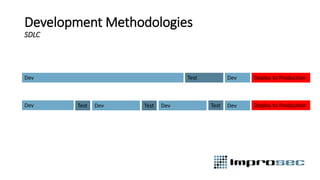
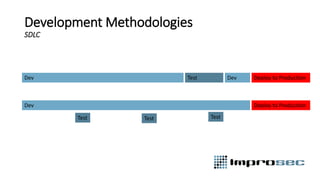
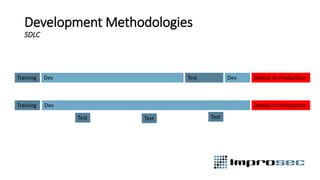
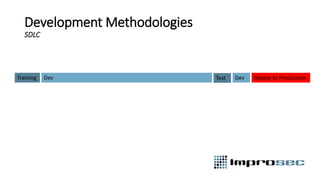
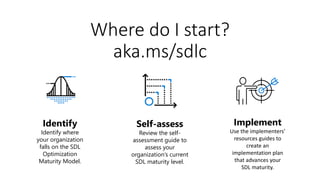
The document discusses security best practices across the software development lifecycle (SDLC). It covers:
- The Microsoft Security Development Lifecycle (SDL) methodology which includes activities like threat modeling, security testing, using approved tools and cryptography standards, managing third-party components, and establishing an incident response process.
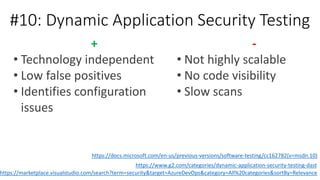
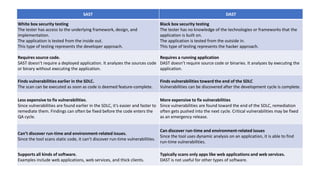
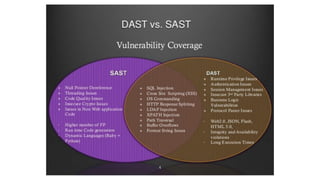
- Static and dynamic application security testing (SAST and DAST) - SAST analyzes source code for vulnerabilities while DAST tests running applications. Both have tradeoffs in terms of when issues are found, expenses to fix, and what types of vulnerabilities are discovered.
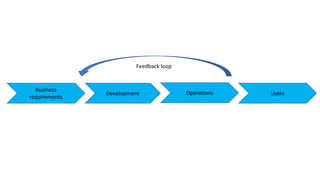
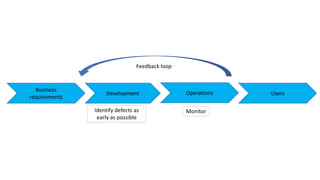
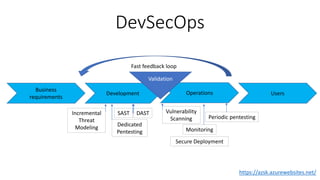
- DevSecOps practices like integrating security activities into each stage of development through techniques like incremental threat modeling, automated testing, and continuous