Michaelcreations-Political-Rally-Security-Solution
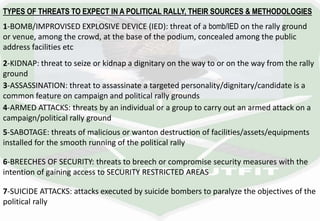
- 1. TYPES OF THREATS TO EXPECT IN A POLITICAL RALLY, THEIR SOURCES & METHODOLOGIES 1-BOMB/IMPROVISED EXPLOSIVE DEVICE (IED): threat of a bomb/IED on the rally ground or venue, among the crowd, at the base of the podium, concealed among the public address facilities etc 2-KIDNAP: threat to seize or kidnap a dignitary on the way to or on the way from the rally ground 3-ASSASSINATION: threat to assassinate a targeted personality/dignitary/candidate is a common feature on campaign and political rally grounds 4-ARMED ATTACKS: threats by an individual or a group to carry out an armed attack on a campaign/political rally ground 5-SABOTAGE: threats of malicious or wanton destruction of facilities/assets/equipments installed for the smooth running of the political rally 6-BREECHES OF SECURITY: threats to breech or compromise security measures with the intention of gaining access to SECURITY RESTRICTED AREAS 7-SUICIDE ATTACKS: attacks executed by suicide bombers to paralyze the objectives of the political rally
- 2. 8-RETALIATORY ATTACKS: threats to execute a retaliatory attack against a rival candidate is a common feature on campaign and political rally grounds SOURCES OF THREATS 1-TERRORISTS 2-CRIMINALS 3-THE MENTALLY DISTURBED 4-DISSATISFIED GOVT. WORKERS/THOSE WITH CRIMINAL MOTIVES 5-POLITICAL RIVALS 6-ACHANS IN THE CAMP
- 3. METHODOLOGIES Some of the methods used by criminals in political rallies/campaigns include the following: 1-KIDNAPPING 2-SABOTAGE: this involves the use of explosives or incendiaries (or a combination of both) on rally ground or against installed facilities 3-MANPADS 4-SUICIDE BOMBER 5-CBRN 6-SUBTERFUGE: the use of an unknowing person to commit an act of terrorism or crime 7-Poisons : the use of poisons to eliminate personalities considered as “Political threats”
- 4. SOLUTION 1- Thorough security scrutiny, evaluation and assessment of the venue to be used for the rally/campaign before the D-DAY. 2-Implementation of security measures that will neutralize every threat envisaged. 3-Choosing to be proactive rather than being reactive is a virtue that can never be quantified in monetary terms and yet it can save and secure many things money cannot buy. 4-Proper and effective access control 5-Making sure that vehicles/cars of candidates/dignitaries/political figures are located/parked in SRAs 6-Proper and effective crowd control, collaborating with emergency & health workers. 7-Proper Screening of all entering into the campaign/rally ground.
- 5. 8-Distinctive labels on all ENTRY and EXIT points, EMERGENCY EXITS etc. 9-Effective communication & networking system among all security operatives on the rally ground. 10-Ambulances/health and medical workers on ground to attend to any case of emergency 11-Mobile police, anti-riot police are to be on ground as well, so that we can be able to focus on the work of surveillance through the LCD MONITORS.
- 6. PAST VICTIMS OF POLITICAL ASSASSINATIONS J.F.KENEDY –NOV 22,1963 BENAZIR BHUTTO-DEC 27,2007 INDIRA GANDHI-OCT 31,1984 MAHATMA GANDHI-JAN 30,1948
- 7. YASSER ARAFAT-NOV 11,2004 MARTIN LUTHER KING JNR-APRL 4,1968 KURDISH WOMEN MURDERED IN PARIS-2013/01/10 ,SANKINE CANSIZ AMONG
- 8. PROMINENT NIGERIAN CASES/PHOTOS OMITTED FOR FAMILY’S SAKE 1-CHIEF BOLA IGE (A.D.) 2-HARRY MARSHAL (ANPP) 3-ENG. FUNSHO WILLIAMS(PDP) 4-AYO DARAMOLA(PDP) 5-JESSE ARUKWU(ACO) 6-OGBONAYA UCHE(ANPP) 7-A.K. DKKIBO(PDP) 8-DIPO DINA(AC) 9-ODUNAYO OMOBOLANLE OLAGBAJU(AD) 10-CHIEF CHUKWUDI OKAFOR(ANPP) 11-MODU FANNAMI GUBIO(ANPP) AND OTHERS IS IT TRUE THAT HISTORY DO REPEAT ITSELF BECAUSE WE DON’T LEARN FROM “HISTORY”? WE CAN CHANGE
- 9. HHMD-HAND HELD METAL DETECTORS
- 10. COMBINED USAGE- SECURITY PERSONNEL USING HHMDs & WTMDs@ THE AIRPORT
- 11. SECURITY CHECKS IN THE COURT OF LAW SECURITY CHECKS USING HHMD, HAND HELD METAL DETECTOR
- 13. GROUND SEARCH USING A GROUND SCANNER/METAL DETECTORS; TO LOCATE HIDDEN,CONCEALED AMMUNITIONS,MINES,WEAPONRY …….etc
- 14. Surveillance tools and equipments
- 15. A complete surveillance kit
