Embed presentation
Downloaded 203 times








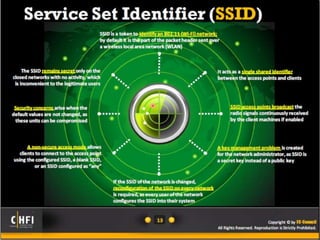
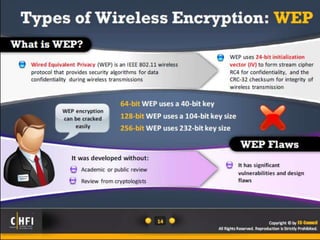
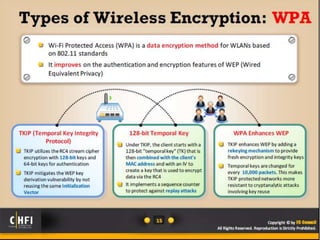
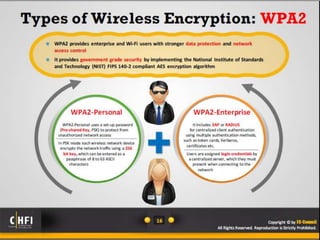
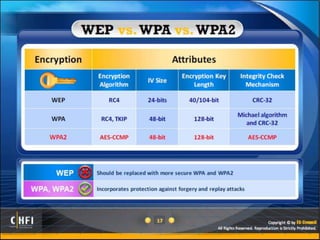

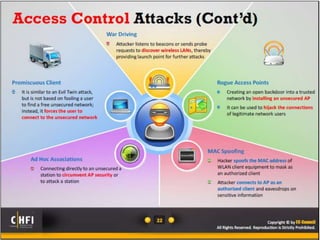
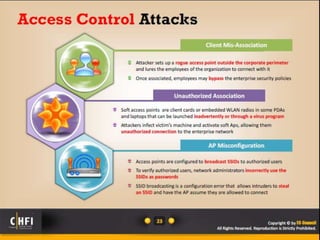
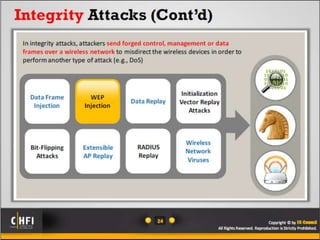



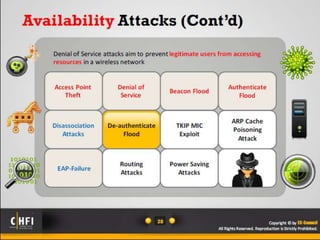
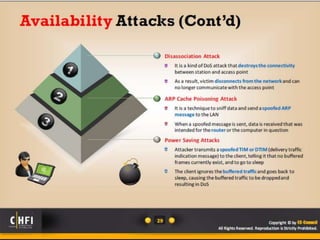

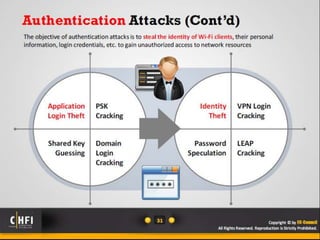
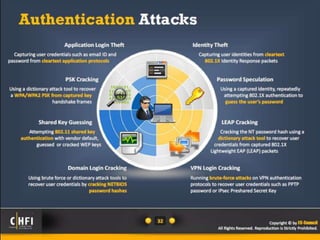

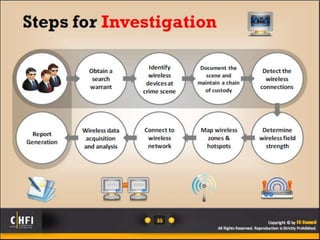
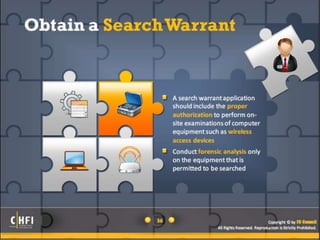
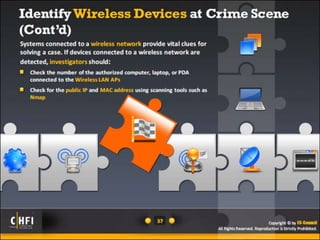


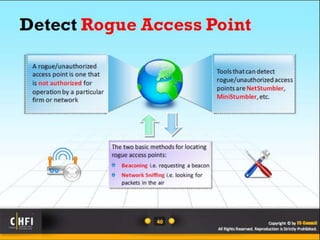


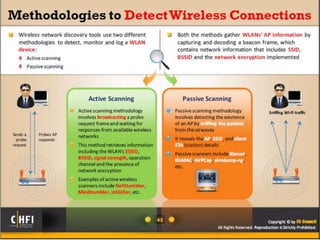
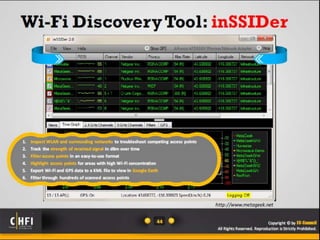
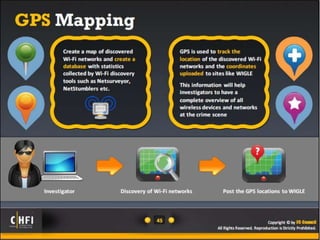
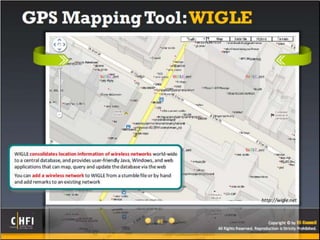
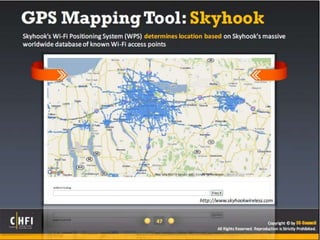
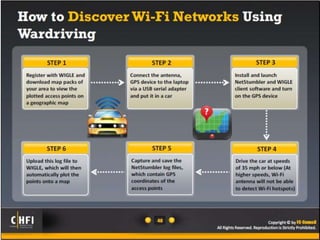

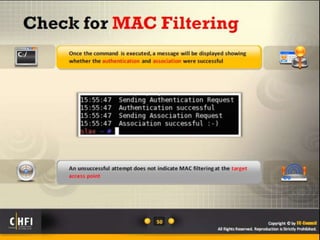

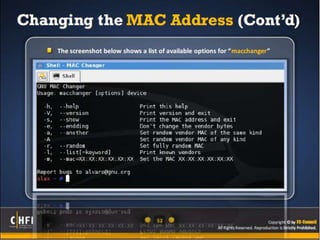



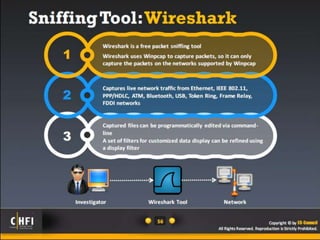
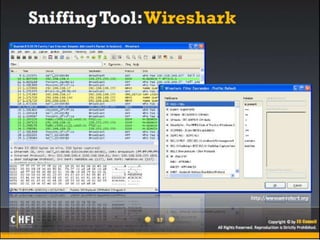
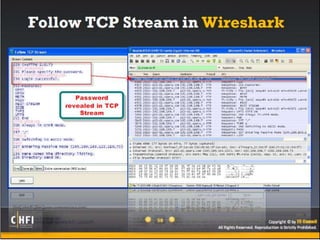
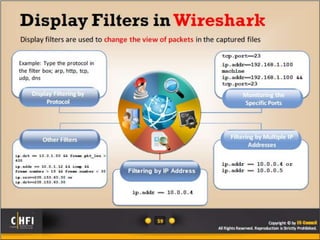

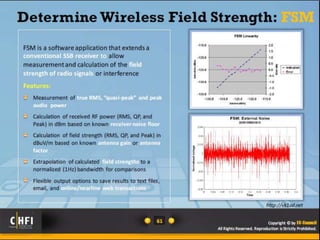


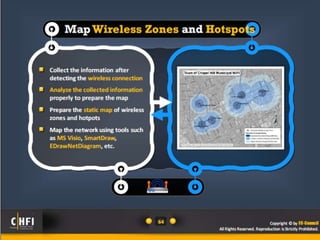
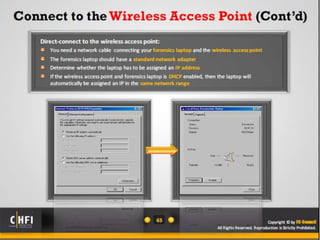

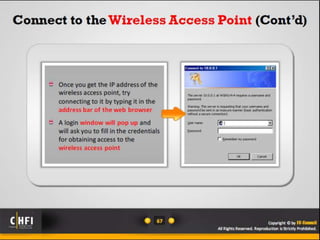


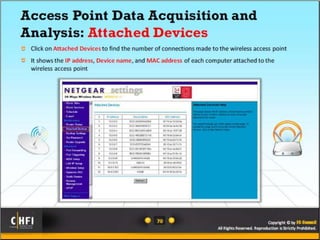



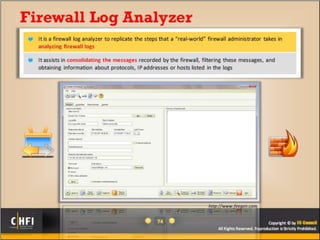
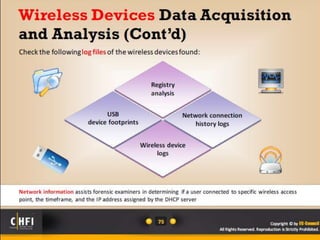
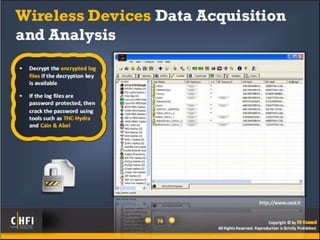


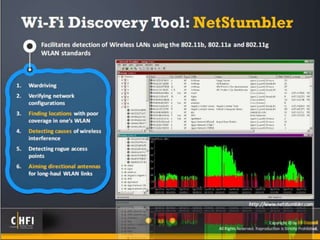
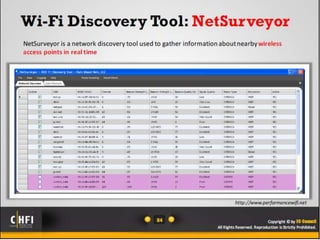

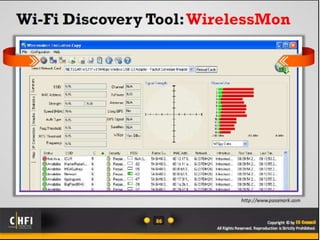
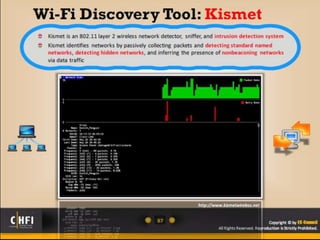
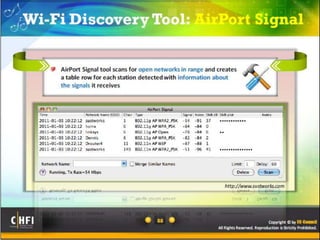


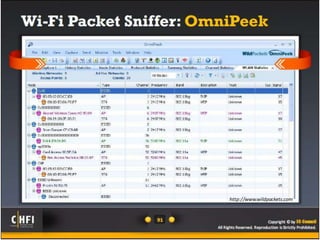
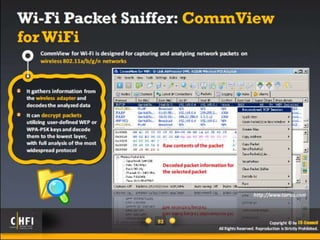
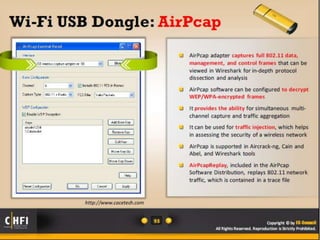
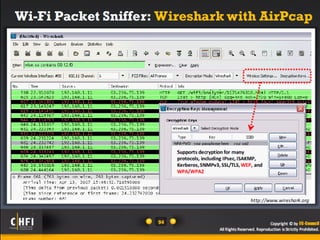
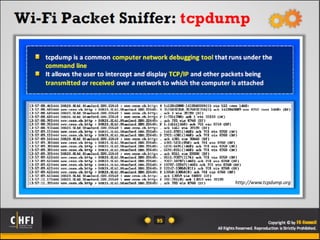


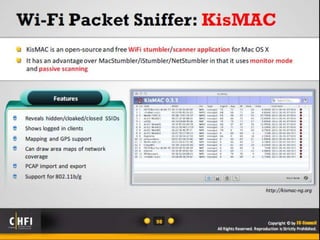





The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise has also been shown to increase gray matter volume in the brain and reduce risks for conditions like Alzheimer's and dementia.










































































































