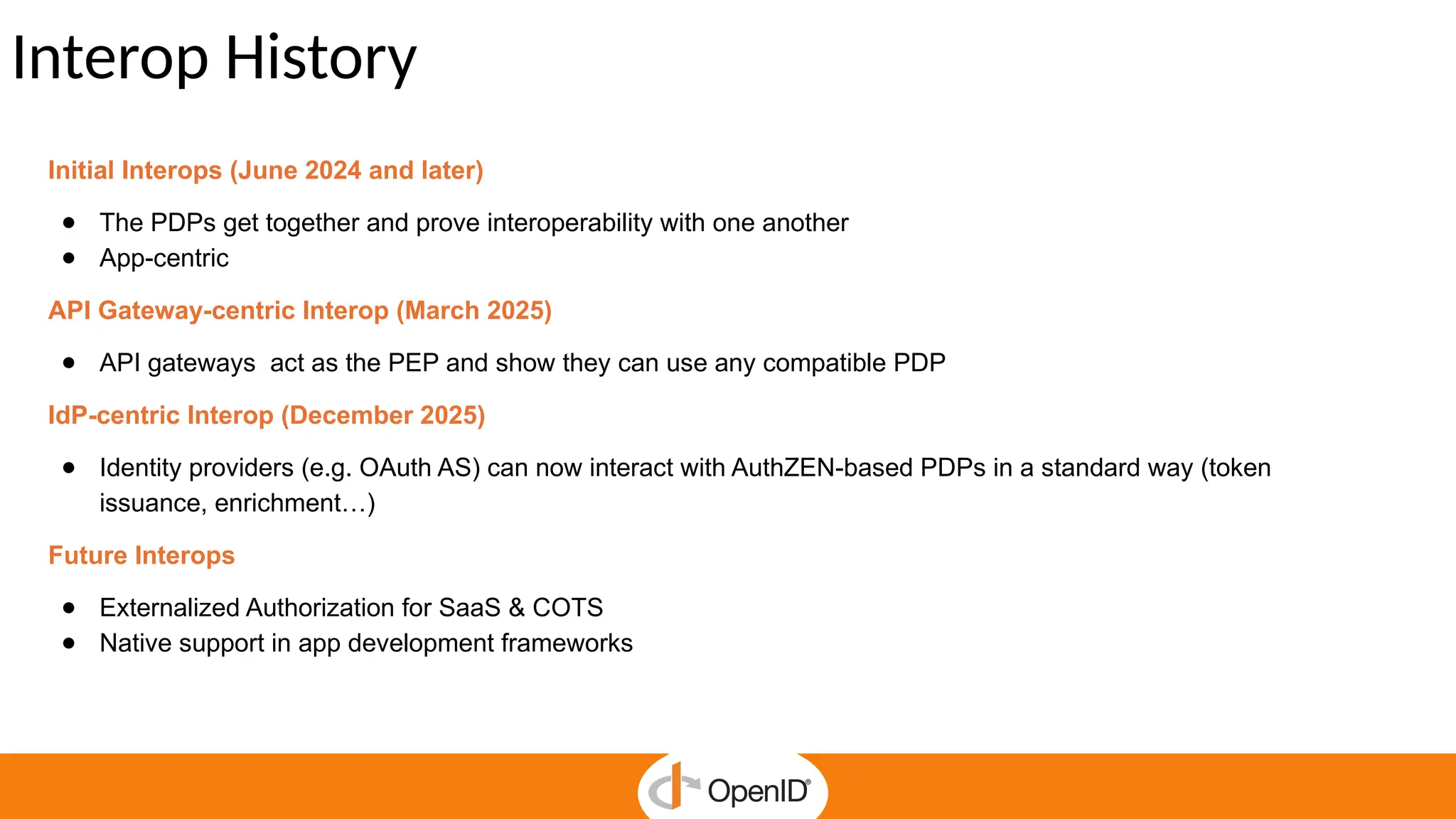
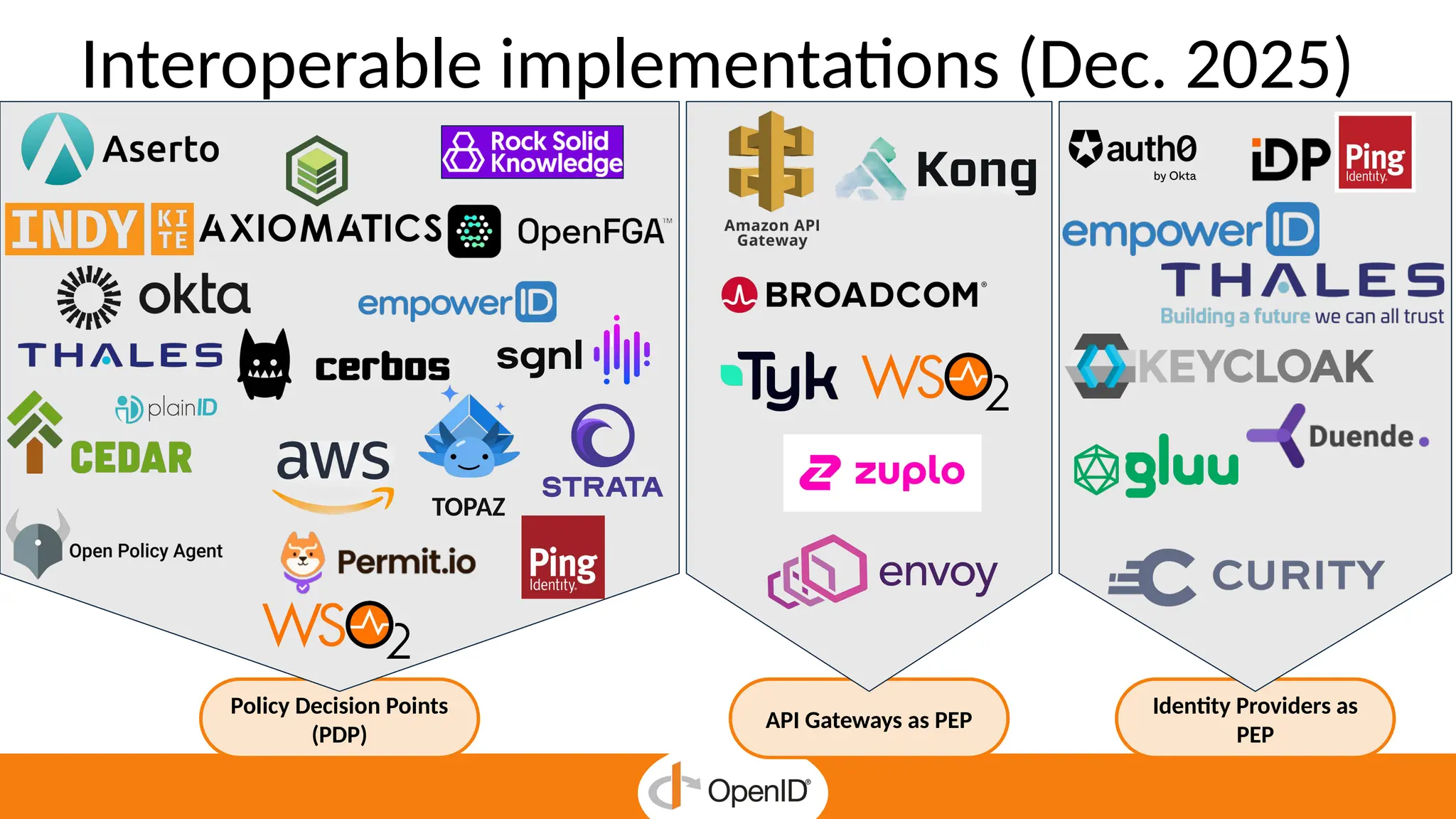
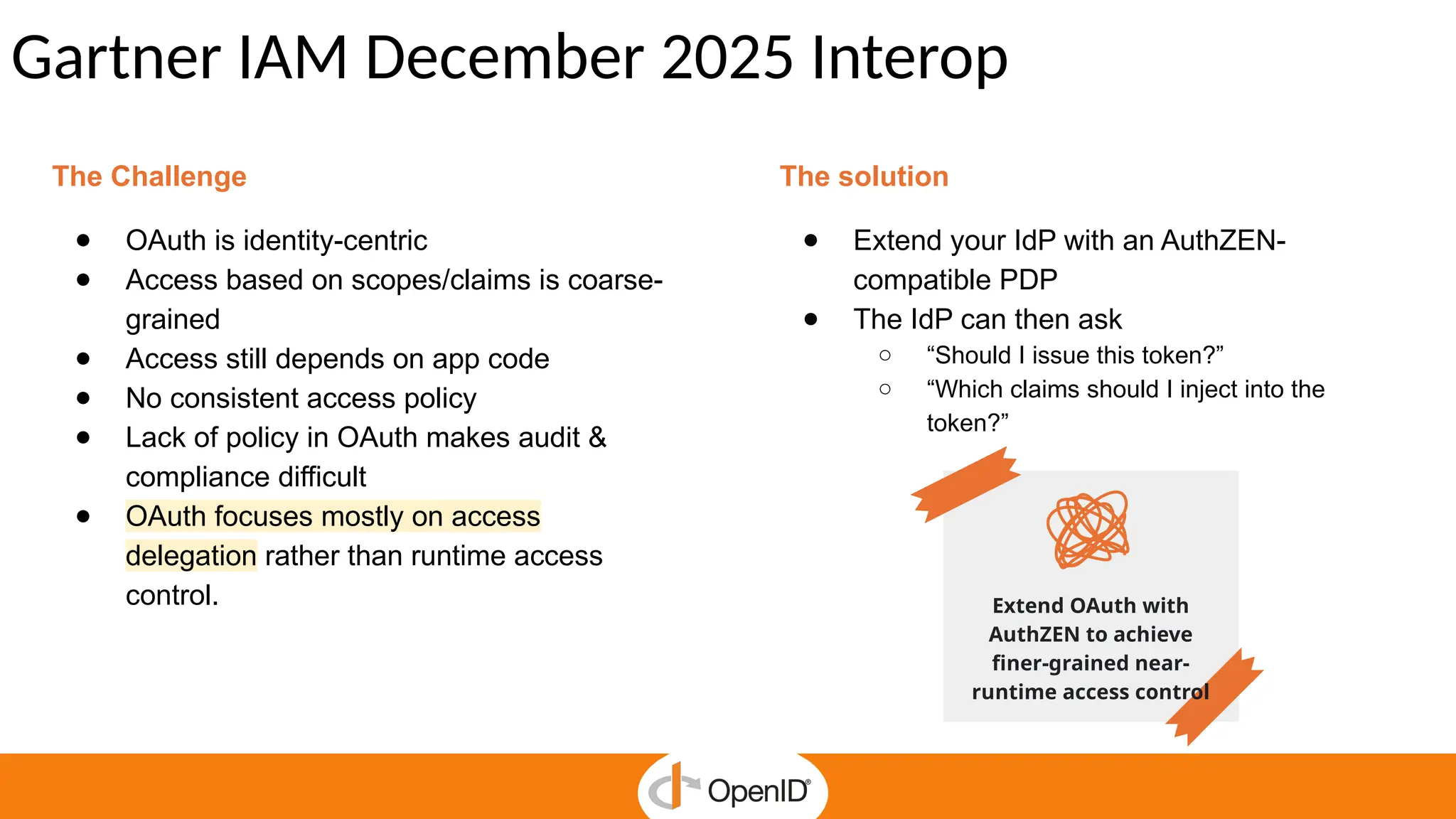
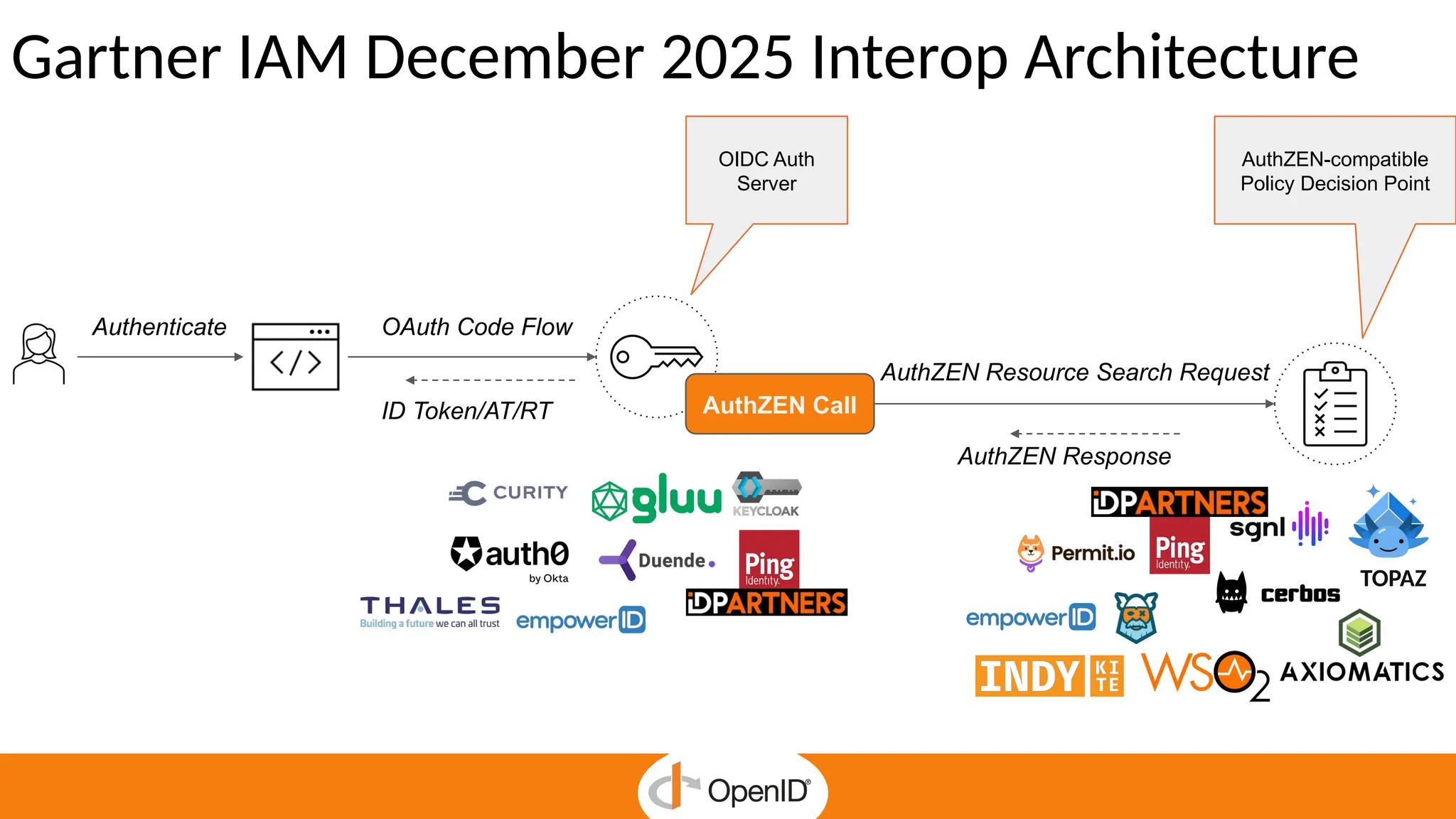
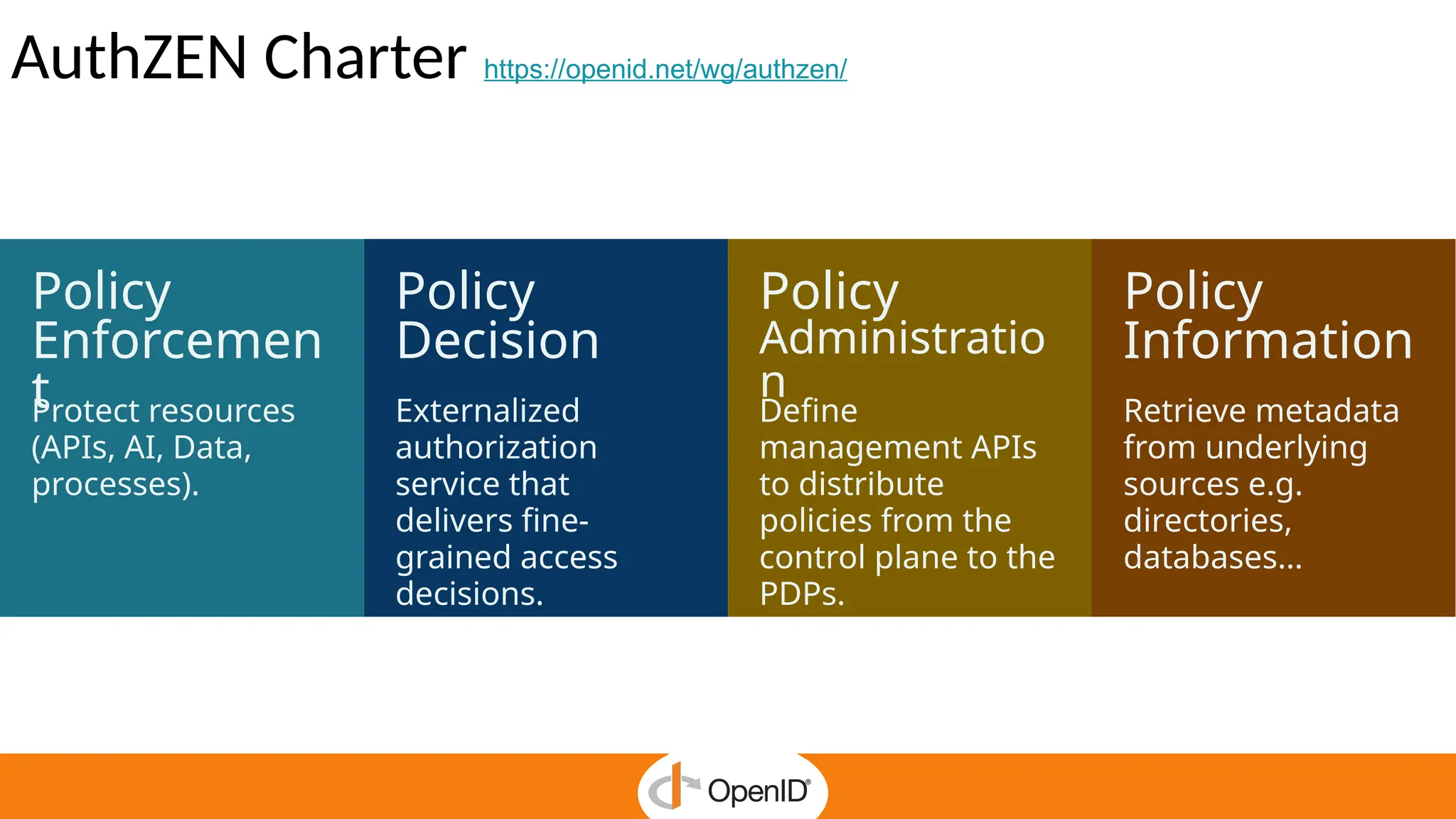
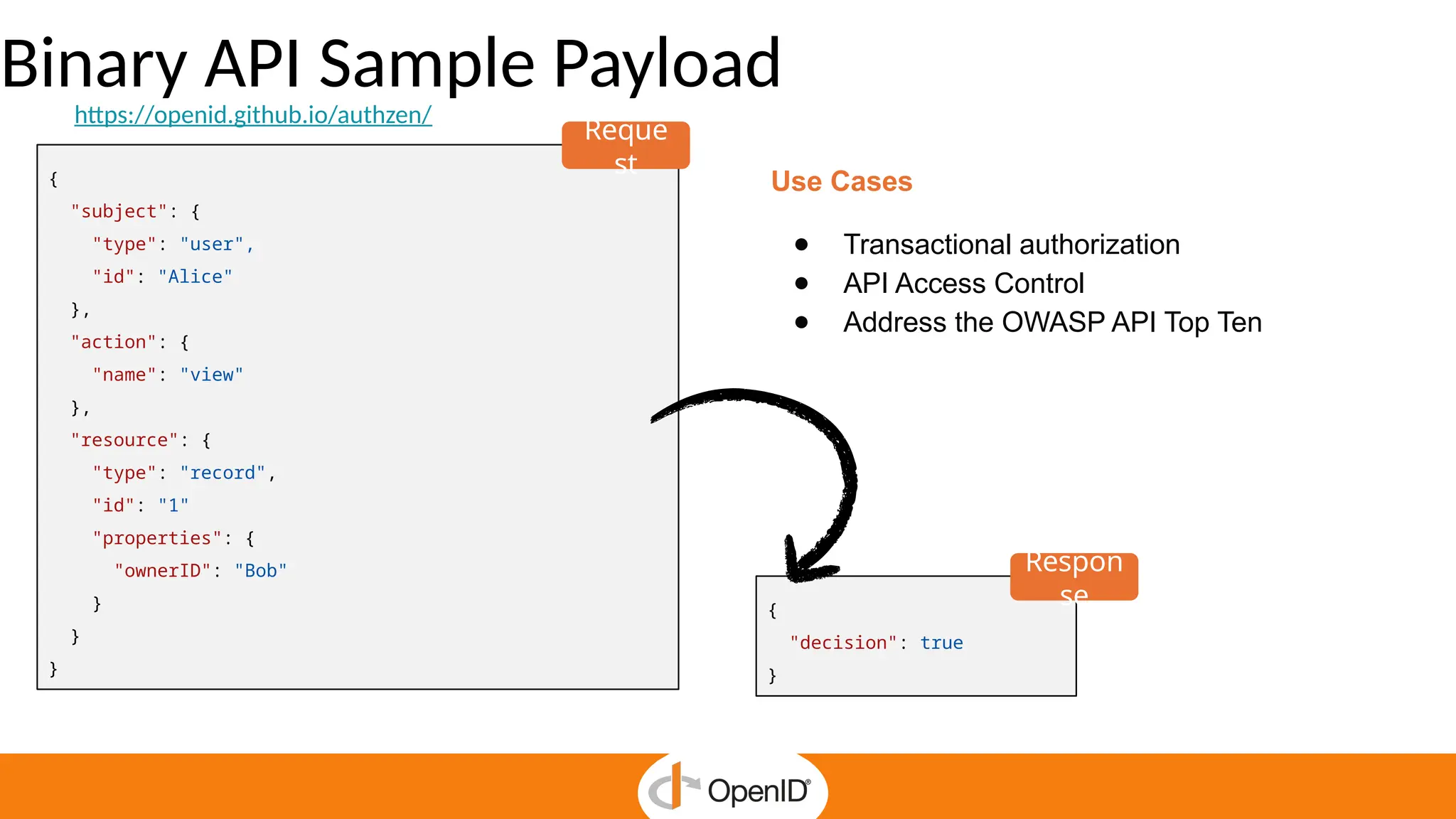
* AuthZEN frees developers to focus on business features by delegating authorization to a service.
* Centralized policy management streamlines access reviews and improves auditability and compliance.
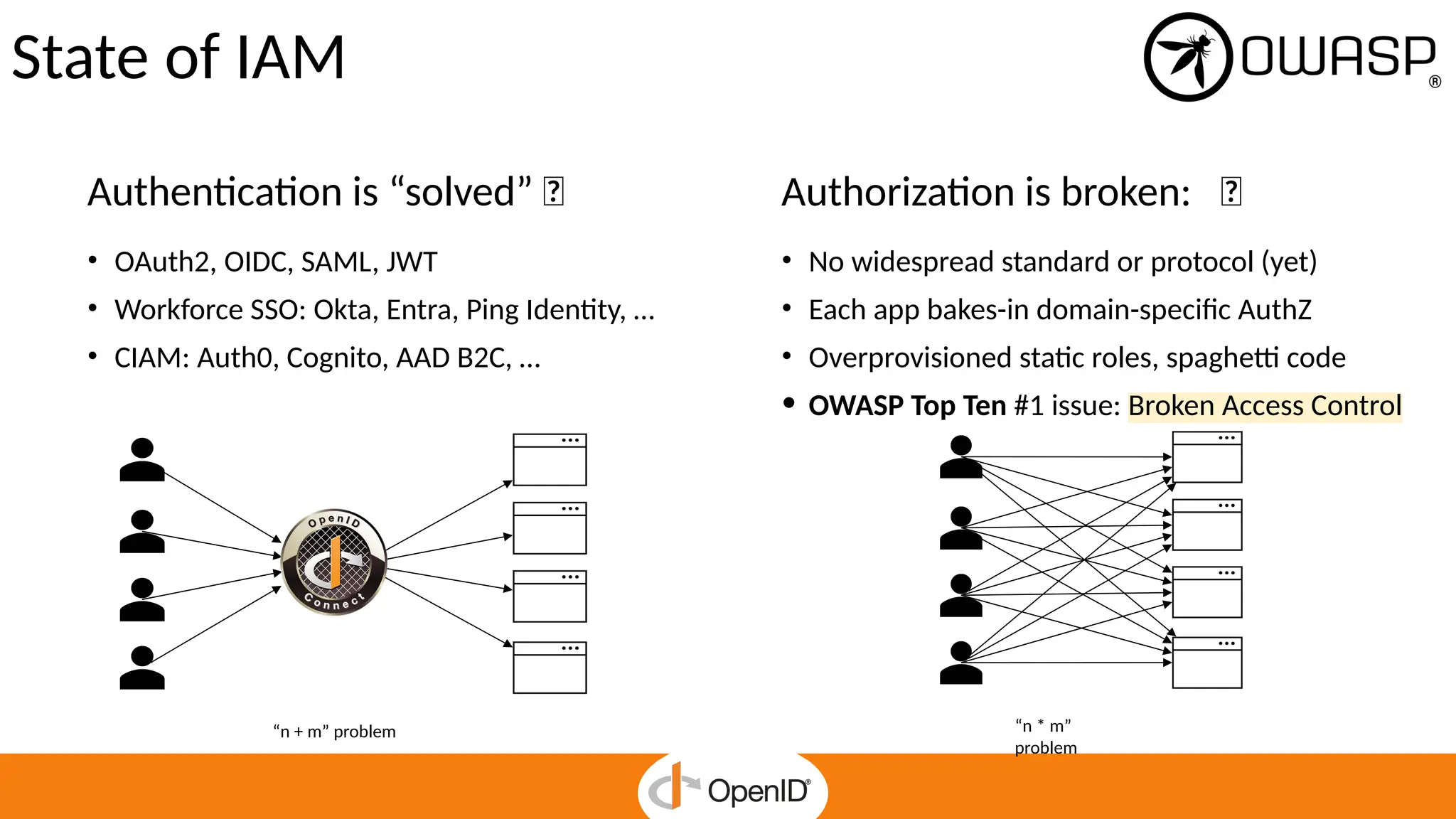
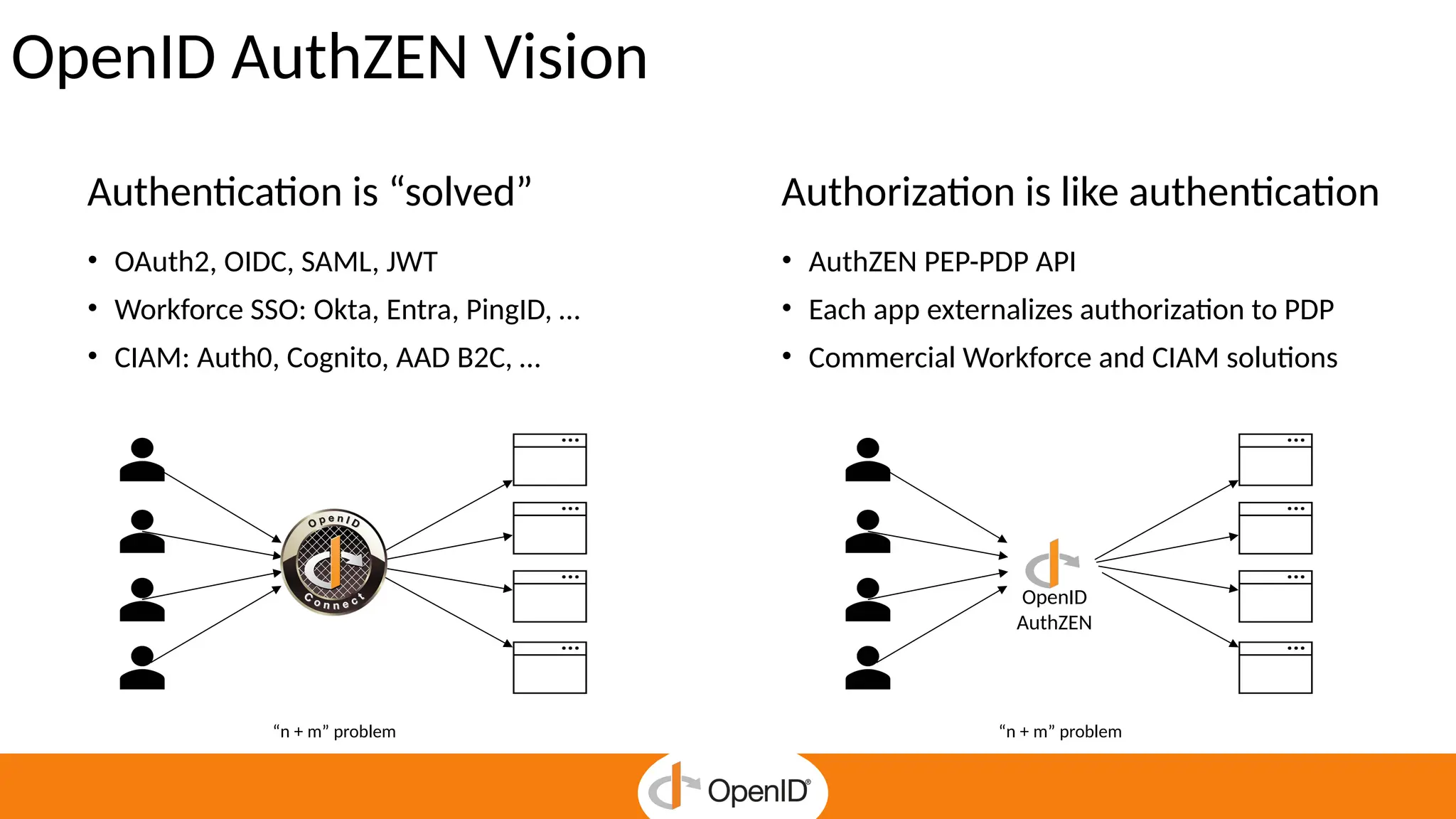
* The standard simplifies fine-grained authorization, reducing complexity and custom-made integrations.
* It enables Zero Trust security and continuous enforcement through a standard runtime access.

![Batch Binary API: Sample Payload
Use Cases
● Same as previous API plus
● Functional access control
● UI access control
● Access to medium-sized datasets
● Access to fields of a given record…
{
"subject": {
"type": "user",
"id": "alice@example.com"
}, "resource": {
"type": "record",
"id": "123"
}, "evaluations": [{
"action": {
"name": "read"
}
},{
"action": {
"name": "edit"
}
}]}
{"evaluations": [
{"decision": true},
{"decision": false}
]}
Reque
st
Respon
se](https://image.slidesharecdn.com/authzen-gartner-iam-2025-grapevine-251212092628-c90c9511/75/OpenID-AuthZEN-Overview-Gartner-IAM-25-14-2048.jpg)
![Search API: Sample Payload
Search APIs
● Subject Search
○ Who can view record #1?
● Resource Search
○ Which record can Alice view?
● Action Search
○ What can Alice do on record #1?
Use Cases
● Dynamic data filtering
● Entitlement access review
● Entitlement provisioning
● Access matrix generation
● Authorization logic testing
{
"subject": {
"type": "user"
},
"action": {
"name": "view"
},
"resource": {
"type":
"record",
"id": "101"
}
}
{
"results": [
{
"type": "user",
"id": "bob"
},
{
"type": "user",
"id": "carol"
}]
}
Reque
st
Respon
se
Who can view
record 101?
Bob and Carol](https://image.slidesharecdn.com/authzen-gartner-iam-2025-grapevine-251212092628-c90c9511/75/OpenID-AuthZEN-Overview-Gartner-IAM-25-15-2048.jpg)