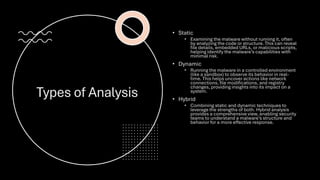
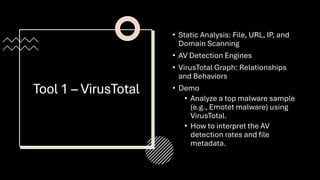
The document outlines a mission for cybersecurity professionals to analyze and neutralize various types of malware, including trojans, bots, and ransomware, using tools like VirusTotal, Malware Bazaar, and AnyRun. It emphasizes the importance of malware analysis for understanding and mitigating cyber threats and describes different analysis methods: static, dynamic, and hybrid. Additionally, it provides practical steps for using these tools to analyze specific malware samples and suggests a comprehensive approach by combining insights from all three tools.