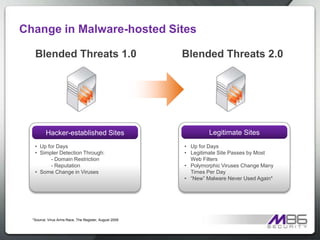
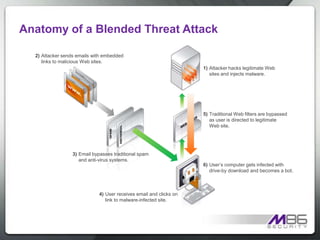
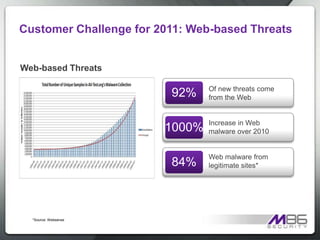
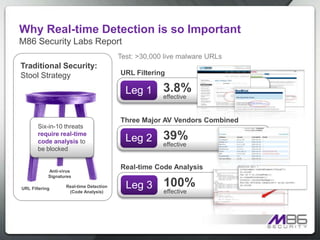
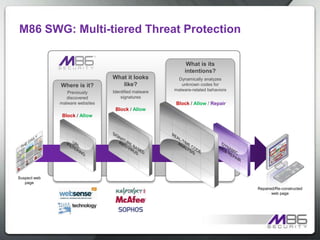
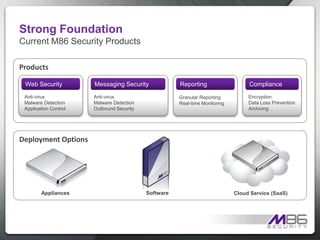
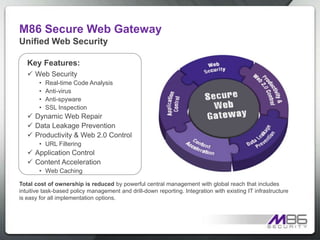
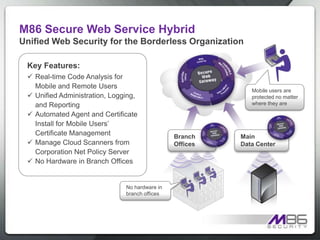
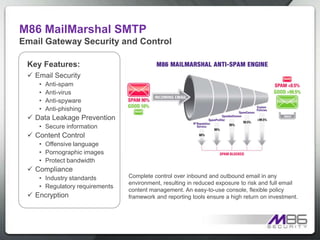
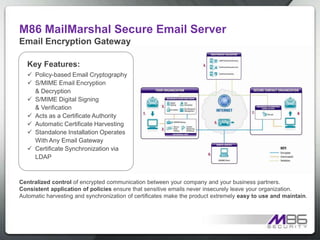
The document discusses internet security threats and solutions from M86 Security. It notes that malware is increasingly being hosted on legitimate websites through hacking or by embedding malicious code. It also discusses "blended threats" where attackers send links to malware-infected legitimate websites that can bypass traditional security filters. The document outlines M86 Security's multi-tiered threat protection approach using URL filtering, signatures, and real-time code analysis. It provides an overview of M86 Security products including appliances, software, and cloud-based options for web security, email security, and compliance needs.