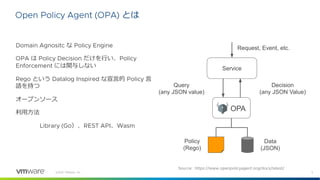
The document provides an introduction to the Open Policy Agent (OPA), a domain-agnostic policy engine that focuses on policy decisions without enforcing them. It covers the use of Rego, a declarative policy language, through examples and discusses concepts such as complete and partial rules, logical operations, and built-in functions. The content is aimed at developers and practitioners interested in using OPA for managing policies across various systems.



![6
©2021 VMware, Inc.
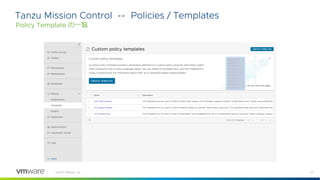
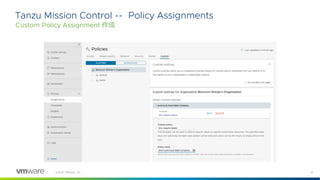
Rego Primer by example
Network, Server, App Toplogies
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
JSON
web app db
p1 p2 p3 p4
Net1 (public)
Net2 (private)
https ssh tomcat mysql
Internet](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-6-320.jpg)
![7
©2021 VMware, Inc.
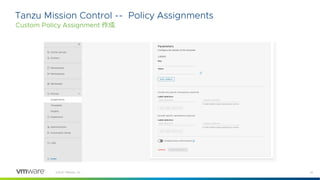
Rego Primer by example (1)
Complete Rules, Arrays, Logical AND, Assignments, Anonymous Variable, Packages
package example.rules
any_public_networks = true {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"any_public_networks": true
}
Policy Input
Output](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-7-320.jpg)
![8
©2021 VMware, Inc.
Rego Primer by example (1)
Complete Rules, Arrays, Logical AND, Assignments, Anonymous Variable, Packages
package example.rules
any_public_networks = true {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"any_public_networks": true
}
Policy Input
Output
Complete Rule:
<head> = <term> { <body> }
<body> が true であれば <head> = <term> になる。
”= true” は省略可能。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-8-320.jpg)
![9
©2021 VMware, Inc.
Rego Primer by example (1)
Complete Rules, Arrays, Logical AND, Assignments, Anonymous Variable, Packages
package example.rules
any_public_networks = true {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"any_public_networks": true
}
Policy Input
Output
“input” は予約されたグローバル変数。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-9-320.jpg)
![10
©2021 VMware, Inc.
Rego Primer by example (1)
Complete Rules, Arrays, Logical AND, Assignments, Anonymous Variable, Packages
package example.rules
any_public_networks = true {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"any_public_networks": true
}
Policy Input
Output
[ ] は配列を表す。‘_’ は無名変数。後に参
照する必要がなければ無名変数を使うこと
ができる。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-10-320.jpg)
![11
©2021 VMware, Inc.
Rego Primer by example (1)
Complete Rules, Arrays, Logical AND, Assignments, Anonymous Variable, Packages
package example.rules
any_public_networks = true {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"any_public_networks": true
}
Policy Input
Output
<body> 中の複数⾏の <expression> は、Logical
AND として解釈される。”<express1> ;
<expression2>” と書いても同様。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-11-320.jpg)
![12
©2021 VMware, Inc.
Rego Primer by example (1)
Complete Rules, Arrays, Logical AND, Assignments, Anonymous Variable, Packages
package example.rules
any_public_networks = true {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"any_public_networks": true
}
Policy Input
Output
”:=” は assginment(代⼊) operator。Rego の変数
は immutable なので、同じ変数に⼆度 ”:=” で代⼊す
ることはできない。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-12-320.jpg)
![13
©2021 VMware, Inc.
Rego Primer by example (1)
Complete Rules, Arrays, Logical AND, Assignments, Anonymous Variable, Packages
package example.rules
any_public_networks = true {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"any_public_networks": true
}
Policy Input
Output
Package は Rego のルールに名前空間
を作り出す。Data API で呼び出される
場合も、この名前空間が使われる。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-13-320.jpg)
![14
©2021 VMware, Inc.
Rego Primer by example (2)
Partial Rules
package example.rules
public_network[net.id] {
net := input.networks[_]
net.public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"public_network": [
"net1"
]
}
Policy Input
Output
<head> が [ ] を持っている場合は、Partial
Rule と呼ばれ、複数の値をセットするのに
使われる。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-14-320.jpg)
![15
©2021 VMware, Inc.
Rego Primer by example (3)
Logical OR
package example.rules
shell_accessible[server.id] {
server := input.servers[_]
server.proto[_] == "telnet"
}
shell_accessible[server.id] {
server := input.servers[_]
server.proto[_] == "ssh"
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"shell_accessible": [
"web"
]
}
Policy Input
Output
同じ <head> を持つルールが複数ある場合
は、それらは Logical OR と解釈される。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-15-320.jpg)
![16
©2021 VMware, Inc.
Rego Primer by example (4)
Iterations
package example.rules
public_ports[id] {
some i, j
id := input.ports[i].id
input.ports[i].network == input.networks[j].id
input.networks[j].public
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"public_ports": [
"p1"
]
}
Policy Input
Output
Rego では <expression> に “some” で宣⾔
した変数を埋め込むことで暗黙的にループ
が形成される](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-16-320.jpg)
![18
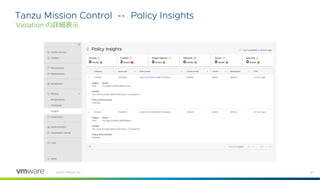
©2021 VMware, Inc.
クイズ
Public な network に接続されている port を持っている server のリストを取得
package example.rules
public_servers[server] {
some i, j, k
input.servers[i].ports[_] == input.ports[j].id
input.networks[k].id == input.ports[j].network
input.networks[k].public
server := input.servers[i].id
}
{
"servers": [
{ "id": "web",
"proto": ["https", "ssh"],
"ports": ["p1", "p2"]},
{ "id": "app",
"proto": ["tomcat"],
"ports": ["p3"]},
{ "id": "db",
"proto": ["mysql"],
"ports": ["p4"]}
],
"networks": [
{"id": "net1", "public": true},
{"id": "net2", "public": false}
],
"ports": [
{"id": "p1", "network": "net1"},
{"id": "p2", "network": "net2"},
{"id": "p3", "network": "net2"},
{"id": "p4", "network": "net2"}
]
}
{
"public_servers": [
"web"
]
}
Policy Input
Output
??? 回答は後⽇ Tweet します。](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-17-320.jpg)



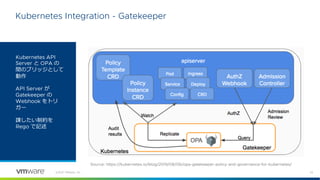
![24
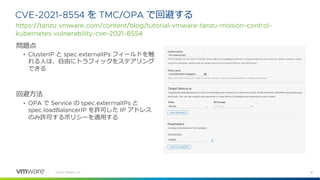
©2021 VMware, Inc.
Policy Template and Policy Instance CRD
apiVersion: templates.gatekeeper.sh/v1beta1
kind: ConstraintTemplate
metadata:
name: k8srequiredlabels
spec:
crd:
spec:
names:
kind: K8sRequiredLabels
validation:
# Schema for the `parameters` field
openAPIV3Schema:
properties:
labels:
type: array
items: string
targets:
- target: admission.k8s.gatekeeper.sh
rego: |
package k8srequiredlabels
violation[{"msg": msg, "details": {"missing_labels": missing}}] {
provided := {label | input.review.object.metadata.labels[label]}
required := {label | label := input.parameters.labels[_]}
missing := required - provided
count(missing) > 0
msg := sprintf("you must provide labels: %v", [missing])
}
apiVersion:
constraints.gatekeeper.sh/v1beta1
kind: K8sRequiredLabels
metadata:
name: ns-must-have-gk
spec:
match:
kinds:
- apiGroups: [""]
kinds: ["Namespace"]
parameters:
labels: ["gatekeeper"]](https://image.slidesharecdn.com/openpolicyagentopaprimer-210120125242/85/Open-Policy-Agent-OPA-23-320.jpg)