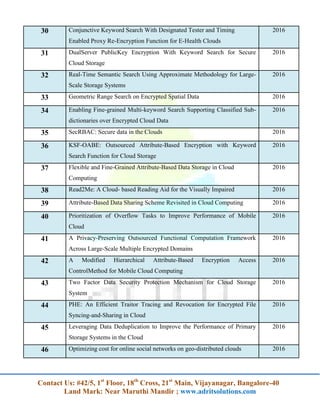
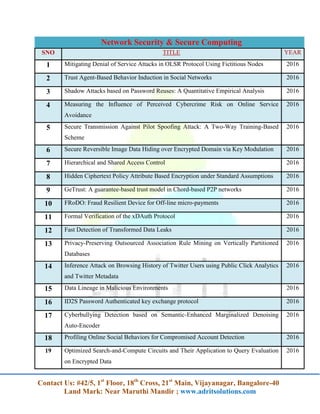
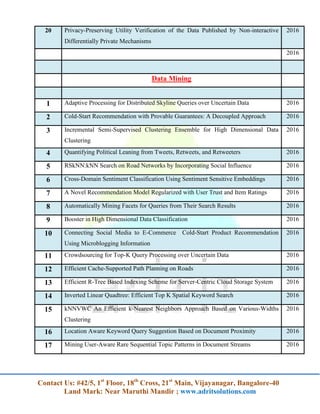
The document lists a series of projects and research topics related to cloud computing, network security, data mining, mobile computing, and other computing technologies for the year 2016. It provides detailed titles and focuses on various innovations such as data security, efficient algorithms, and privacy-preserving techniques. Additionally, it encourages contacting the organization for more information.