The document details the deployment of Puppet at OnApp, describing their infrastructure, which includes around 20 physical servers and 200 VMs in a homogeneous 64-bit Debian environment. It outlines the integration of Puppet for configuration management, emphasizing its reliability and self-documenting properties, as well as its role in maintaining package updates and service management. The setup uses a Git version control system for manifest organization, facilitating efficient deployment and management of cloud edge servers on the OnApp platform.




![Core Infra Manifest Excerpt
$portal_domain = "portal.alpha.onappcdn.com" node
"monitoring.alpha.onappcdn.com" {
$portal_db_host = "portal.alpha.onappcdn.com"
include base
$portal_db_user = "aflexi_webportal"
include s_db_monitoring
include s_monitoring_server
$auth_nameservers = { "ns1" => "175.143.72.214",
include collectd::rrdcached
"ns2" => "175.143.72.214",
include s_munin
"ns3" => "175.143.72.214",
include s_monitoring_alerts
"ns4" => "175.143.72.214",
include s_monitoring_graph
}
}
$monitoring_host_server = class collectd::rrdcached {
package { "rrdcached":
[ "monitoring.alpha.onappcdn.com",
"dns.alpha.onappcdn.com" ] ensure => latest,
}
service { "rrdcached":
BLUE – env config definitions ensure => running,
RED – node definitions }
GREEN – class definitions }](https://image.slidesharecdn.com/03waikeenwoonpuppetcampsea2012-130403231549-phpapp02/75/PuppetCamp-SEA-1-Puppet-Deployment-at-OnApp-12-2048.jpg)
![Package Repo Integration
l Jenkins builds debs of our code and stores it into an apt
repository for the environment it is built for.
l Puppet keeps packages up-to-date (ensure => latest)
and restarts services on package upgrades.
Puppet-agent[25431]:
(/Stage[main]/Debian/Exec[apt-get-update]/returns) executed
successfully
puppet-agent[25431]:
(/Stage[main]/Python::Aflexi::Mq/Package[python-aflexi-mqcore]/
ensure)
ensure changed '7065.20120530.113915-1' to '7066.20120604.090916-1'
puppet-agent[25431]:
(/Stage[main]/S_mq/Service[worker-rabbitmq])
Triggered 'refresh' from 1 events
puppet-agent[25431]: Finished catalog run in 16.08 seconds](https://image.slidesharecdn.com/03waikeenwoonpuppetcampsea2012-130403231549-phpapp02/75/PuppetCamp-SEA-1-Puppet-Deployment-at-OnApp-13-2048.jpg)
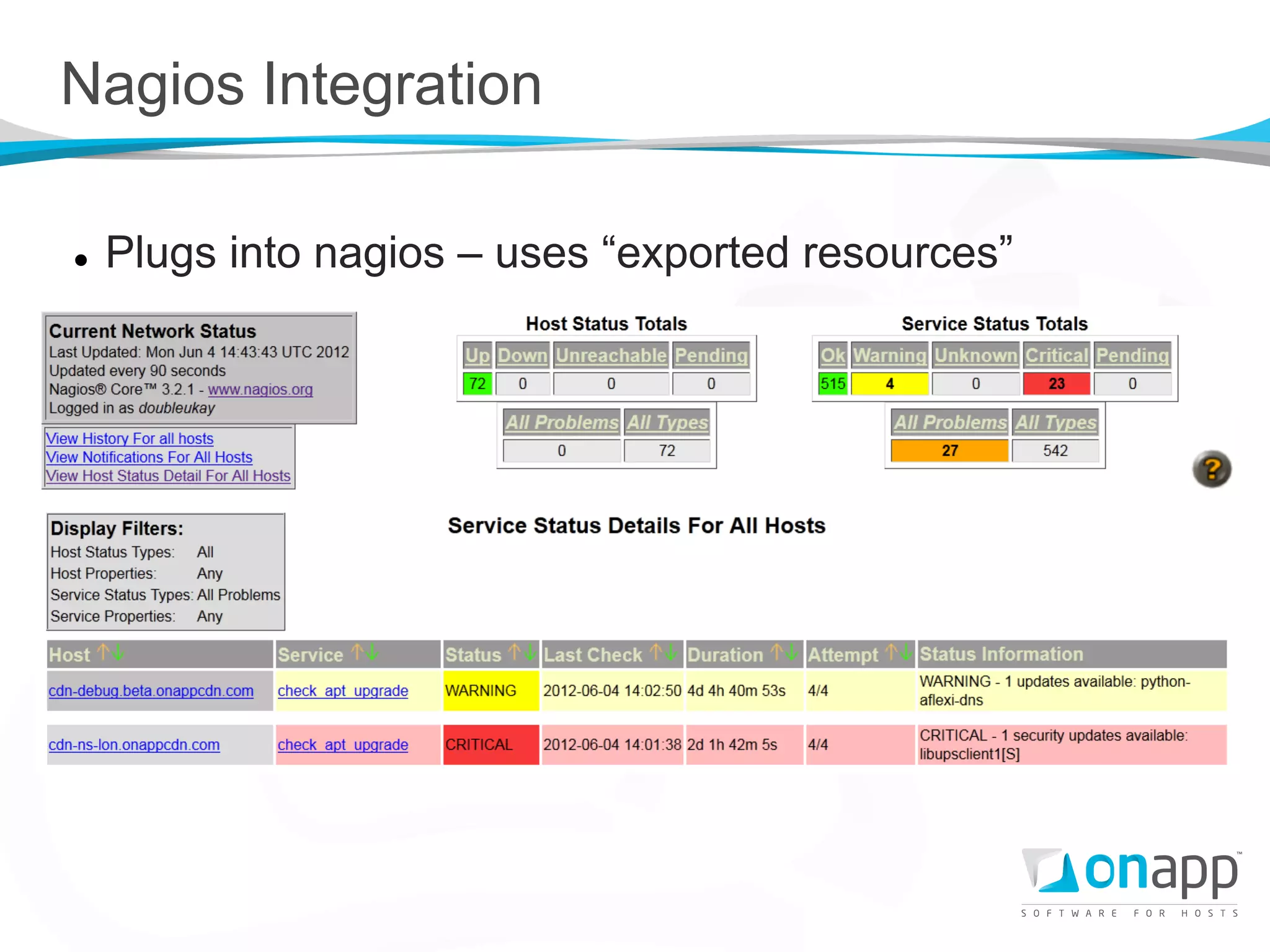
![Nagios Integration
Server manifest Nagios service manifest
*collects the resources to check
*exports the service that is checked
@@nagios_service { "check_load_$fqdn": Nagios_service <<| tag == "onappcdn.cm" |>>
{
check_command => target => "/etc/n3/conf.d/services.cfg",
"check_nrpe_1arg!check_load", require => Package["nagios3"],
use => "generic-service", notify => Exec["reload-nagios"],
host_name => $fqdn, }
service_description => "check_load",
tag => $domain,
}](https://image.slidesharecdn.com/03waikeenwoonpuppetcampsea2012-130403231549-phpapp02/75/PuppetCamp-SEA-1-Puppet-Deployment-at-OnApp-15-2048.jpg)
![Nagios Integration
l What's logged on the nagios server when puppet runs?
puppet-agent[15293]: (/Stage[main]/Nagios::Monitor_private/
Nagios_host[hrm.onappcdn.com]/ensure) created
puppet-agent[15293]: (/Stage[main]/Nagios::Monitor_private/
Nagios_service[check_load_hrm.onappcdn.com]/ensure) created
nagios3: Nagios 3.2.1 starting... (PID=5601)
puppet-agent[15293]: (/Stage[main]/Nagios::Base/Exec[reload-
nagios]) Triggered 'refresh' from 8 events](https://image.slidesharecdn.com/03waikeenwoonpuppetcampsea2012-130403231549-phpapp02/75/PuppetCamp-SEA-1-Puppet-Deployment-at-OnApp-16-2048.jpg)


![Edge Servers – External Node Classifier
l No text manifest – all code, using “external node
classifier”.
l Assign variables and classes specific to the edge
server through node classifier. E.g. its password, the
services it runs.
l In python,
output = {}
output[“classes”] = [ “class1”, “class2” ]
output[“parameters”] = { “param1”: “value1” }
print yaml.dump(output)](https://image.slidesharecdn.com/03waikeenwoonpuppetcampsea2012-130403231549-phpapp02/75/PuppetCamp-SEA-1-Puppet-Deployment-at-OnApp-23-2048.jpg)
![Edge Servers – External Node Classifier
l This YAML-encoded structure...
$ puppet-nodeclassifier 85206671.onappcdn.com
classes: [base, nginx ]
parameters: { edge_secret_key: 86zFsrM7Ma, monitoring_domain:
monitoring.alpha.onappcdn.com }
l … is equivalent to this textual manifest:
node 85206671.onappcdn.com {
$edge_secret_key = “86zFsrM7Ma”
$monitoring_domain = “monitoring.alpha.onappcdn.com”
include base
include nginx
}](https://image.slidesharecdn.com/03waikeenwoonpuppetcampsea2012-130403231549-phpapp02/75/PuppetCamp-SEA-1-Puppet-Deployment-at-OnApp-24-2048.jpg)