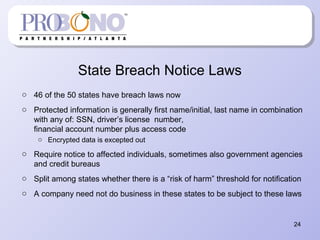
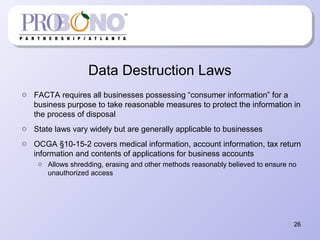
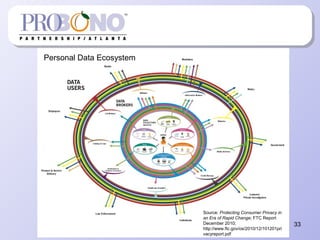
The document provides information about protecting private information for non-profits. It begins with describing recent large data breaches at Sony and other companies to illustrate the risks to organizations. It then discusses the current state of privacy laws, including key acts like COPPA, CAN-SPAM, and state data breach laws. The document outlines best practices for non-profits to implement privacy programs, including developing privacy policies, records management procedures, and staff training. It provides details on the components of an effective privacy policy and records management system to help non-profits comply with relevant laws and protect the information of clients, donors, and employees.