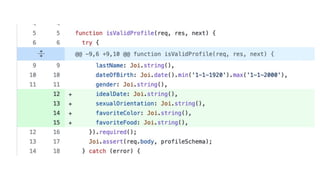
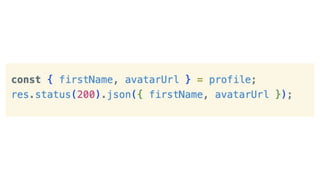
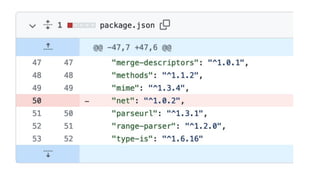
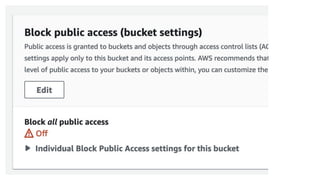
The document outlines essential considerations for reviewing code for security issues, emphasizing the importance of threat modeling, penetration testing, and proper input handling. Key areas to focus on include authentication, authorization, data leaks, dependency management, configuration, and caching issues. It provides practical tips for security awareness and improving security practices during code reviews.