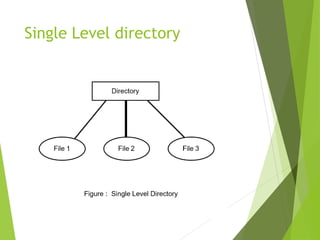
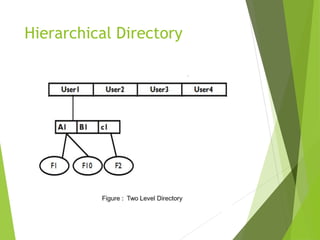
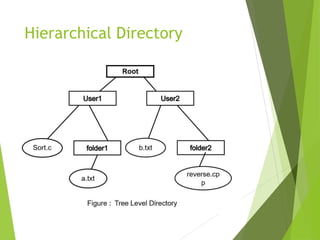
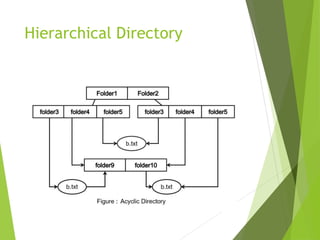
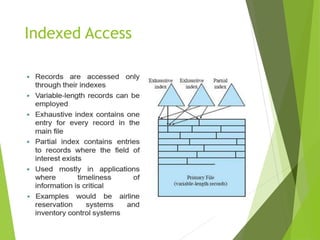
This document provides information about the Operating System & Linux Programming course BCA 301. It covers topics like file concepts, types, operations, directory structure, file security permissions in Linux. File concepts are explained - files store data and act as input/output medium. Types of files are ordinary, directory, device, FIFO. File operations include create, delete, open, close, read, write etc. Directory structure can be single level, hierarchical with examples. File system structure and access methods like sequential, indexed, direct are defined. Linux file security model and permissions for owner, group, other users are described. Methods to view, modify permissions using symbolic and numeric modes with chmod command are explained.
Human: Thank