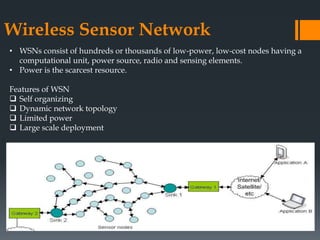
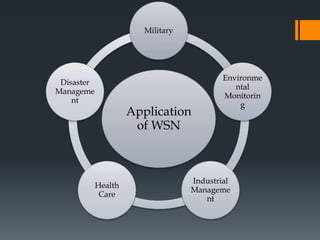
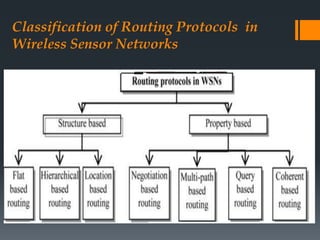
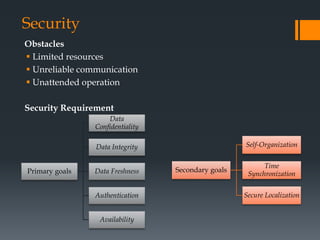
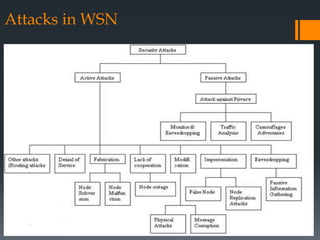
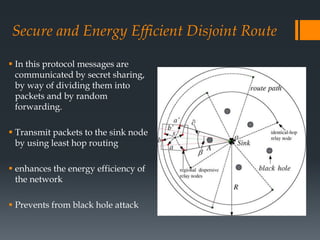
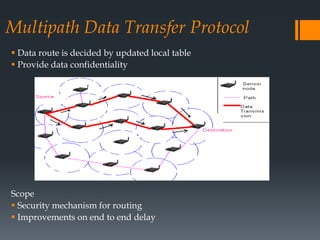
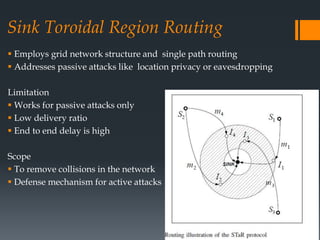
The document discusses secure routing protocols for wireless sensor networks. It begins by describing the components and design challenges of wireless sensor networks, including limited resources and security issues. It then discusses various attacks on wireless sensor networks like spoofing, selective forwarding, and sinkhole attacks. The document analyzes several secure routing protocols that aim to prevent such attacks, including Distributed Security Framework, Multipath Data Transfer Protocol, Secure and Energy Efficient Disjoint Route, and Bio-inspired Self-Organized Secure Autonomous Routing Protocol. It concludes by discussing future work to develop a new routing approach with low energy consumption, high delivery ratio, and strong security against possible threats.