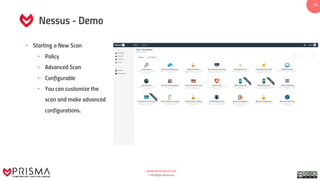
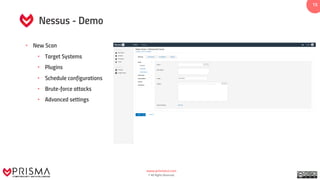
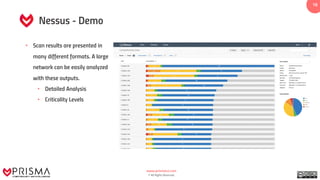
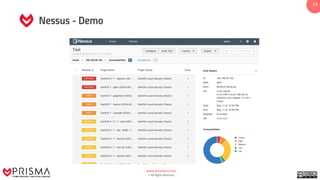
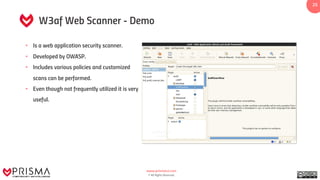
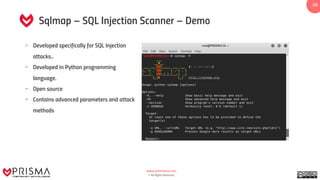
This document presents a training guide on vulnerability detection, covering definitions, sources, the vulnerability management cycle, and automated scanning tools. It reviews various scanners such as Nessus, OpenVAS, and Burp Suite, alongside their capabilities and applications in identifying risks and managing vulnerabilities. The document emphasizes the importance of using intelligence data collected from systems to understand and utilize discovered vulnerabilities effectively.


![www.prismacsi.com
© All Rights Reserved.
3
What is a Vulnerability?
• Vulnerabilites are defined as conditions in an application, service or protocol, previously or
recently discovered in research work, that give a cyber attacker the opportunity to execute any
type of attack which may affect the normal operation of a system.
• [Senaryo]](https://image.slidesharecdn.com/vulnerabilitydetection-181024193123/85/Practical-White-Hat-Hacker-Training-Vulnerability-Detection-3-320.jpg)