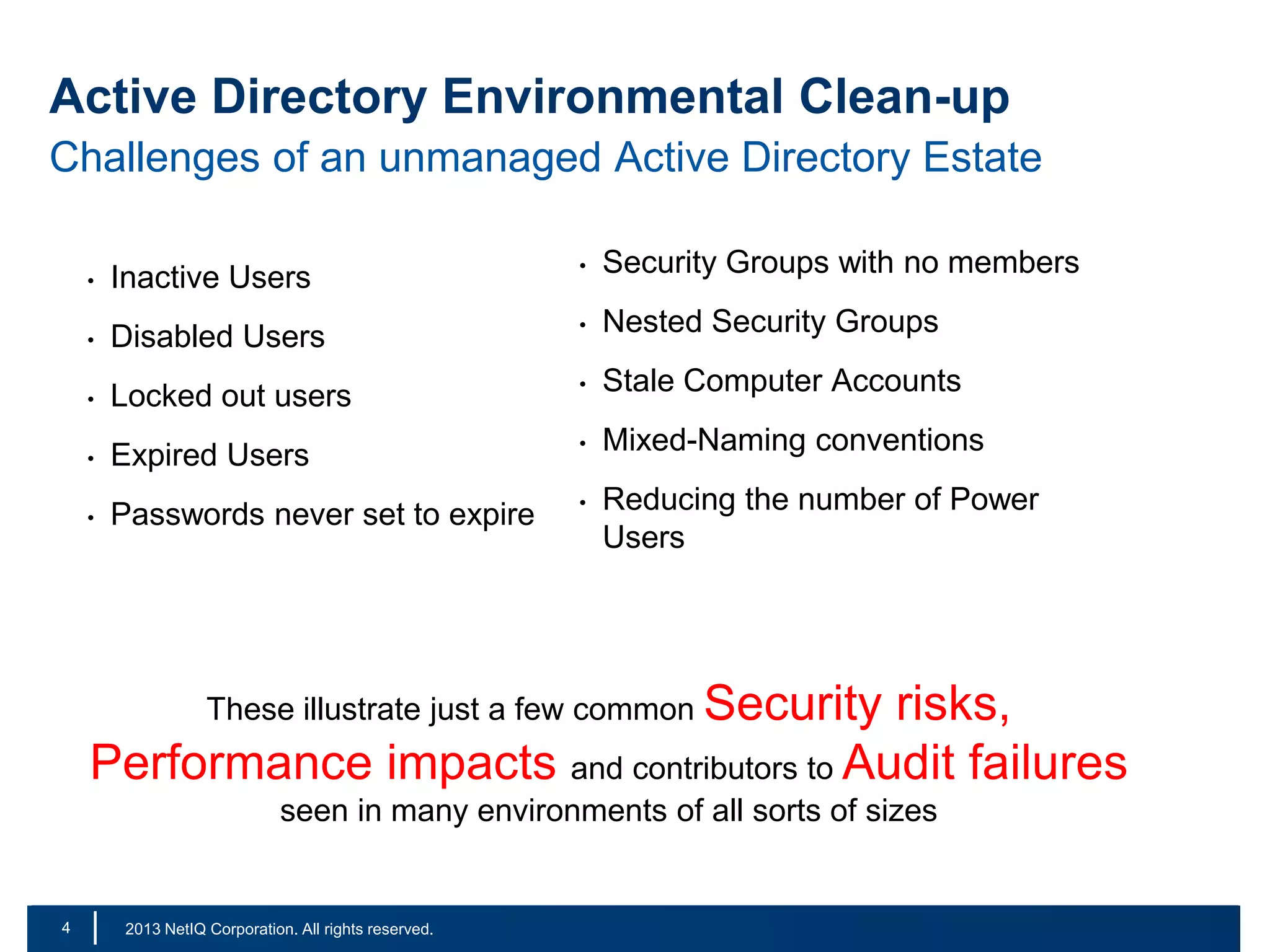
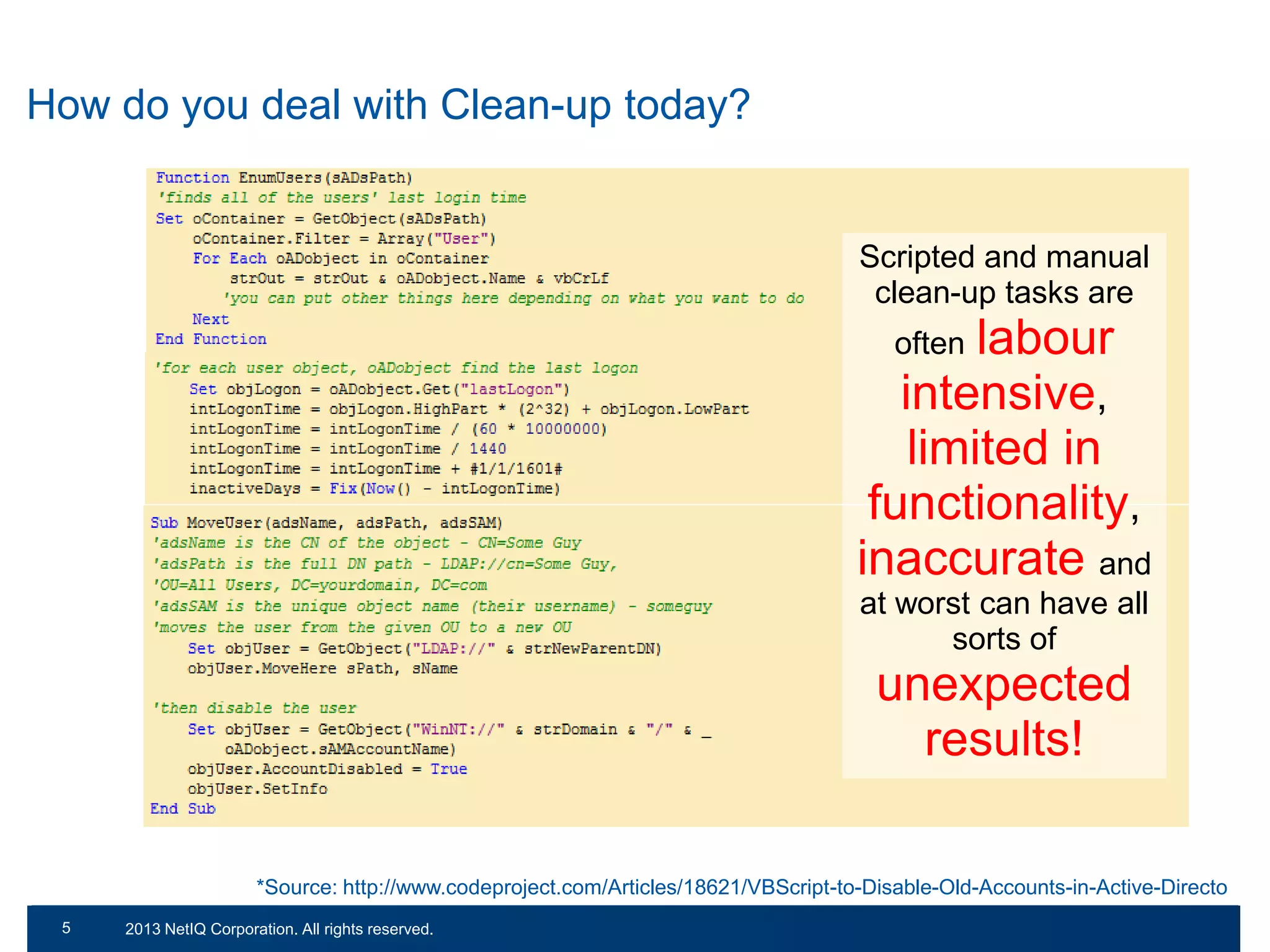
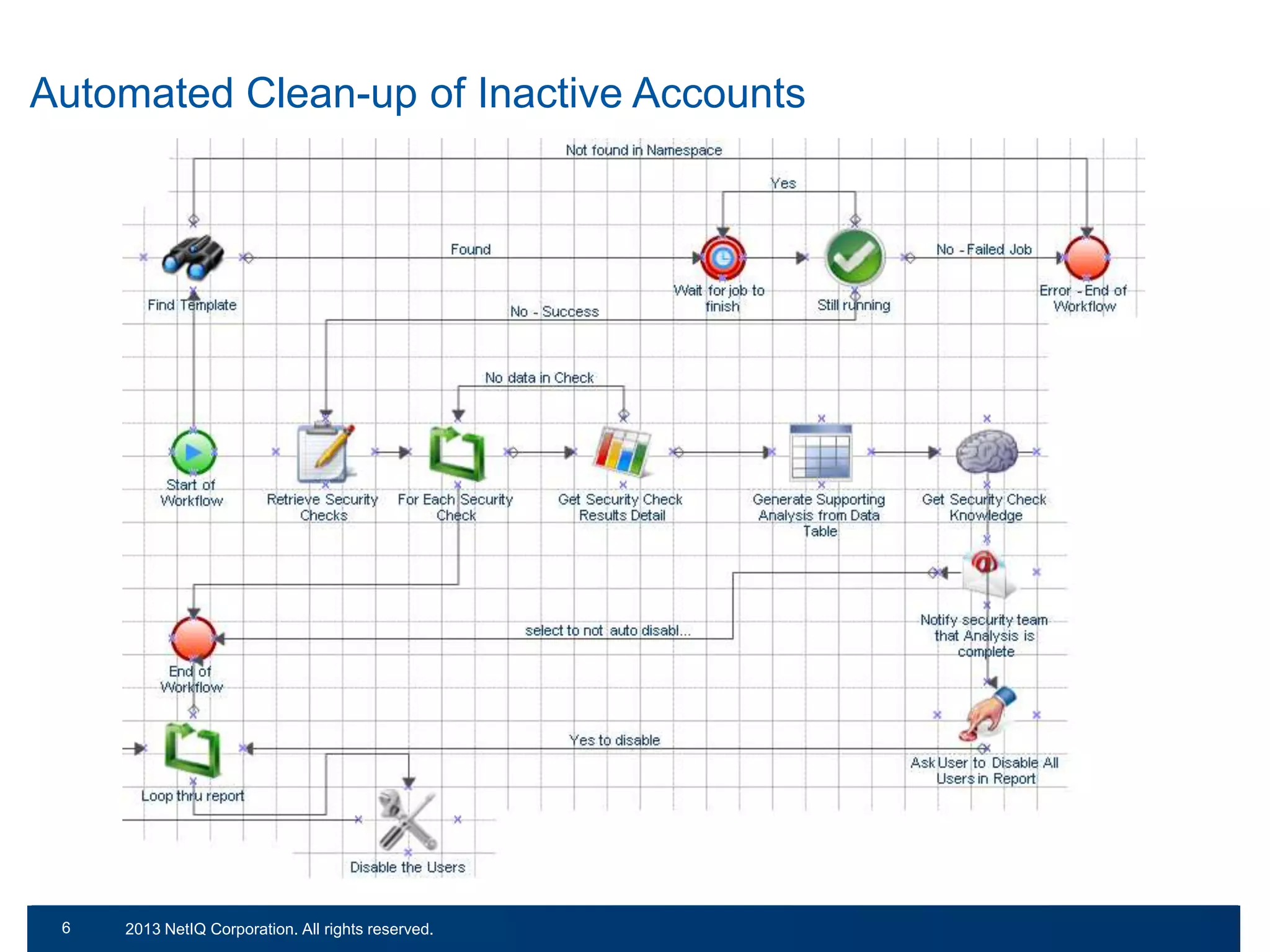
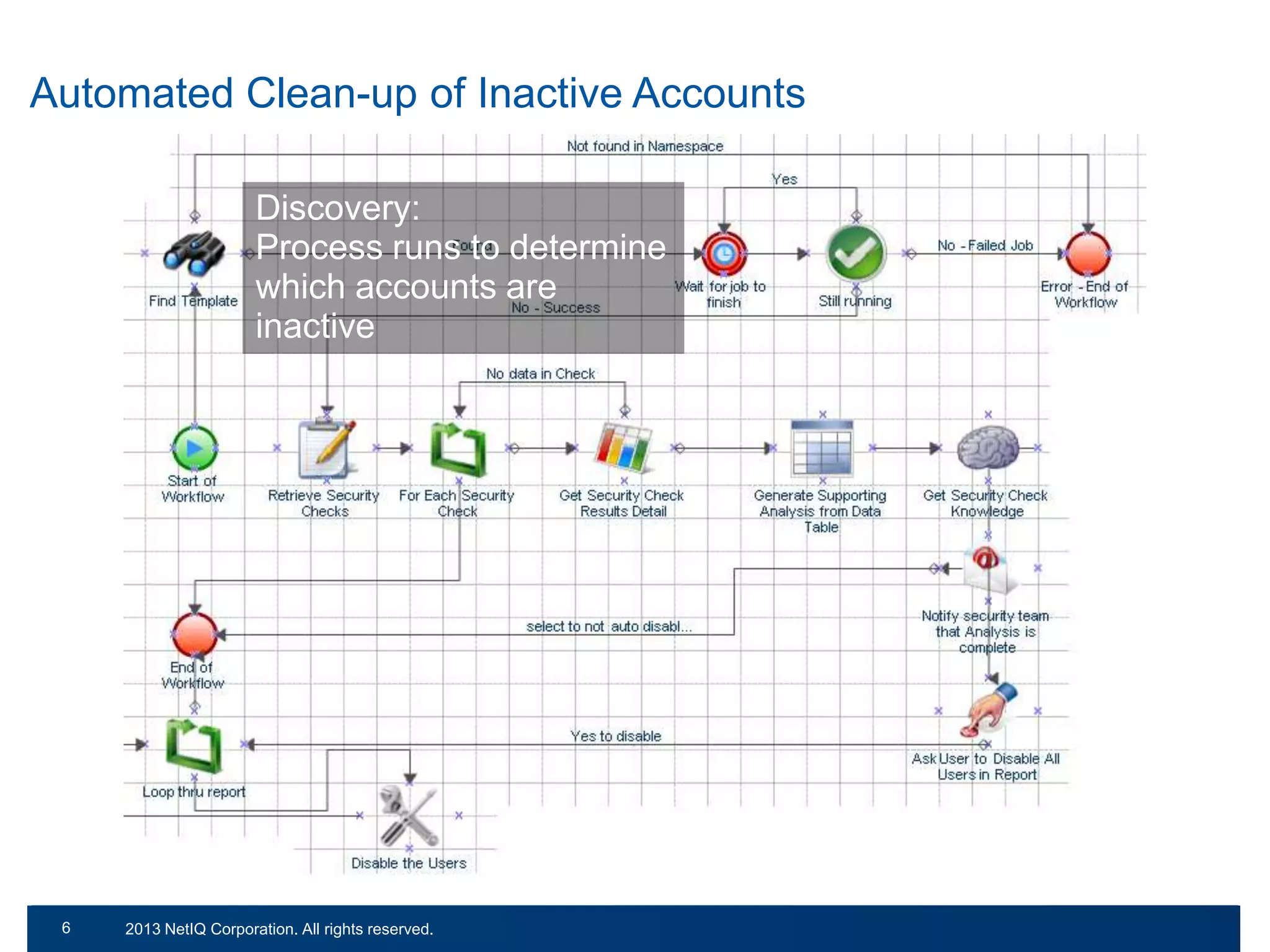
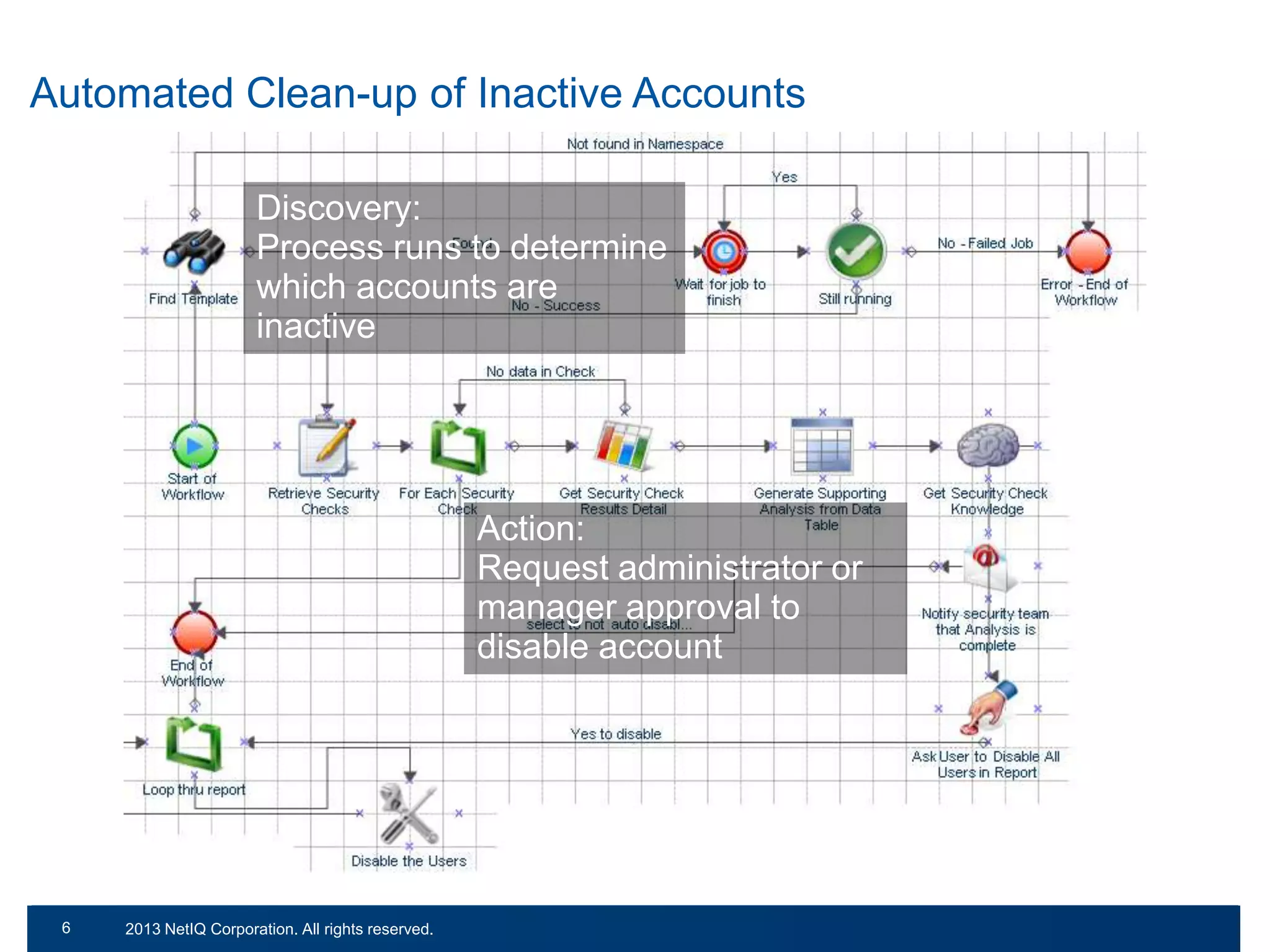
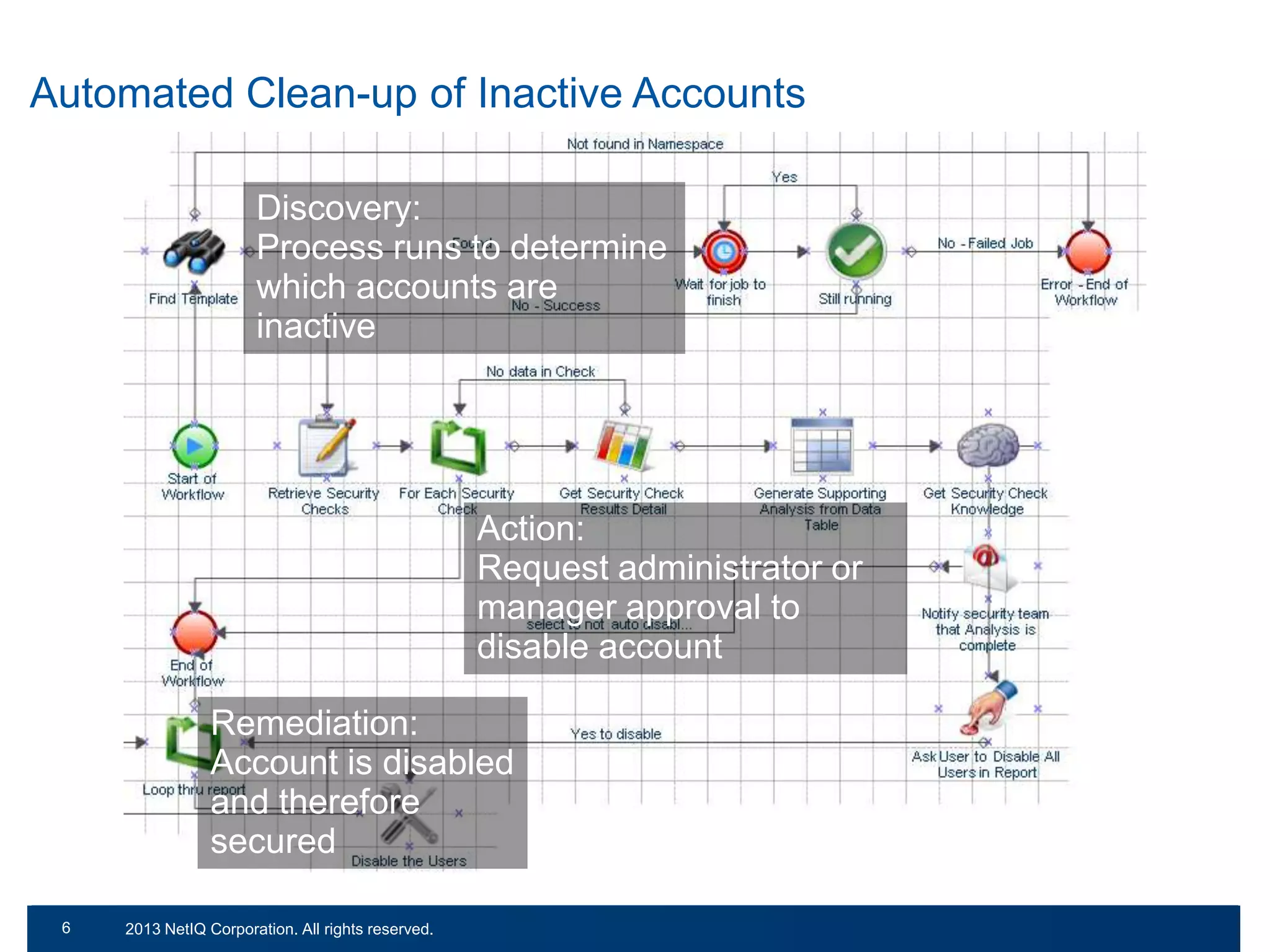
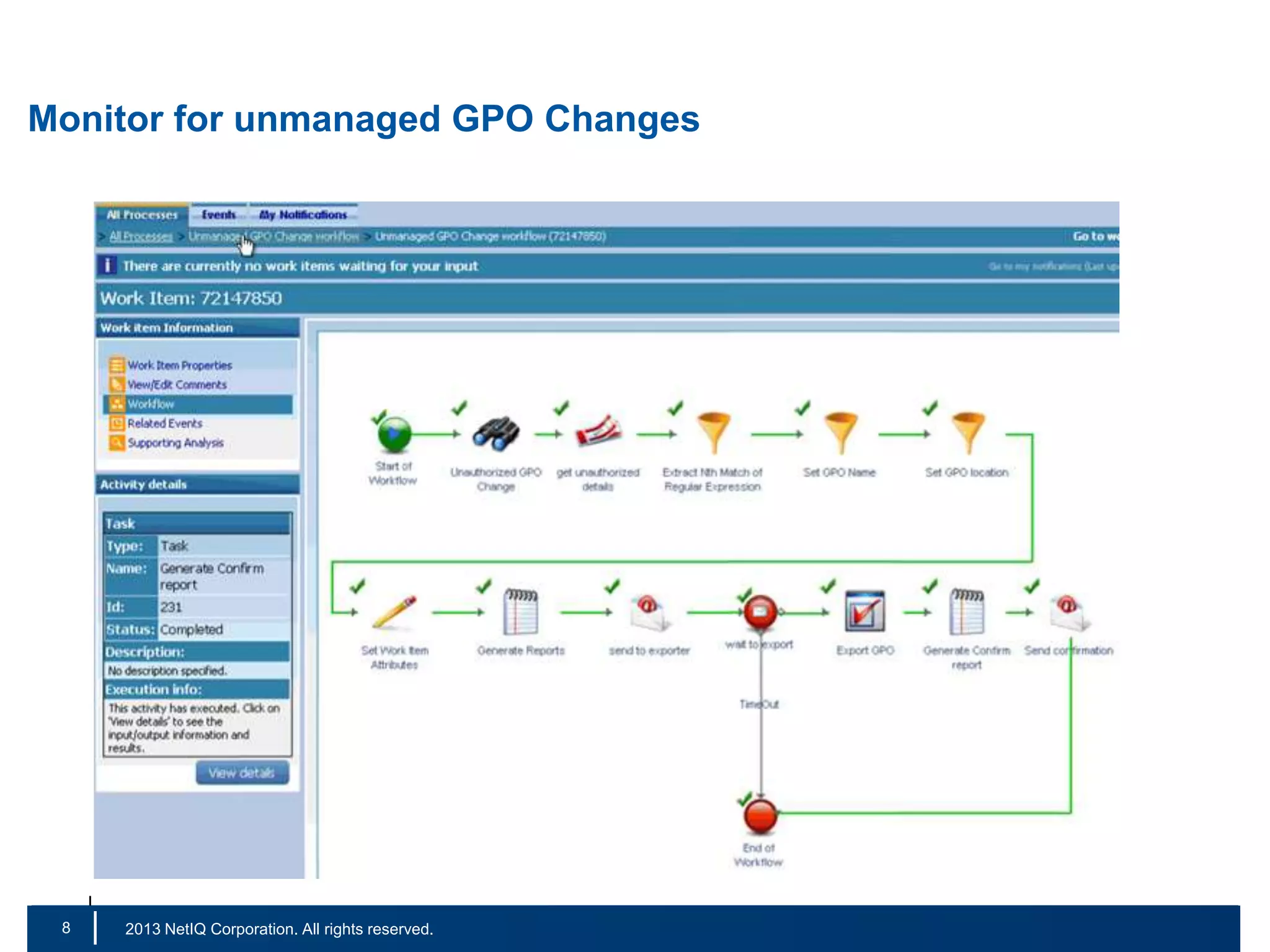
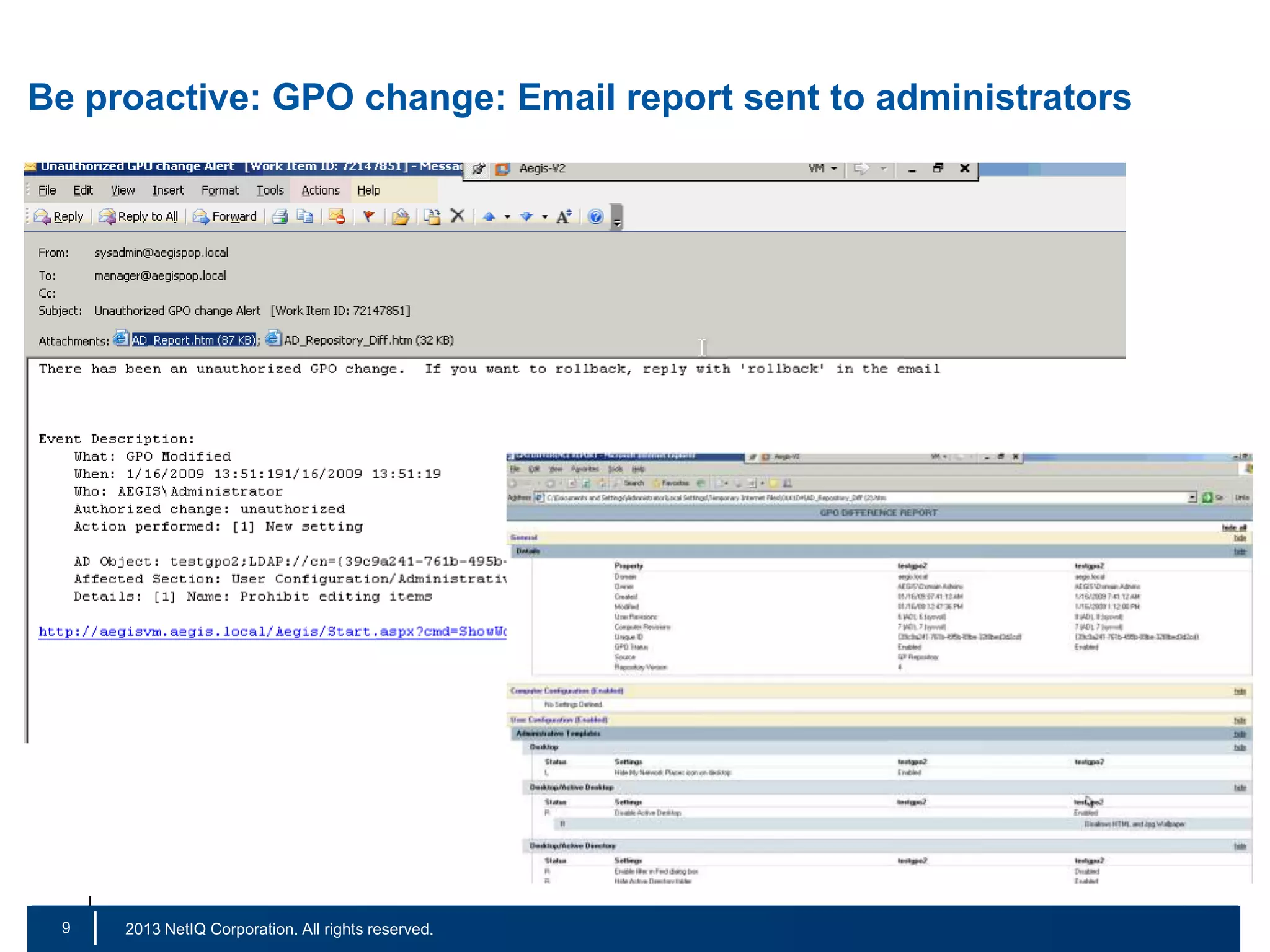
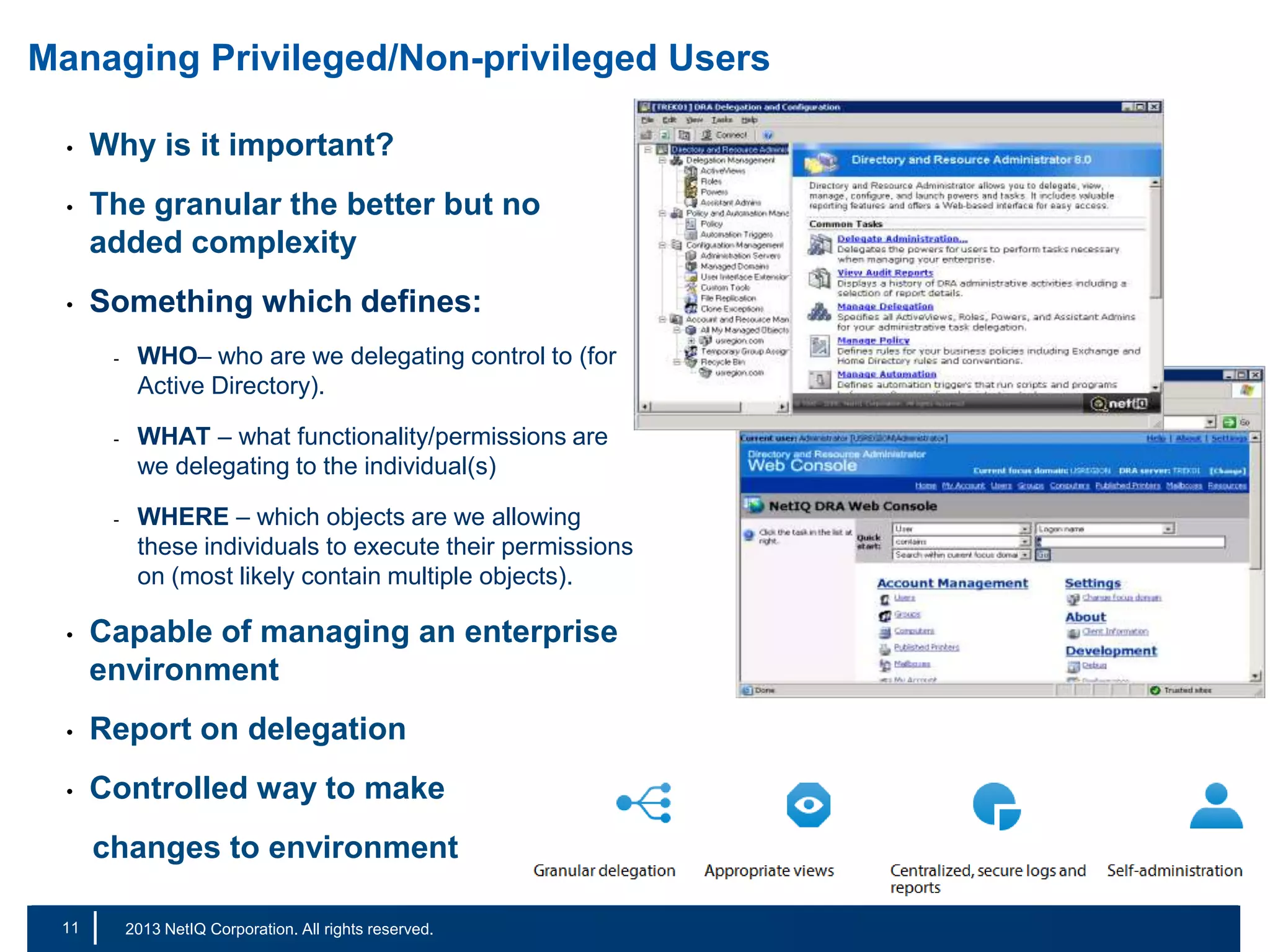
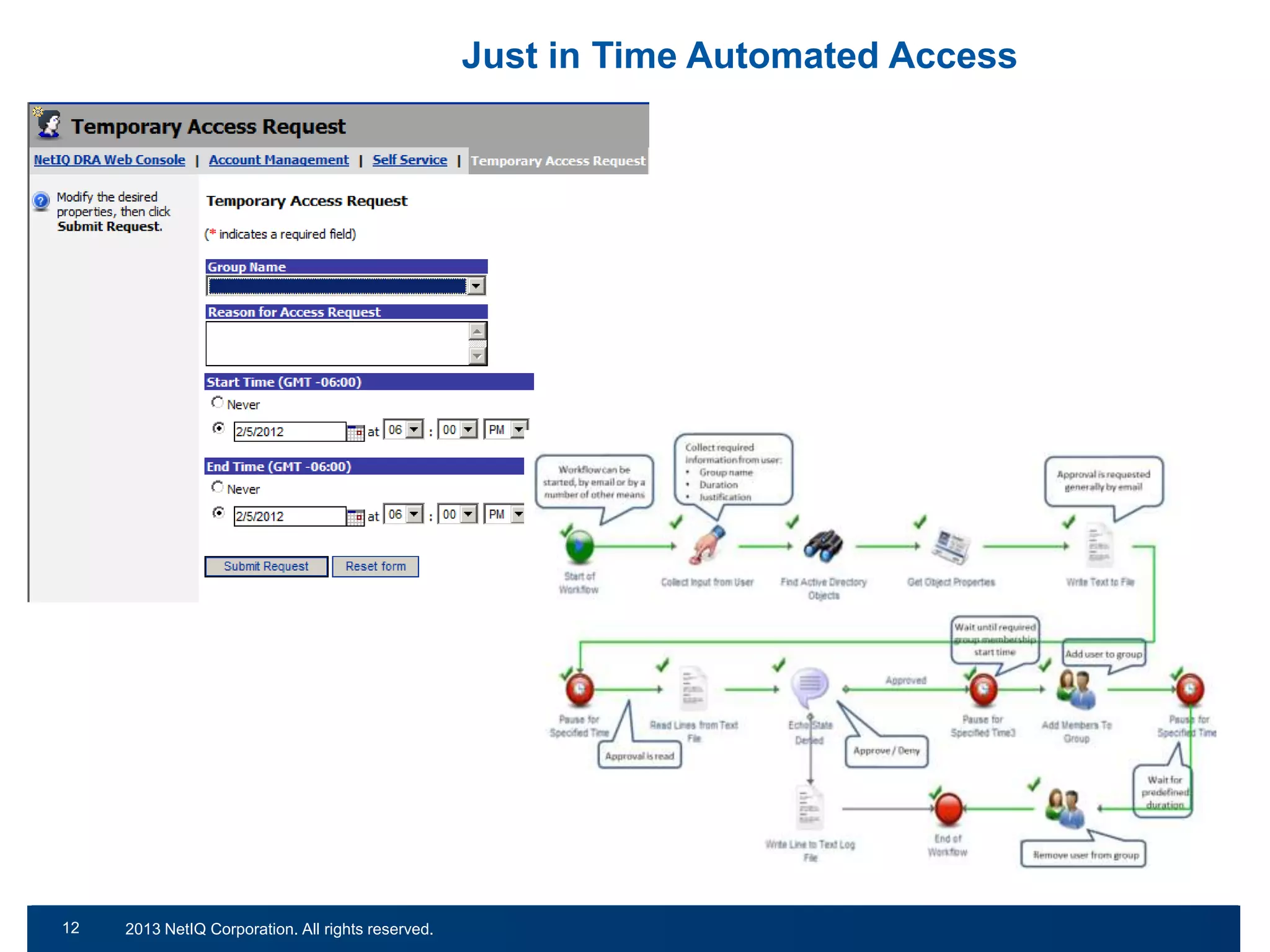
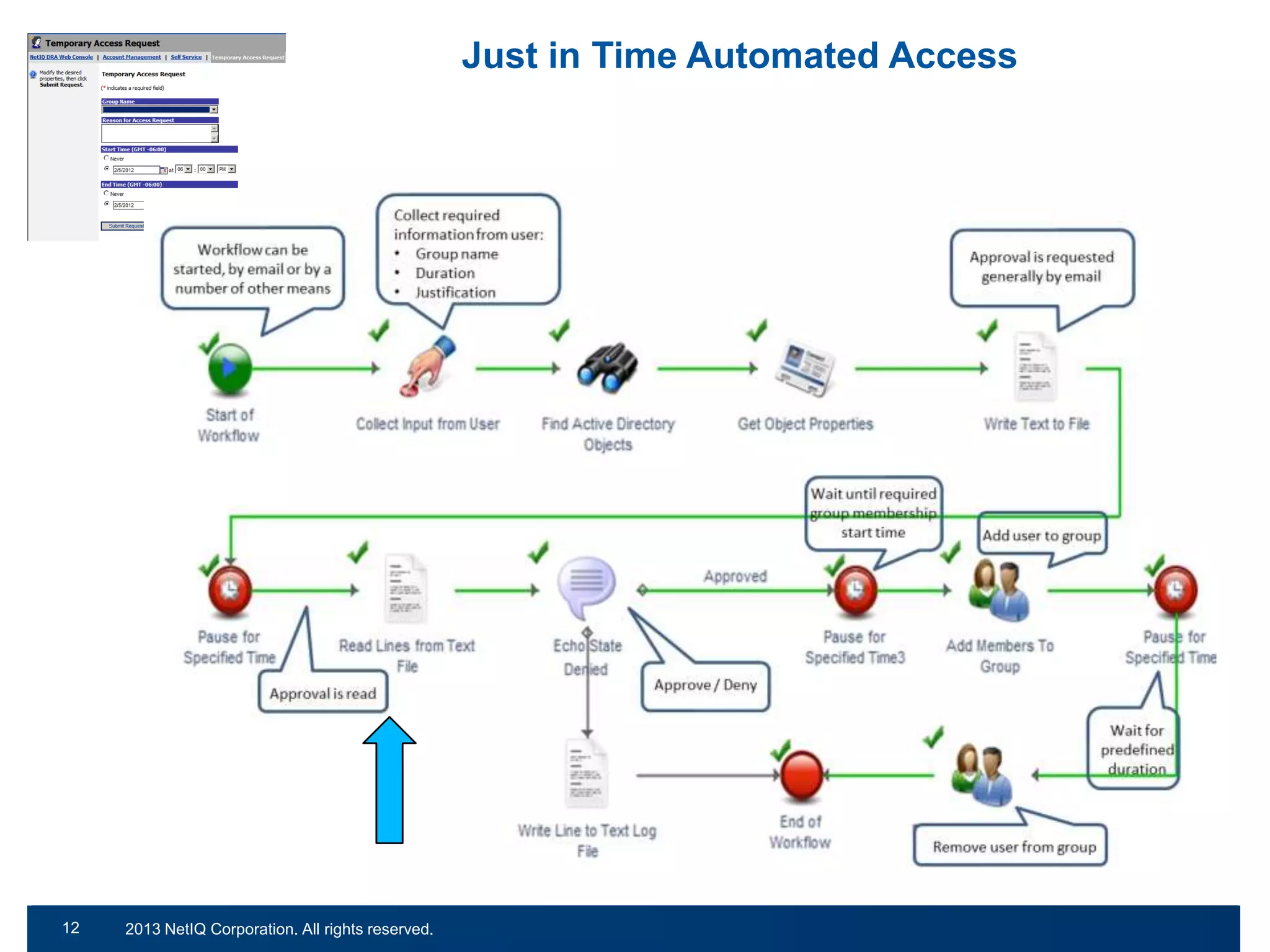
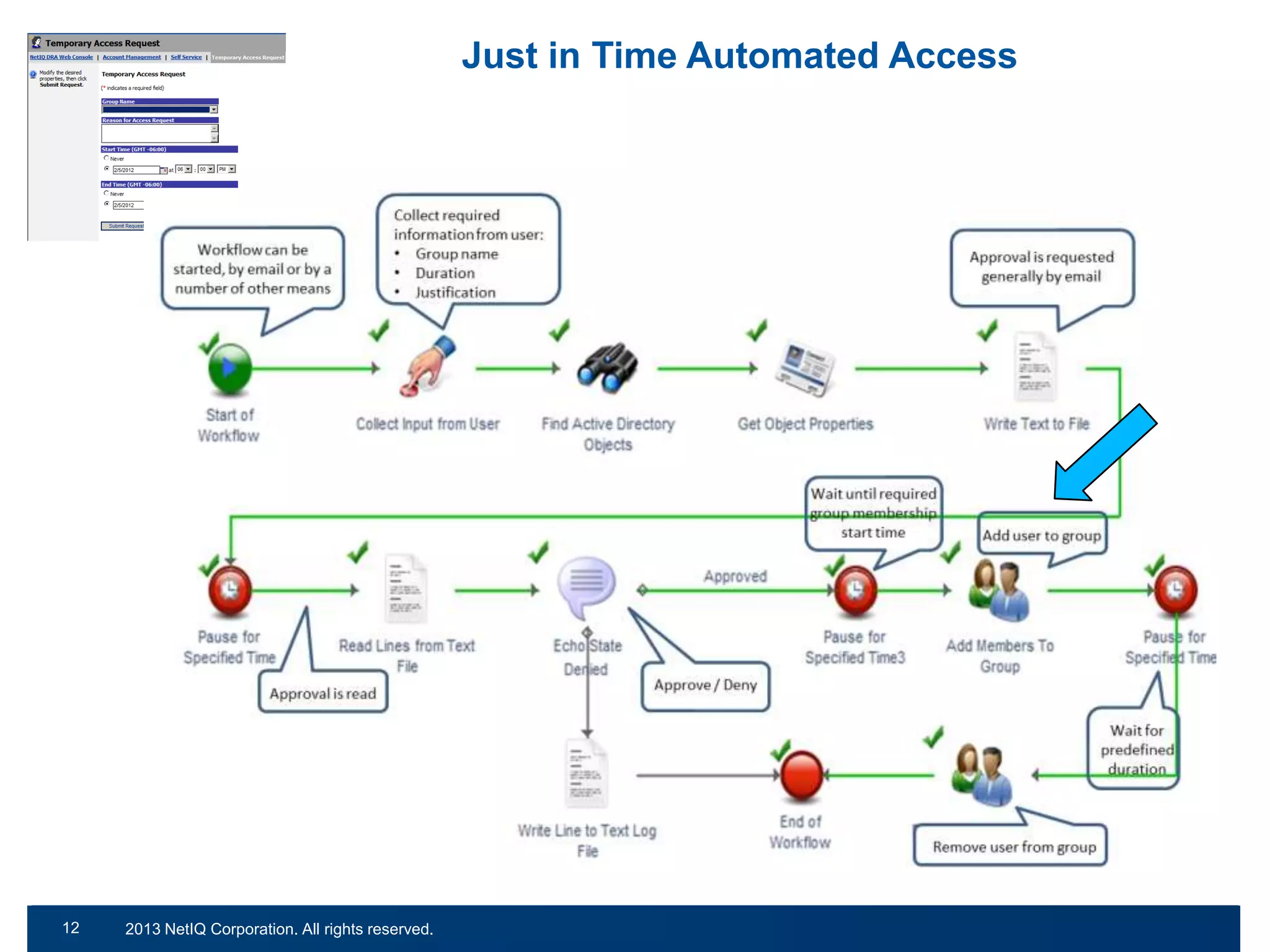
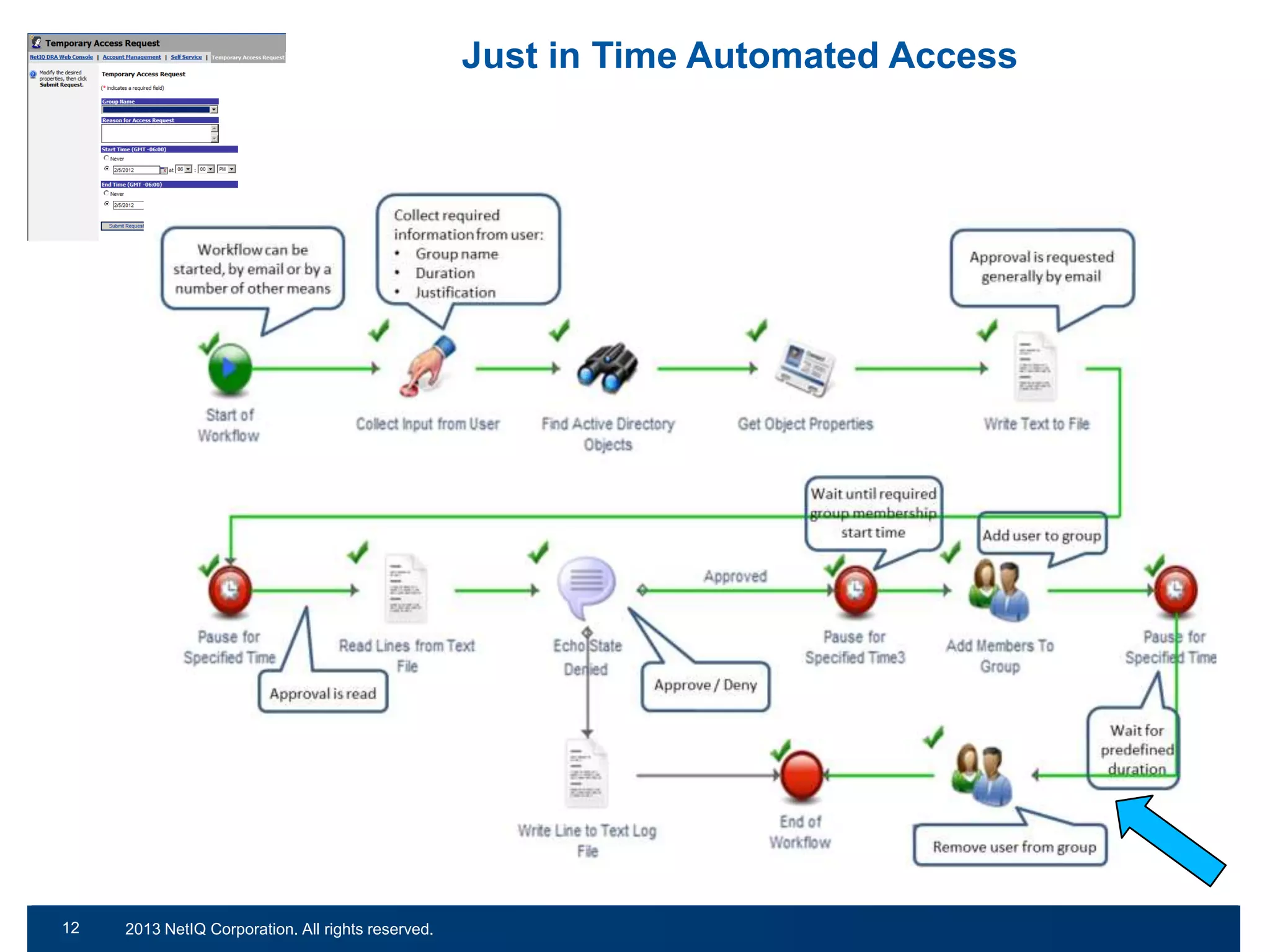
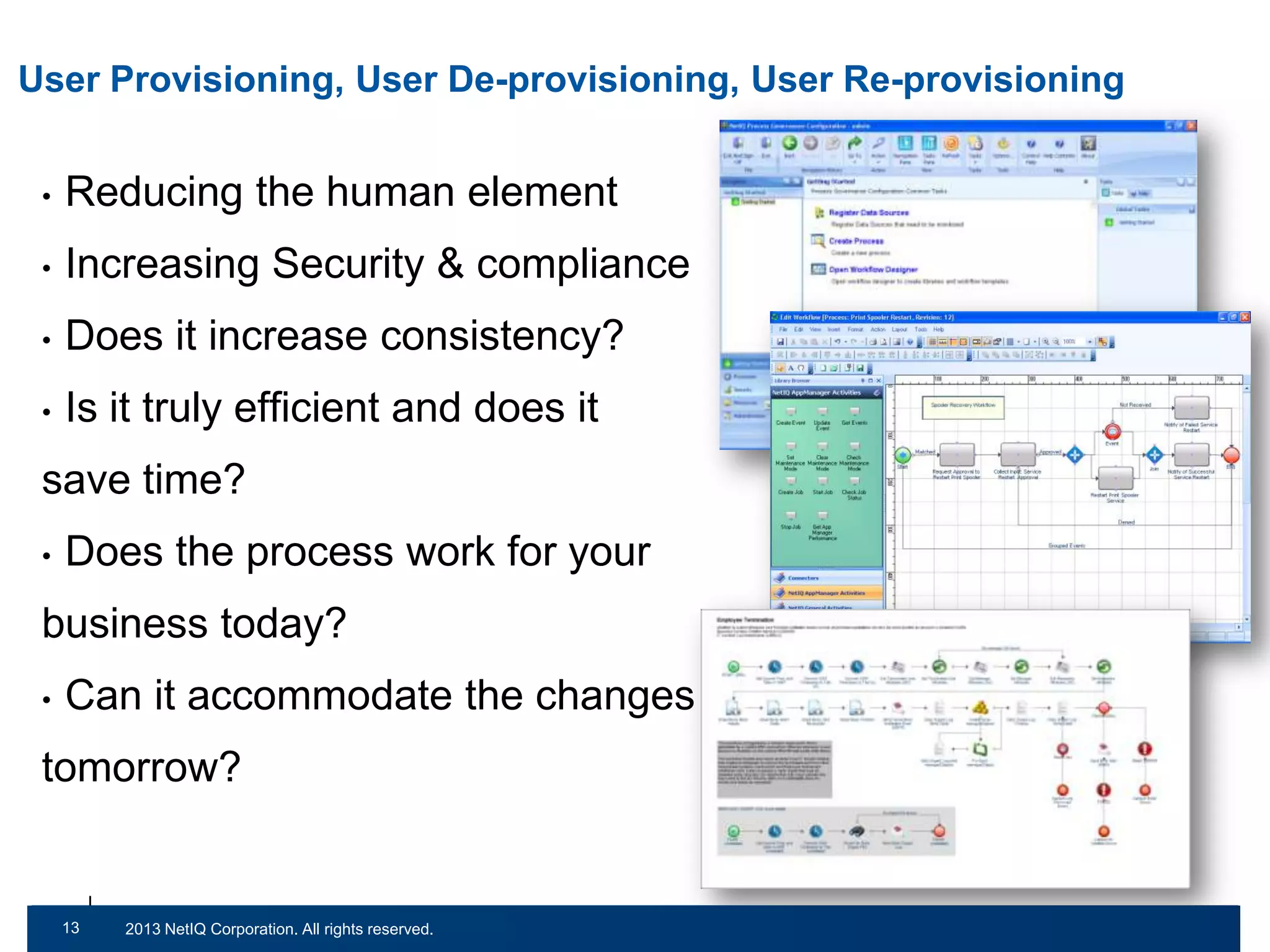
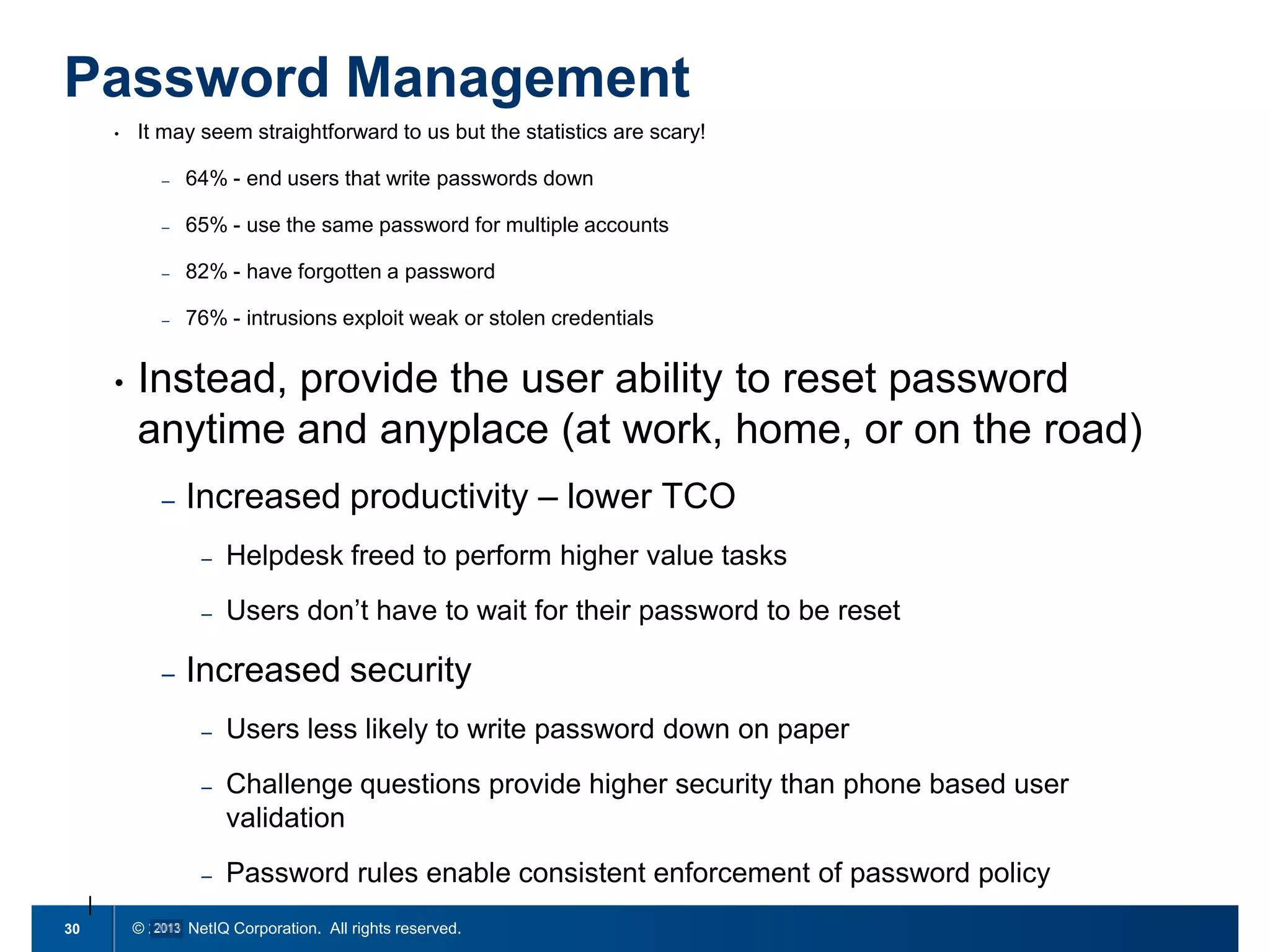
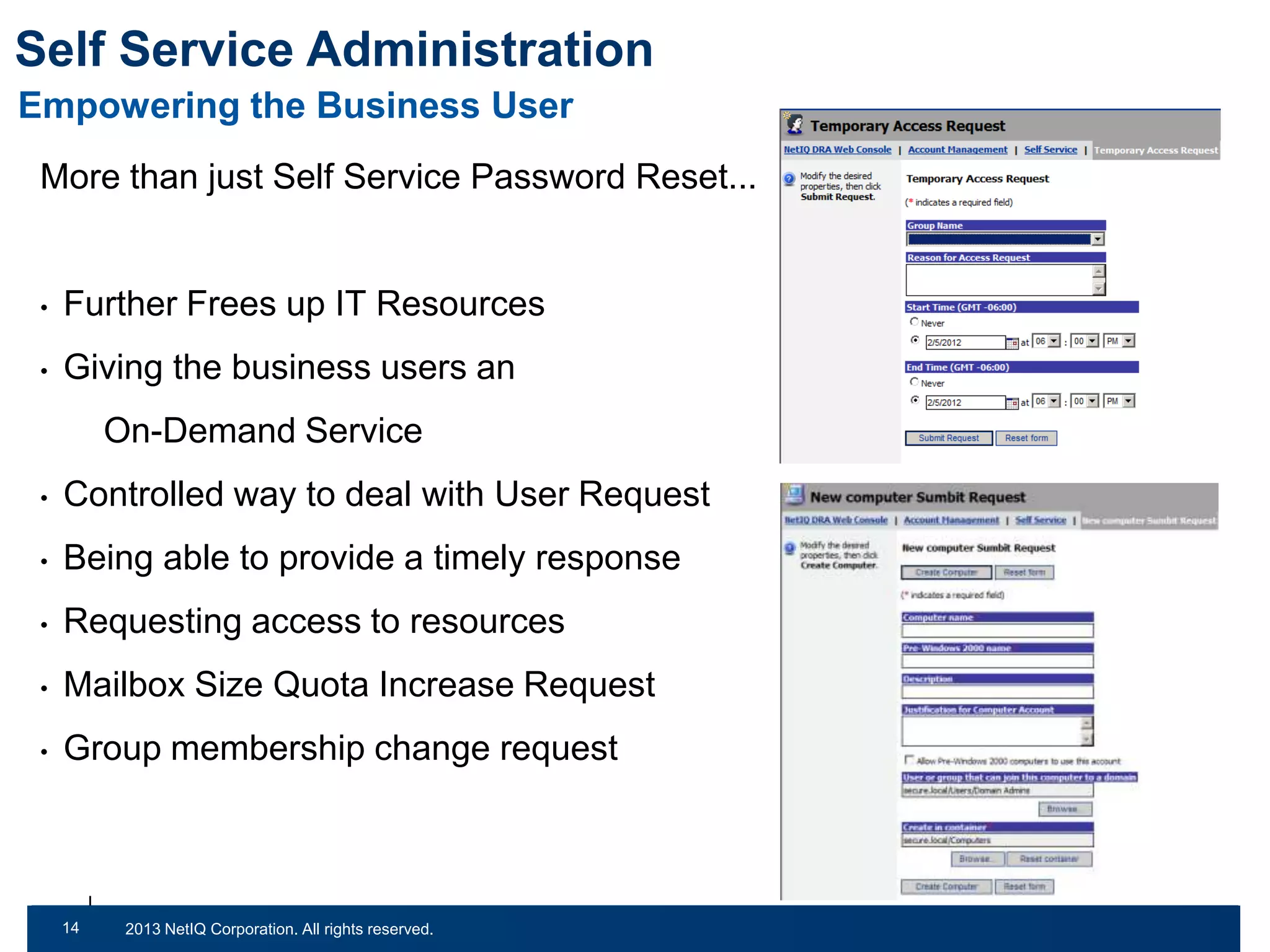
The document discusses the importance of cleaning up Active Directory environments to mitigate risks associated with inactive and unmanaged accounts, emphasizing the need for automated cleanup processes to enhance security and compliance. It highlights challenges faced by organizations in managing user accounts and the necessity of effective user lifecycle management as well as self-service options for users. Additionally, it notes the significance of adhering to regulatory standards and improving user empowerment through self-service password management.