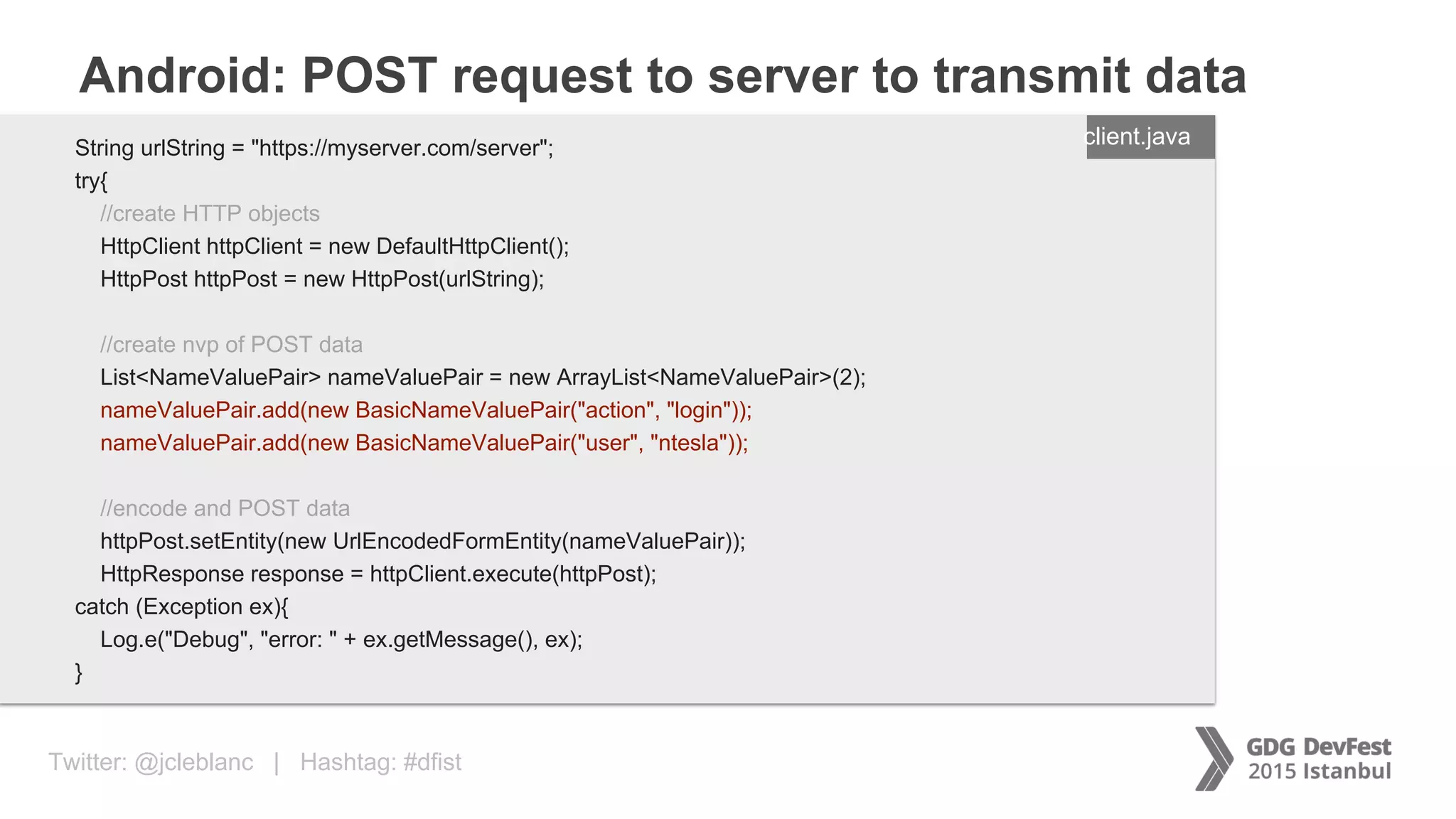
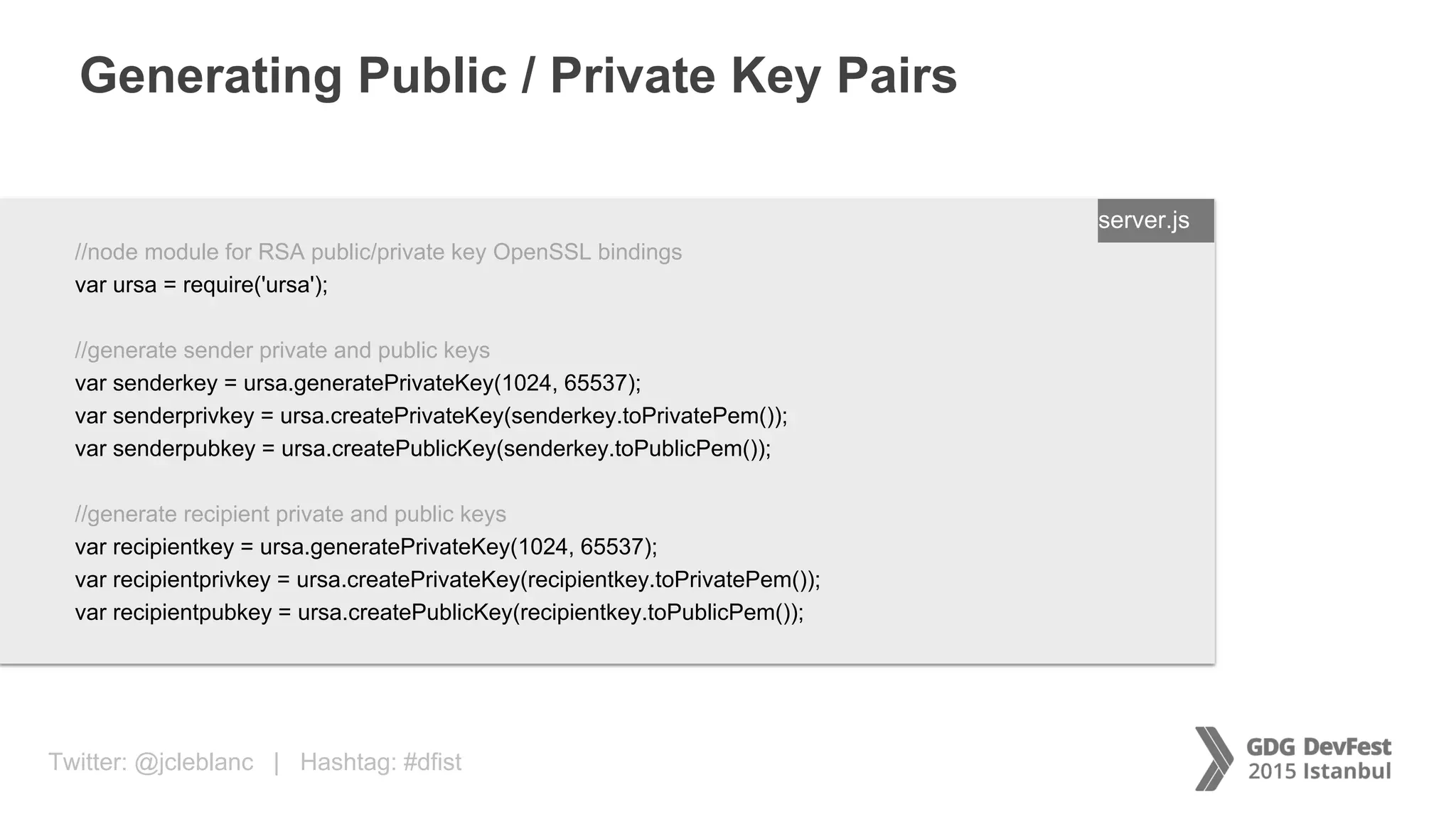
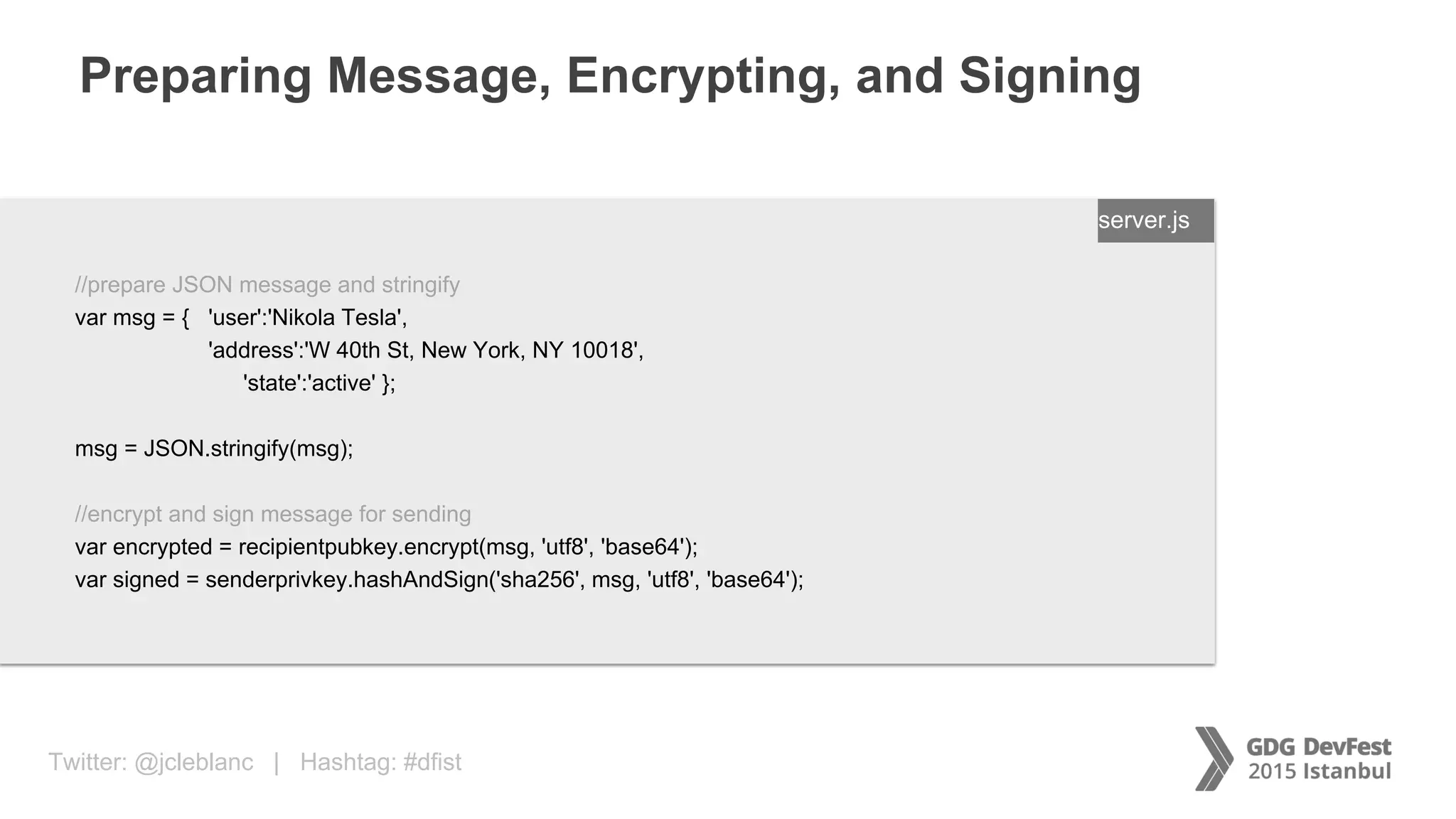
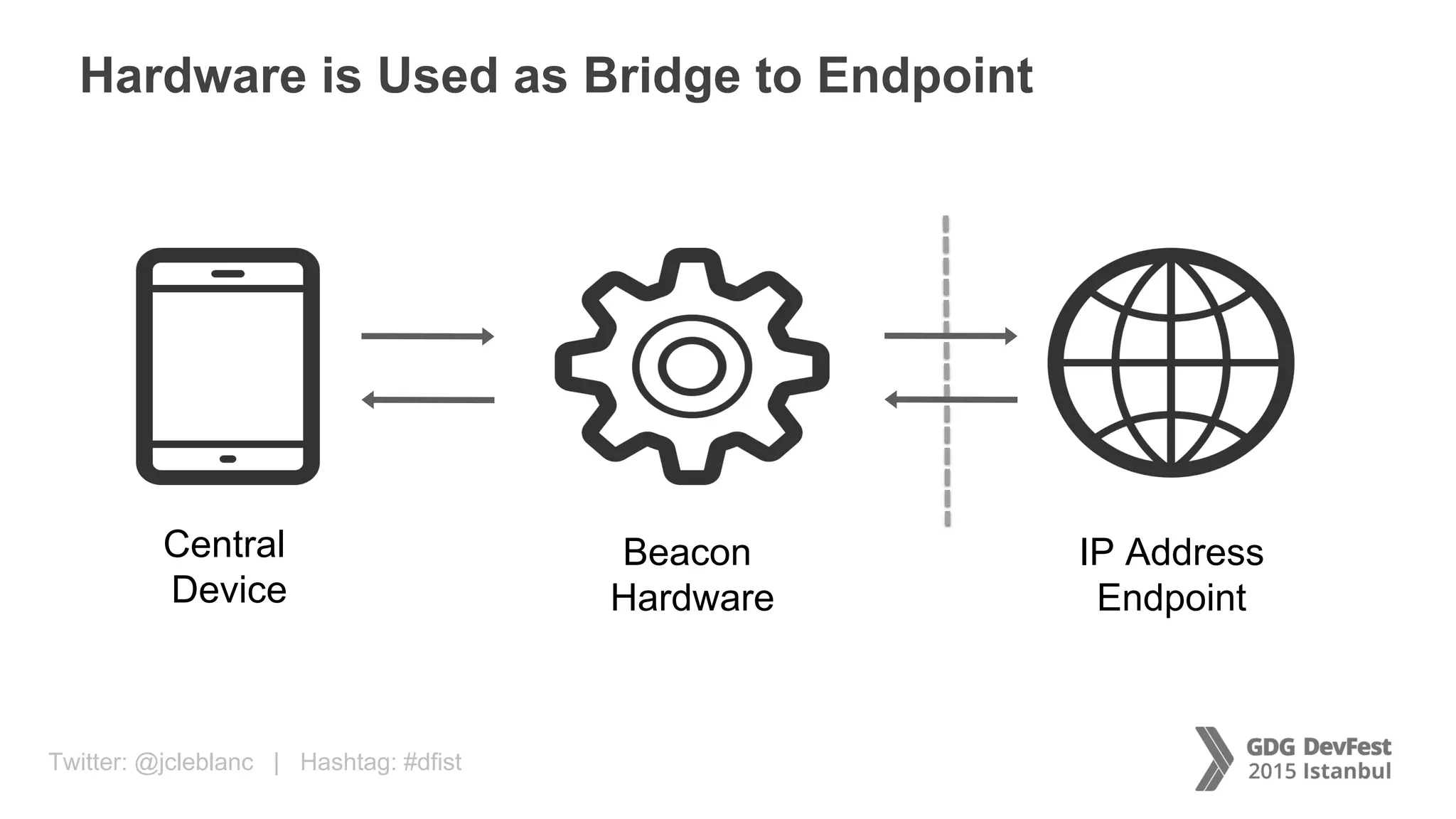
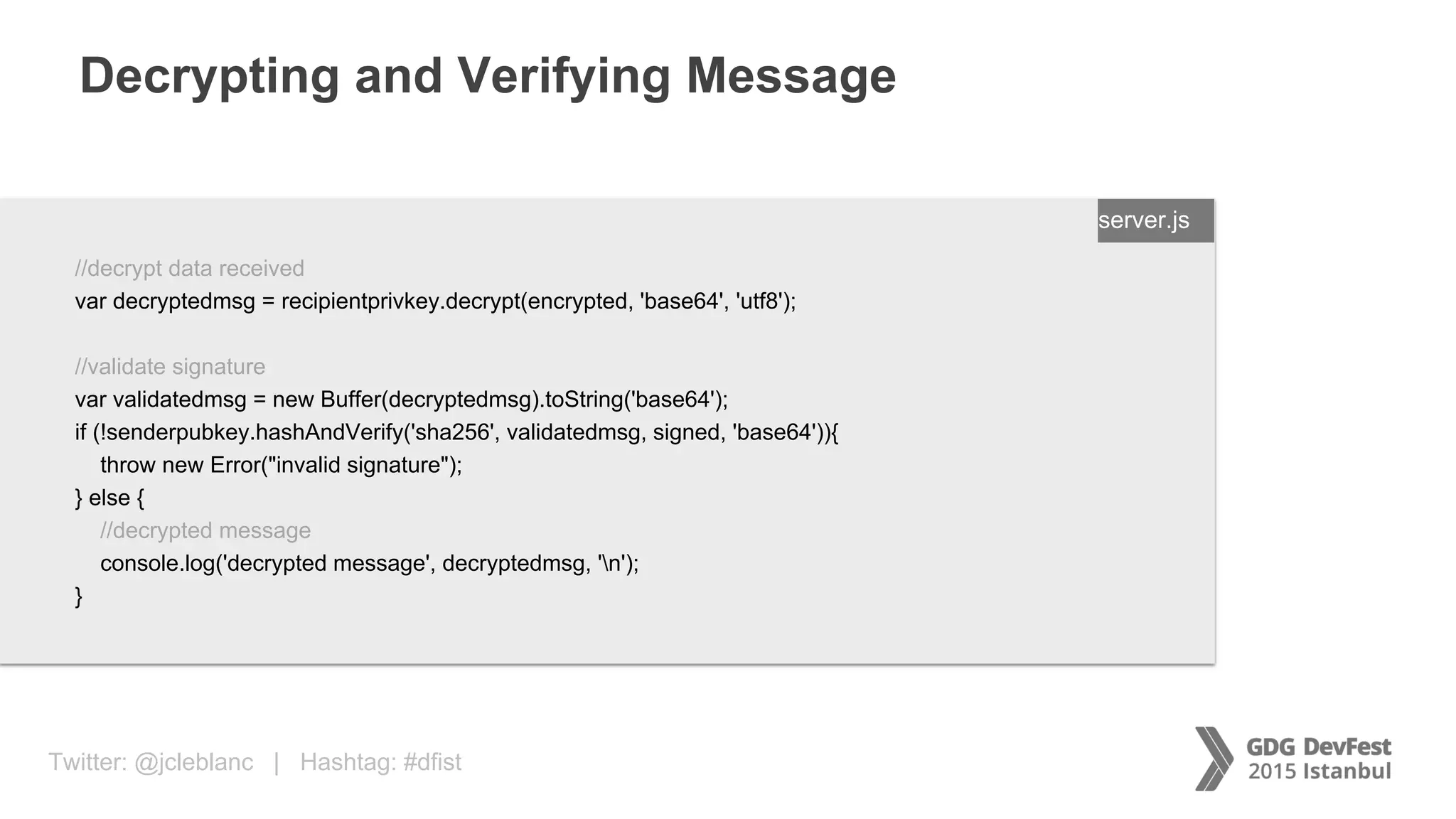
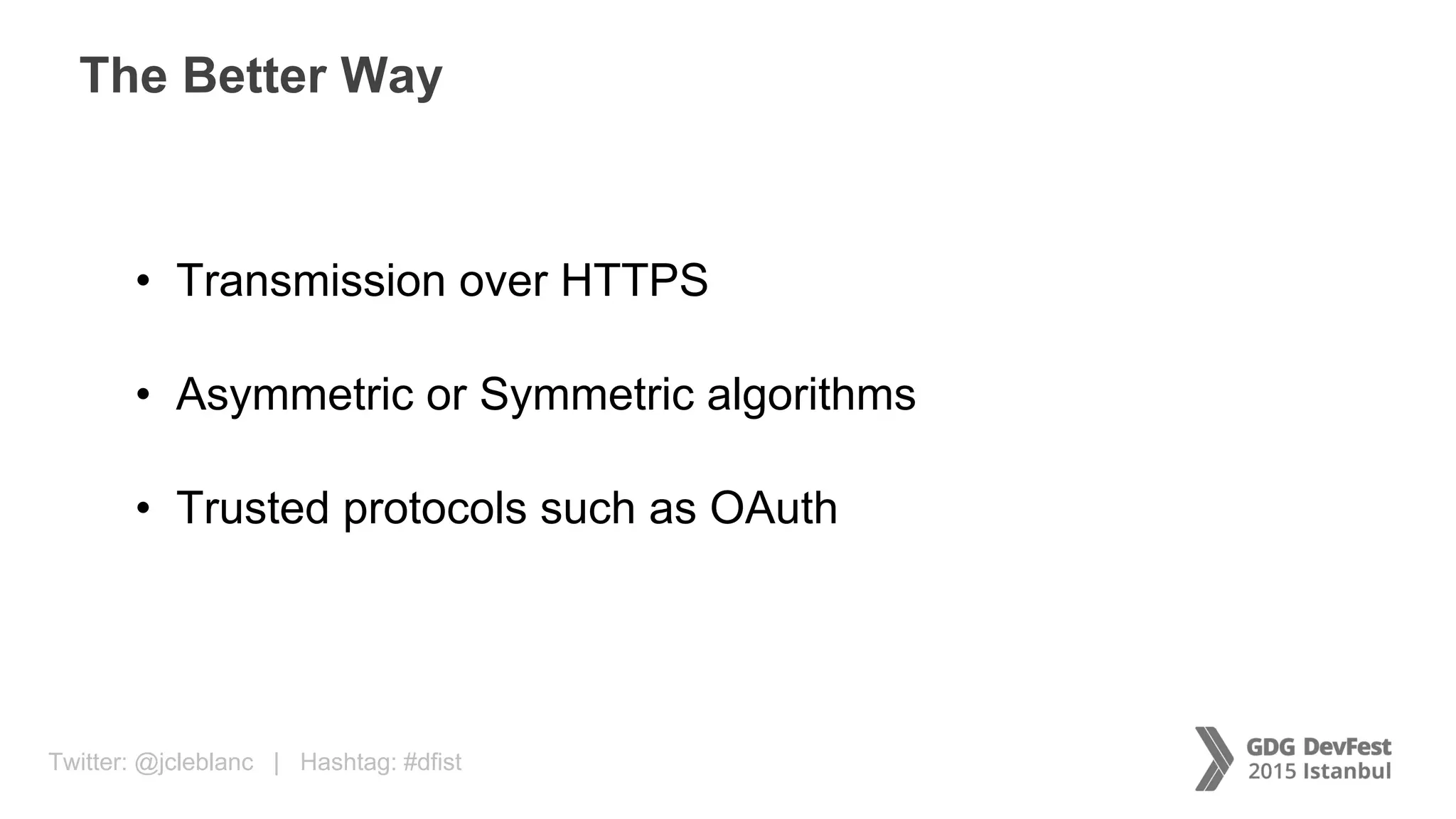
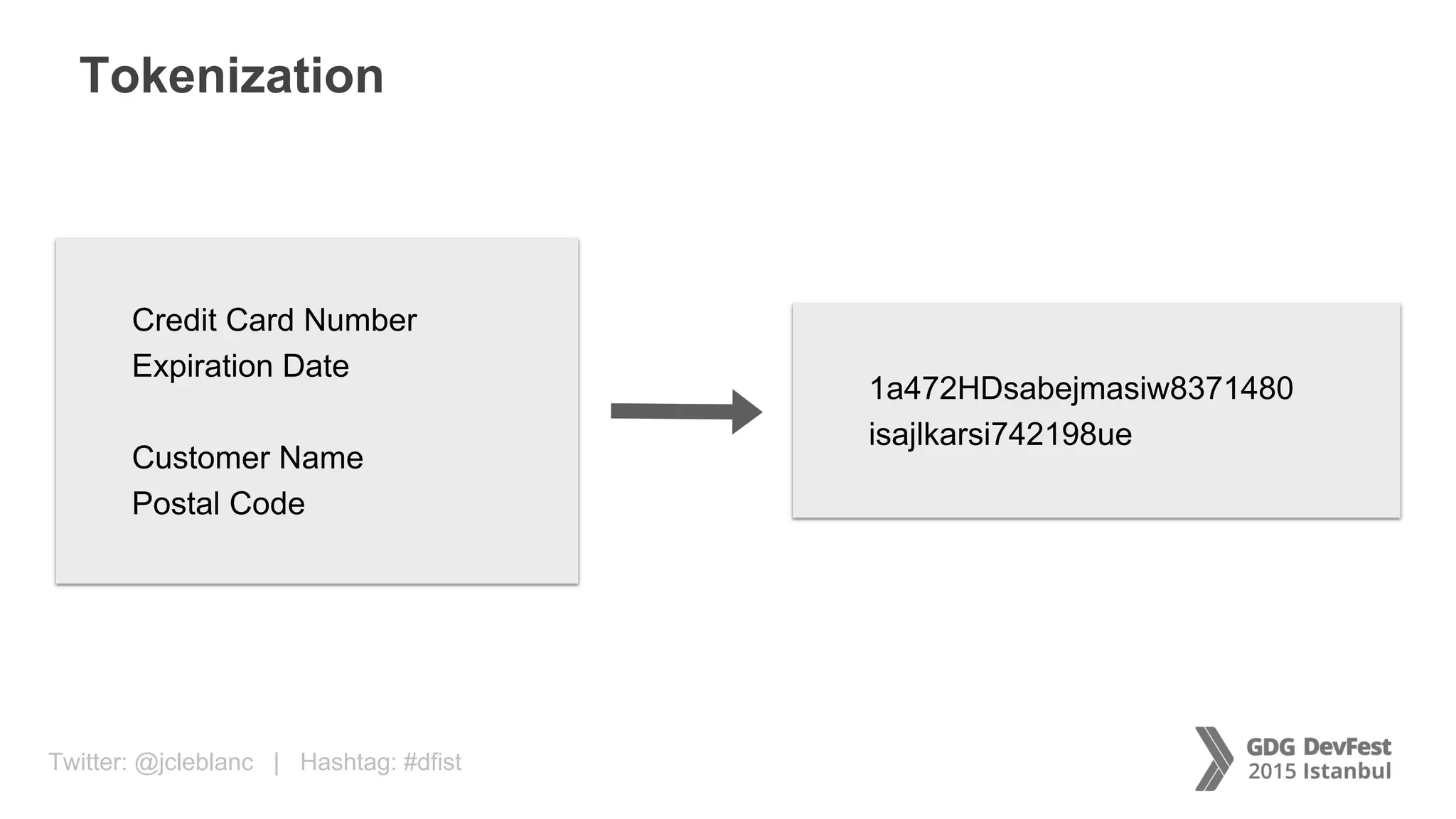
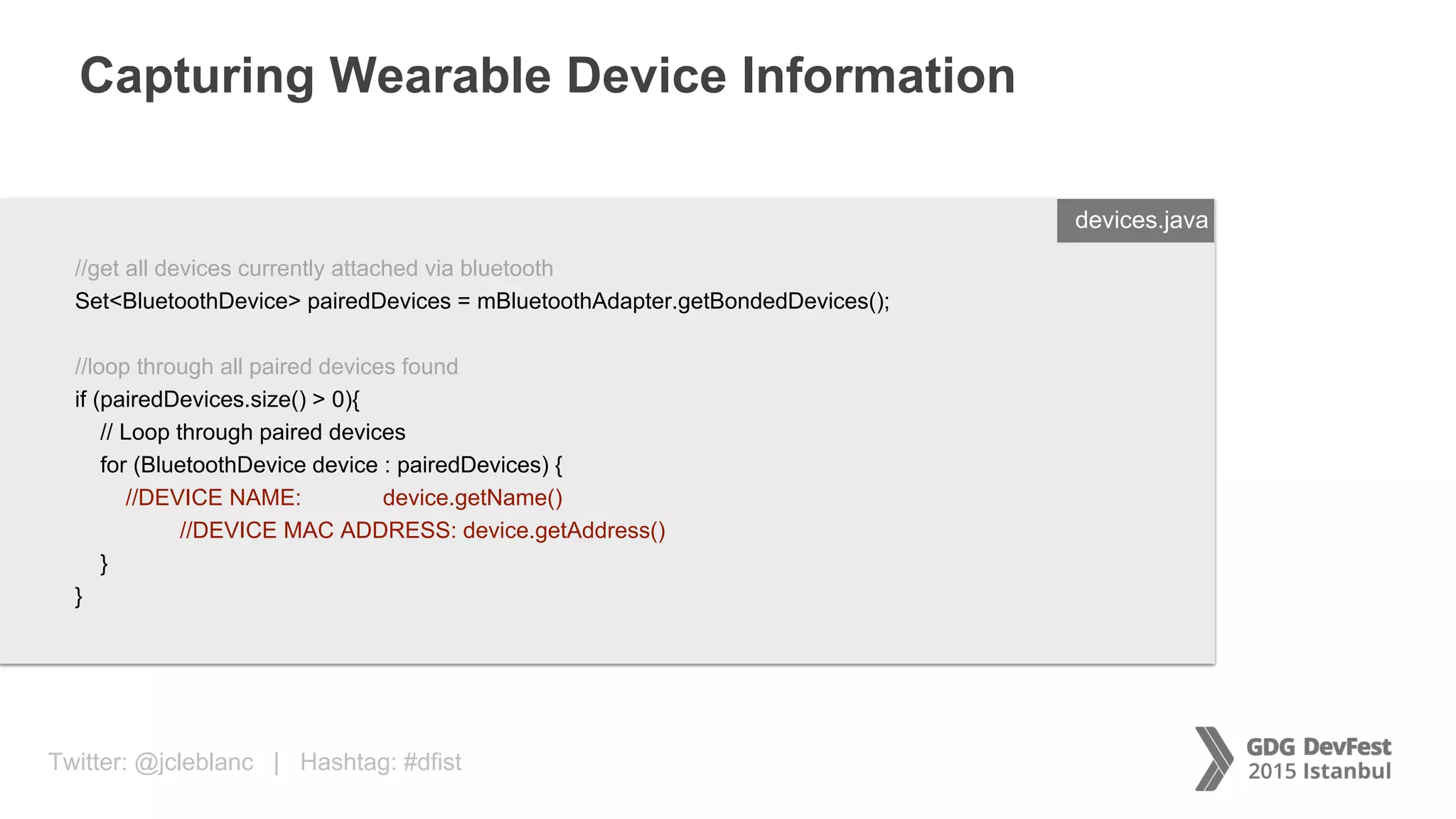
The document discusses secure payment practices across various communication media, focusing on identity protection, data integrity during transmission, and security for payment transactions. It highlights techniques for password protection, encryption methods, and the use of asymmetric and symmetric algorithms to secure data in motion. Additionally, it covers the importance of wearable technology in extending security measures and mentions key coding examples for implementing these practices.