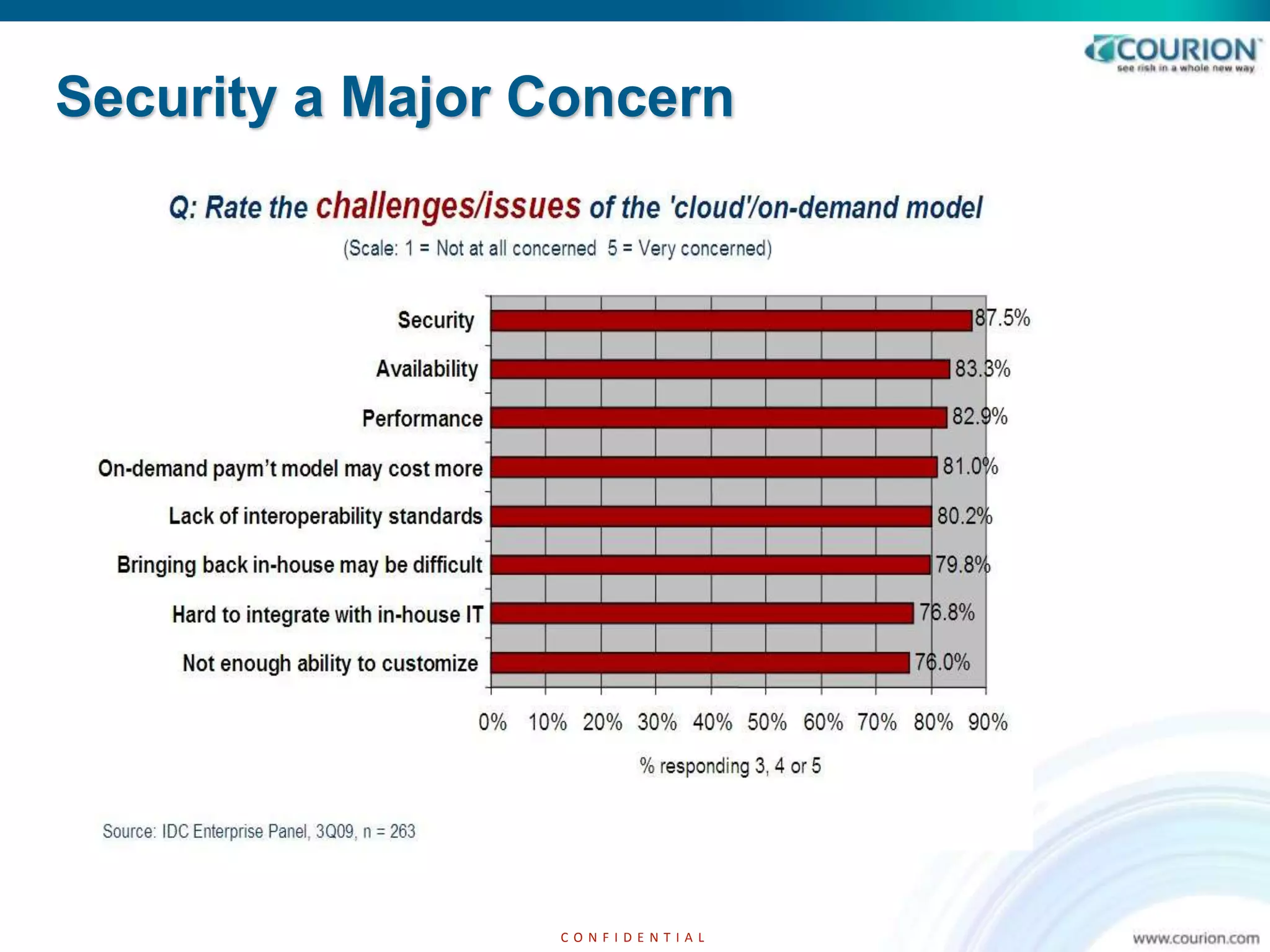
This document discusses managing access security risks in the cloud. It notes that security is a major concern for organizations moving to the cloud. The top internal and external audit findings relate to identity and access management. The document advocates adopting a risk-driven identity and access management model to ensure the right people have the right access to the right resources. It acknowledges that while security technologies are important, managing risk should be the focus. An architecture for access intelligence is proposed that uses analytics and monitoring to detect threats and risks in real-time and enable contextual remediation.