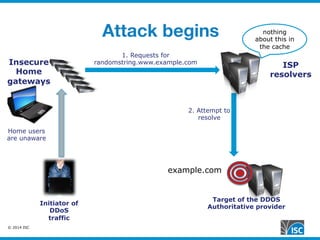
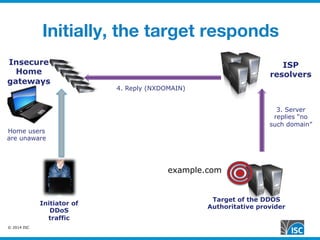
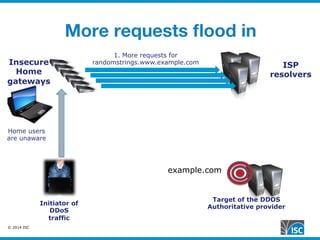
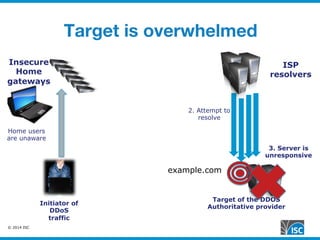
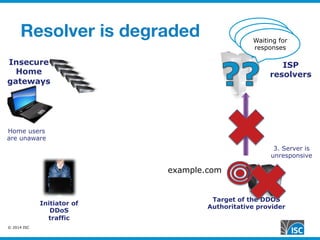
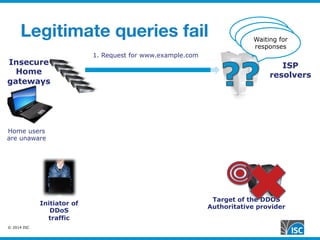
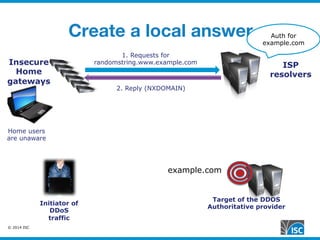
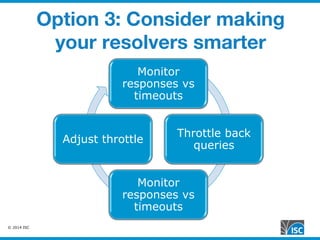
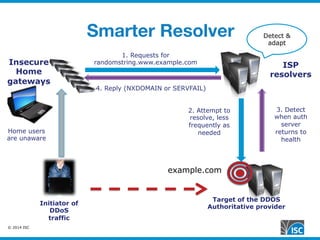
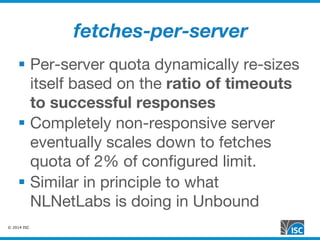
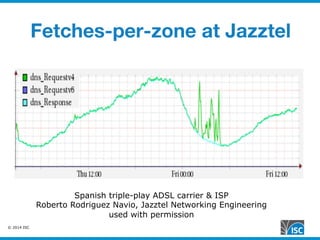
The document discusses DNS query attacks that aim to degrade DNS resolvers by flooding them with requests for nonexistent subdomains. It describes the attacks, identifying features like high volumes of random subdomain queries. It then outlines several mitigation techniques resolvers have used, including temporarily authorizing themselves to answer authoritatively, filtering requests using real-time blocklists, and making resolvers smarter by monitoring responses and throttling queries adaptively on a per-server or per-zone basis. The best long-term solution mentioned is closing insecure home gateways that are often hijacked to initiate such attacks.