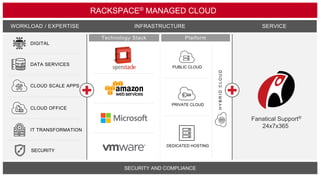
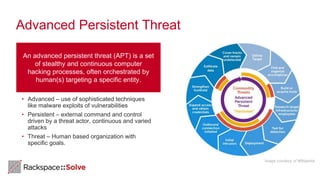
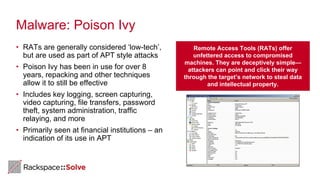
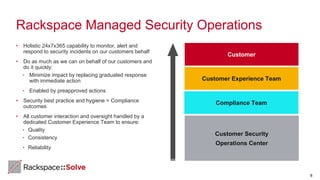
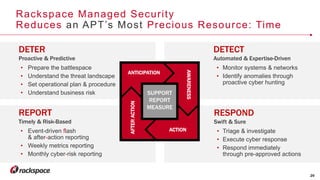
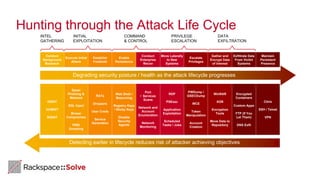
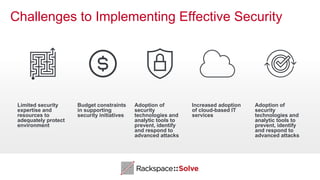
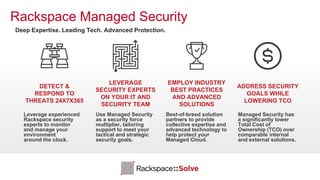
The document highlights the increasing security threats faced by Australian businesses, with the average cost of data breaches reaching $2.5 million and a reported increase in global security incidents. It outlines Rackspace's managed security offerings, emphasizing proactive detection, rapid response, and the need for experienced security analysts. Additionally, it discusses the tactics used by advanced persistent threats (APTs) and suggests a comprehensive approach to security that includes vulnerability management, compliance assistance, and advanced protection technologies.