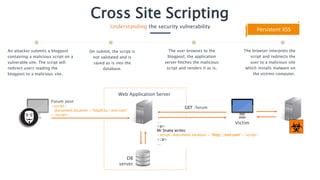
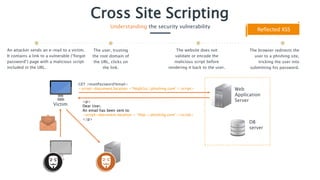
Cross-Site Scripting (XSS) is a security vulnerability that allows attackers to inject malicious scripts into users' browsers, potentially stealing credentials and compromising user data. There are three types of XSS: reflected, persistent, and DOM-based, each posing significant risks like data theft or malware installation. To prevent XSS, it's crucial to properly encode user input, employ server-side validation against a whitelist, and use security features like HTTP headers and content security policies.