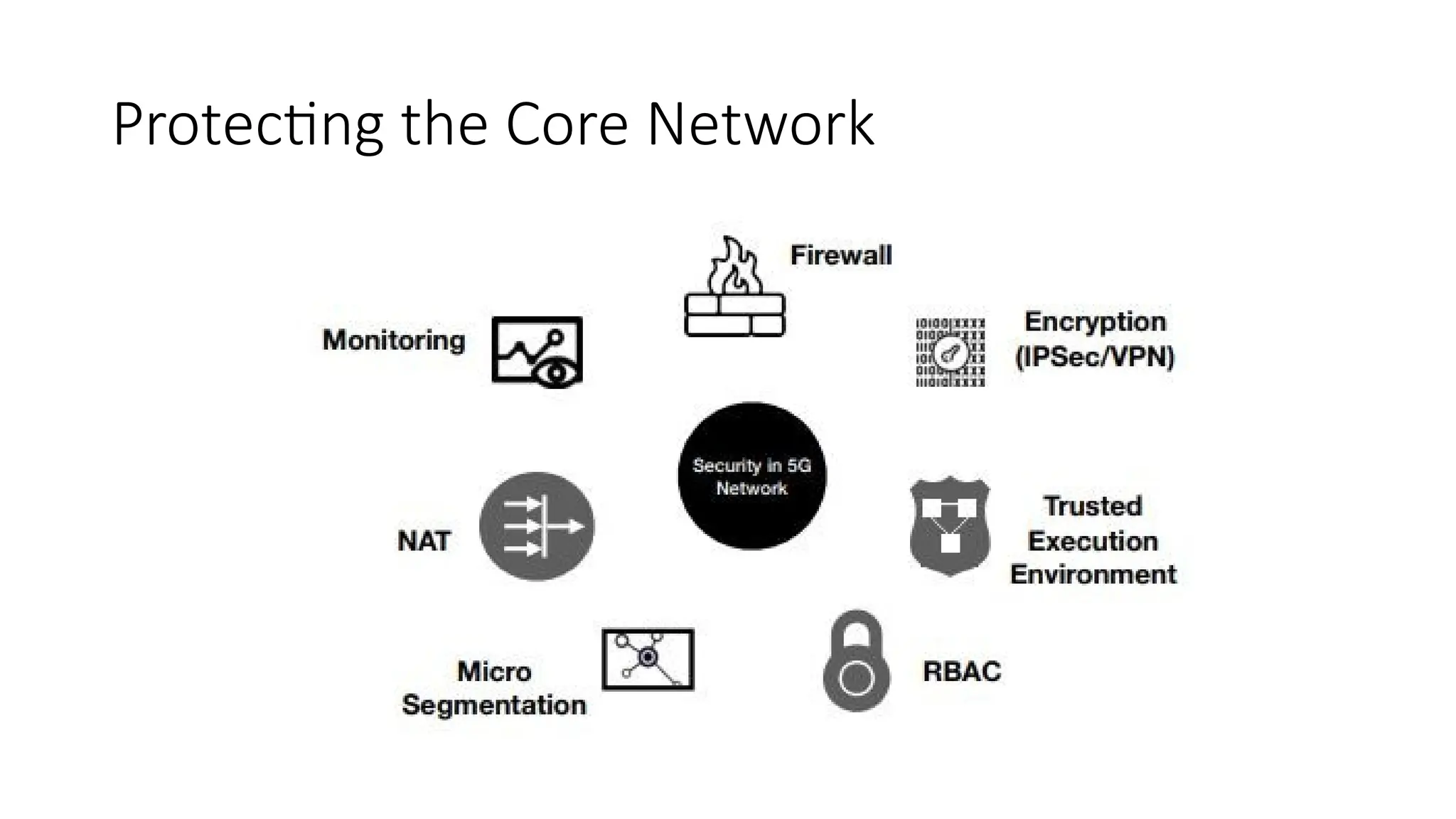
MEC is one of the vulnerable entities in a 5G network, as it gets deployed at the edge of the network.
The risk can be minimized by deploying endpoint protection software in the MEC host.
MEC applications and services can be protected and secured by configuring and enforcing application or service specific policies.
For example, configuring role-based access control for administrators managing the MEC applications and services.
In addition, implement monitoring to provide enhanced visibility of the MEC applications, MEC services and the MEC infrastructure components.