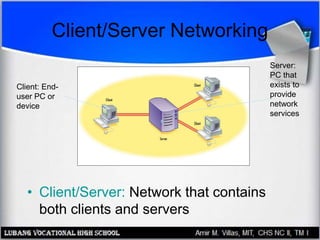
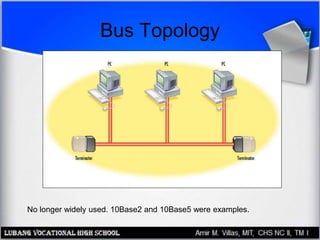
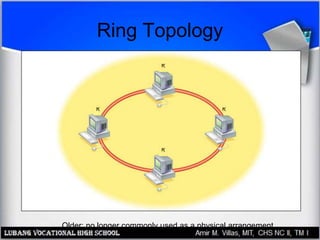
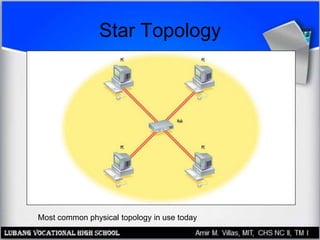
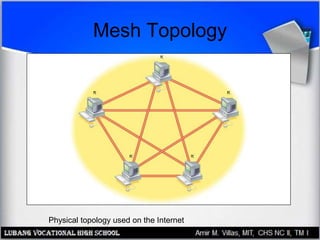
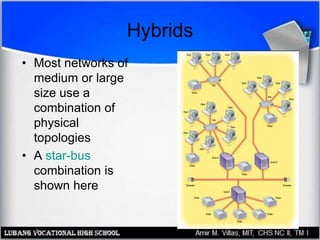
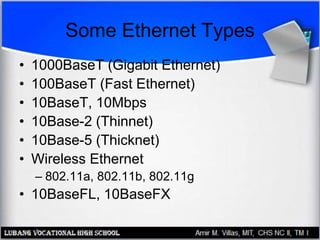
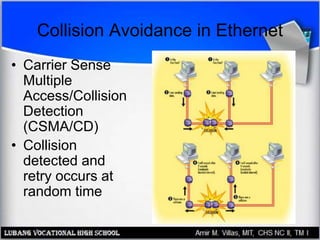
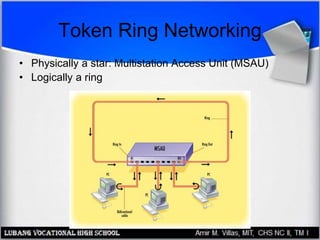
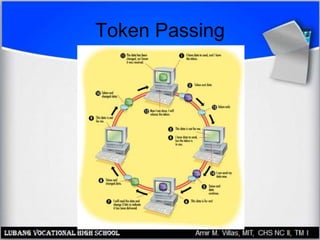
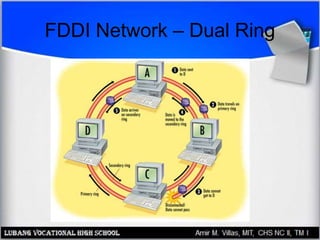
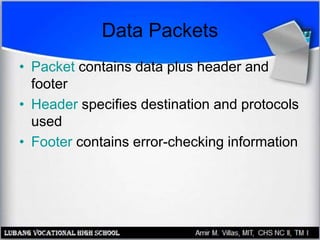
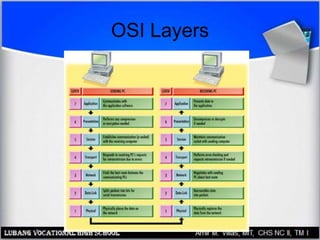
This document discusses networking hardware concepts and components. It describes common networking topologies like star, bus, ring and mesh. It also covers common networking standards for wired connections like Ethernet, Token Ring and FDDI as well as wireless standards like 802.11a, 802.11b, and 802.11g. Finally, it discusses the hardware components needed to create both wired and wireless networks, including hubs, switches, routers and network interface cards.