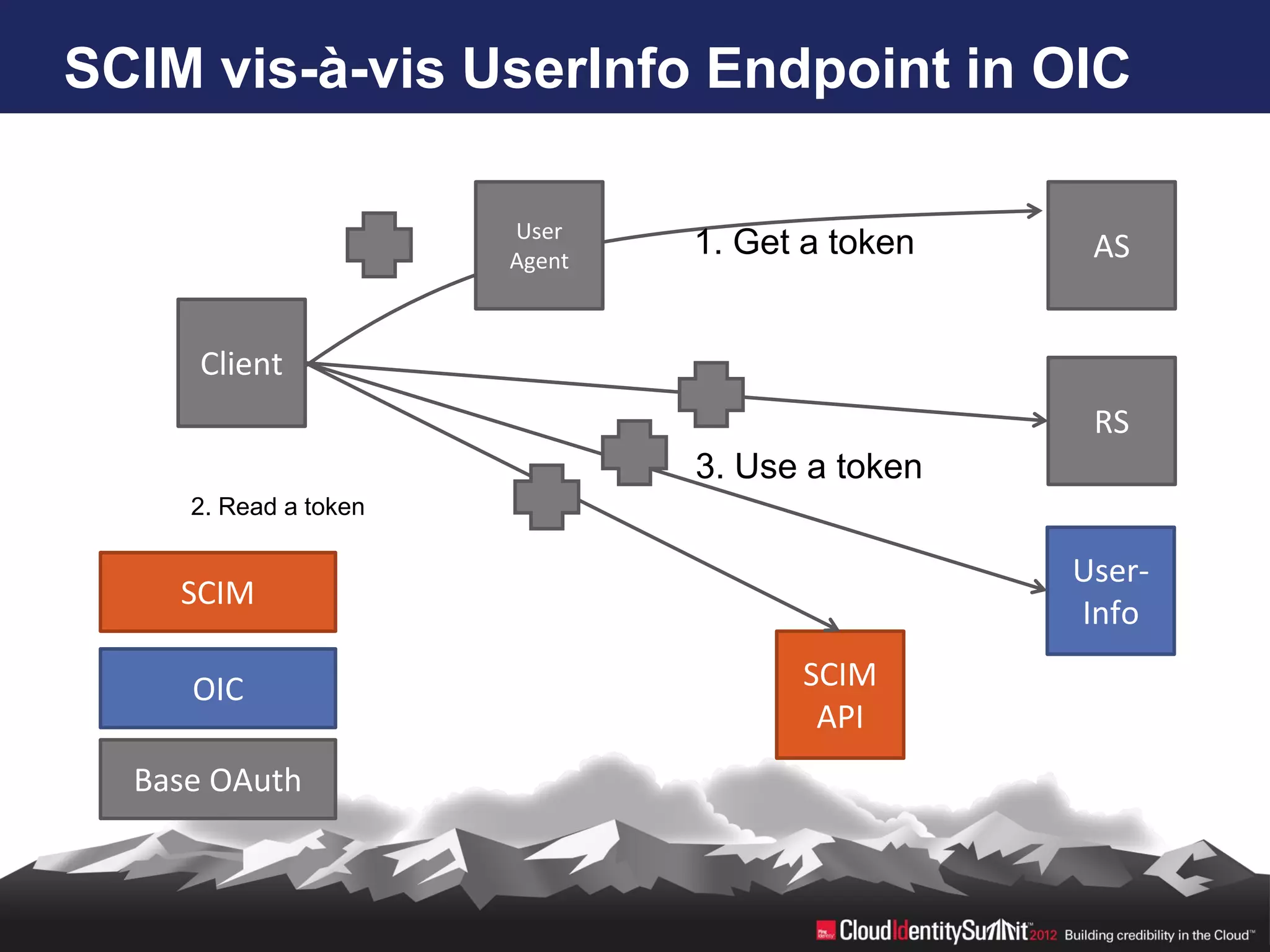
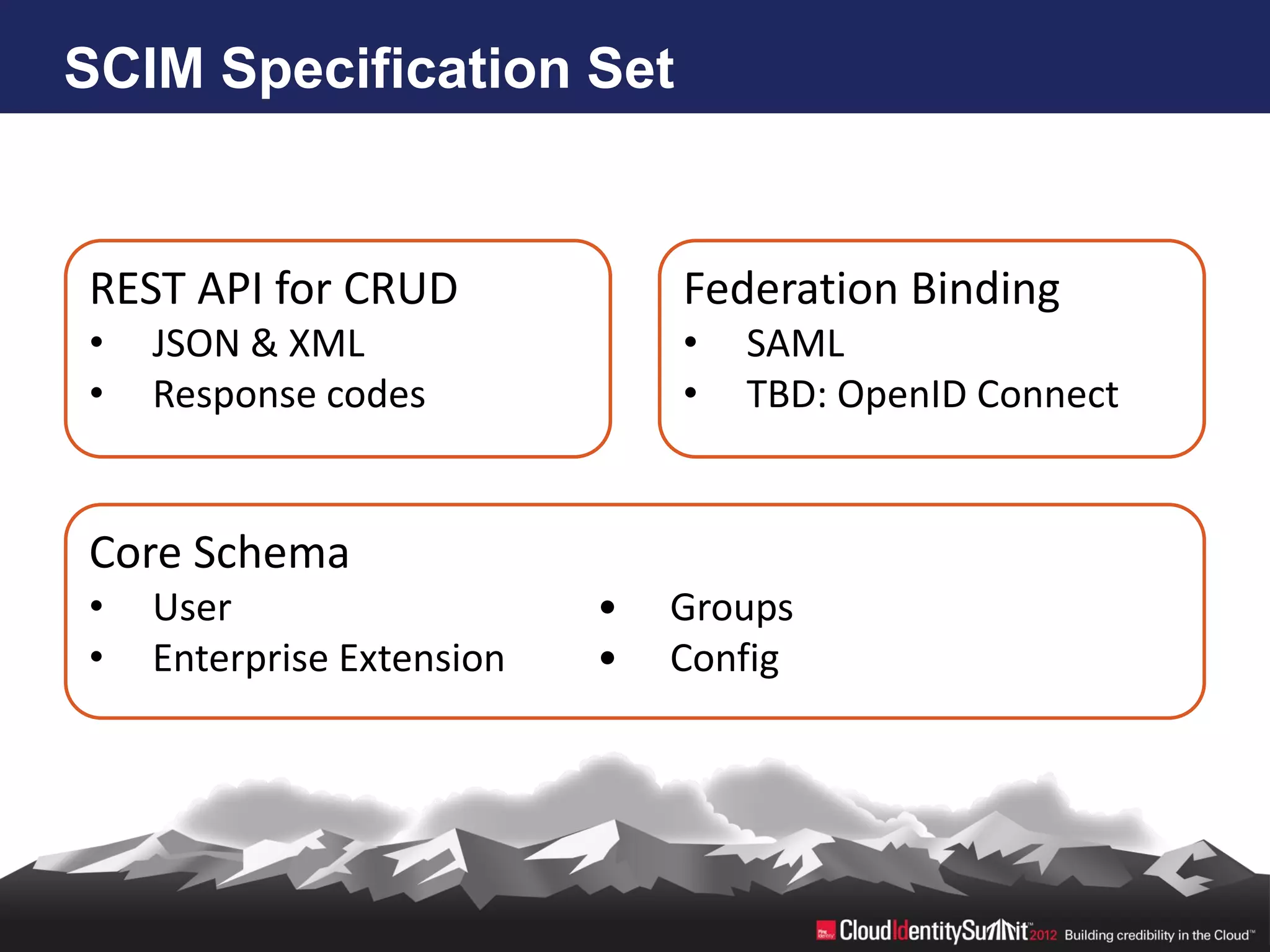
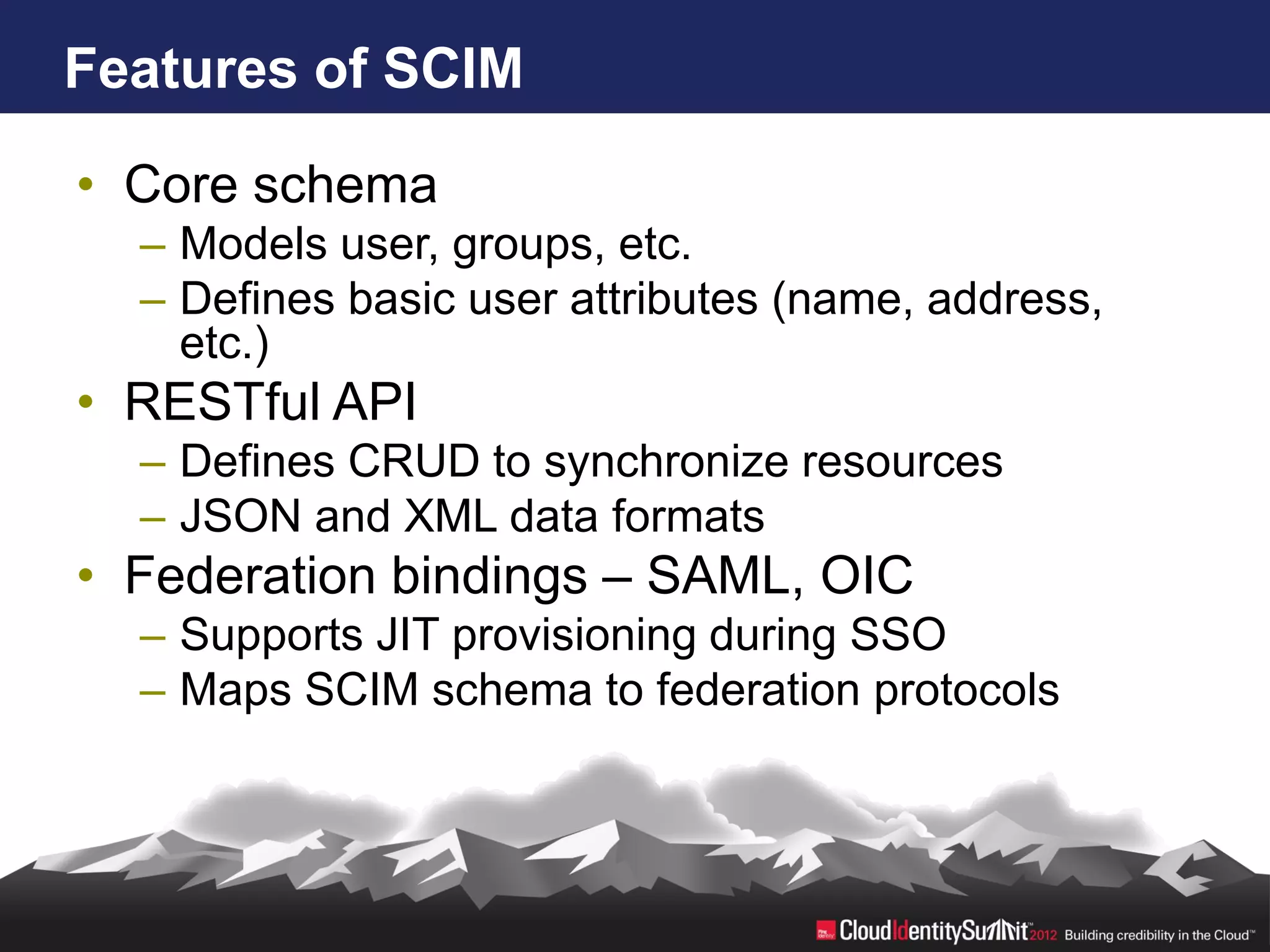
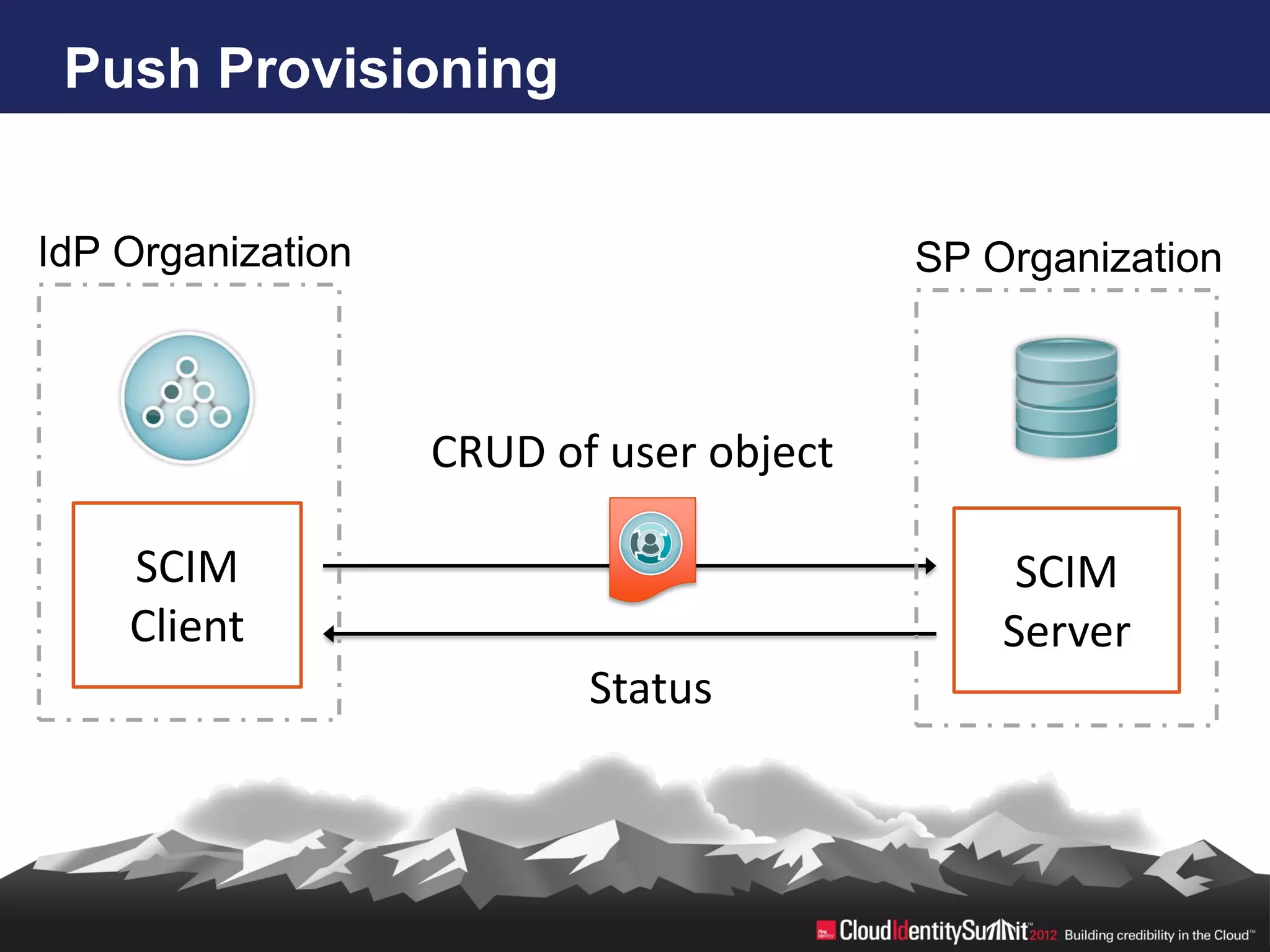
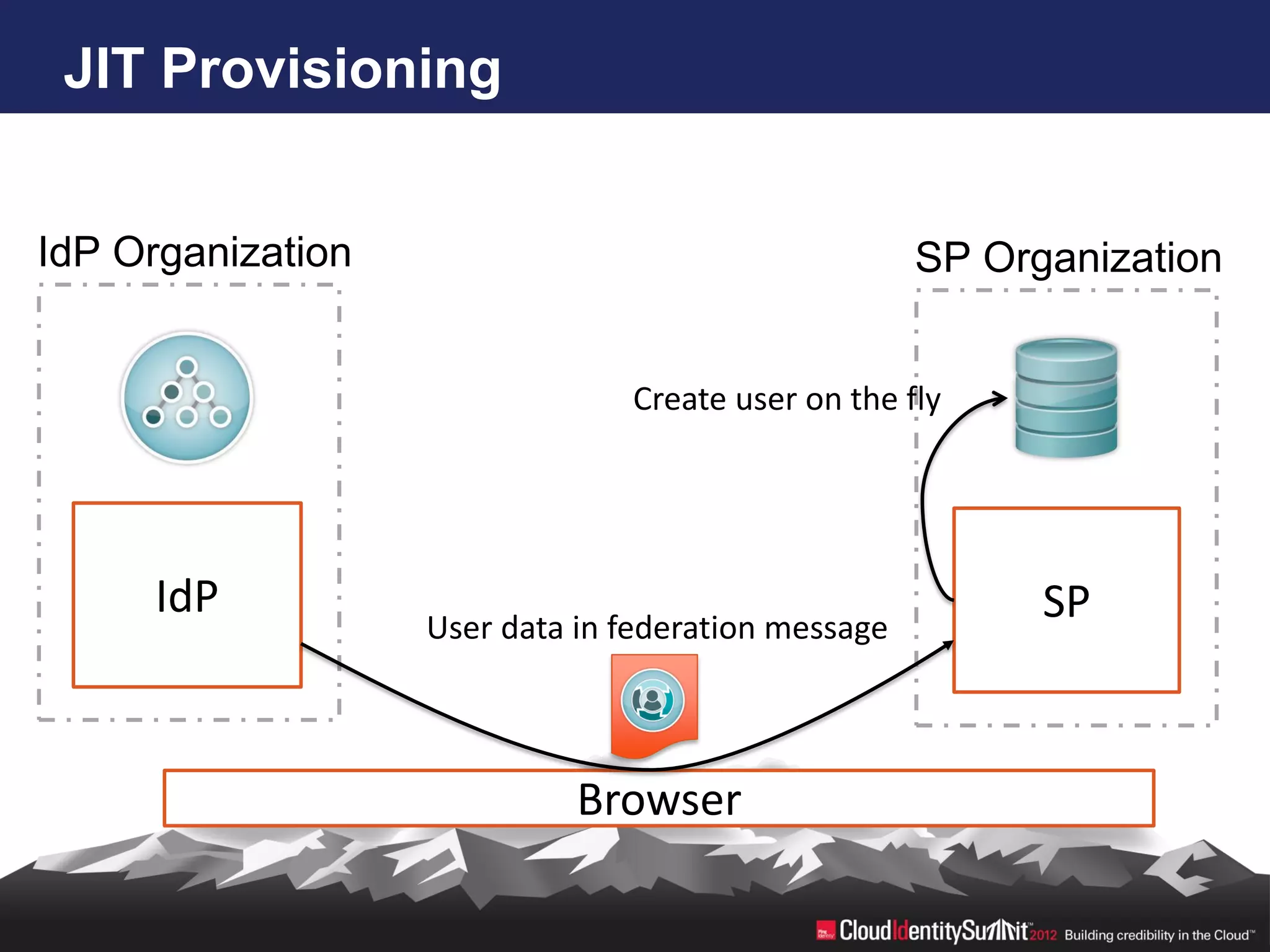
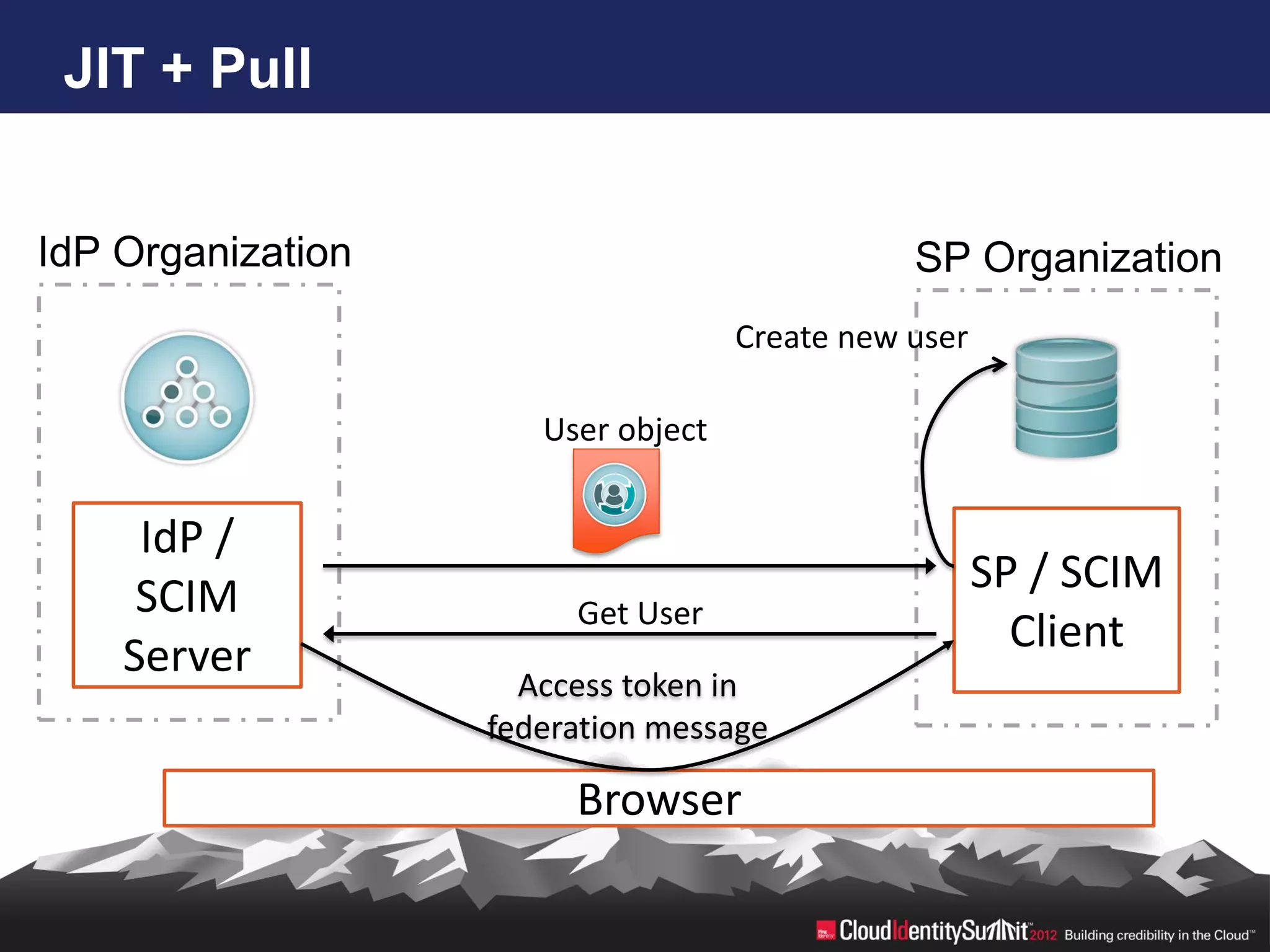
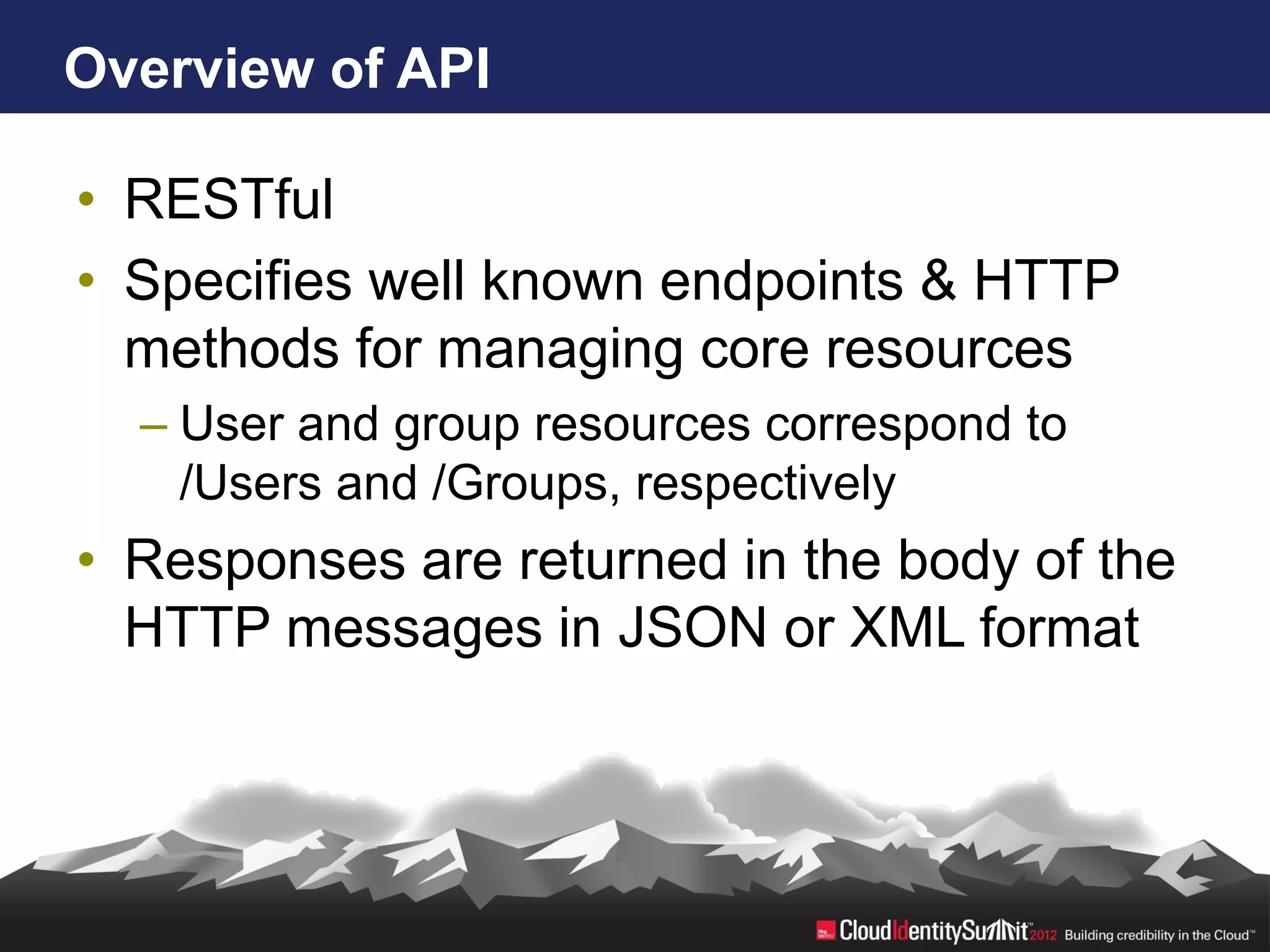
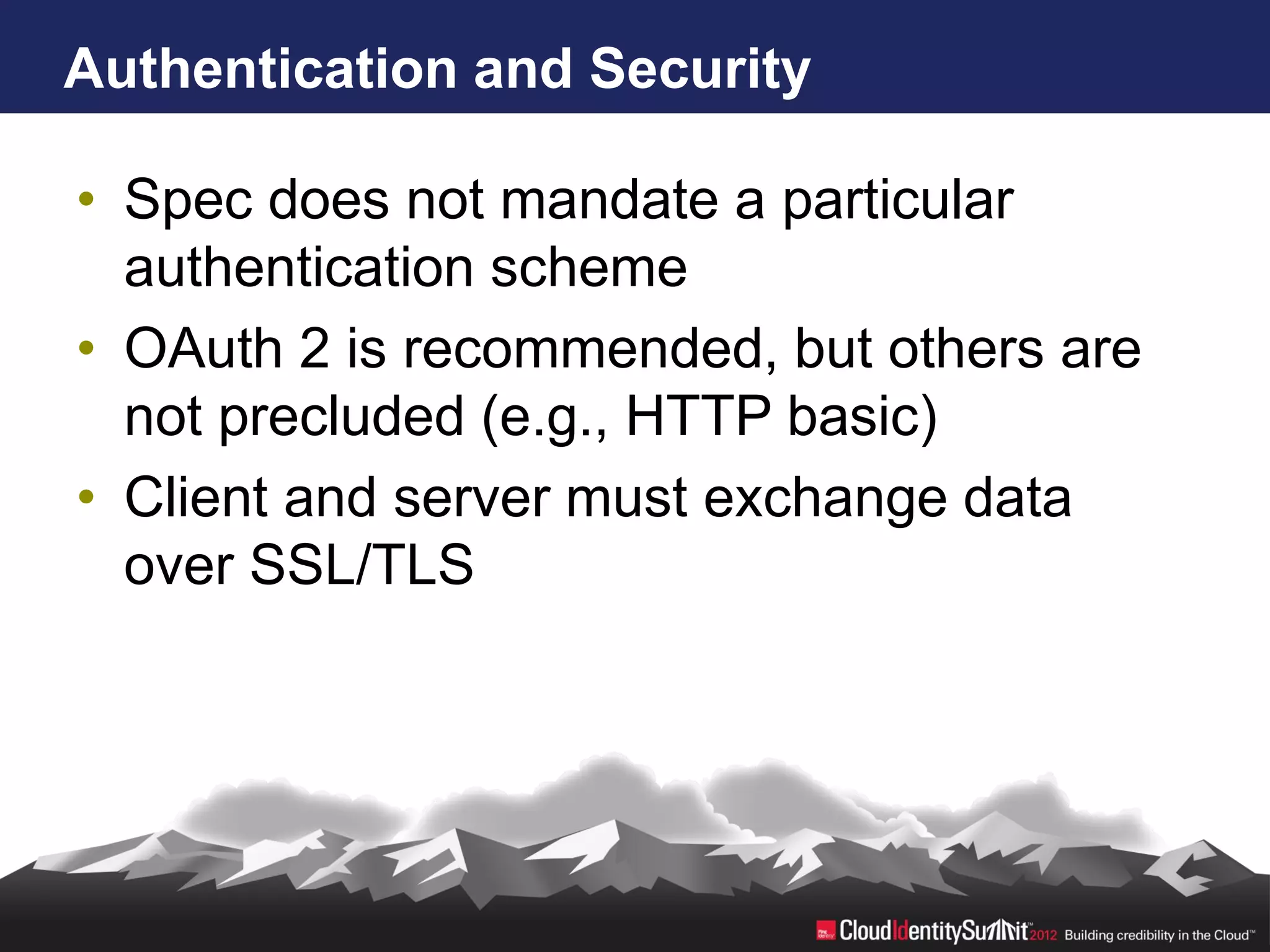
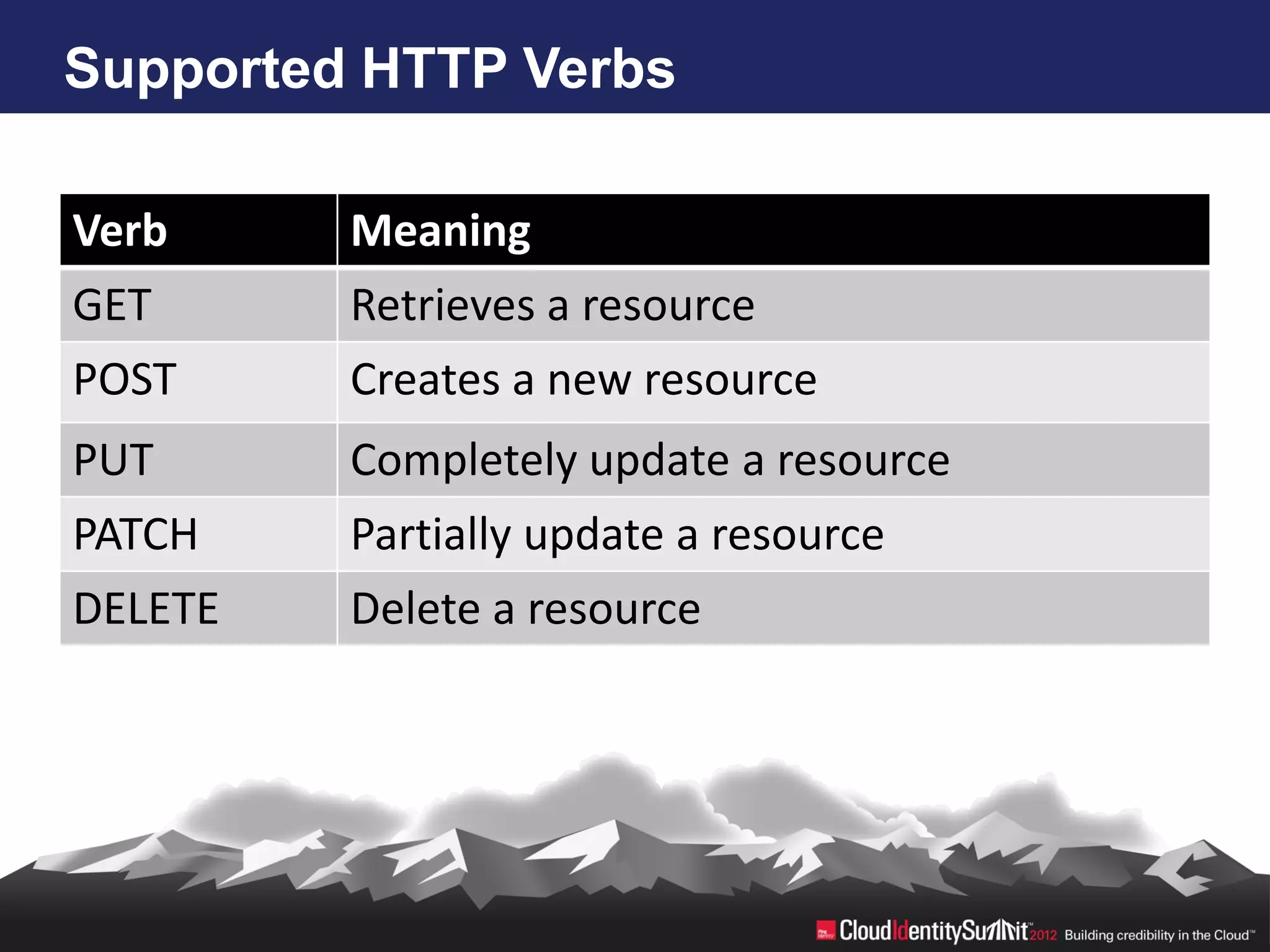
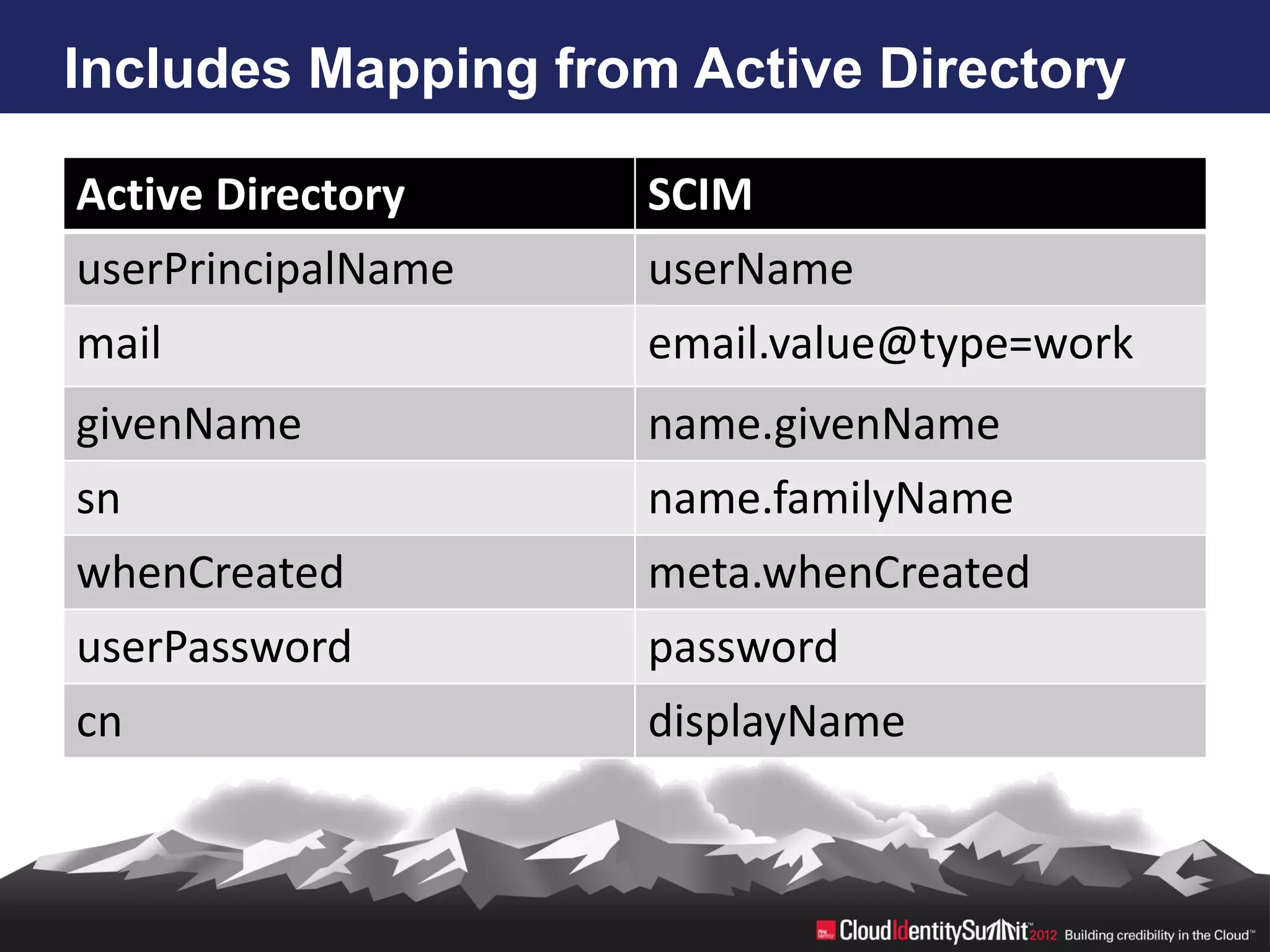
SCIM is an open standard aimed at automating user and group management across distributed systems, addressing challenges from diverse cloud providers and integration issues. The specification facilitates CRUD operations through RESTful APIs using JSON and XML, supports secure access via OAuth 2, and allows for extensibility with enterprise extensions. Industry implementations are growing, and the IETF working group aims to enhance SCIM's adoption and functionality by 2014.



![Updating a Group with a new Member
PATCH /Groups/acbf3ae7-8463-4692-b4fd-
PATCH = only 9b4da3f908ce
update what’s Host: example.com Secure access
changed Accept: application/json using OAuth 2
Authorization: Bearer h480djs93hd8
ETag: W/"a330bc54f0671c9"
{
"schemas": ["urn:scim:schemas:core:1.0"],
"members": [
{
"display": "Babs Jensen", New group
"value": "2819c223-7f76-453a…" member; others
}
are unchanged
]
}](https://image.slidesharecdn.com/cis-2012-120806075959-phpapp01/75/SCIM-presentation-from-CIS-2012-18-2048.jpg)