This document provides an overview of key network terminology and concepts, including:
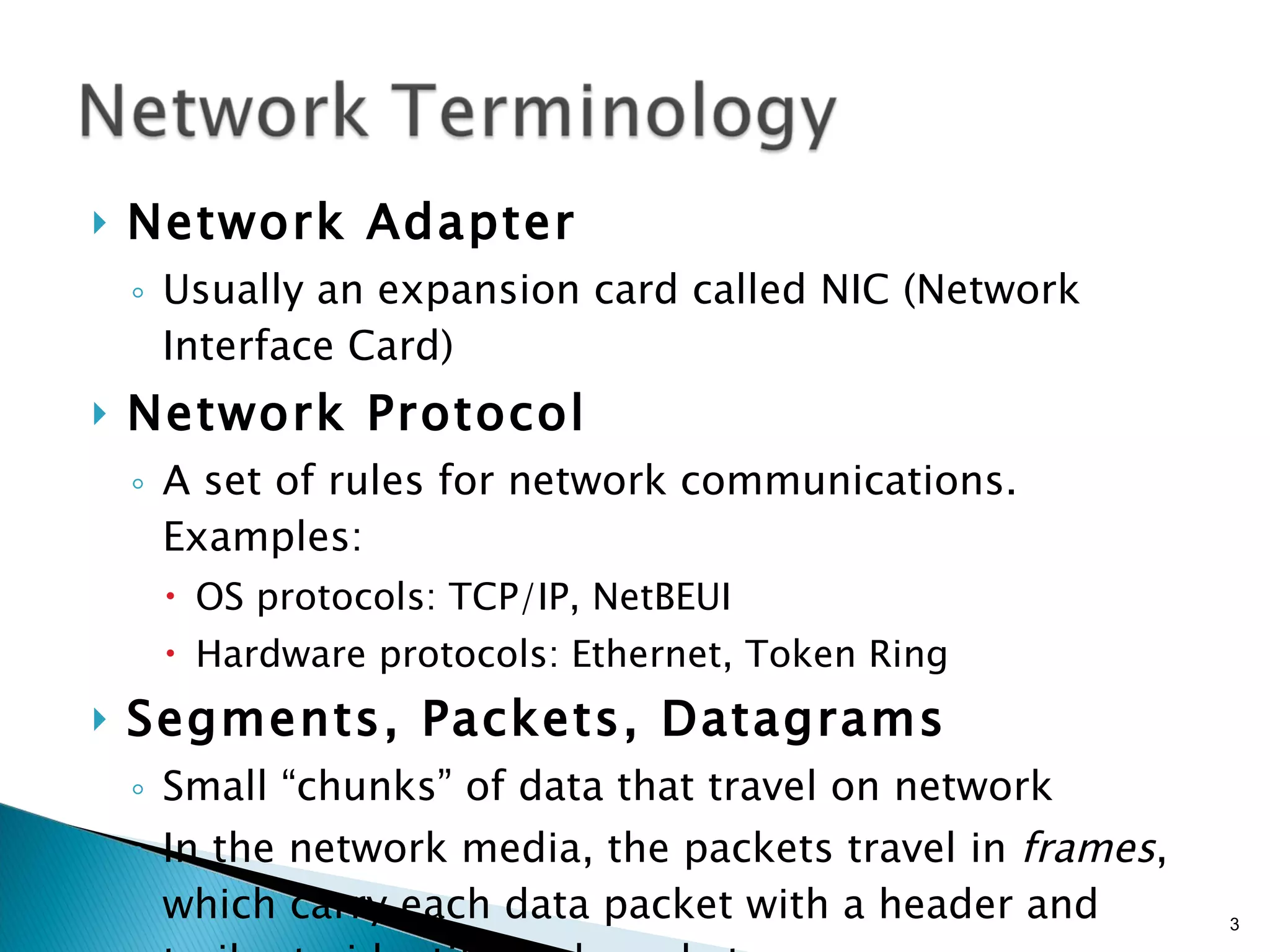
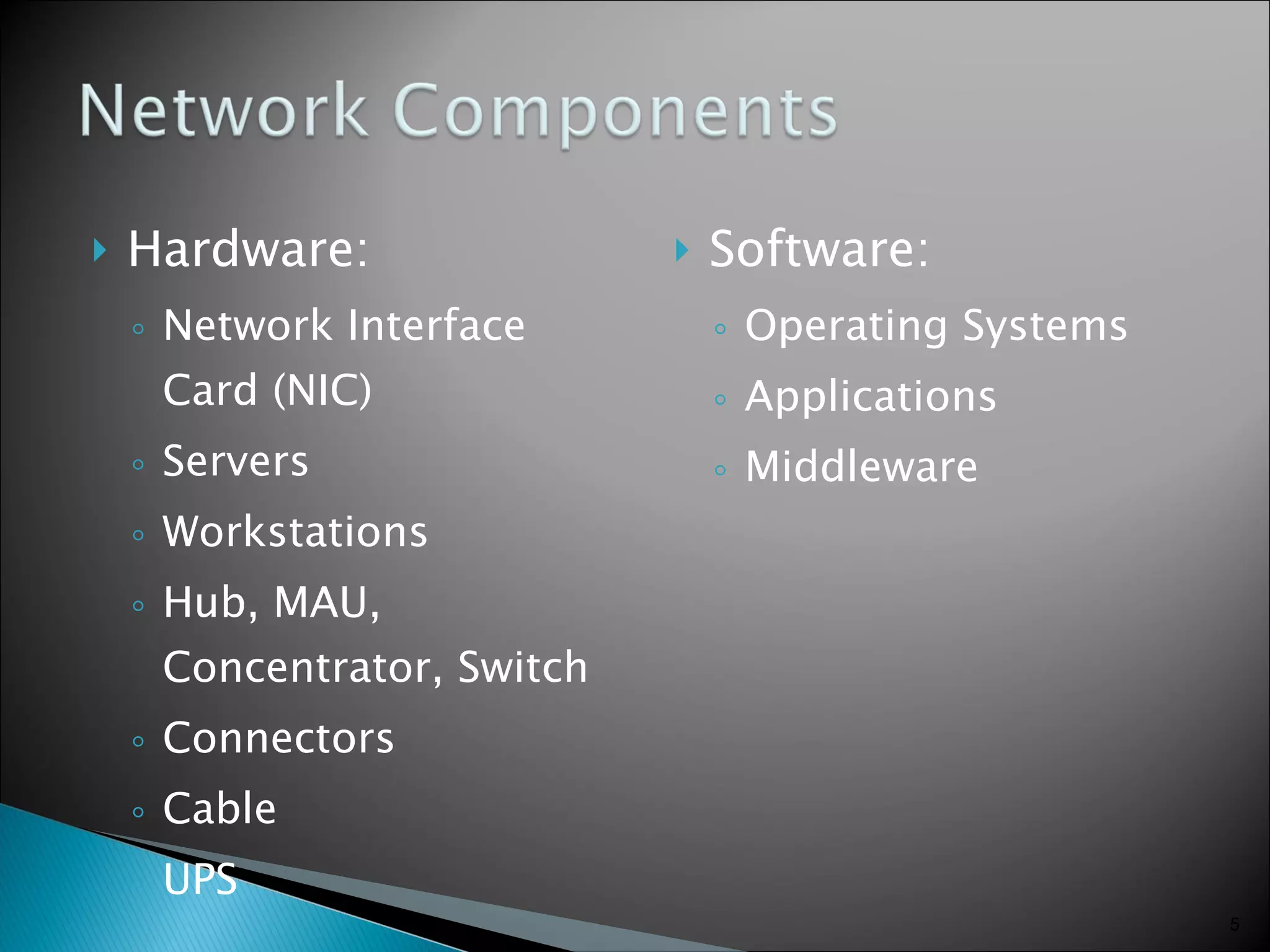
- Network components like network interface cards, hubs, switches, and cables.
- Network protocols and how they allow different devices to communicate.
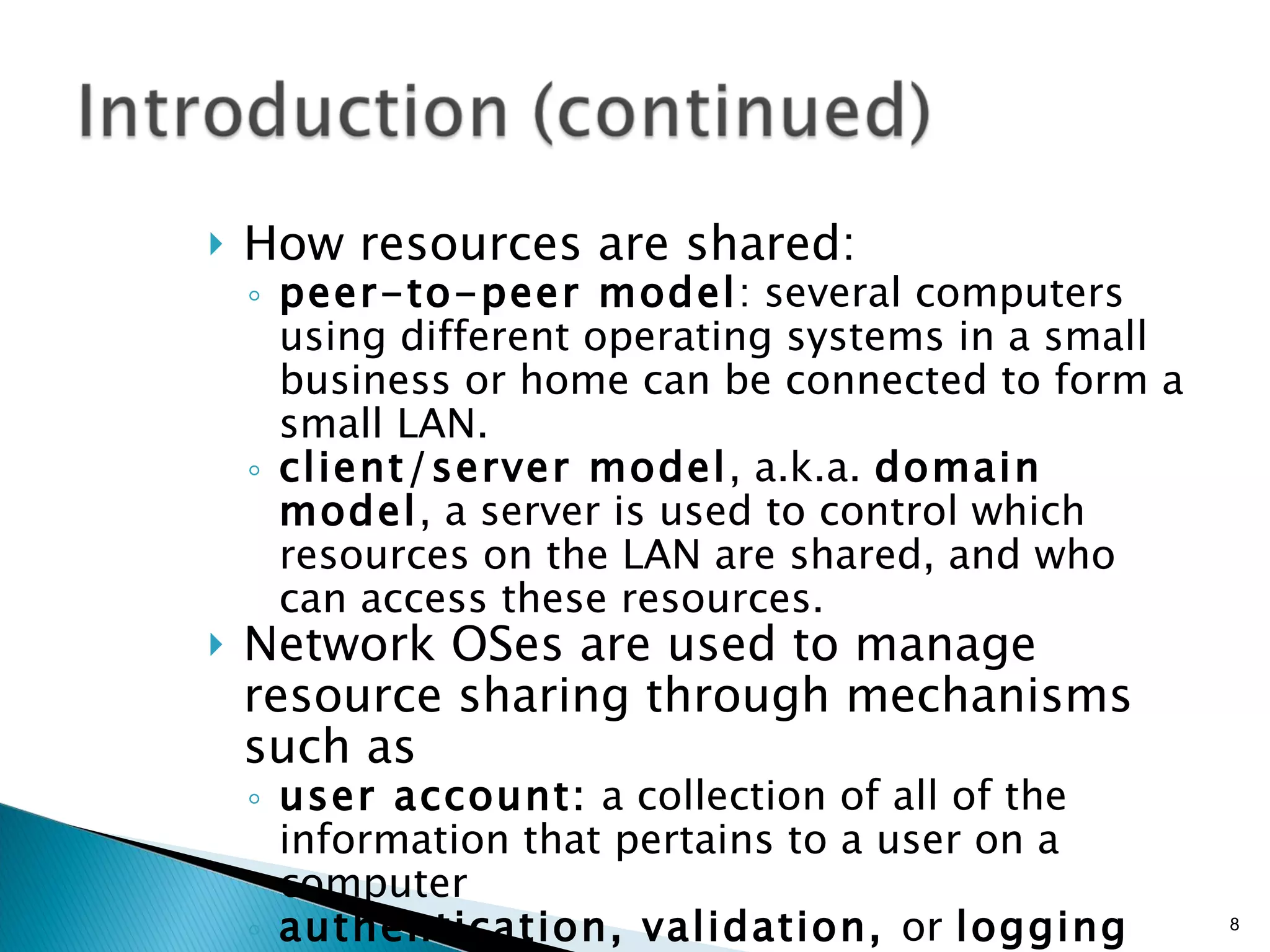
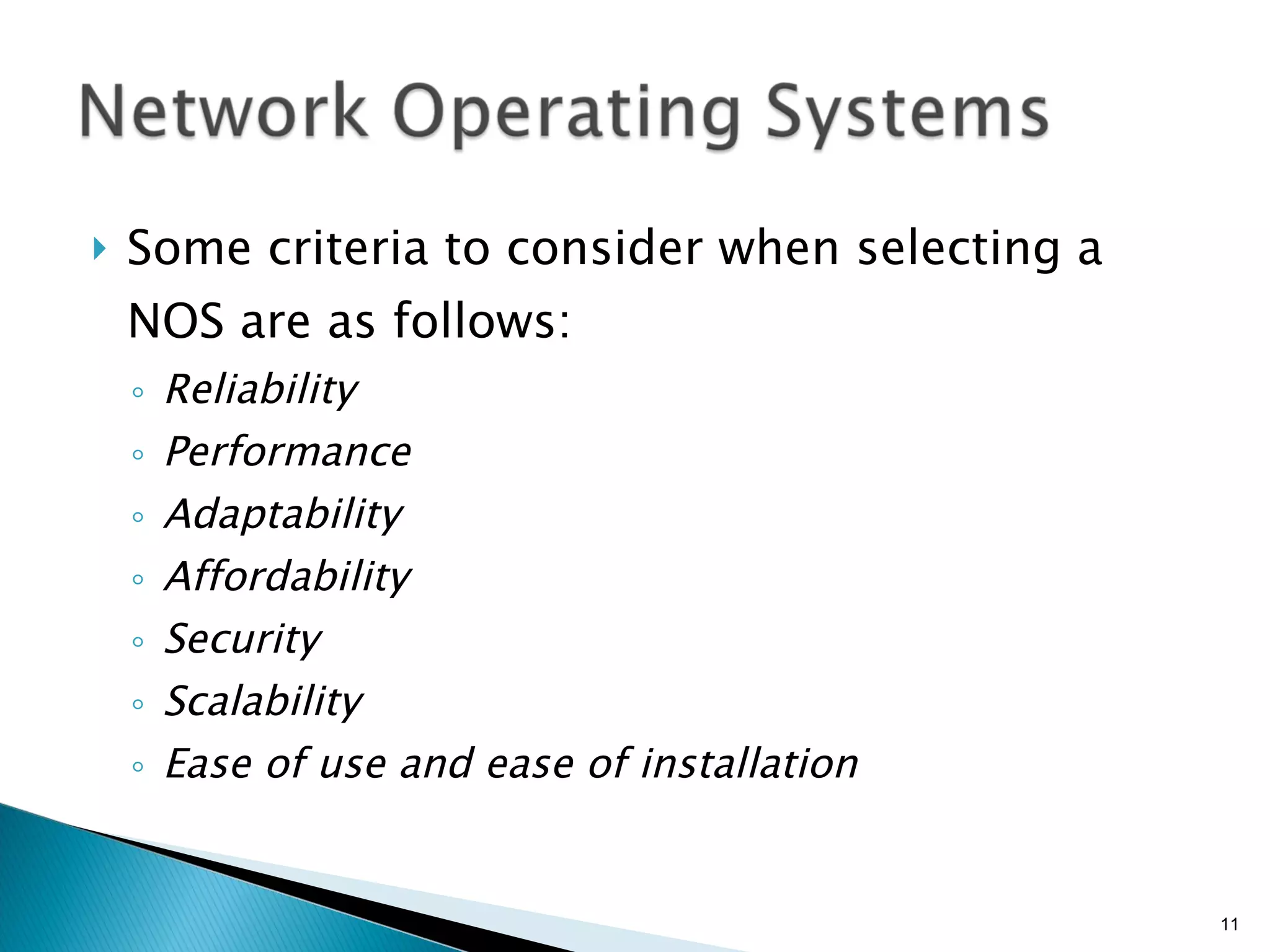
- Operating systems' role in managing network resources and enabling sharing.
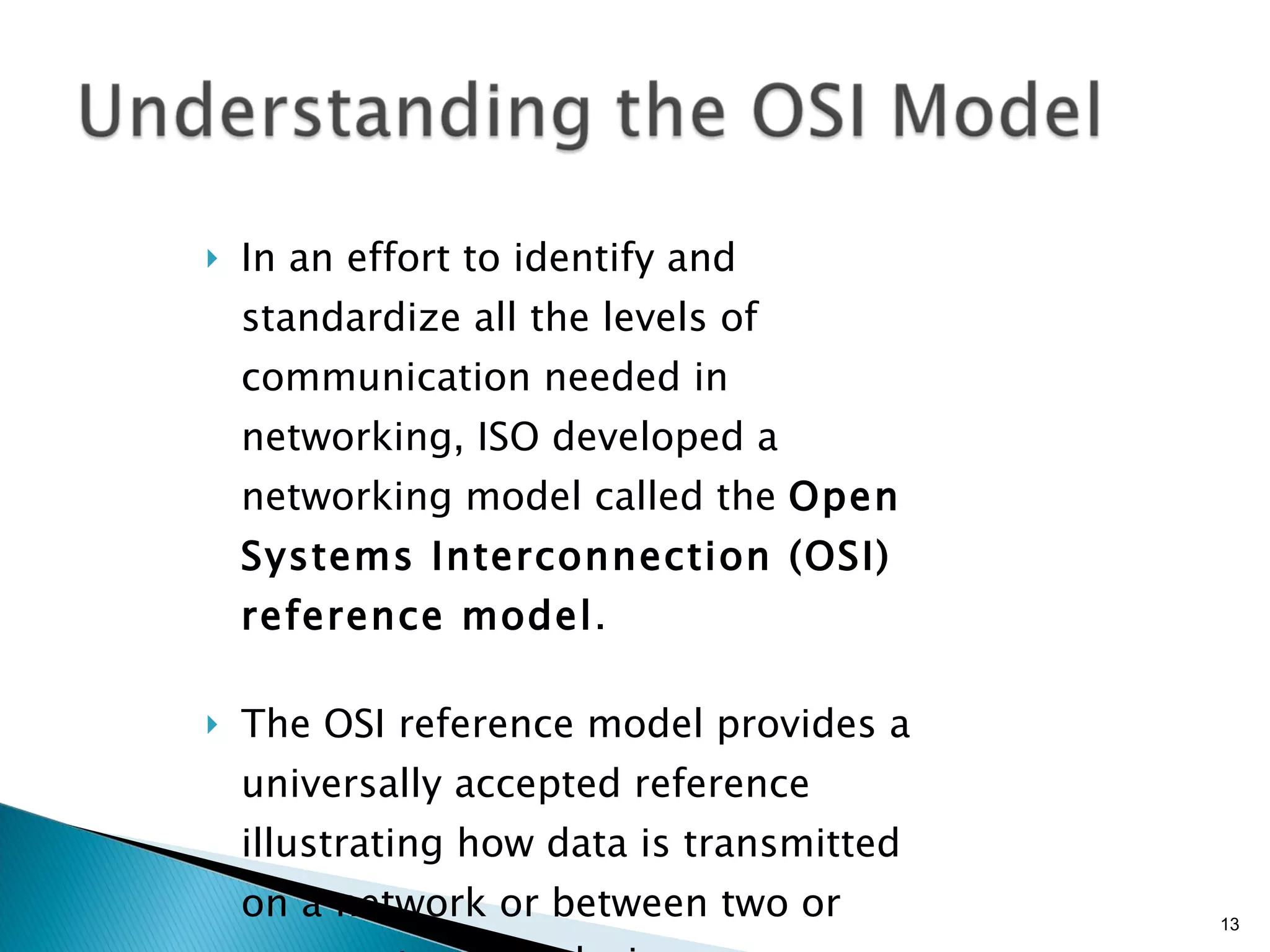
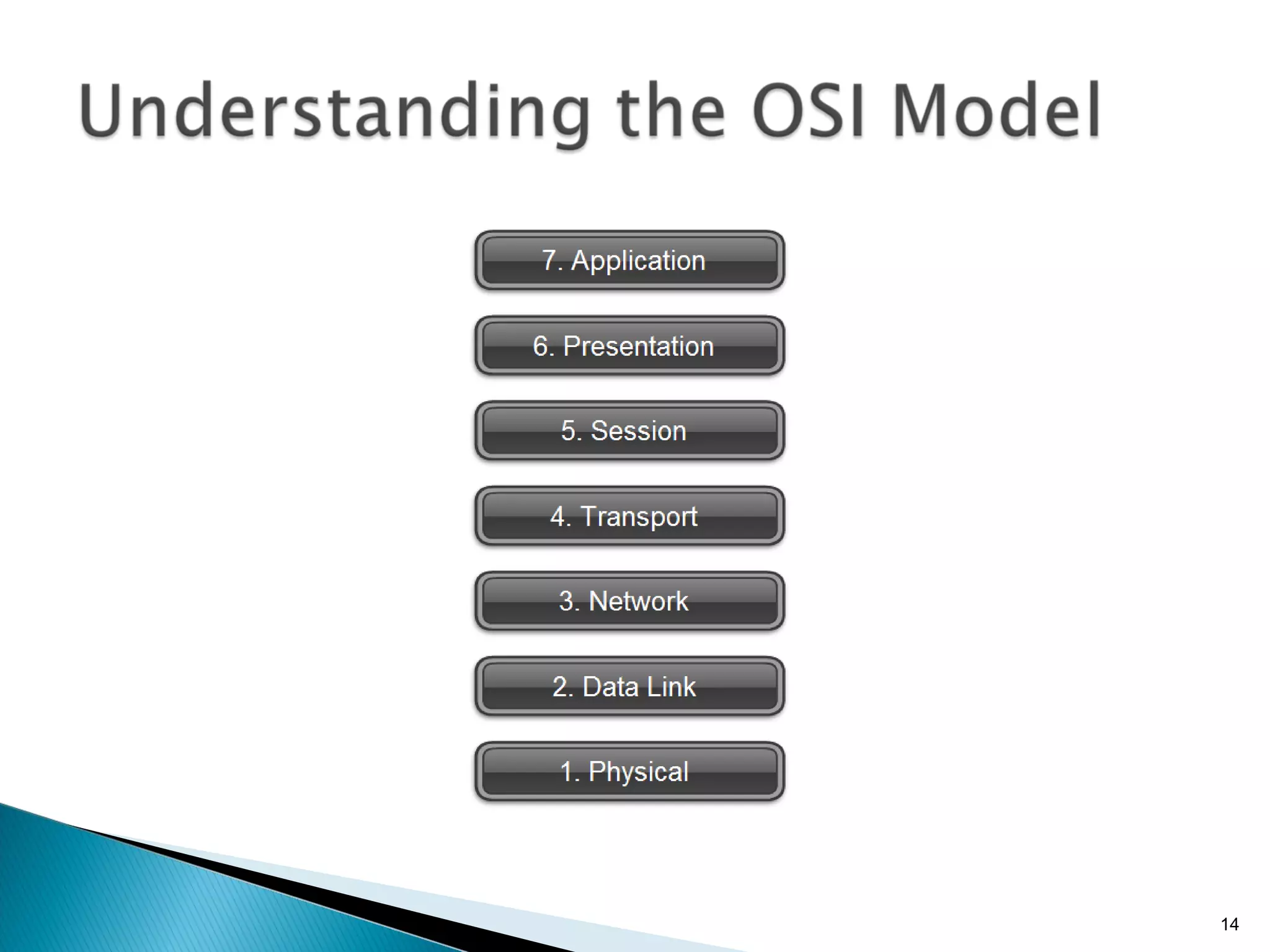
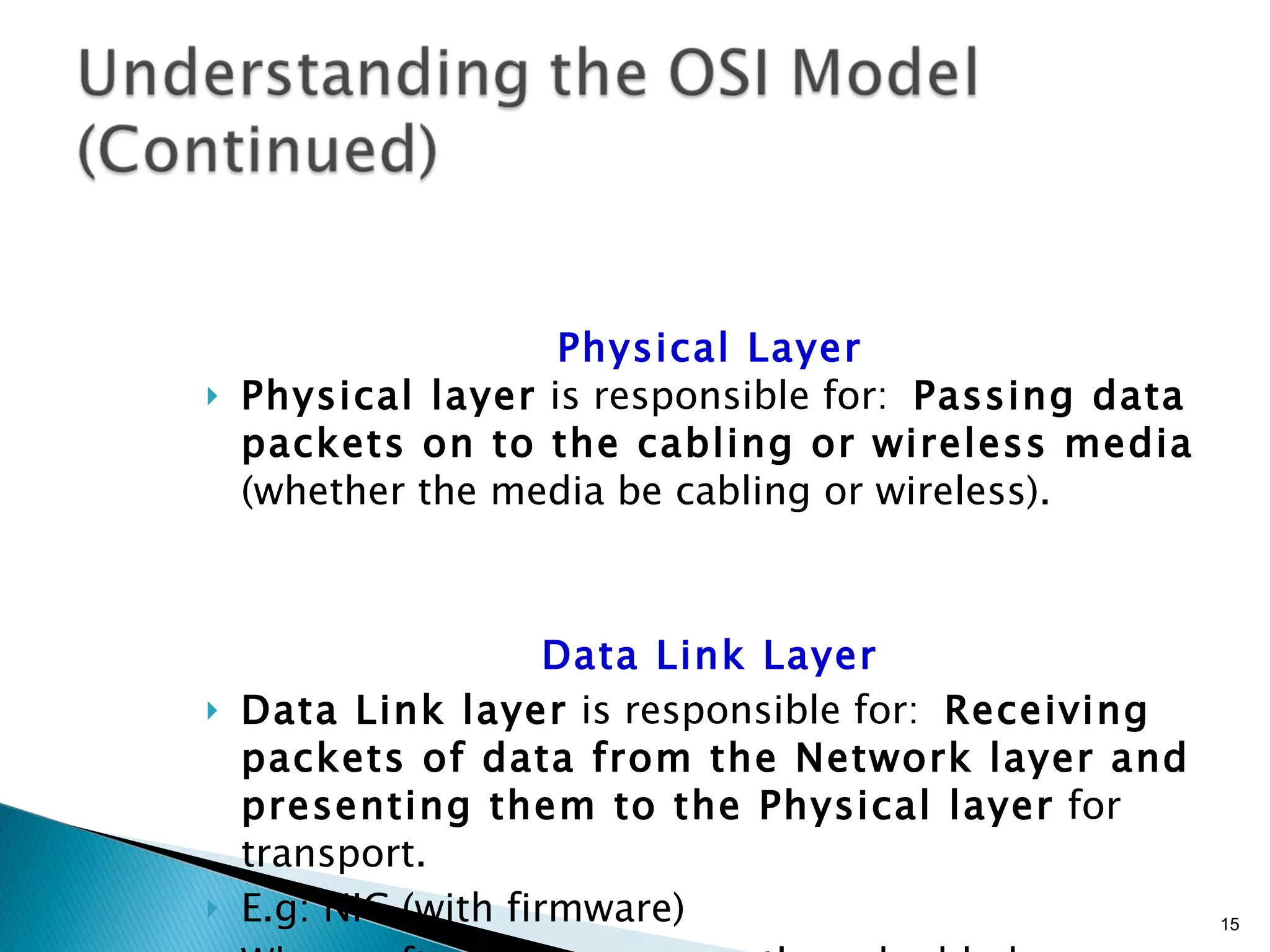
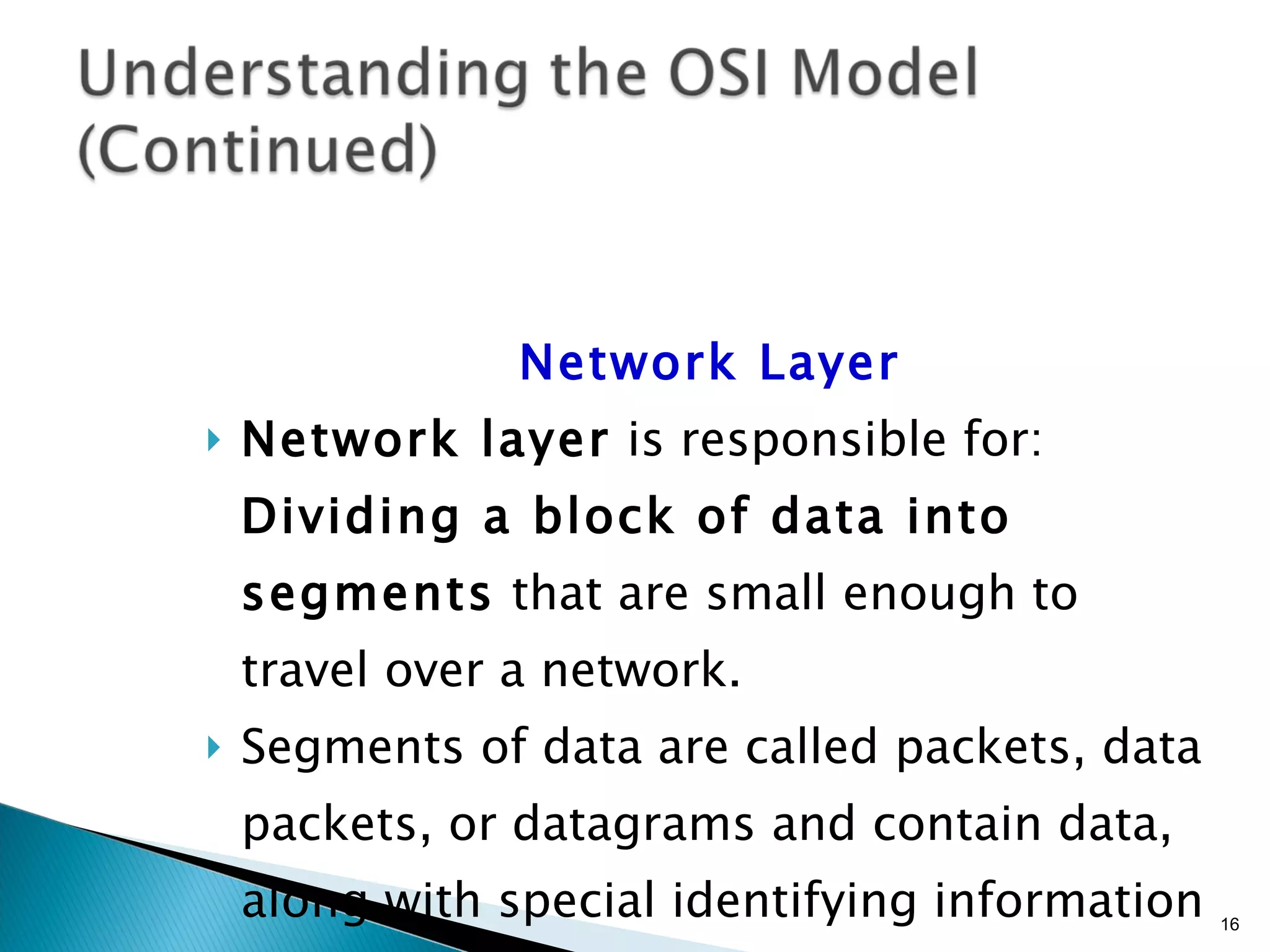
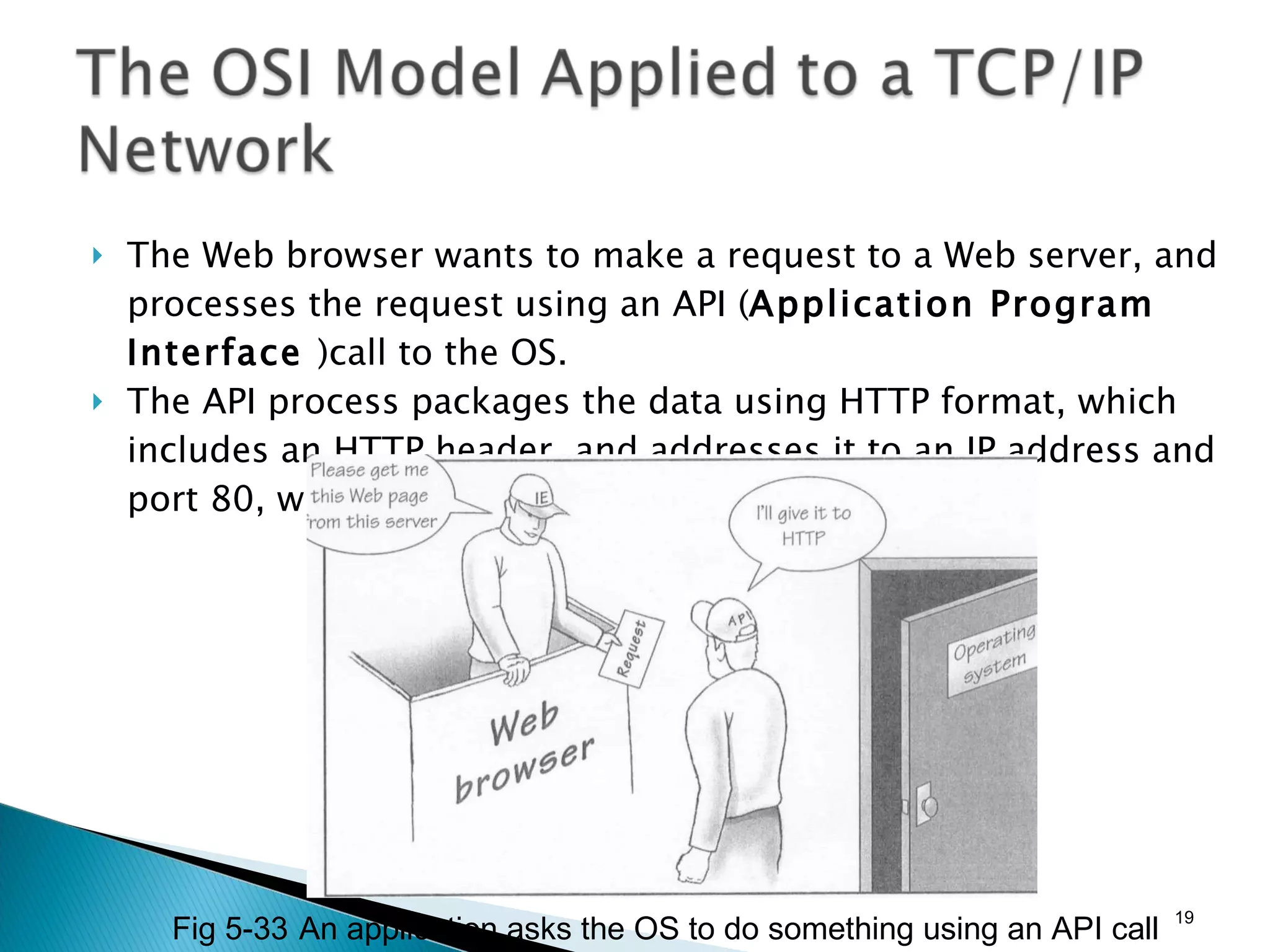
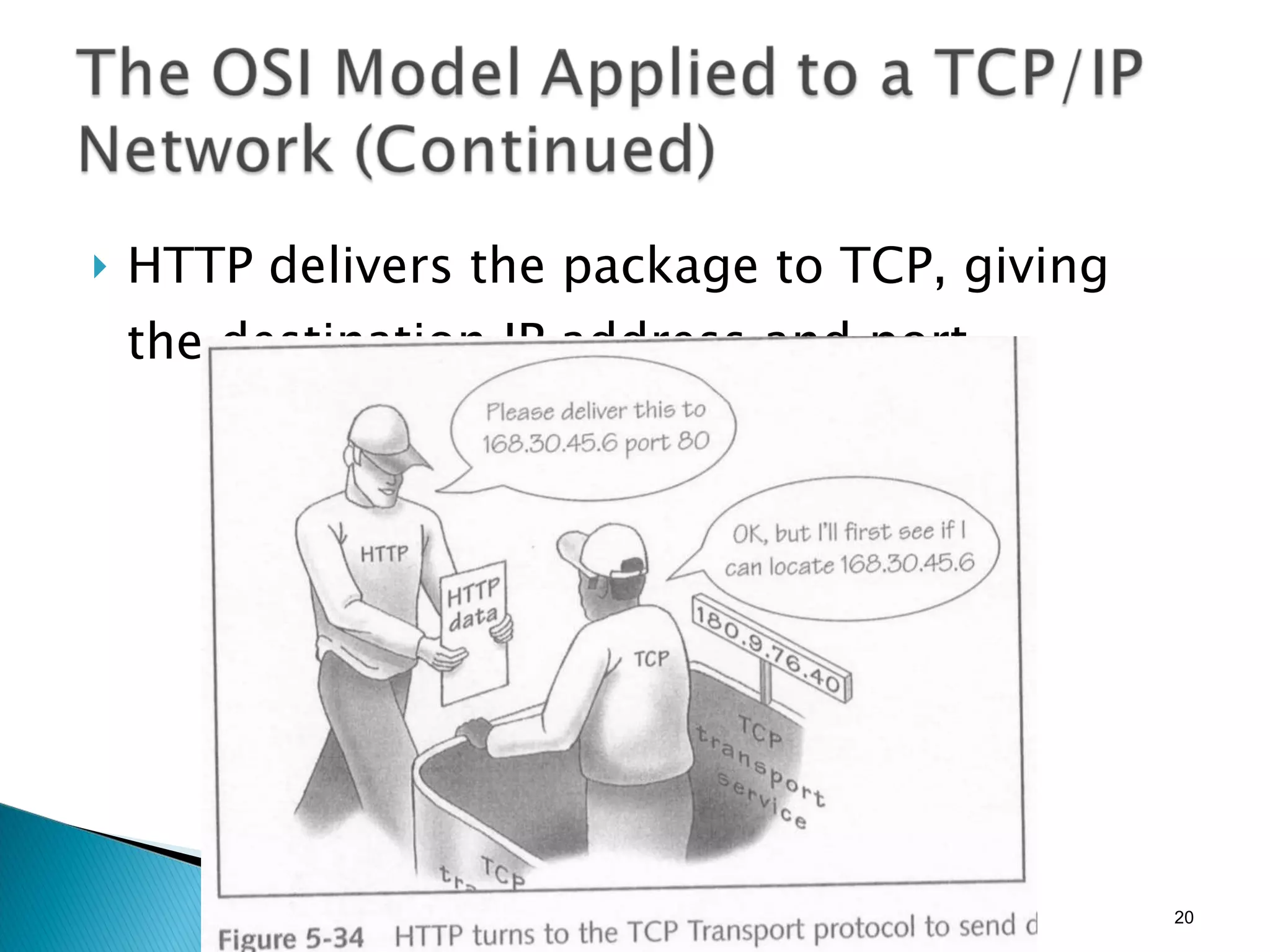
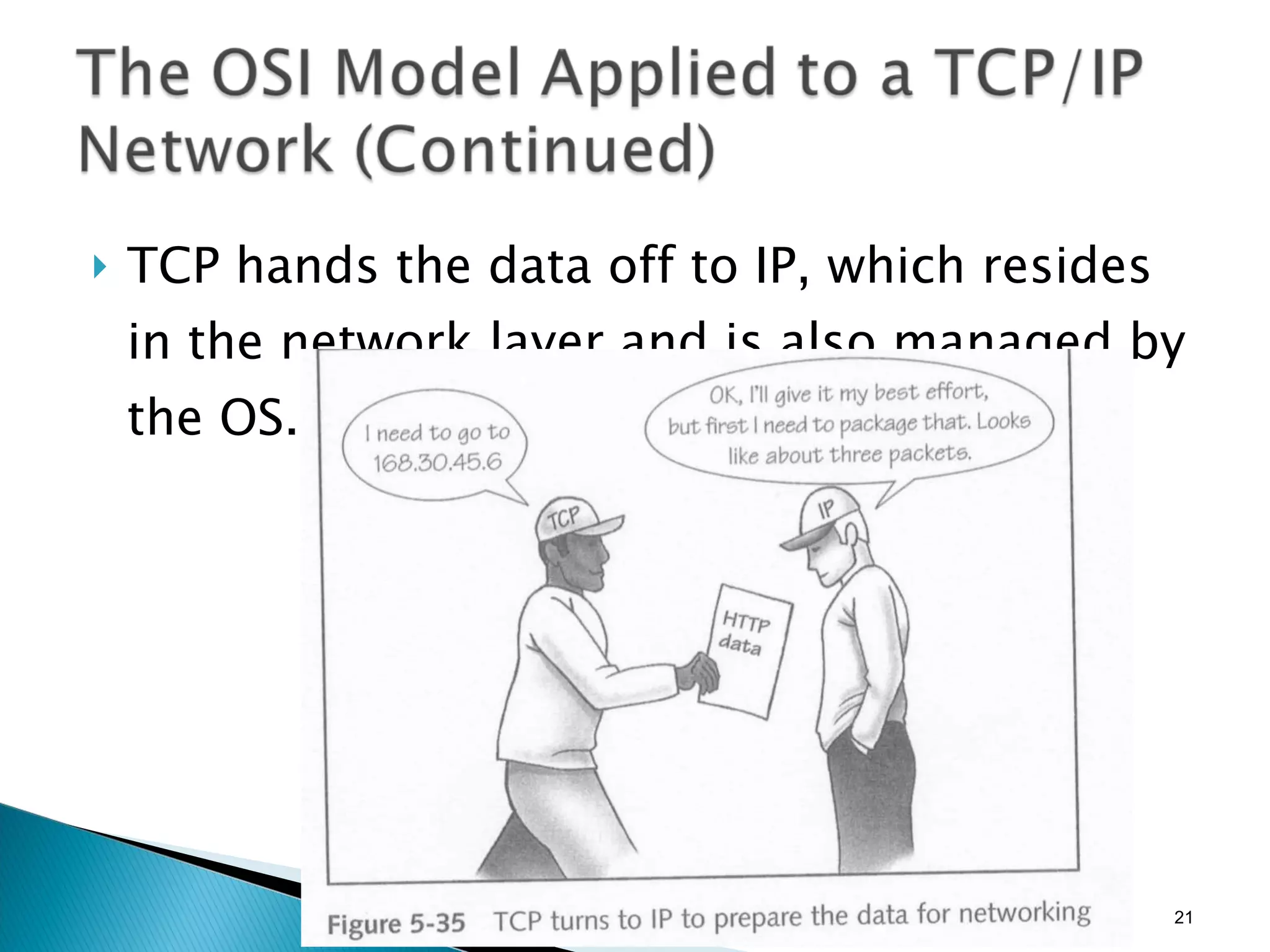
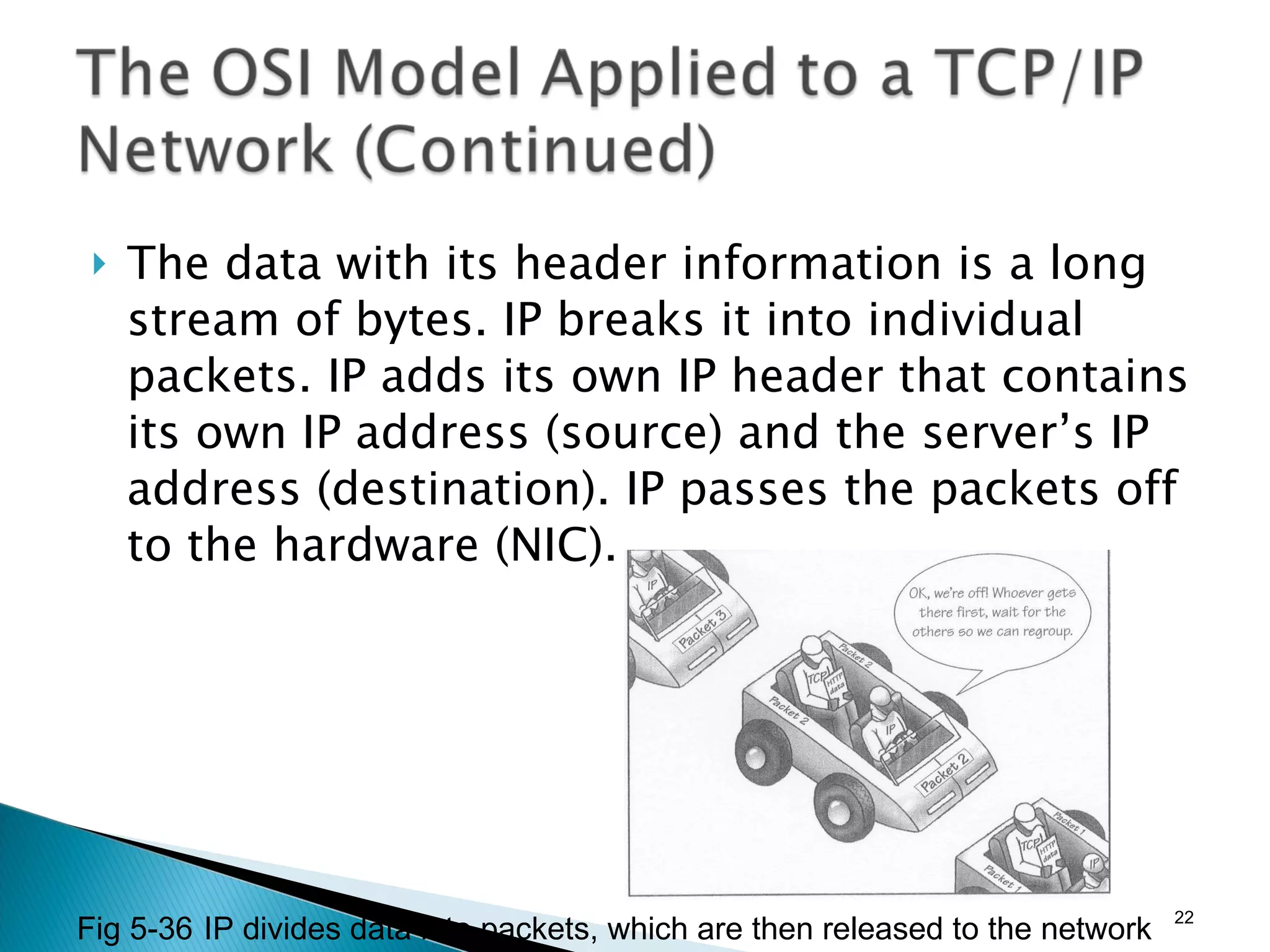
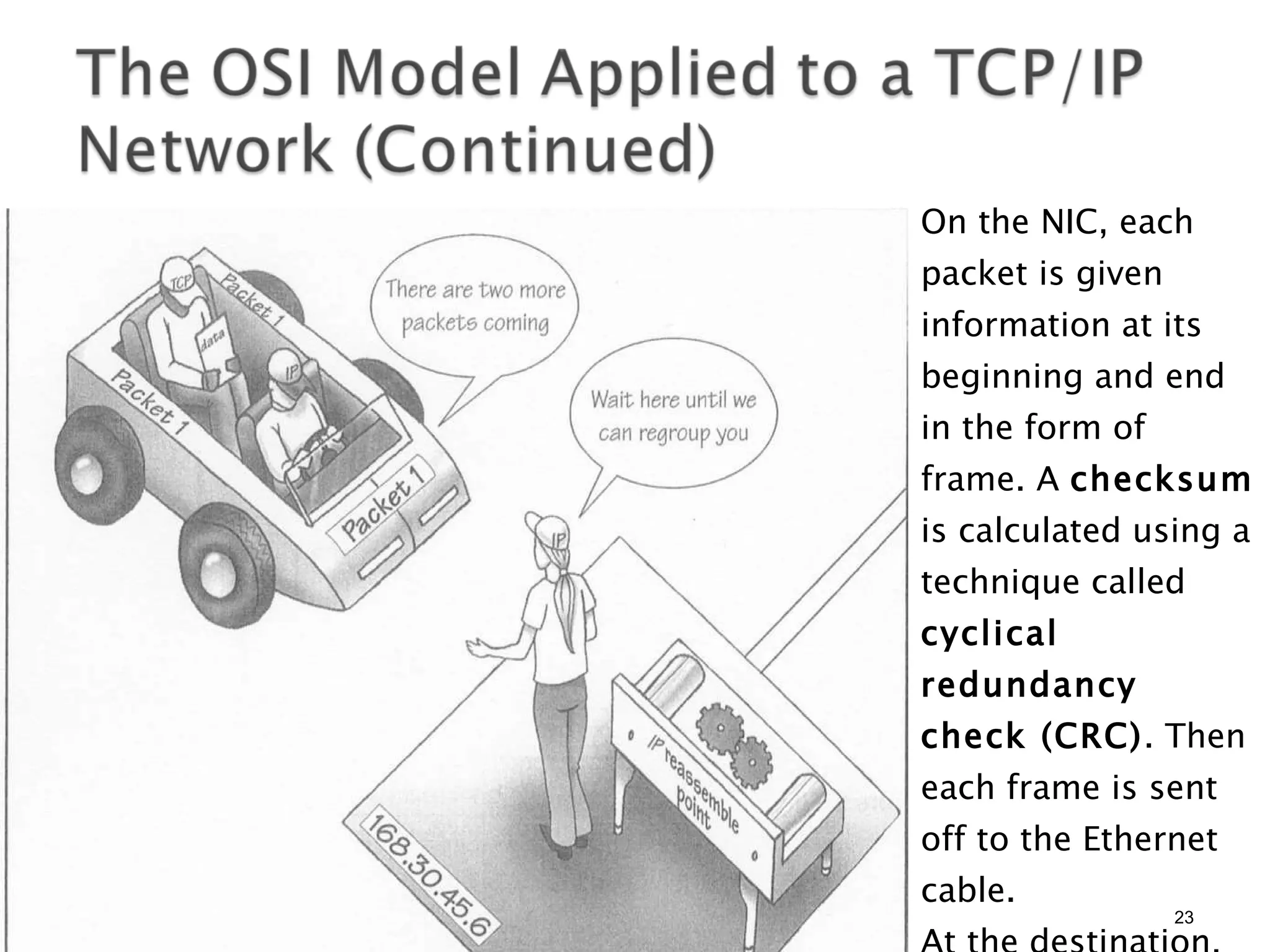
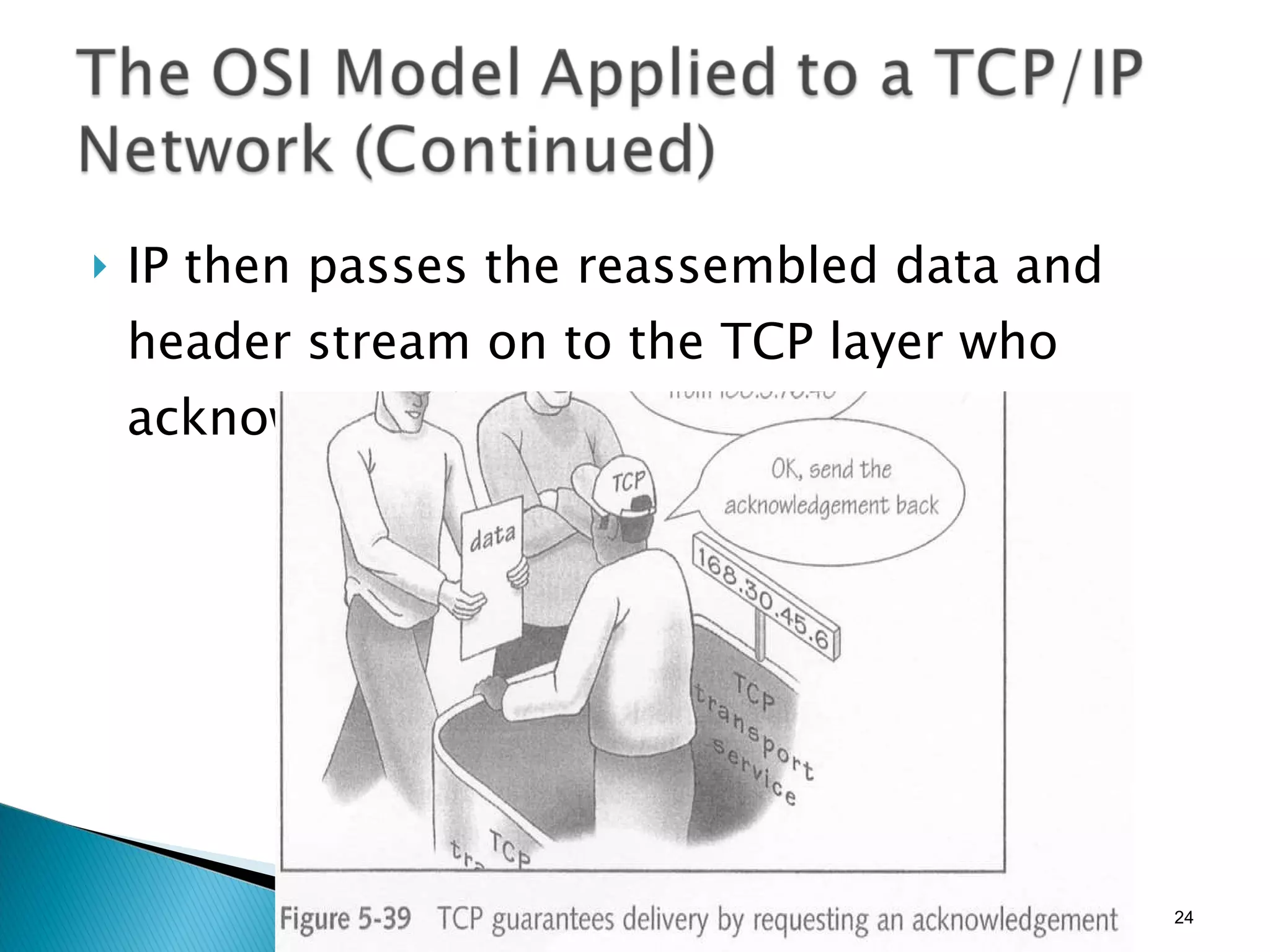
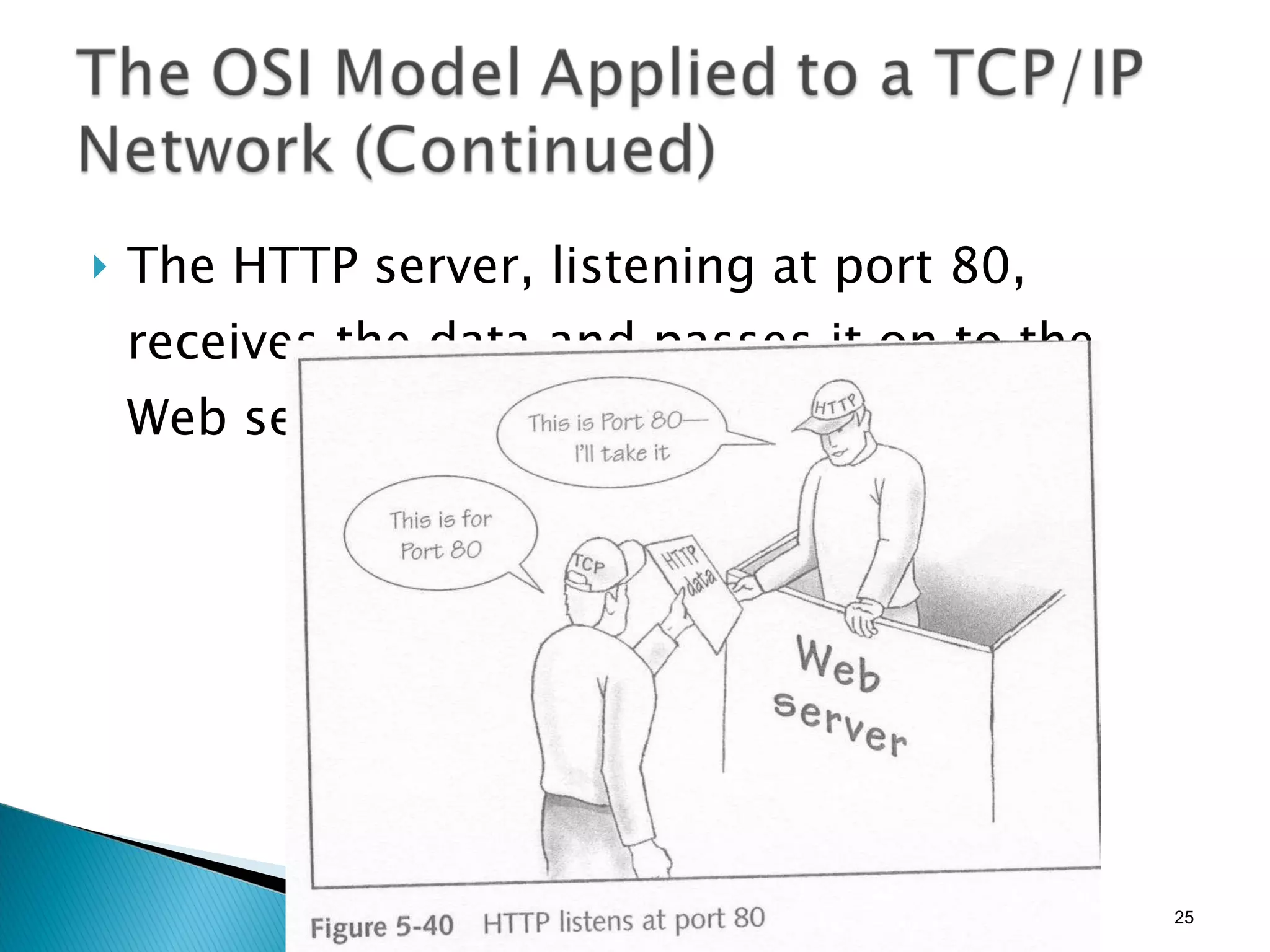
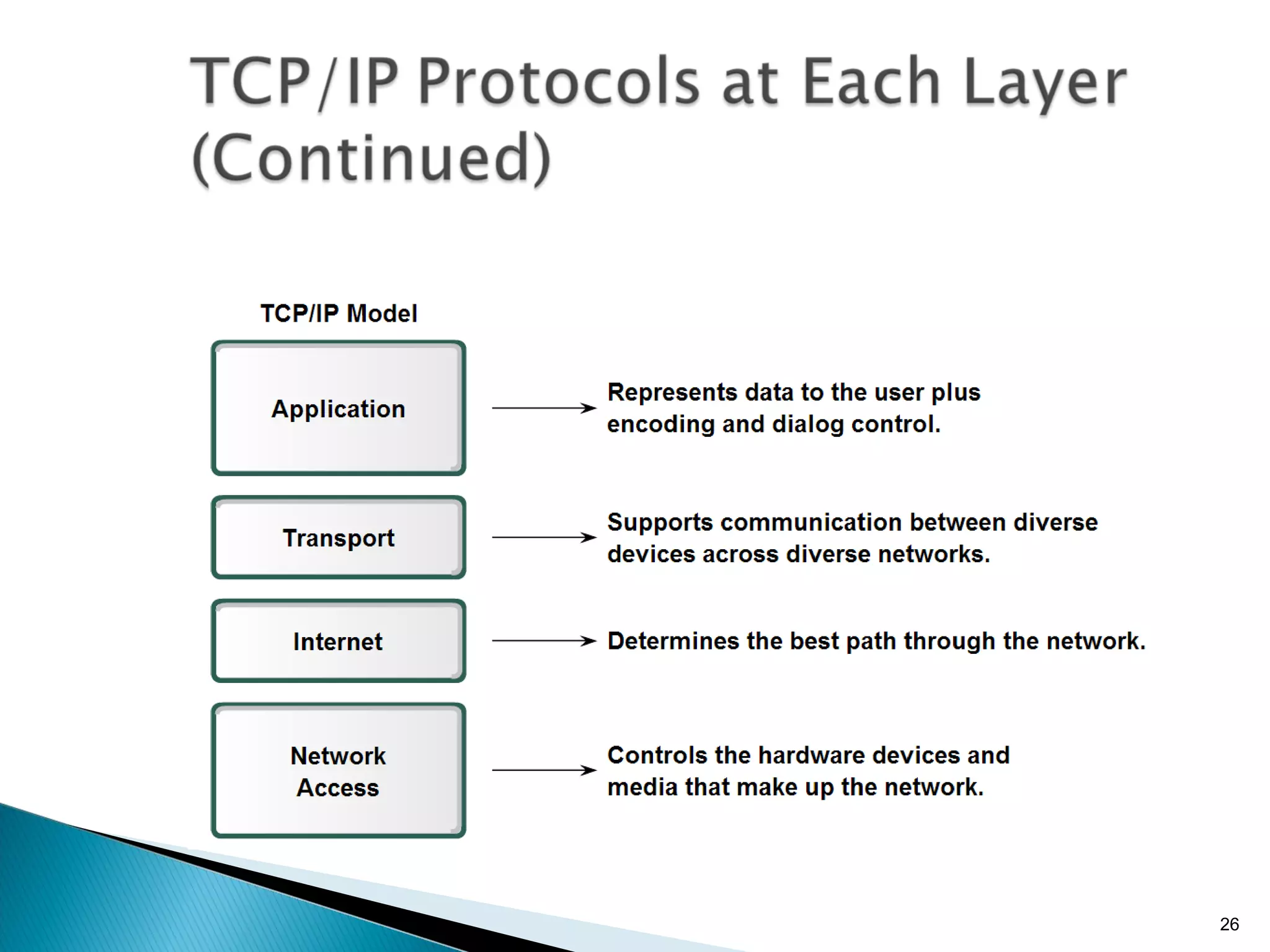
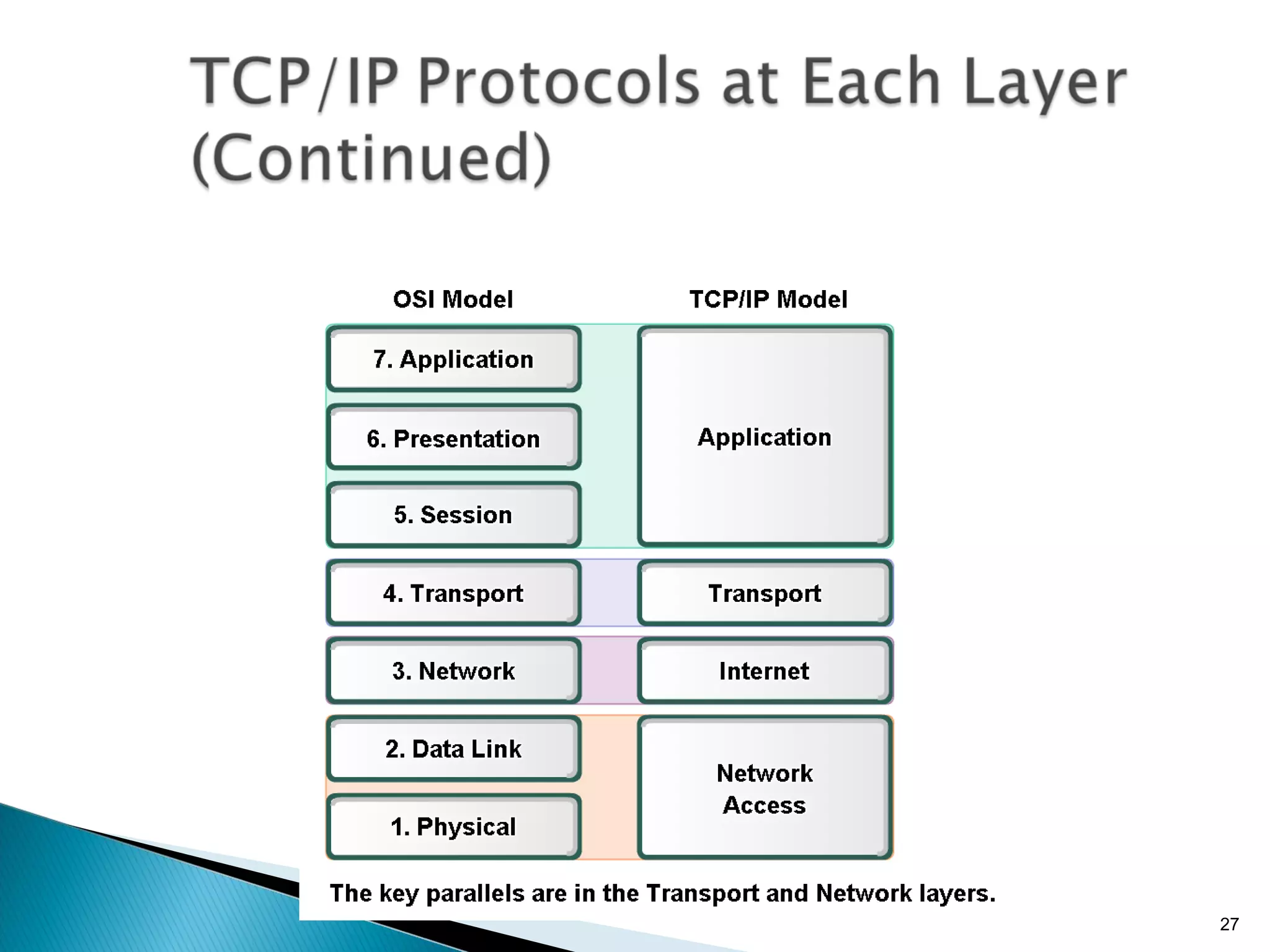
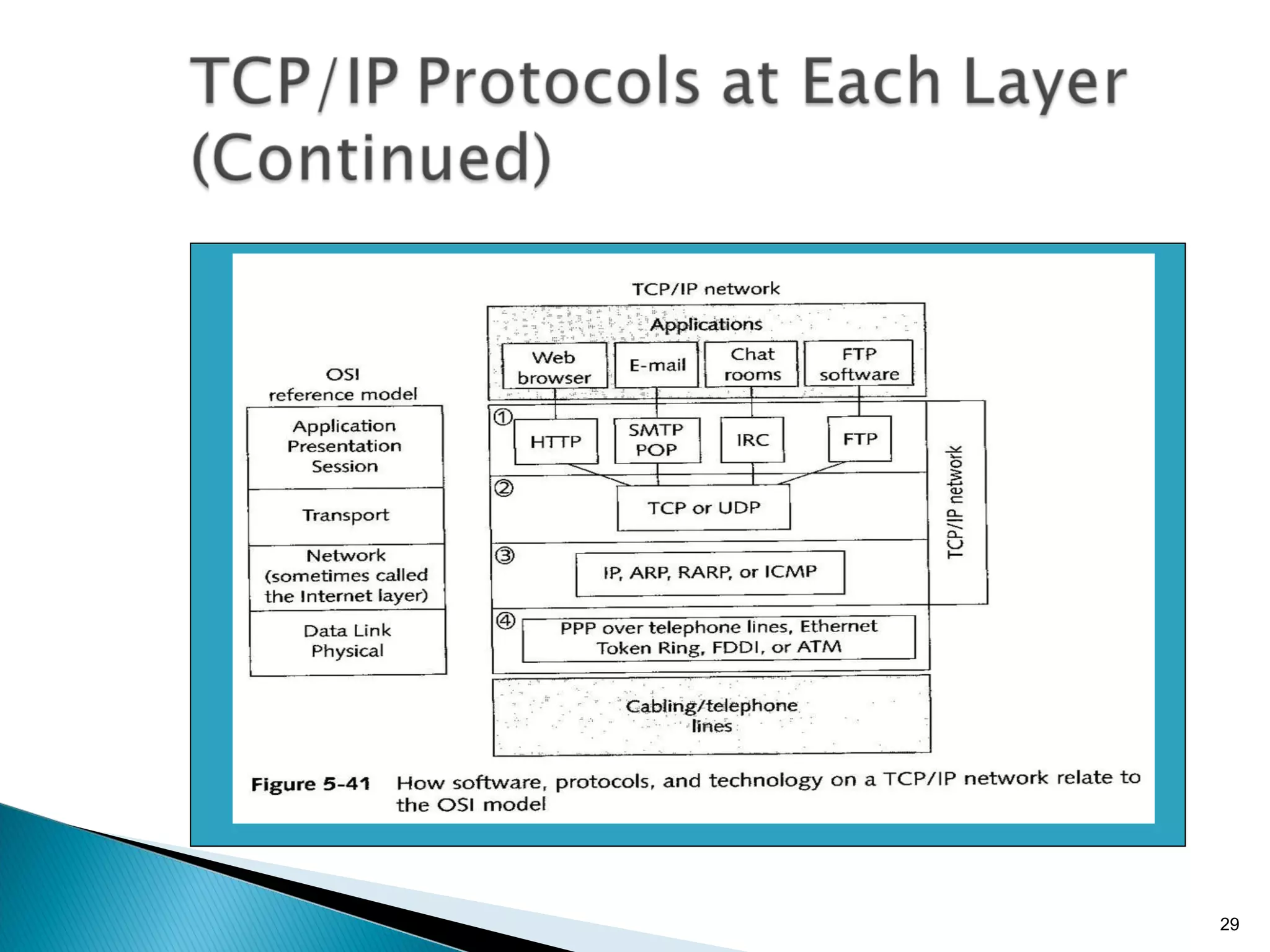
- The OSI model and what each layer is responsible for in data transmission.
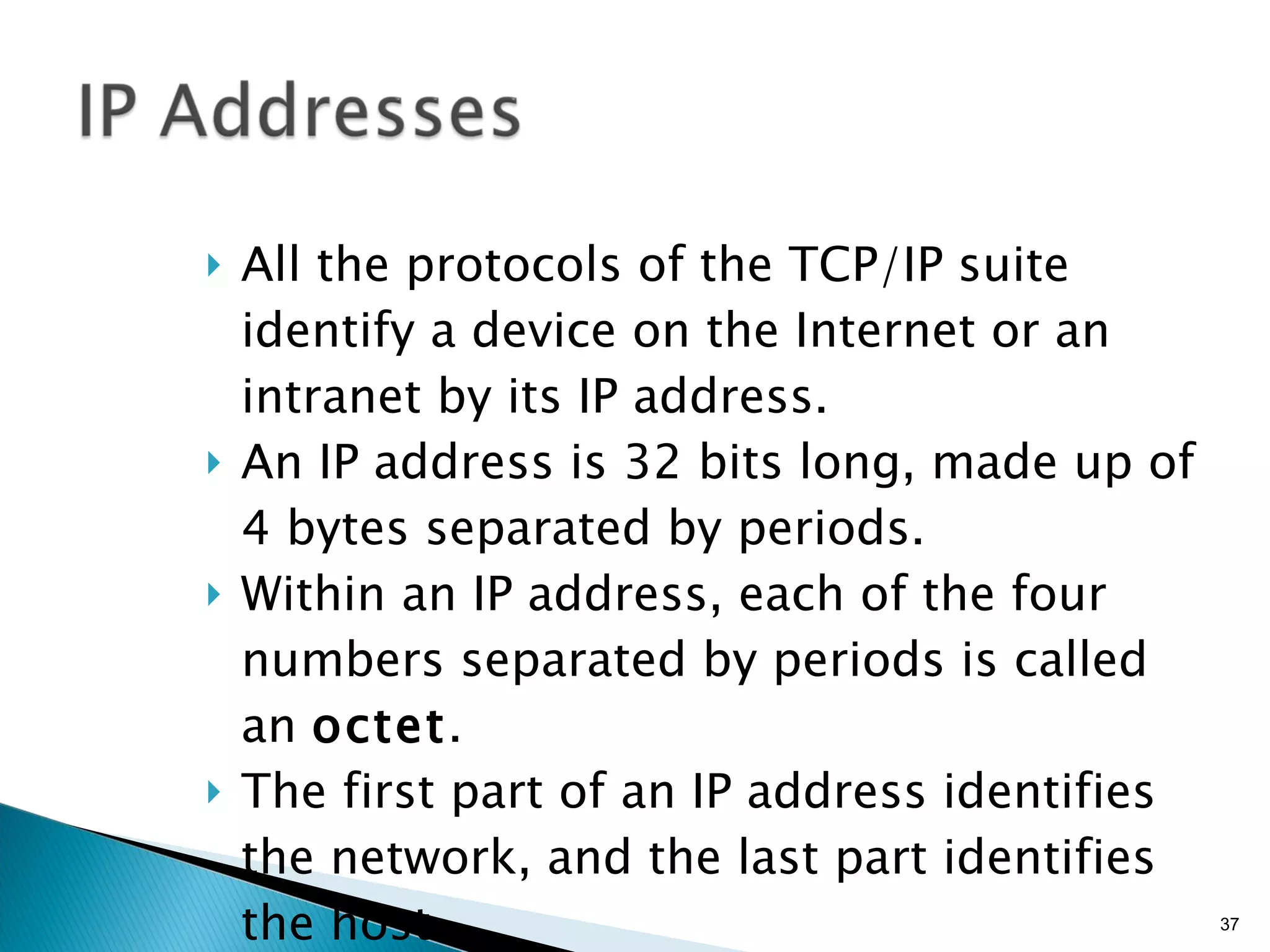
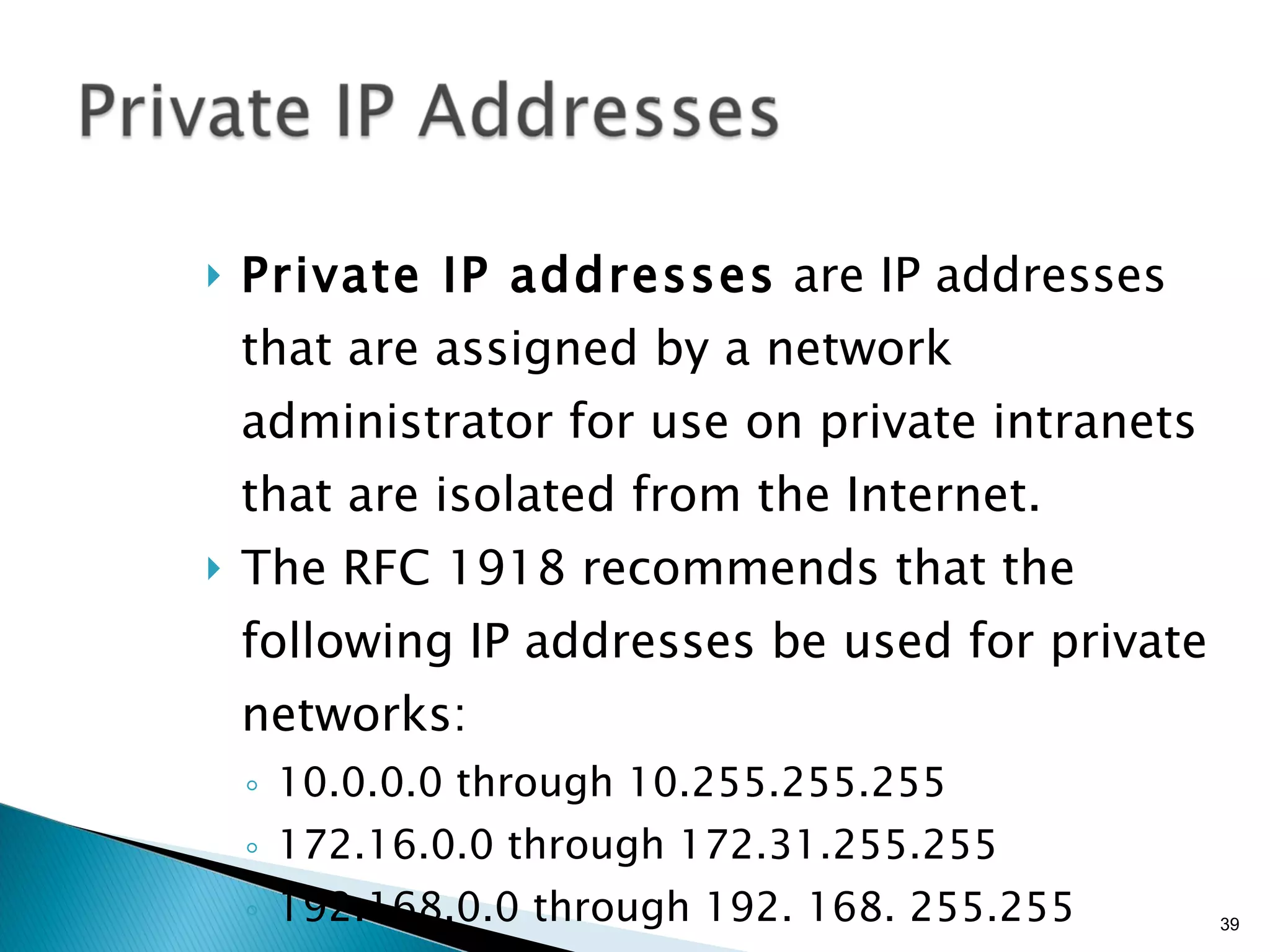
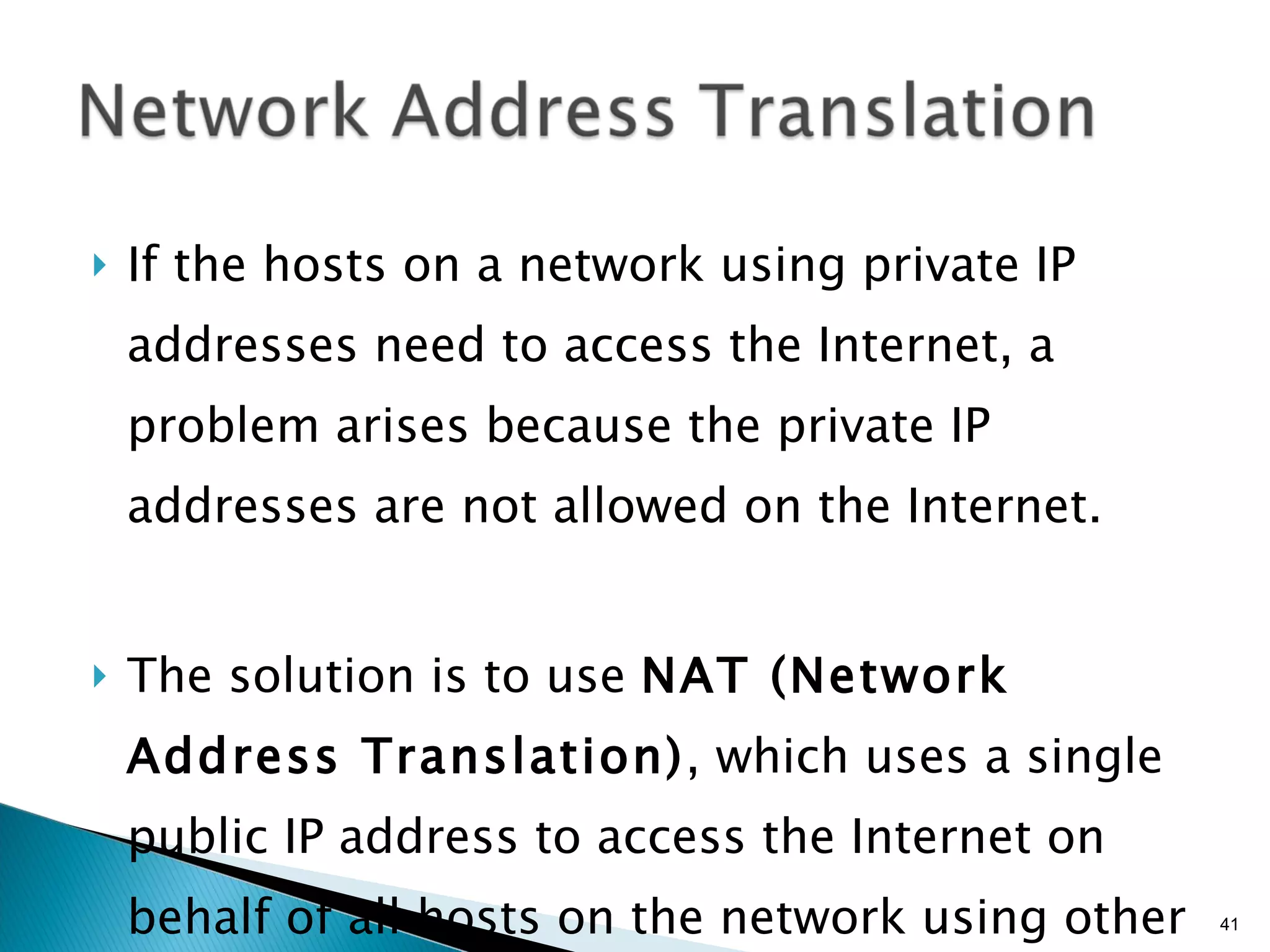
- Common network addressing schemes and protocols like IP, TCP, UDP, and IPv6.