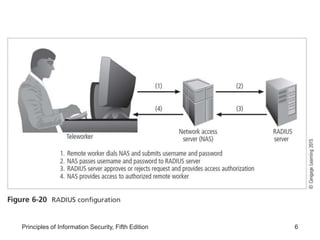
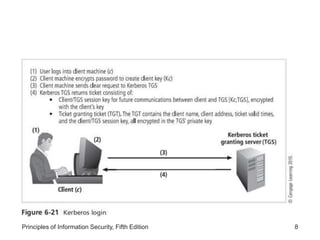
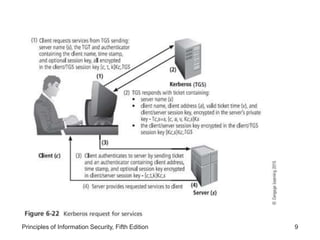
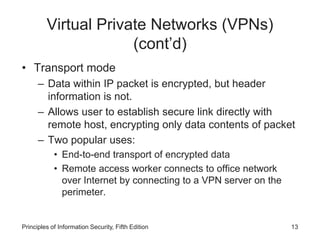
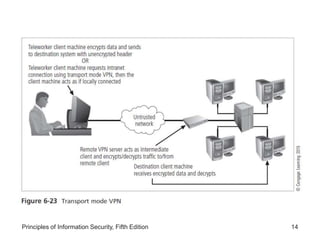
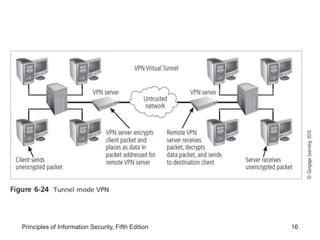
This document discusses remote access security and virtual private networks. It covers authentication technologies like RADIUS, Diameter, TACACS, Kerberos and SESAME that secure remote access. It also describes firewalls, content filtering and the use of VPNs to securely extend private networks over public networks using encryption and authentication. VPNs can operate in transport mode, encrypting only data, or tunnel mode, encrypting the entire network traffic packet.