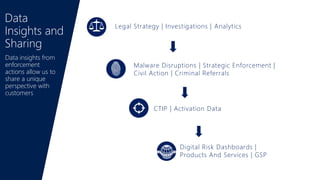
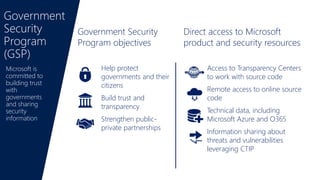
Big data, cybersecurity threats, and cybercrime are growing issues according to the document. Microsoft takes a layered approach to security across its many products and services to help protect customers. Key aspects of Microsoft's security approach include detection of threats using signals and machine learning, responding quickly to issues, and protecting endpoints. The Microsoft Digital Crimes Unit works with law enforcement and through public-private partnerships to disrupt malware and fight technical support scams and other technology-facilitated crimes.