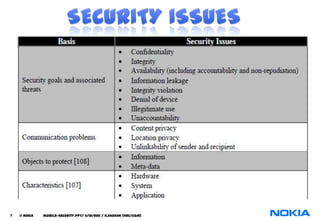
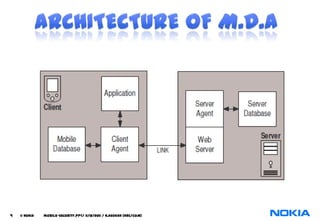
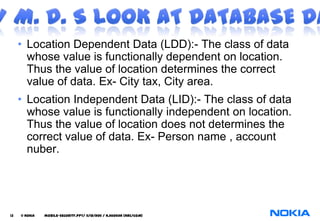
The document discusses security considerations for mobile databases. It notes that mobile users need to work offline due to poor connections, and applications need access to local hardware. It also describes location dependent data and location independent data. The document recommends using HTTPS to synchronize mobile and central databases securely and encrypting the local mobile database for protection. Database triggers are used to control user access and authorization for data manipulation.