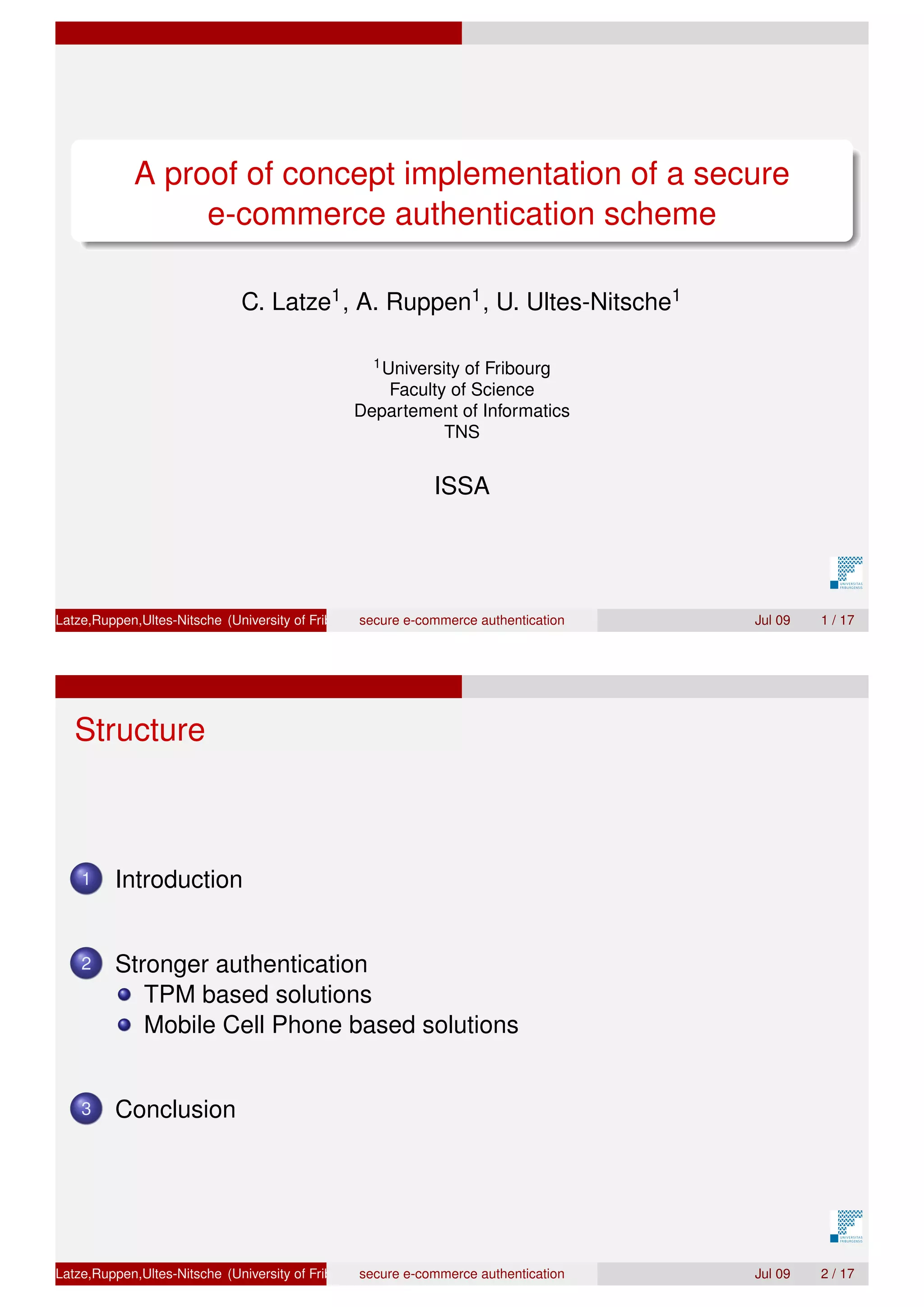
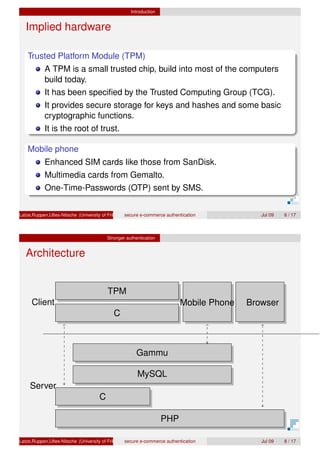
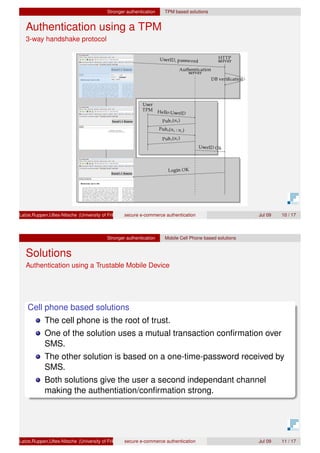
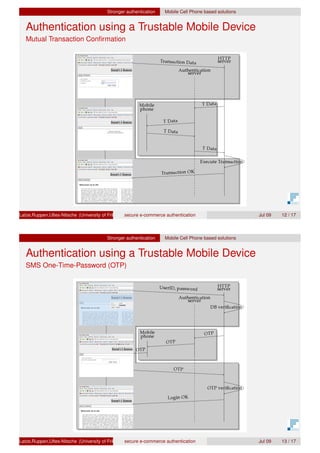
The document presents a proof of concept for a secure e-commerce authentication scheme, focusing on user protection against attacks like phishing and pharming. It discusses the use of hardware-based solutions, particularly Trusted Platform Module (TPM) and mobile devices, to ensure a higher level of security through methods like three-way handshake protocols and one-time passwords. The evaluation indicates that all proposed protocols exhibit good security and usability, with varying authentication times.