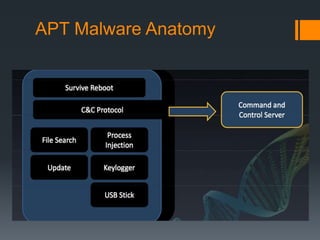
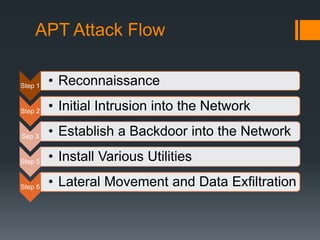
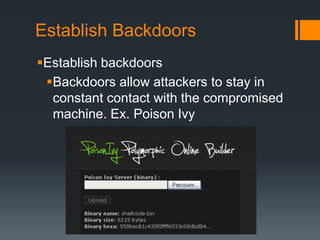
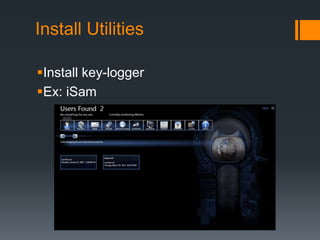
This document discusses advanced persistent threats (APTs). APTs are sophisticated cyber attacks that are carried out over an extended period to steal information. They use various techniques to evade detection, like polymorphic shellcode and packet splitting. APTs typically start with reconnaissance, then spear phishing to gain initial access. Attackers establish backdoors, install utilities like keyloggers, and move laterally within the network to exfiltrate data. Nation-states are often behind APTs to gain intelligence or competitive advantages. Organizations should monitor for unusual logins or anomalies to detect signs of an APT attack.