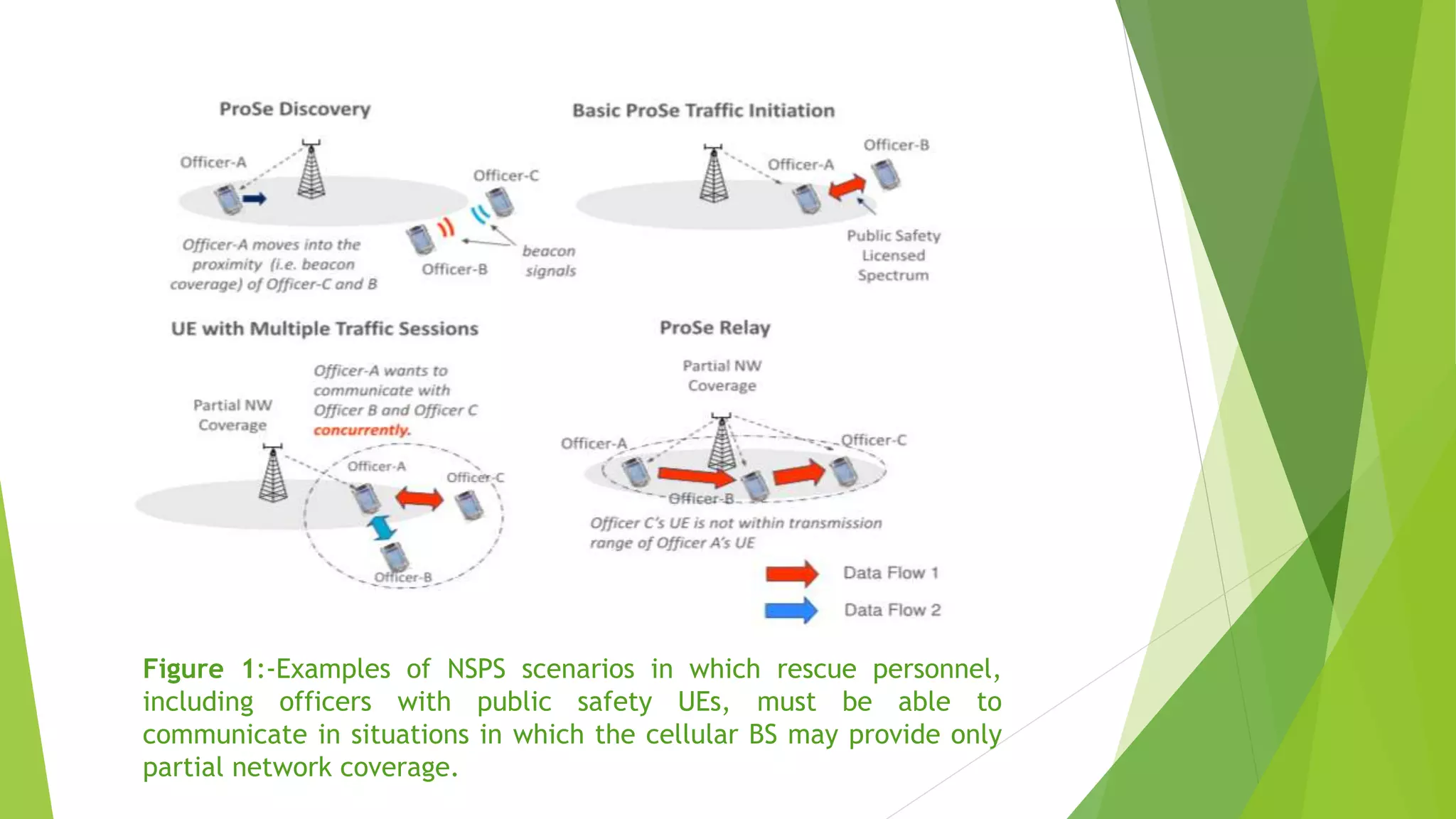
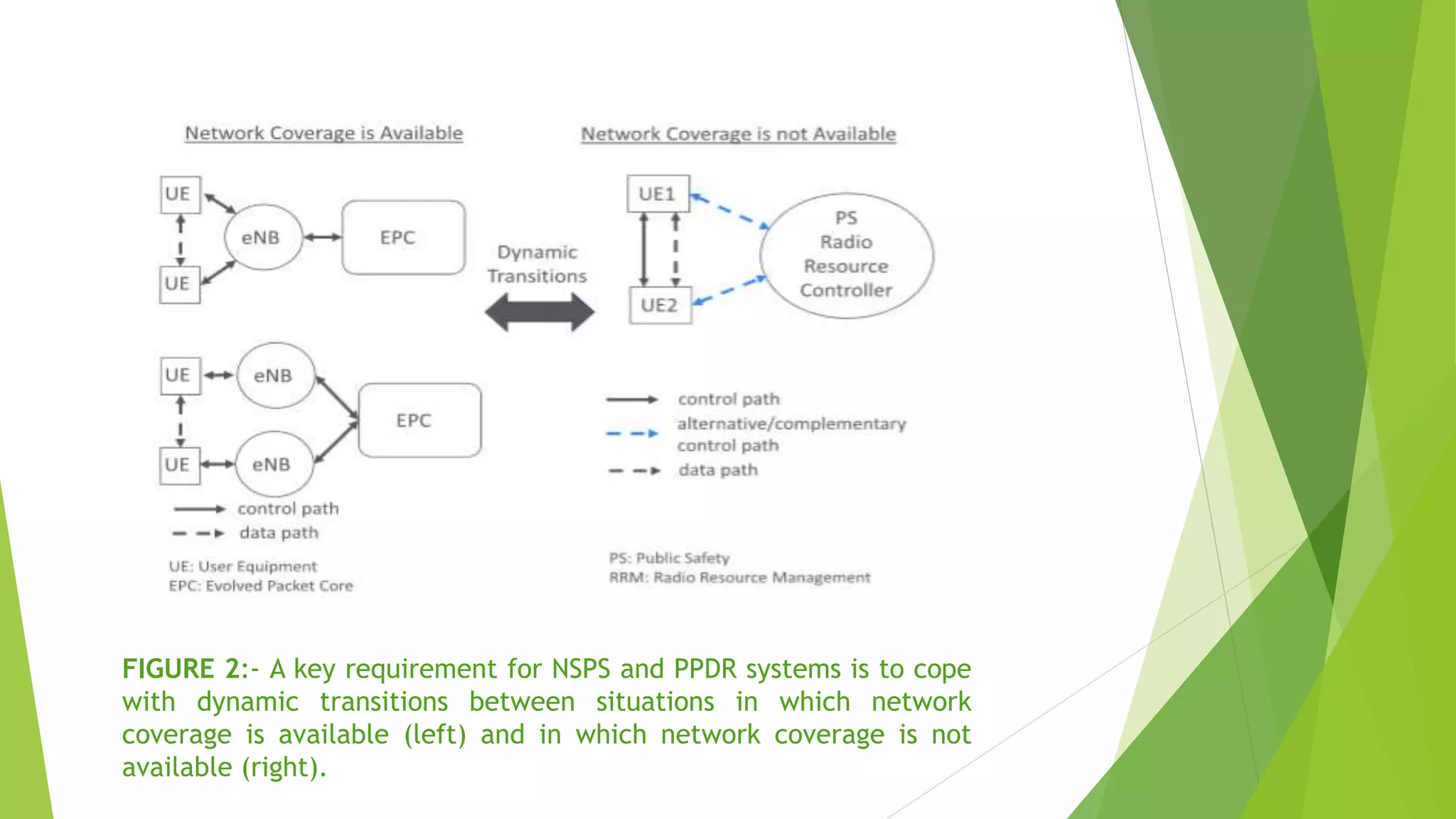
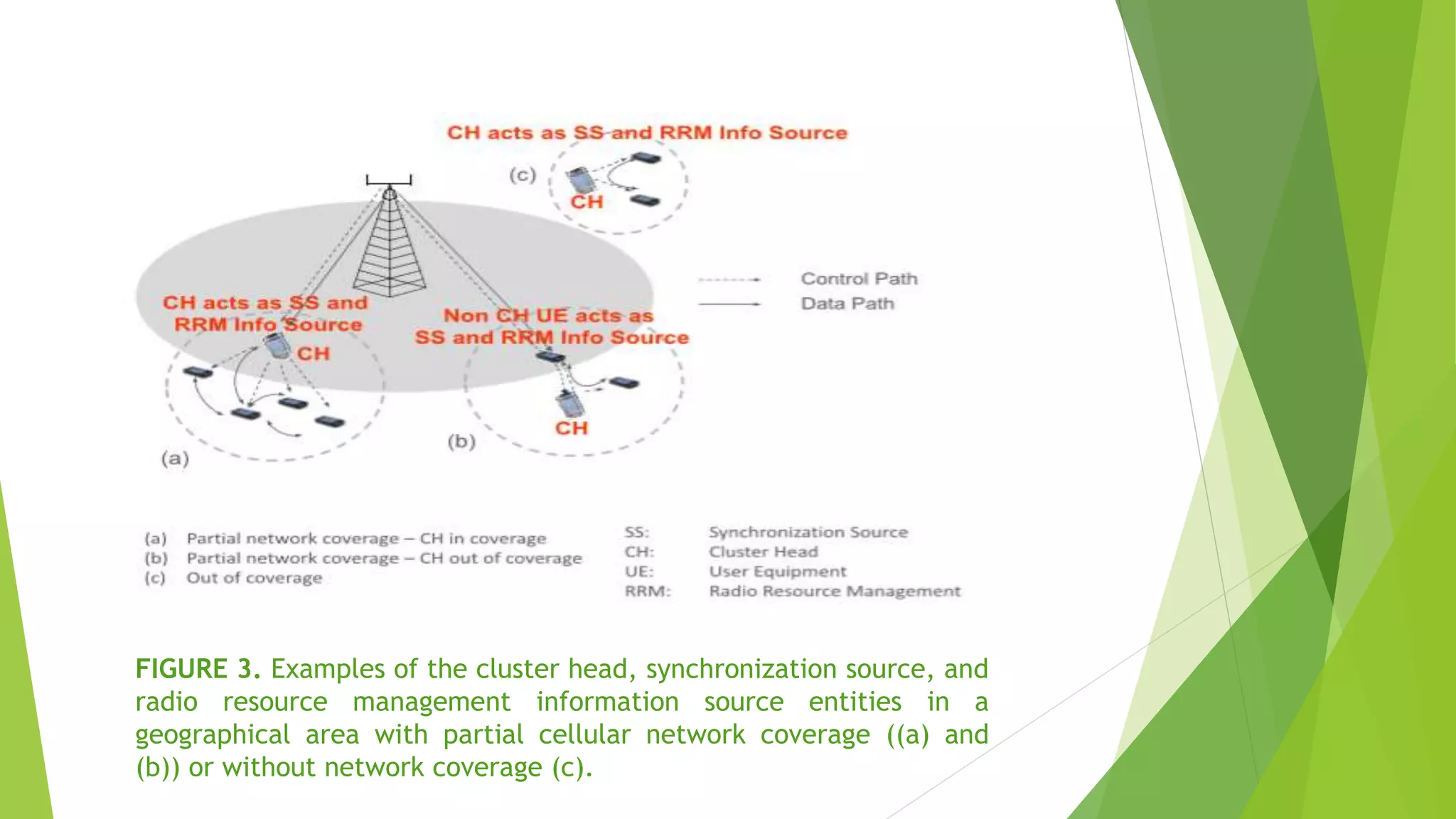
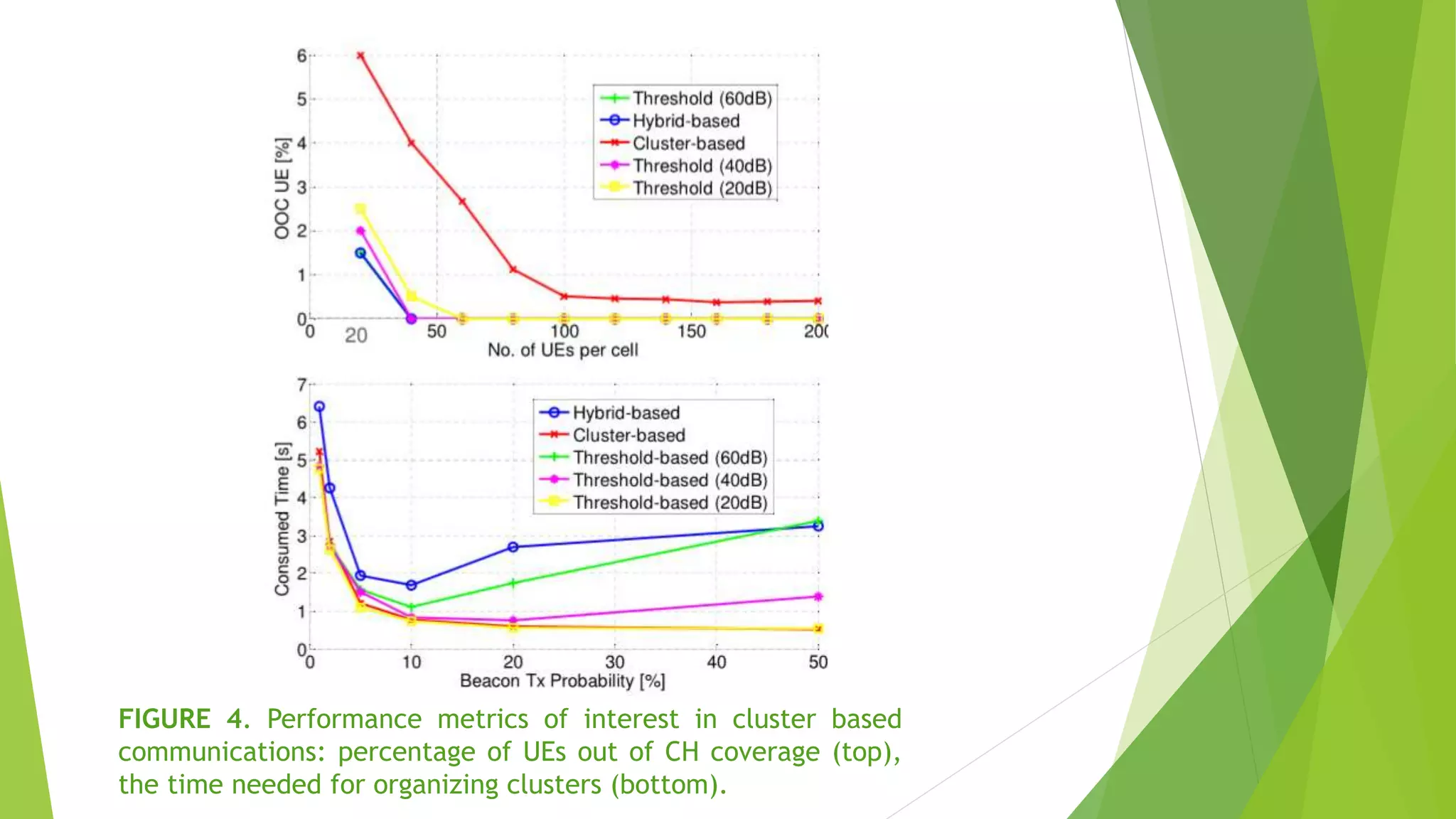
The document discusses using device-to-device (D2D) communications to provide national security and public safety services when cellular infrastructure may be unavailable. It proposes a clustering solution where user equipment take on roles like cluster head, synchronization source, and resource manager. This allows for communication even without network coverage by enabling devices to directly communicate and self-organize. The clustering approach supports both infrastructure-based and standalone D2D operation to ensure emergency access to services.